6.6 Access and Permissioning Management
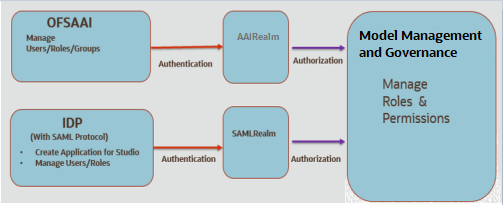
MMG uses a realm based on unique authentication and authorization for its users. Realm indicates the functional grouping of Database Schemas and roles that must be secured for an application. Realms protect data from access through system privileges and do not provide its owner or participants additional privileges. Realm based authorization establishes a set of database accounts and roles that can manage, or access objects protected in realms and are authorized to use its system privileges. It provides a runtime mechanism to check logically if a user's command can access objects specified in the command and proceed with its execution. Realms (AAIRealm, SAMLRealm) are selected based on the Identity Provider (IDP) during the installation. For more information, see the OFS MMG Installation Guide. After you select the realms, you can register a set of schema objects or roles (secured objects) for realm protection and authorize a set of users or roles to access the secured objects. The MMG Application is accessed using the following realms that you have selected during the installation of the MMG Application:
- AAIRealm: This uses Oracle Financial Services Analytical Applications Infrastructure (OFSAAI) Identity Management System for User Authentication. Users, Roles, and Groups are created in the OFSAAI. The OFSAAI facilitates System Administrators to provide access, monitor, and administer users along with the infrastructure metadata operations. The required permissions to roles or groups are authorized in the MMG applications using the Permission feature.
- SAMLRealm: The SAMLRealm uses an identity provider (IDP) Identity Management System for User Authentication. Security Assertion Markup Language (SAML) is an open standard that allows Identity Providers (IDP) to pass authorization credentials to Service Providers (SP). IDP acts as the Single Sign-On (SSO) service. Users and Roles are created in the IDP. The required permissions to Users and Roles are authorized in the MMG Applications using the Permission feature.
Figure 6-2 Authentication and Authorization process in MMG