Additional Source for Data Security
Some applications, such as RI and LPO, use data security configurations to limit what users see in the user interface.
These tables are normally populated from MFCS or from a set of flat files such as RAF_SEC_USER.dat, as defined
in the RAP interfaces guide. If you want to use Innovation Workbench to populate these tables, however, you must leverage
an alternate data flow and batch program. The steps to maintain this data from IW are:
-
Create programs or REST APIs that insert data into the following staging tables from IW:
RAF_FILTER_GROUP_MERCH_STG RAF_FILTER_GROUP_ORG_STG RAF_SEC_USER_STG RAF_SEC_GROUP_STG RAF_SEC_USER_GROUP_STG -
From POM, enable and run the adhoc process
RAF_SEC_FILTER_LOAD_ADHOCin the AIF DATA schedule, which contains just one job namedRAF_SEC_FILTER_LOAD_JOB. This job truncates the target data warehouse tables (likeRAF_SEC_USER), then insert the contents from the staging table to the target table. -
If you are moving the data downstream to LPO or other AIF applications, run the associated data security load jobs for those applications.
The relationship between the internal RAF tables is shown in the diagram below.
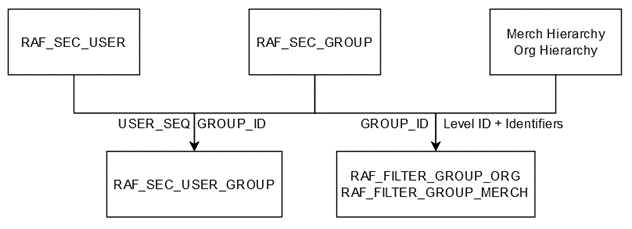
Note:
The same set ofRAF_* tables exist in multiple database schemas, so you must be careful when querying
and loading them. When you want to query the tables populated by the AIF DATA job, you must specify RADM01 as the owner of the table (such as select * from RADM01.RAF_SEC_USER). When you want to query the tables
owned by AIF APPS, you must specify RASE01 as the owner.