14 Inadvertent Capture of PAN
This appendix explains how to address the inadvertent capture of PAN on a Linux system.
Clear Swap Space on Your System
Perform the following commands:
-
Run
free(to review swap usage). The following information appears: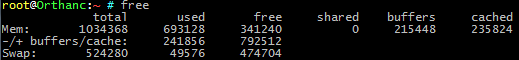
-
Run
swapoff -a(requires elevated privs). -
Run
swapon -a(requires elevated privs). -
Run
free(should show that swap has been cleaned out). The following figure shows an example: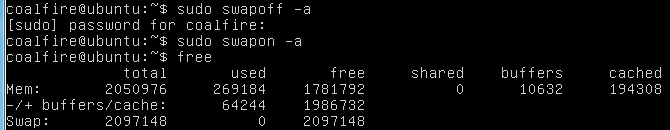
You can disable the swap space as described in the following section.
Disable Swap Space
Disable swap space can be risky to the operation of your system. With no swap space, the Linux or Unix operating system will automatically kill processes if the amount of physical RAM needed for all running processes is exceeded:
Comment out the swap entry in /etc/fstab.
Encrypt the Swap Space on Your System
This section explains encrypting swap through the use of dm-crypt. This requires you to run a 2.6 kernel. For example, the swap partition will be /dev/VolGroup00/LogVol01. This is the default swap partition for RedHat systems. The swap partition does not need to be part of an Logical Volume Manager (LVM). As noted previously, dm-crypt can encrypt disk partitions (/dev/hda2) or whole disks (/dev/hda). Be sure to change the commands to fit your swap partition accordingly.)
When encrypting your swap partition, you will need to temporarily turn off swap. This means you need to shut all unnecessary applications to free up memory. If this memory is not freed, you will be unable to turn off the swap space. The best way to handle this is to boot the system into single user mode. This shuts down most services with the exception of a single root shell. To boot the system into single user mode, run the following command:
# /sbin/telinit
s
Turn off the swap space by running the following command:
# swapoff -a
To ensure a completely clean and sterile swap space, overwrite the swap partition with random data. This will help prevent the recovery of any data written to swap before the encryption process. The shred command overwrites the specified file or device with random data:
# shred -v /dev/VolGroup00/LogVol01
Create a file named /etc/crypttab. The main page for crypttab covers the particulars of crypttab. The below example
-
Creates an encrypted block device named swap at /dev/mapper (first field).
-
Specifies /dev/VolGroup00/LogVol01 as the underlying block device (second field).
-
Specifies /dev/random as the encryption password (third field).
-
Specifies the encrypted device as a swap device with an encryption cypher with AES encryption and unpredictable IV values (fourth field).
swap /dev/VolGroup00/LogVol01 /dev/random swap,cipher=aes-cbc-essiv:sha256
Edit /etc/fstab to point to the encrypted block device, /dev/mapper/swap as opposed to /dev/VolGroup00/LogVol01. The file should look like the following example:
/dev/VolGroup00/LogVol01 swap swap defaults 0 0
Change the file to look like this:
/dev/mapper/swap swap swap defaults 0 0
Reboot your system to create the encrypted swap space with the following command:
# reboot -n
If you do not want to reboot, you can create the encrypted swap partition with the following commands:
# cryptsetup -d /dev/random create swap /dev/VolGroup00/LogVol01 (the -d part of the command specifies cryptsetup
to use /dev/random as the key file and the create part of the command creates a mapping with the name, swap backed
by the device, /dev/VolGroup00/LogVol01)
# mkswap /dev/mapper/swap
# swapon -a