Authenticate with ADW Using Resource Principal Authentication (Recommended)
Resource Principal Authentication lets your notebook use other OCI services securely without explicit credentials.
Resource Principal Authentication is a secure authentication method offered by Oracle Cloud Infrastructure (OCI) that allows cloud-native resources (like OCI Data Science notebooks, functions, or OCI-based virtual machines and containers) to interact with other OCI services (for example, Vault, Object Storage, Database) without explicitly managing user credentials or API keys in your code.
When you run code in a Data Science notebook, OCI manages a special identity (resource principal) for the session. Identity and Access Management (IAM) policies assigned to the project or notebook session govern the identity, permitting or restricting which OCI resources it can access. See Resource Princpal to access OCI Resources for more information.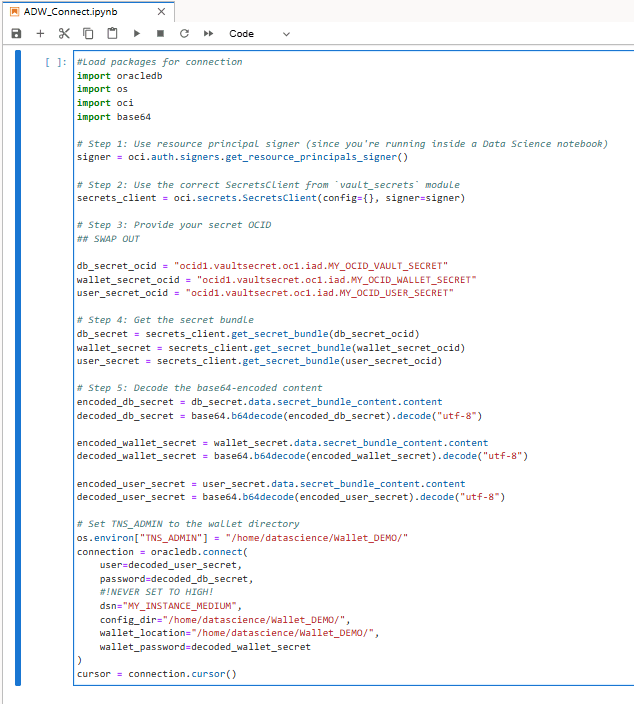
#Load packages for connection
import oracledb
import os
import oci
import base64
# Step 1: Use resource principal signer (since you're running inside a Data Science notebook)
signer = oci.auth.signers.get_resource_principals_signer()
# Step 2: Use the correct SecretsClient from `vault_secrets` module
secrets_client = oci.secrets.SecretsClient(config={}, signer=signer)
# Step 3: Provide your secret OCID
## SWAP OUT
db_secret_ocid = "ocid1.vaultsecret.oc1.iad.MY_OCID_VAULT_SECRET"
wallet_secret_ocid = "ocid1.vaultsecret.oc1.iad.MY_OCID_WALLET_SECRET"
user_secret_ocid = "ocid1.vaultsecret.oc1.iad.MY_OCID_USER_SECRET"
# Step 4: Get the secret bundle
db_secret = secrets_client.get_secret_bundle(db_secret_ocid)
wallet_secret = secrets_client.get_secret_bundle(wallet_secret_ocid)
user_secret = secrets_client.get_secret_bundle(user_secret_ocid)
# Step 5: Decode the base64-encoded content
encoded_db_secret = db_secret.data.secret_bundle_content.content
decoded_db_secret = base64.b64decode(encoded_db_secret).decode("utf-8")
encoded_wallet_secret = wallet_secret.data.secret_bundle_content.content
decoded_wallet_secret = base64.b64decode(encoded_wallet_secret).decode("utf-8")
encoded_user_secret = user_secret.data.secret_bundle_content.content
decoded_user_secret = base64.b64decode(encoded_user_secret).decode("utf-8")
# Set TNS_ADMIN to the wallet directory
os.environ["TNS_ADMIN"] = "/home/datascience/Wallet_DEMO/"
connection = oracledb.connect(
user=decoded_user_secret,
password=decoded_db_secret,
#!NEVER SET TO HIGH!
dsn="MY_INSTANCE_MEDIUM",
config_dir="/home/datascience/Wallet_DEMO/",
wallet_location="/home/datascience/Wallet_DEMO/",
wallet_password=decoded_wallet_secret
)
cursor = connection.cursor()You can share the code, but other users cannot access your secrets just by having the secret OCIDs. Even if someone knows your db_secret_ocid, they must be running a resource (like a notebook session) with IAM permissions to both access OCI Vault to retrieve that specific secret. Never share secret OCIDs unless absolutely necessary, and always use OCI Vault and IAM to tightly control which identities and resources can access sensitive secrets.
Parent topic: Connect to Oracle Health Real-World Data from Notebooks