4.4 Mapping Security Attributes to Users
You can determine which security attribute controls the user's access permissions. Using this User Interface (UI), an Administrator can map Organizations and Users to different Security attributes.
Note:
Do not combine this activity with any other Administration Configuration activities.To map a Security Attribute, follow these steps:
- Log in as the KYC Administrator. The KYC application home page is displayed.
- Click User Security Administration , and then click Security Attribute Administration. The Anti Money Laundering page is displayed.
- In the Administration menu, select the User Administration sub-menu, and click Security Attribute Administration. The Security Attribute Administration page is displayed.
- Select the user type from the Choose User Type drop-down list (Organization or User).
Note:
Before proceeding with providing a user access through this User Interface (UI), all necessary data must be available in the appropriate database tables and the user must be created. - To view the Onboarding users, map the Onboarding role to the OB KYC Administrator group.
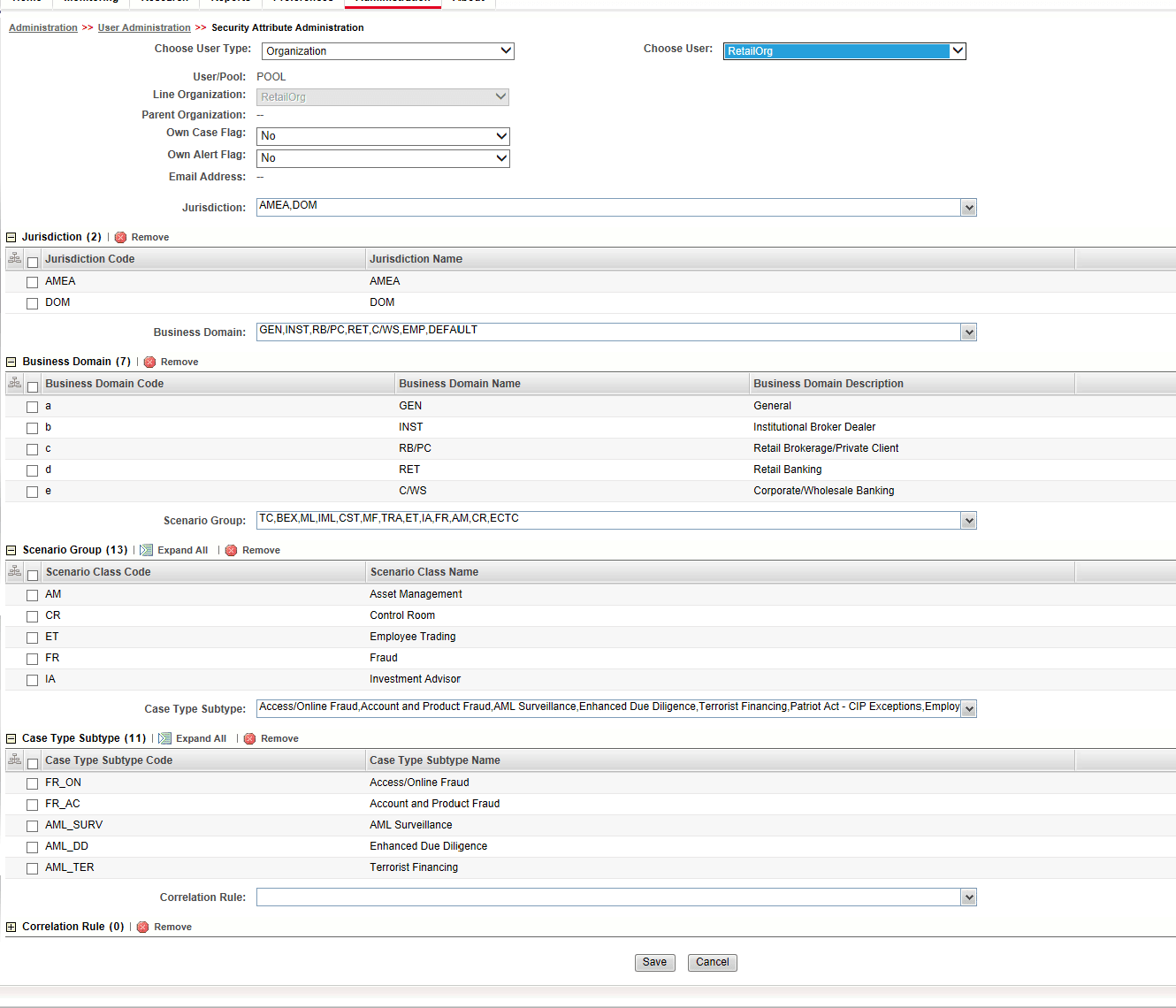
- Based upon your User Type selection, the Choose User drop-down list changes. Select the user from the Choose User drop-down list. The relevant Security Attribute Administration page is displayed.
