2.2 Access Compliance Studio Using SAML Realm
This section provides information on managing users who can access Compliance Studio with Identity Provider (IdP or IDP). The IdP acts as the Single Sign-On (SSO) service provider for implementations between Compliance Studio, Investigation Hub, and Enterprise Case Management. This configuration prevents separate login for each application.
An identity provider (IdP) is a service that stores and verifies user identity. IdPs work with single sign-on (SSO) providers to authenticate users. An identity provider (IdP or IDP) stores and manages users' digital identities. An IdP checks user identities via username-password combinations and other factors, or it may simply provide a list of user identities that another service provider (like an SSO) checks.
See the User Groups section for Preconfigured Groups to access Compliance Studio using SAMLRealm.
- Create the following Group in the IDP system. For more information
on creating groups in IDP, see the OFS Admin Console User
Guide.
- Create the new groups with the same name as the pre-configured groups. For more information, see the User Groups section.
- Create a SAML application in IDP.
- Configure the SAML application.
Key configurations in the SAML application is as follows:
- Entity ID:
https://<FQDN of Compliance studio Linux Server>:7001/cs - Assertion Consumer URL:
http:// <FQDN of Compliance studio Linux Server>:7001/cs/homeNote:
Response in SAML response must be signed. - Include Signing Certificate in Signature:Enabled
- Include Signing Certificate in Signature: SHA-256
- Enable Single Logout: Enabled
- Logout Binding: POST
- Single Logout URL
(SAML_LOGOUT_URL):
http://<FQDN of compliance studio>:7001/cs/signoff - Logout Response URL:
http://<FQDN of compliance studio>:7001/cs/signoff - Encrypt Assertion: Disabled
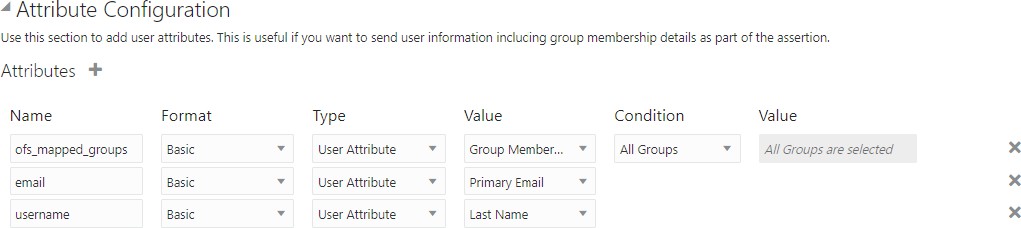
- SAML Attribute Configuration
Update the SAML attribute configuration as tabulated in the following table.
Table 2-4 Attribute Configuration
Name Format Type Value Condition ofs_mapped_groups Basic User Attribute Group Member All Groups email Basic User Attribute Primary Email - username Basic User Attribute Last Name -
- Entity ID:
- Create a user and map the user groups to the respective user based on the user roles.