Rule sandbox details
All user-defined function DLLs executed by the Oracle Central Designer rule engine run in a sandbox. The rule sandbox is a .NET AppDomain. You can think of it as a light-weight process inside the OS process.
The rule sandbox has the minimum set of permissions possible. This means the permission to execute code (SecurityPermissionFlag.Execution), which is the maximum restriction possible in .NET.
There are two types of user-defined function assemblies:
- Trusted—When loaded into the sandbox, code in trusted assemblies executes as safe-critical code or as security-critical, and can elevate permissions to perform extra operations, such as DB access.
- Untrusted—Untrusted user-defined function assemblies have the same permissions as a rule: only basic operations, which are not outlined in the Rules Reference Guide as requiring special permission. Untrusted code or transparent code can access only safe-critical code in assemblies marked with the attribute AllowPartiallyTrustedCallers.
The following diagram shows the relationship between the sandbox and the main application (Oracle Health Sciences InForm or Oracle Central Designer), and the assembly structure inside the sandbox.
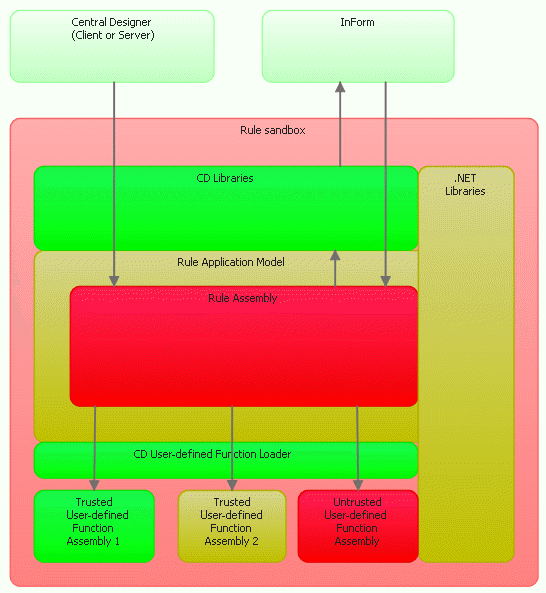
Color codes:
- Green—Good, trusted code that does not allow partially trusted callers (security-critical).
- Yellow—Trusted code that can be called by untrusted code (security safe-critical).
- Red—Untrusted code (transparent code).
The two light-green boxes on top represent AppDomains for the main application: Oracle Central Designer or Oracle Health Sciences InForm. These domains run in full trust. AppDomain technology isolates them from the sandbox. Communication between AppDomains (represented by arrows on the diagrams) is done with remoting calls (inter-process communication or RPCs).
If you follow a call from the Oracle Central Designer box to invoke the rule from the rule assembly:
- The call is first created in the sandbox.
- The call loads Oracle Central Designer libraries inside the sandbox and uses a proxy to invoke the method from Oracle Central Designer libraries (calls a green code).
- The Oracle Central Designer libraries load the rule assembly (red code) and invoke the method from the rule assembly.
- The rule assembly can make calls through the Rule Application Model into Oracle Central Designer libraries (arrow going up).
- The rule assembly can make calls through the Rule Application Model into user-defined functions (arrows going down).
Note:
The code executed when any of these calls are made is restricted to the set of sandbox permissions. It does not matter if it is trusted or untrusted code, unless trusted code chooses to temporarily elevate the permissions. .NET does not propagate elevated permissions to untrusted code.For more information, see: