4. Configure Provisioning and User Attribute Mappings in the Identity Provider (Okta)
Connect the Okta app to the OCI IAM confidential app using the domain URL and secret token from an earlier step.
- In the newly created application page, click the Sign On tab.
- Click Edit next to Settings.
- Scroll down to Advanced Sign-on Settings and enter the Identity Domain ID under the Oracle Cloud Infrastructure IAM GUID.
- Click Save.
- Near the top of the page, click the Provisioning tab.
- Click Configure API Integration.
- Select Enable API Integration.
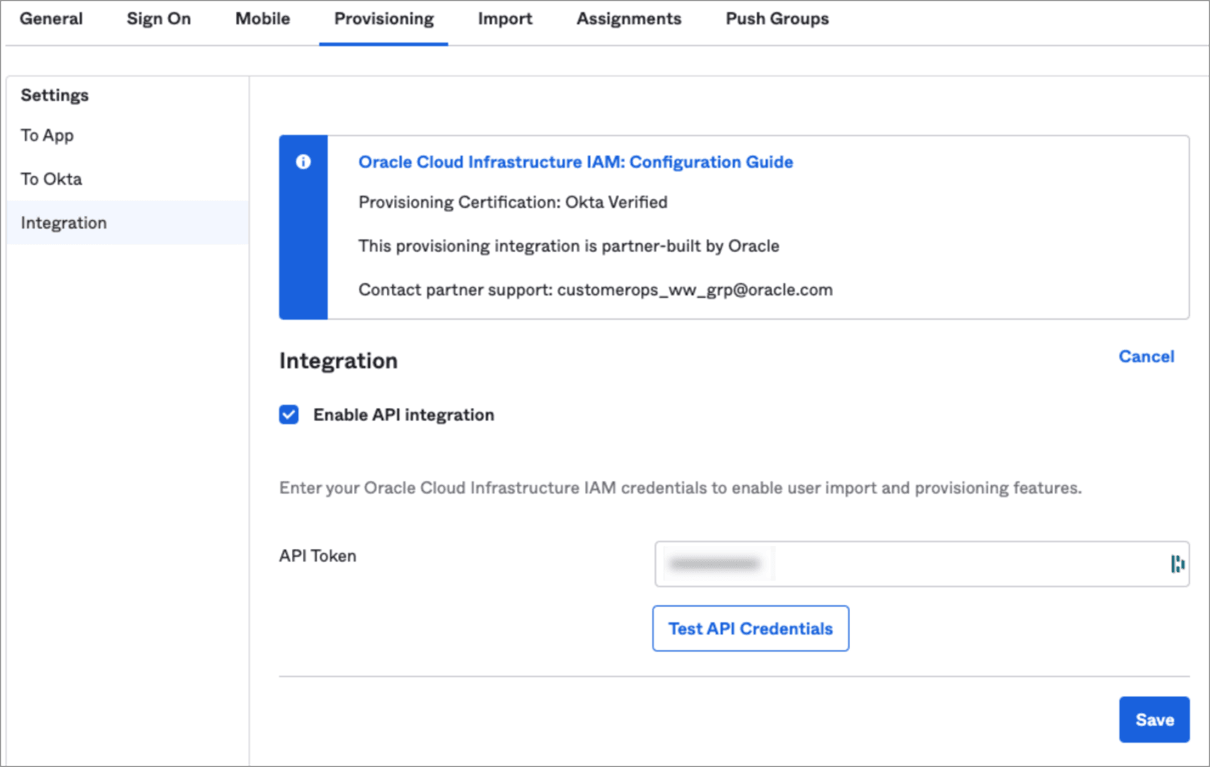
- Enter the secret token value you copied earlier in API Token.
- Click Test API Credentials.
If you get an error message, check the values that you have entered and try again.
Okta has successfully connected to the OCI IAM SCIM endpoint when you get the ‘Oracle Cloud Infrastructure IAM was verified successfully!’ message.
- Click Save.
The Provisioning to App page opens, where you can create users, update user attributes, and map attributes between OCI IAM and Okta.
