- Installation Guide
- Configure SSO using the Oracle Access Manager 11g
- Install SSO on Oracle Access Manager 11g
Install SSO on Oracle Access Manager 11g
- Navigate to the Oracle Access Manager 11g Oracle Access Manager Console URL (http://oam_server:port/oamconsole) and login with the Oracle Access Manager Admin credentials.
- Select the System Configuration Tab.
- Select the Access Manager Settings sub menu in the left navigation window of the browser.
- Double-click the SSO Agents > OAM
Agents option to open the OAM Agents sub
window.
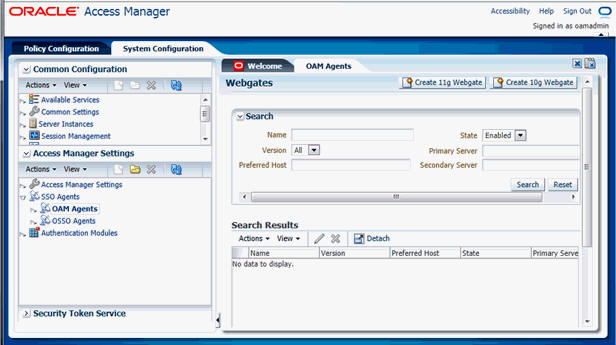
- Click the Create 11g Webgate button and enter the
following details:
- Name: ArgusAnalyticsPolicy
- Security: Open
- Host Identifier: <obiee_server>
- Auto Create Policies: Checked
Note:
The <obiee_server> refers to the server where the Oracle Business Intelligence Enterprise Edition 12c is installed along with Oracle Web Tier and Oracle Webgate.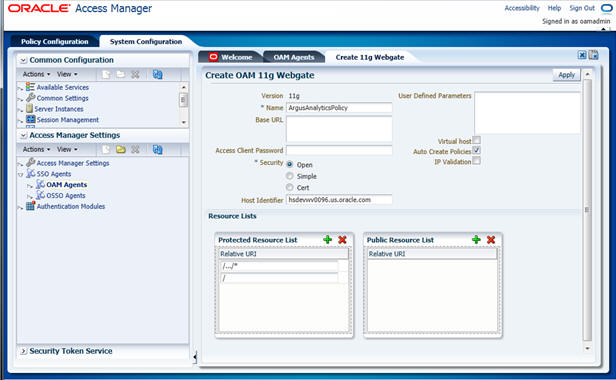
- Click Apply to save and register the 11g Webgate and policies with Oracle Access Manager.
- On the subsequent page, update the details for the ArgusAnalyticsPolicy
created in the above step:
- Cache Pragma Header: Private
- Cache Control Header: Private
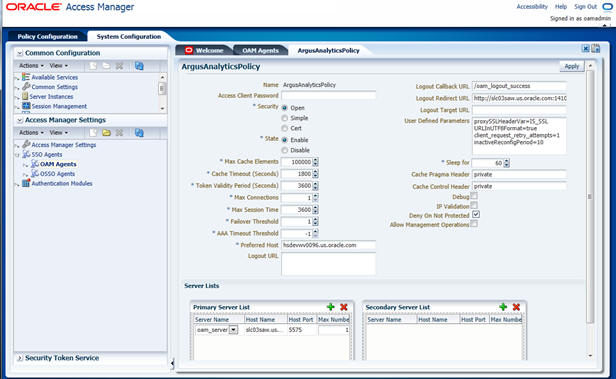
- Click Apply.
- Navigate to the Policy Configuration tab.
- Expand and double-click the Shared Components >
Resource Type > Host
Identifiers > <obiee_server>
(like, hsdevwv0096.oracle.com) to open the Host
Identifiers window and add the following details:
- <obiee_server>
- <obiee_server> <port>
- <obiee_server_ip>
- <obiee_server_ip> <port>
Note:
<obiee_server> refers to the server where the Oracle Business Intelligence Enterprise Edition 12c is installed along with Oracle Web Tier and Oracle Webgate. The port refers to the Oracle Web Tier Port.
Example:
Hostname Port obiee_server.oracle.com
--
obiee_server.oracle.com
7777
<ip address>
--
<ip address>
7777
- Expand and double-click Application Domains > ArgusAnalyticsPolicy > Authentication Policies > Protected Resource Policy.
