2 About Oracle Financial Services Trade-Based Anti Money Laundering
This topic provides a brief overview of Oracle Financial Services Trade-Based Anti Money Laundering (TBAML) in terms of its architecture and operations.
About TBAML
- Efficiently screen goods, ports and involved party names extracted from SWIFT MT messages as well as on federal trade data against various lists such as sanctions lists, watch lists, and so on.
- Continuously monitor trade finance transactions using a risk based approach for potential TBML activities, such as TBML red flag topologies, by assessing the trade finance customer, transactions (specifically goods, contract amount, goods price), and involved counterparties (name and address).
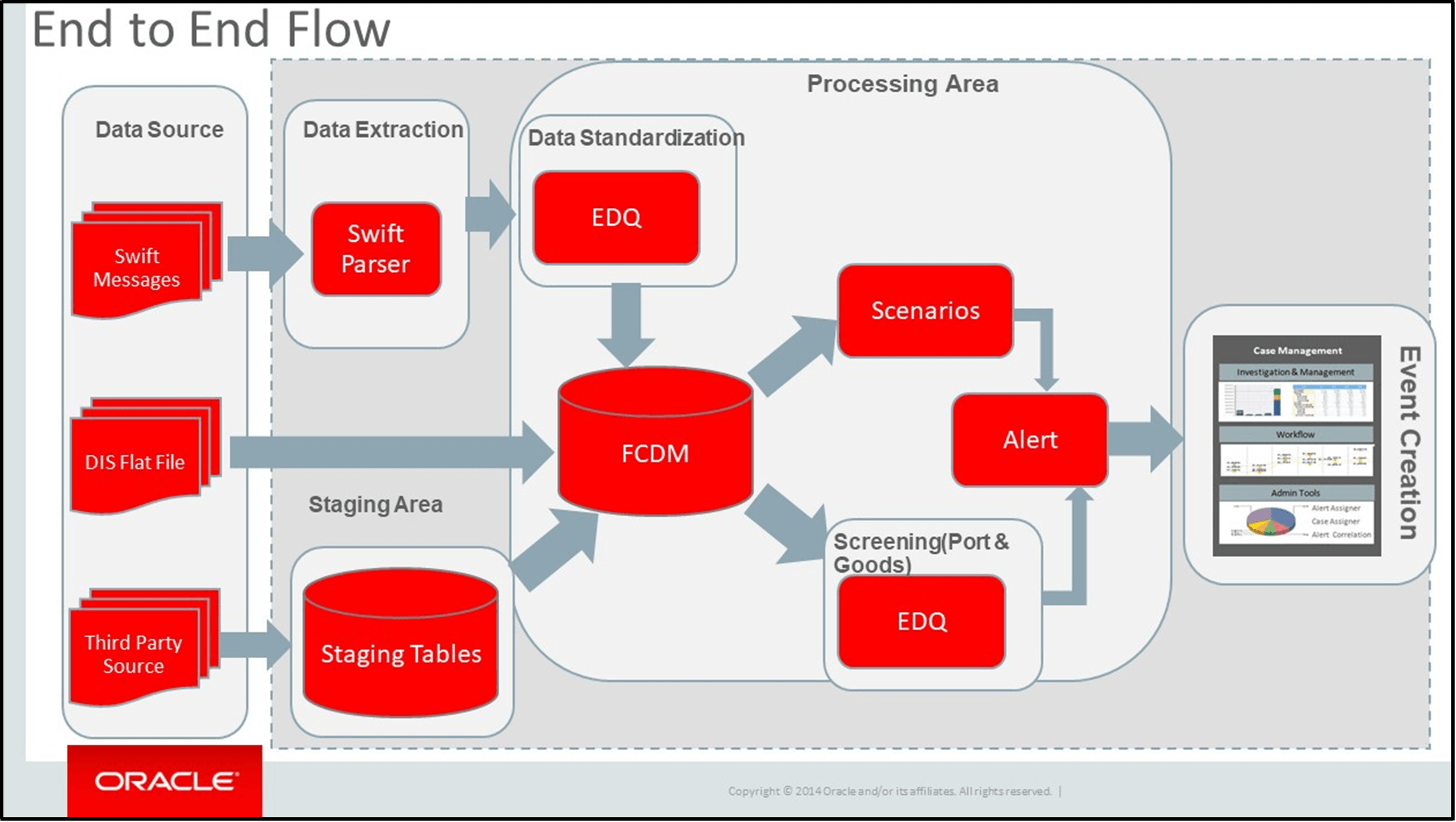
TBAML Architecture
TBAML extracts data from SWIFT messages via the Swift Parser functionality. That data, and data provided by the Oracle client via DIS File or another source, is fed into staging tables and then into the FCDM where the data is either standardized (Port) and screened (Port, Goods, Name and Address) through EDQ functionality, or run through scenarios to generate an FCM event.
Deployment View
The TBAML architecture from the perspective of its deployment illustrates deployment of the major subsystems across servers. Additionally, the deployment view shows the primary communications links and protocols between the processing nodes.
- Web browser
- Web server
- Web application server
Security View
The security view describes the architecture and use of security features of the network in a TBAML architecture deployment. TBAML uses an inbuilt Security Management System (SMS) for its authentication and authorization. The SMS has a set of database tables which store information about user authentication.
Installation of 128-bit encryption support from Microsoft can secure the web browser. Oracle encourages using the Secure Socket Layer (SSL) between the web browser and web server for login transaction, while the web Application server uses a browser cookie to track a user's session. This cookie is temporary and resides only in browser memory. When the user closes the browser, the system deletes the cookie automatically.
TBAML uses Advanced Encryption Standard (AES) security to encrypt passwords that reside in database tables in the ATOMIC schema on the database server and also encrypts the passwords that reside in configuration files on the server.
The EAM tool is an optional third-party pluggable component of the security view. The tool’s integration boundaries provide an Authorization header, form field with principal, or embedded principal to the web Application server through a web server plug-in. The tool also passes the same user IDs that the TBAML directory server uses.