- Under Setting list, Provisioning to App screen, Click Edit.
- Enable Create Users, Update User Attributes & Deactivate Users. Click Save.
- Scroll down to the Attribute Mappings section.
- Click Go to Profile Editor. The Attribute section lists the OCI IAM
Attributes.
Refer to the User Mapping table below to map user attributes between OCI IAM and Okta, adding any required attributes including the mandatory attributes.
- Under Attributes, click Add Attribute.
- Refer to the Table 2-1 User Mapping and add all the mandatory attributes one by one. Some
attributes may have already been created by default, so you do not
need to add them.
To Add an attribute, enter the following details on the Add Attribute window:
- Data Type: Add the value from the Mapping Type column from the User Mapping Table.
- Display Name: Add the value from the IAM Domain (IDCS) User Attribute column from the User Mapping Table.
- Variable Name: Add the value from the IAM Domain (IDCS) User Attribute column from the User Mapping Table.
- External Name: Automatically populated by the value of the variable name.
- External Namespace: Add the value from the External Namespace column from the User Mapping Table. If there is no value in the column, leave it blank.
- Attribute Type: Select Personal.
Click Save and add another. Repeat this process until all the mandatory attributes have been added.
Table 2-1 User Mapping
Okta Attribute IAM Domain (IDCS) User Attribute External Namespace Mapping Type Attribute Value Description Mandatory Attribute login
userName
Direct
Map from Okta profile
User name
Yes
lastName
name.familyName
Direct
Map from Okta profile
Last name
Yes
email
emails[type eq "work"].value
Direct
Map from Okta profile
Email address
Yes
(user.email != null && user.email != '') ? 'work' : ''
emailType
Expression
(user.email != null && user.email != '') ? 'work' : ''
Email Type
Yes
extensionAttributePrimaryWorkLocation
OC_PrimaryWorkLocation
urn:ietf:params:scim:schemas:idcs:extension:custom:User
Expression
Same value for all Users. Refer description
Mandatory Single Valued User Attribute. Indicates the User primary work location. Primary Work Location can have values <CHAINCODE>:C for multi chain customers derived from the User profile. For customers having only a single chain, the source value can be set to constant <CHAINCODE>:C for all users.
Yes
isFederatedUser
isFederatedUser
urn:ietf:params:scim:schemas:oracle:idcs:extension:user:User
Expression
true
Enable Federated User flag in Identity Domain.
Yes
bypassNotification
bypassNotification
urn:ietf:params:scim:schemas:oracle:idcs:extension:user:User
Expression
true
The bypass notification flag controls whether an email notification is sent after creating or updating a user account in Identity Domain. The bypassNotification must be set to "true" for Federated users. This disables user account activation notification in IAM Identity Domain for the user.
Yes
firstName
name.givenName
Direct
Map from Okta profile
First name
No
preferredLanguage
preferredLanguage
Direct
Map from Okta profile
The User's preferred written or spoken language for localized user interfaces.
No
displayName
displayName
Direct
Map from Okta profile
Display name
No
title
title
Direct
Map from Okta profile
Title
No
mobilePhone
phoneNumbers[type eq "mobile"].value
Direct
Map from Okta profile
The User's mobile phone number.
No
employeeNumber
OC_UserEmployeeNo
urn:ietf:params:scim:schemas:idcs:extension:custom:User
Direct
Map from Okta profile
Numeric or alphanumeric identifier assigned to a person, typically based on order of hire or association with an organization.
No
userType
OC_UserType
urn:ietf:params:scim:schemas:idcs:extension:custom:User
Direct
Map from Okta profile
Possible Values:
-
FULL-TIME EMPLOYEE
-
PART-TIME EMPLOYEE
-
TRAINEE
-
CONTRACTOR
-
CONSULTANT
-
OTHER
Used to identify the organization-to-user relationship.
No
department
OC_Department
urn:ietf:params:scim:schemas:idcs:extension:custom:User
Direct
Map from Okta profile
Specifies the User's department.
No
primaryPhone
phoneNumbers[type eq "work"].value
Direct
Map from Okta profile
The User's work phone number.