- Ensure that the Authentication Scheme is set as LDAPScheme.
- Ensure that the following resources are present:
- /
- /…/*
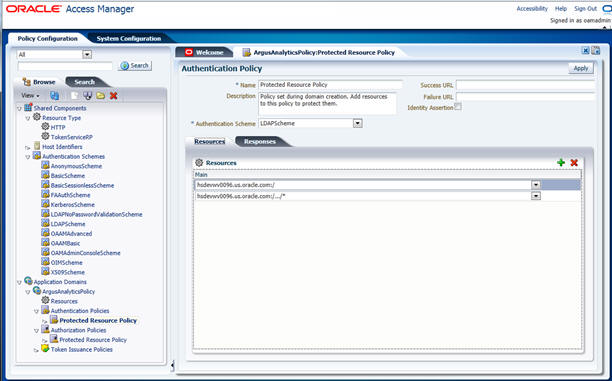
- Add the following Response variables:
- Name: OAM_REMOTE_USER
- Type: Header
- Value: $user.attr.uid [based on the LDAP schema setup]
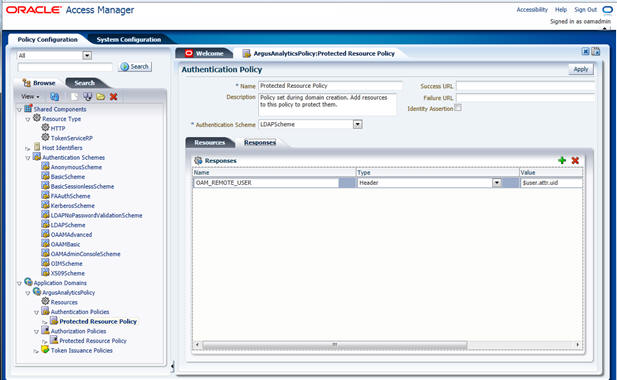
- Click Apply and save the changes.
- Expand and double-click Application Domains > ArgusAnalyticsPolicy > Authorization Policies > Protected Resource Policy
- Ensure that the following resources are present:
-
/
-
/…/*
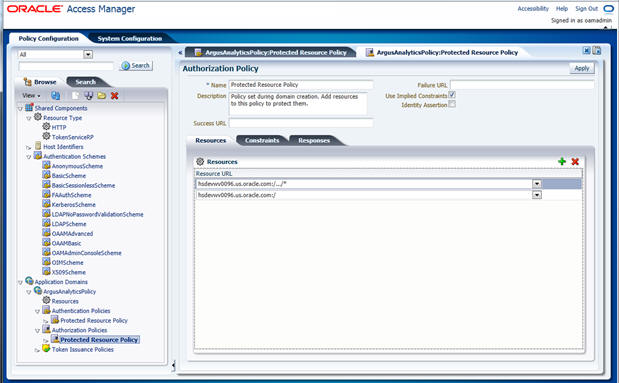
-
- Add the following Response variables:
- Name: OAM_REMOTE_USER
- Type: Header
- Value: $user.attr.uid [as based on the LDAP schema setup]
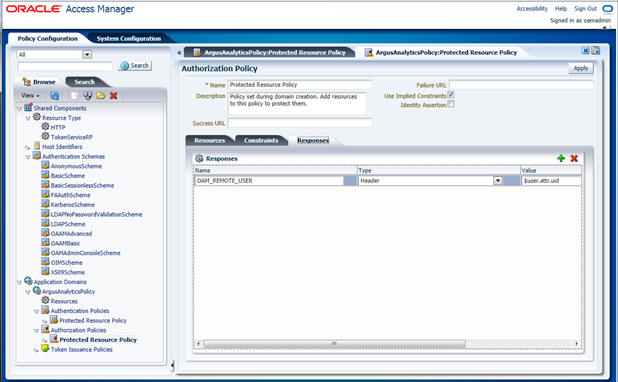
- Click Apply to save the changes
- Navigate to the OPVA Web Tier Machine [<obiee_server>], which is the machine where you have installed the OPVA Oracle Business Intelligence Enterprise Edition Server, and run the installer for Webgate (OFM Webgate 11g for Oracle Access Manager 11g) to complete the installation.
