3.1.4 Managing Data
This section explains different methods used to load and process data. Figure 7 shows the sequence for data loading:
Figure 3-5 Data Loading For AML/Fraud/KYC/FATCA/CTR Applications
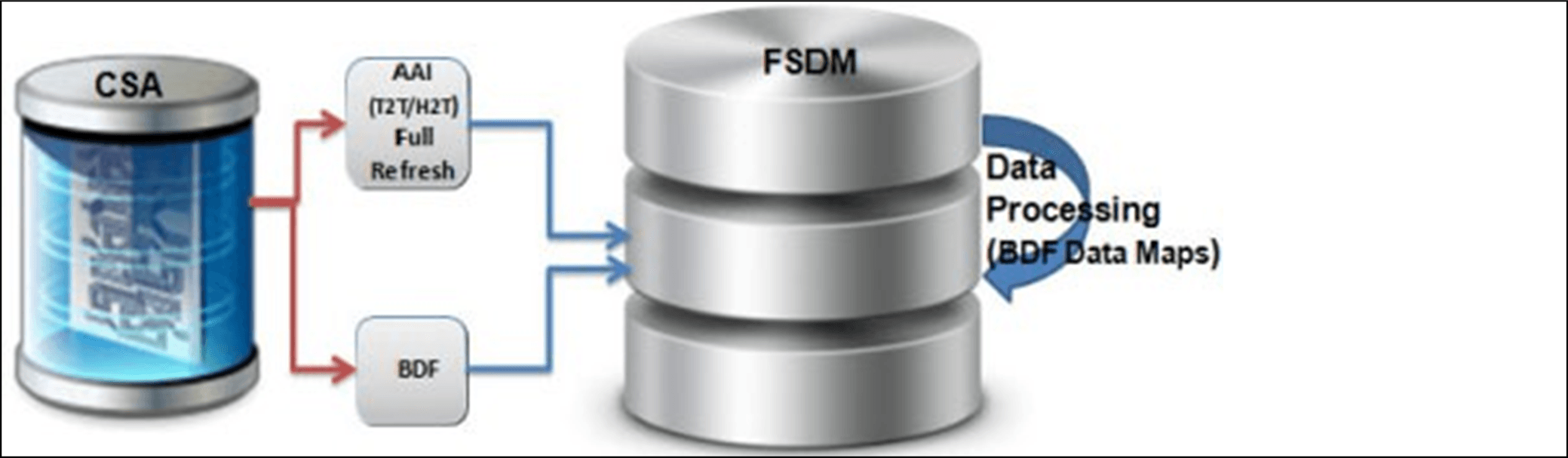
The following table provides the steps required to load data for Behavior Detection Applications, including CTR.
| Application | Steps | Group |
|---|---|---|
|
AML Fraud KYC FATCA CTR |
|
Group1 Group2 Group3 Group4 Group5 |