No
extensionAttributeUserOwnerCode
OC_UserOwnerCode
urn:ietf:params:scim:schemas:idcs:extension:custom:User
Direct
Map from Okta profile
Unique code (typically, the sales manager's initials) for the owner. For example, oc_ownercode=First_Last_Initial.
No
extensionAttributeHonorificPrefix
name.honorificPrefix
Direct
Map from Okta profile
User Initials
No
extensionAttributeMiddleName
name.middleName
Direct
Map from Okta profile
User Middle name
No
extensionAttributeHonorificSuffix
name.honorificSuffix
Direct
Map from Okta profile
Suffix
No
extensionAttributeTimezone
timezone
Direct
Map from Okta profile
User's timezone
No
extensionAttributeLocale
locale
Direct
Map from Okta profile
Used to indicate the User's default location for purposes of localizing items such as currency, date and time format, numerical representations, and so on.
No
extensionAttributeActAs
oc_actas
urn:ietf:params:scim:schemas:idcs:extension:custom:User:OC_ActAs
Direct
Map from Okta profile
Possible Values:
-
Reservation Sales Person
-
Conference Sales Person
-
External System
OPERA Cloud attribute. Determines the Originating Application value in Blocks and Manage Block (see Managing Blocks) referenced by the Origin list field in Group Rooms Control (see Using Group Rooms Control) search and in reports.
No
extensionAttributeActAt
oc_actat
urn:ietf:params:scim:schemas:idcs:extension:custom:User:OC_ActAt
Direct
Map from Okta profile
Possible Values:
-
Property
-
Central
OPERA Cloud attribute. Determines the Originating Application value in Blocks and Manage Block (see Managing Blocks) referenced by the Origin list field in Group Rooms Control (see Using Group Rooms Control) search and in reports.
No
extensionAttributeHubs
String array
urn:ietf:params:scim:schemas:idcs:extension:custom:User:OC_Hubs
Direct
N/A
Assign one or more hubs to a user to determine their property location access in multi-property operations. oc_hubs is a String array in IAM Domain and the Identity Provider should should map a multi valued attribute to oc_hubs. Value for oc_hubs needs to be sent in all uppercase.
No
extensionAttributeHubsString
String
urn:ietf:params:scim:schemas:idcs:extension:custom:User:OC_Hubs_String
Direct
N/A
Assign one or more hubs to a users to determine their property location access in multi-property operations. OC_Hubs_String needs to be sent in all uppercase as comma separated values.
No
- Once all the mandatory attributes have been created, click Mapping. Click the tab Okta User to Oracle Cloud Infrastructure.
- Refer to the Attribute Value column in the Table 2-1 User Mapping and update the values for all the mandatory attributes.
- Save the mappings and return to the Application in Okta.
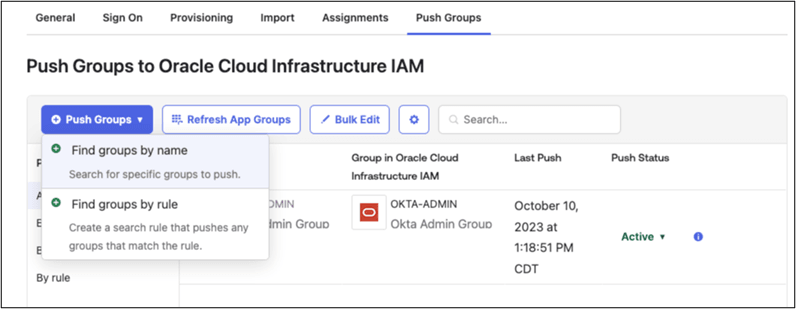
- Syncing Groups from Okta to Oracle Identity Domain can be done manually or can be automated by selecting the Push Group tab to define a rule. Select the Push Group tab and click Push Group.
- Click Find groups by name and enter the group name to push from Okta to
OCI IAM Domain. Click Save.
You can also define a rule to automate Group synchronization.