- Configure the 11g Webgate using the following steps to communicate with the Oracle Access Manager 11g server:
Note:
Refer to the following link for advanced details:
http://docs.oracle.com/cd/E21764_01/install.1111/e12002/webgate.htm
- Move to the following directory under your Oracle Home for Webgate:
On UNIX Operating Systems:
<Webgate_Home>/webgate/ohs/tools/deployWebGateOn Windows Operating Systems:
Webgate_Home>\webgate\ohs\tools\deployWebGate - On the command line, run the following command to copy the required
bits of agent from the Webgate_Home directory to
the Webgate Instance location:
On UNIX Operating Systems:
./deployWebgateInstance.sh -w <Webgate_Instance_Directory> -oh <Webgate_Oracle_Home>On Windows Operating Systems:
deployWebgateInstance.bat -w <Webgate_Instance_Directory> -oh <Webgate_Oracle_Home>Where <Webgate_Oracle_Home> is the directory where you have installed Oracle HTTP Server Webgate and created as the Oracle Home for Webgate, as shown in the following example:
MW_HOME>/Oracle_OAMWebGate1
The <Webgate_Instance_Directory> is the location of Webgate Instance Home, which is the same as the Instance Home of Oracle HTTP Server, as shown in the following example:
<MW_HOME>/Oracle_WT1/instances/instance2/config/OHS/ohs1
- Run the following command to ensure that the
LD_LIBRARY_PATH variable contains
<Oracle_Home_for_Oracle_HTTP_Server>/lib:
On UNIX (depending on the shell):
export LD_LIBRARY_PATH=$LD_LIBRARY_PATH:
<Oracle_Home_for_Oracle_HTTP_Server>/libOn Windows:
Set the
<Webgate_Installation_Directory>\webgate\ohs\liblocation and the<Oracle_Home_for_Oracle_HTTP_Server>\binlocation in the PATH environment variable. Add a semicolon (;) followed by this path at the end of the entry for the PATH environment variable. - From your present working directory, move up one directory level:
On UNIX Operating Systems, move to:
<Webgate_Home>/webgate/ohs/tools/setup/InstallToolsOn Windows Operating Systems, move to:
<Webgate_Home>\webgate\ohs\tools\EditHttpConf - On the command line, run the following command to copy the
apache_webgate.template from the
Webgate_Home directory to the Webgate
Instance location (renamed to webgate.conf) and update the
httpd.conf file to add one line to include
the name of webgate.conf:
On UNIX operating systems:
./EditHttpConf -w <Webgate_Instance_Directory> -oh <Webgate_Oracle_Home> -o <output_file>On Windows operating systems:
EditHttpConf.exe -w <Webgate_Instance_Directory> -oh <Webgate_Oracle_Home> -o <output_file>Where <Webgate_Oracle_Home> is the directory where you have installed Oracle HTTP Server Webgate for Oracle Access Manager and created as the Oracle Home for Webgate, as shown in the following example:
<MW_HOME>/Oracle_OAMWebGate1
The <Webgate_Instance_Directory> is the location of Webgate Instance Home, which is the same as the Instance Home of Oracle HTTP Server, as shown in the following example:
<MW_HOME>/Oracle_WT1/instances/instance2/config/OHS/ohs1
The <output_file> is the name of the temporary output file used by the tool, as shown in the following example:
Edithttpconf.log
- Copy Generated Files (Artifacts) to the Webgate Instance Location from
the Oracle Access Manager 11g server.
The 11g Webgate Agent (ArgusAnalyticsPolicy), which was created in the Oracle Access Manager 11g Oracle Access Manager Console earlier, would have also created the following artifacts on the Oracle Access Manager 11g server:
cwallet.sso
ObAccessClient.xml
This is based on the Security Mode that you have configured, which in this case is Open.
On the Oracle Access Manager 11g server, these files are present at the following location:
<OAM_FMW_HOME>/user_projects/domains/<OAM_domain>/output/ArgusAnalyticsPolicyCopy these files to the <obiee_server> in the following directory:
<Webgate_Instance_Directory>/webgate/configdirectory[Example:<MW_HOME>/Oracle_WT1/instances/instance2/config/OHS/ohs1/webgate/config]
- Restart the Oracle HTTP Server Instance.
