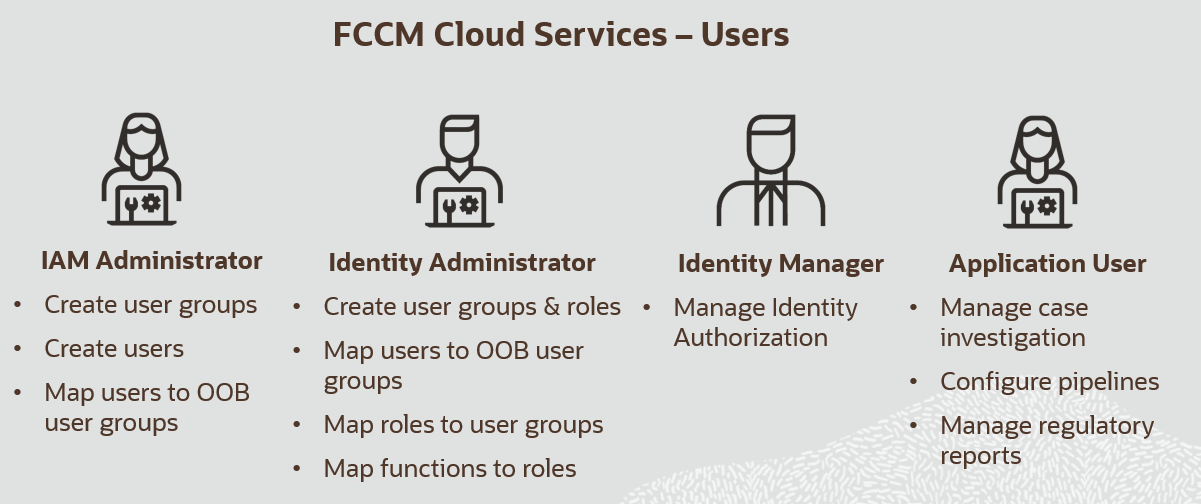
3 User Roles and Privileges
This topic provides information about mapping users, groups, roles, and functions to access the application.
In Oracle Financial Crime and Compliance Management Cloud Service, users have roles through which they gain access to functions and data. Users can have any number of roles.
The following figure shows the User Persona Details:
Note:
User-Group mapping changes from Identity Access Management will take time to sync with application. If these changes are made during an active user session then it will be reflected on next login.
Role-Based Access Control
Role-based security in Oracle Financial Services Crime and Compliance Management Know Your Customer Cloud Service controls who can do what on which data.
Table 3-1 Role-based Access Control
| Component | Description |
|---|---|
| Who | Is a role assigned to a user? |
| What | Is a function that users with the role can perform? |
| Which Data | Is the set of data that users with the role can access when performing the function? |
Table 3-2 Examples of Role-based Access Control
| Who | What | Which Data |
|---|---|---|
| Data Administrator | Can perform Data Preparation and ingestion | Business Data |
| Case Analyst | Can view, analyze, and act on cases | Business and Operational Data |
User Group and Roles Mapping in Oracle FCCM Cloud Service
The following table provides the User Group, User Role mapping, and activities.
Table 3-3 User Group and Roles Mapping for KYC
| Group | User Role | Functionality |
|---|---|---|
| Identity Administrator | Identity Administrator |
|
| Identity Authorizer | Identity Authorizer | Authorize the Identity and access management operations |
| IAM Administrator | IAM Administrator |
|
| Pipeline Administrator Group | KYC Administrator |
|
| KYC Administrator Group | KYC Administrator |
|
| Job Administrator Group | KYC Administrator | Manage jobs |
| Scheduler Administrator Group | KYC Administrator | Manage batches |
| Master Data Administrator Group | KYC Administrator | Configure master data |
| Watchlist Administrator Group | KYC Administrator |
|
| KYC Analyst Group | KYC Analyst |
|
| KYC Group | KYC Analyst |
|
| KYC Group | KYC Supervisor |
|
| KYC Supervisor Group | KYC Supervisor |
|
User Roles and Activities in KYC
Table 3-4 User Roles for KYC Analyst and Supervisor
| Privileges | KYC Supervisor | KYC Analyst |
|---|---|---|
| Search for Cases | x | x |
| Investigate Cases | x | x |
| Set a case due date | x | x |
| Recommend case closure | x | |
| Perform risk assessments | x | x |
| Promote to case | x | x |
| Perform risk assessments | x | x |
| Approve or reject recommendations to close cases | x | |
| Close cases | x |
User Roles in KYC Administrator
Table 3-5 User Roles in KYC Administrator
| Privileges | KYC Administrator |
|---|---|
| Load watch list data | x |
| Configure pipelines | x |
| Configure threshold sets | x |
| Configure dimension data | x |
| Map jurisdictions to pipelines | x |
| Manage jobs | x |
| Configure master data | x |