Figure 5: Security Attribute Administration Page
Figure 4-4 Security Attribute Administration Page
Note:
- To update the user profiles before proceeding with mapping any security attributes, select User from the Choose User Type drop-down list. When chosen, all the updates made to all the user profiles through User Maintenance UI are imported from the CSSMS_USER_PROFILE table of the OFS AAI ATOMIC schema to the KDD_REVIEW_OWNER table of the ATOMIC schema.
- If you delete a user through the Security Management application screen, you must come back to the Security Attribute Administration screen and select the value User from the Choose User Type drop-down list. Then the deleted user is updated in the KDD_REVIEW_OWNER table against the column actv_flg as N, and that user becomes inactive.
The following table shows the security attributes.
Table 4-11 Security Attributes
Column Name Description Organization Select an organization from the drop-down list. A User or Organization's access to other Organizations depends on the selection(s) made for this organization parameter. For example, suppose a user is mapped to Org1 and Org2. In that case, it implies that this user can access alerts and cases belonging to these two organizations, provided other security attributes also match. Own Case Flag Select whether this user type owns a case flag from the drop-down list. Own Alert Flag Select whether this user type owns an alert flag from the drop-down list.
The Own Alert and Case flag is required for taking ownership of the alerts and cases. If an alert user must perform a Promote To Case action, then the user must be mapped to any one of the following user groups:
- Case Supervisor
- Case Analyst1
- Case Analyst2
PRNT_ORG_CD The parent organization of which this organization is a child. This must reference an ORG_CD in the KDD_ORG table. MODFY_DT Last modified date and time for this organization record. MODFY_ID User ID of the user who last modified this organization data. This must reference a user in the Investigation Owner table (KDD_REVIEW_OWNER.OWNER_SEQ_ID). COMMENT_TX Additional remarks added by the user. Business Organization The default Business Organization is displayed, but you can select the business organization from the drop-down list. Jurisdictions Select the jurisdictions from the drop-down list. Mapping one or more jurisdictions to a user or organization allow this user or organization to access cases, alerts, watch lists, and watch list members belonging to the mapped jurisdiction. The selected jurisdictions are displayed in the Jurisdictions section after you save your selection. Business Domain Select the business domains from the drop-down list. Mapping one or more business domains to a user or organization allow this user or organization to access cases, alerts, watch lists, and watch list members belonging to the mapped business domains. The selected jurisdictions are displayed in the Jurisdictions section after you save your selection. Scenario Group Select the scenario group from the drop-down list. Mapping one or more Scenario Groups to a user or organization allows this user or organization to access alerts that belong to the mapped scenario Group. The selected jurisdictions are displayed in the Jurisdictions section after you save your selection. Case Type Select the case type from the drop-down list. Mapping one or more Case Types to a user or organization allows this user or organization to access cases that belong to the mapped Case Type. The selected jurisdictions are displayed in the Case Types section after you save your selection. Correlation Rule Select the correlation rule from the drop-down list. Mapping one or more correlation rules allows the user to view the correlations generated based on the mapped correlation. The selected jurisdictions are displayed in the correlation section after you save your selection. - Click Save. A confirmation message is displayed.
- Click OK. A confirmation message is displayed.
- Click OK. The updated Security Attribute page is displayed.