To stop the Oracle HTTP Server instance, run the following commands on the command line:
<MW_HOME>/Oracle_WT1/instances/instance2/bin/opmnctl stopall
To restart the Oracle HTTP Server instance, run the following commands on the command line:
<MW_HOME>/Oracle_WT1/instances/instance2/bin/opmnctl startall
- Move to the following directory under your Oracle Home for Webgate:
- Configure the HTTP Server as a reverse proxy for the WebLogic Server. To
execute this, modify the mod_wl_ohs.conf file present at the following
location:
OracleWebTierHome\instances\instance2\config\OHS\ohs1The following is a template to configure mod_weblogic:
LoadModule weblogic_module "${ORACLE_HOME}/ohs/modules/mod_wl_ohs.so"
# This empty block is needed to save mod_wl related configuration from EM to this file when changes are made at the Base Virtual Host Level
<IfModule weblogic_module>
# WebLogicHost <WEBLOGIC_HOST>
# WebLogicPort <WEBLOGIC_PORT>
# Debug ON
# WLLogFile /tmp/weblogic.log
# MatchExpression *.jsp
<Location /console>
SetHandler weblogic-handler
WebLogicHost hsdevwv0096.oracle.com
WeblogicPort 7001
WLProxySSL ON
WLProxySSLPassThrough ON
</Location>
<Location /em>
SetHandler weblogic-handler
WebLogicHost hsdevwv0096.oracle.com
WeblogicPort 7001
WLProxySSL ON
WLProxySSLPassThrough ON
</Location>
<Location /analytics>
SetHandler weblogic-handler
WebLogicHost hsdevwv0096.oracle.com
WeblogicPort 9704
WLProxySSL ON
WLProxySSLPassThrough ON
</Location>
<Location /analyticsRes>
SetHandler weblogic-handler
WebLogicHost hsdevwv0096.oracle.com
WeblogicPort 9704
WLProxySSL ON
WLProxySSLPassThrough ON
</Location>
<Location /xmlpserver>
SetHandler weblogic-handler
WebLogicHost hsdevwv0096.oracle.com
WeblogicPort 9704
WLProxySSL ON
WLProxySSLPassThrough ON
</Location>
</IfModule>
# <Location /weblogic>
# SetHandler weblogic-handler
# PathTrim /weblogic
# ErrorPage http:/WEBLOGIC_HOME:WEBLOGIC_PORT/
# </Location>
Restart the Web Tier Instance in WebLogic EM or as described above.
- Configure a new Authenticator for Oracle WebLogic Server on the Oracle Business Intelligence Enterprise
Edition Server using the following steps:
- Login to the WebLogic Server Administrator Console and navigate to Security Realms> myrealm.
- Click the Providers tab.
- Click Lock & Edit on the right corner of the webpage, highlighted as Change Center.
- Click New to create a new Authentication
Provider and add the following details:
Name: OPVAOIDAuthenticator, or a name of your choice
Type: OracleInternetDirectoryAuthenticator
- After saving the details, click the new Authenticator that you have
created and enter the following details:
In the sub tab change the Control Flag as SUFFICIENT
- Click Save.
- Click the Provider Specific tab and enter the
following required settings using values for your environment:
-
Host: Your LDAP host.
For example: oid_server.oracle.com
-
Port: Your LDAP host listening port.
For example: 3060
-
Principal: LDAP administrative user.
For example: cn=orcladmin,cn=Users,dc=us,dc=oracle,dc=com
-
Credential: LDAP administrative user password
-
User Base DN: Same searchbase as in Oracle Access Manager.
For example: cn=Users,dc=us,dc=oracle,dc=com
-
All Users Filter:
For example: (&(uid=*) (objectclass=person))
-
User Name Attribute: Set as the default attribute for username in the directory server.
For example: uid
-
Group Base DN: The group searchbase
For example: cn=Groups,dc=us,dc=oracle,dc=com
- Leave the other defaults as is.
-
GUID Attribute: The GUID attribute defined in the OID LDAP Server
For example: uid
- Click Save.