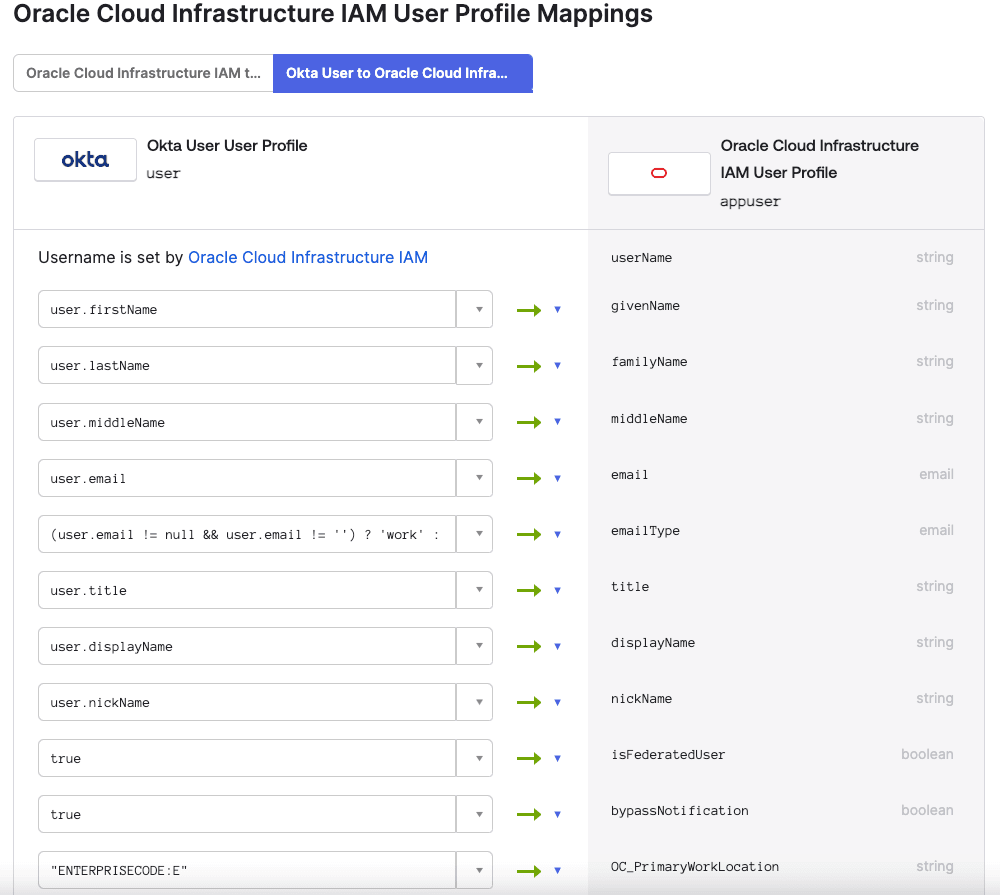
- Save mappings.
- Return to the OIC Application.
- Syncing Groups from Okta to Oracle Identity Domain can be done manually or can be automated by selecting the Push Group tab under the OCI IAM application to define a rule.
- Select the Push Group tab.
You can manually push the group by entering the group name and selecting the group to be pushed.
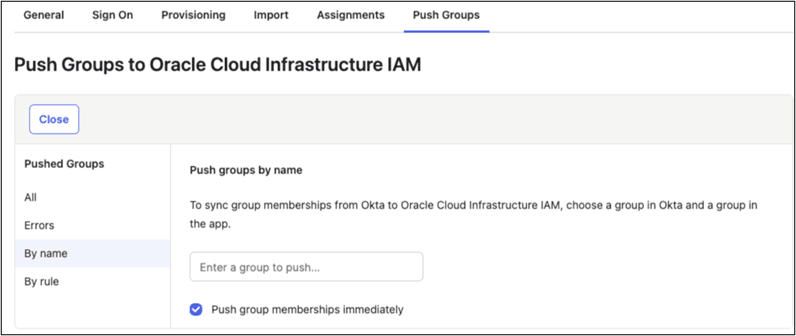
- Enter the group name to push from Okta to OCI IAM Domain.
- You can also define a rule to automate Group synchronization.