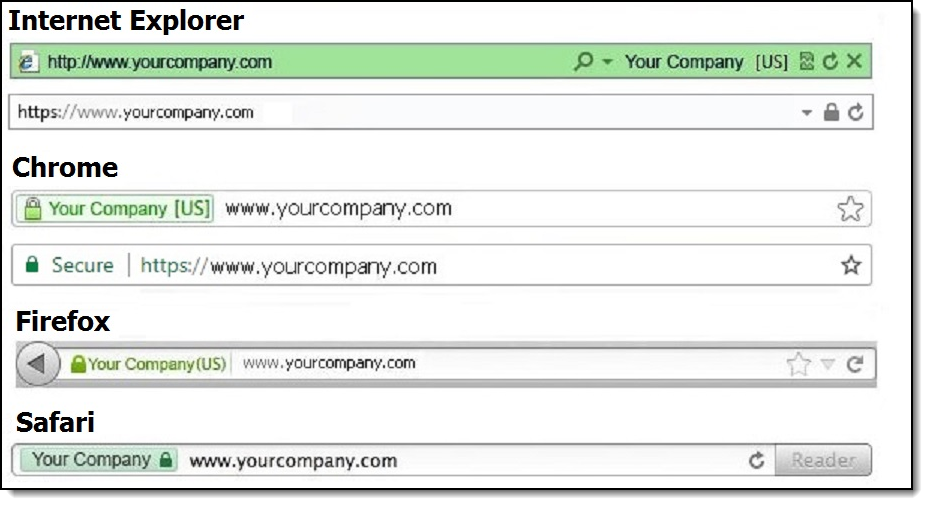
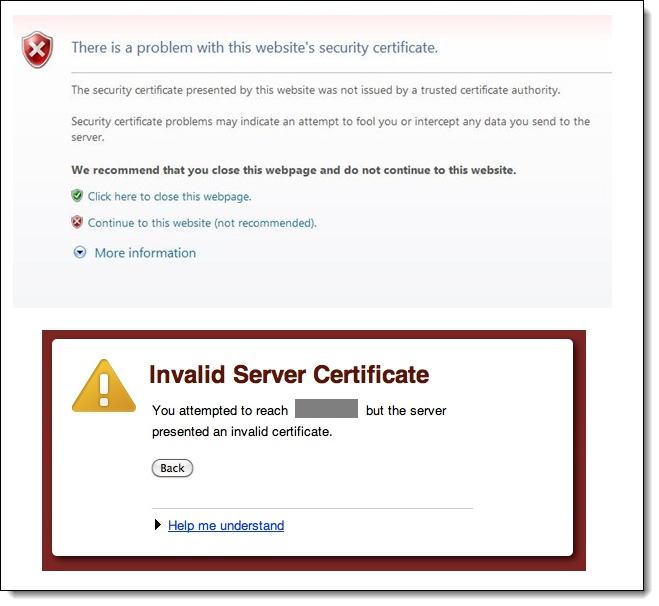
Testing the Enterprise Certificate
CAL authentication relies on establishing a secure (TLS 1.2) connection to the Simphony Enterprise. Each Simphony client being upgraded to release 2.9.1 or later needs to validate the enterprise server certificate and support the TLS 1.2 protocol to establish a secure connection to the Enterprise. The certificate is validated when a connection is established, and in some cases this may require external network access to a certificate authority.
Prior to client upgrade, Oracle recommends that you confirm that the server certificate can be validated on at least one workstation at the property. Skipping this step may cause the upgrade process to fail and requires additional manual steps. To test the enterprise certificate using a web browser:
Parent topic: Enterprise Certificate Verification