-
- Configure a new Identity Asserter for WebLogic Server using the following
steps:
- In the Oracle WebLogic Server Administration Console, select Security Realms from the left pane and click the realm which you want to configure. For example, myrealm. Select Providers.
- Click New and enter the following values in the
fields:
Name: OPVAOAMIdentityAsserter, or a name of your choice
Type: OAMIdentityAsserter
- Click OK.
- Click on the newly created Asserter and set the Control Flag to REQUIRED.
- Ensure that the Active Types that you have selected is OAM_REMOTE_USER.
- Click Save.
- Navigate to the Provider Specific tab and enter
the following details:
-
Transport Security: open
-
Application Domain: ArgusAnalyticsPolicy, as set in the Oracle Access Manager 11g Console
-
Access Gate Name: ArgusAnalyticsPolicy, as specified in the Oracle Access Manager 11g Console
-
Primary Access Server: oam_server.oracle.com:5575, Oracle Access Manager 11g server with port
-
Click Save.
-
- In the Providers tab, perform the following
steps to reorder Providers:
- Click Reorder.
-
On the Reorder Authentication Providers page, select a Provider Name and use the arrows besides the list to order the following providers:
OPVAOAMIdentityAsserter
OPVAOIDAuthenticator
DefaultAuthenticator
DefaultIdentityAsserter
- Click OK to save your changes.
- In the Providers tab, click Default Authenticator and change the Control Flag to Sufficient.
- In the Change Center, click Activate Changes.
- Restart Oracle WebLogic Server
- The BISystemUser present in the default embedded LDAP
must be deleted (using Security Realms in the Administration
Console Link of the WebLogic Server) and the same/another user
must be added in the newly added OID. This user also needs to be added to the
Oracle Business Intelligence Application Roles using the following steps:
- Navigate to Administration Console > Security Realms > myrealm > Users and Groups > Users and select the checkbox against BISystemUser (from Provider: Default Authenticator)
- Click Delete.
- Navigate to Security Realms > myrealm > Roles and Policies > Realm Roles.
- In the tree structure, expand Global Roles node and select the Roles link.
- In the subsequent screen, click the Admin Role link.
- Click the Add Conditions button.
- In the next screen, select the Predicate List as User and click Next.
- In the User Argument Name, enter BISystemUser and click ADD.
- Click Finish.
- In the Role Conditions screen, ensure that the set operator is set to Or.
- Save the configuration.
- Navigate to the Oracle Enterprise Manager of Oracle Business Intelligence Enterprise Edition or the Oracle Fusion Middleware Control page and navigate in the tree structure to the Business Intelligence > coreapplication node.
- In the Oracle Business Intelligence drop-down menu, select Security > Application Roles.
- In the Roles displayed, select BISystem and in the next screen remove the old BISystemUser (from the Default Provider) and add the newly created BISystemUser user in OID.
- Add the trusted user's credentials to the oracle.bi.system credential map.
- Using Oracle Fusion Middleware Control target navigation pane, navigate to
farm > WebLogic
Domain, and select
bifoundation_domain.
- Using the WebLogic Domain menu, select Security > Credentials.
- Open the oracle.bi.system credential map, and select system.user.
- Click Edit.
- In the Edit Key dialog box, enter BISystemUser (or the name that you have selected) in the User Name field.
- In the Password field, enter the trusted user's password that is contained in Oracle Internet Directory.
- Click OK.
- Restart the Managed Servers.
- Enable the SSO Authentication in the Weblogic Server for Oracle Business Intelligence Enterprise
Edition using the following steps:
- Login to Oracle Fusion Middleware Control (EM) of the WebLogic Server.
- Go to theBusiness Intelligence Overview page.
- Go to the Security page.
- Click Lock and Edit Configuration.
- Check Enable SSO, this makes the SSO provider list active.
- Select the configured SSO provider from the list, as Oracle Access Manager.
- In The SSO Provider Logoff URL, specify the following URL: http://<oam_server>:14100/oam/server/logout
- Click Apply.
- Click Activate Changes.
- Restart the Oracle Business Intelligence components using Oracle Fusion Middleware Control.
Parent topic: Configure SSO using the Oracle Access Manager 11g