Create OAuth2 Client Application in IDCS
Use Retail Home for creating the client app in IDCS. Once app is created you will get cli-ent id and client secret both of them necessary to get access token. Follow the instructions below for generating the access token and making service call using OAuth2 token.
-
Login into retail home as retail home administrator.
-
In retail home screen click on Settings menu icon on the left and then click on Application Administration.
-
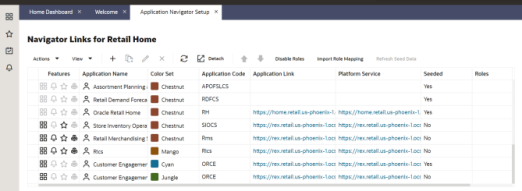
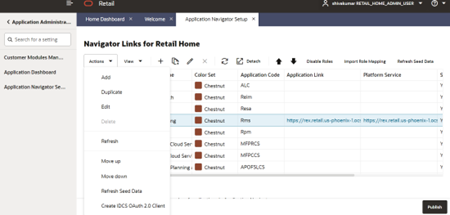
On the Application Administration menu click on Application Navigator Setup. Notice all the hosted applications are listed here with their application and platform service url.
Settings -> Application Administration->Application Navigator Settings
-
Look for application with name RICS. If you are not seeing RICS, application try refreshing seed. Steps
-
Select the row with the application code as Rms.
-
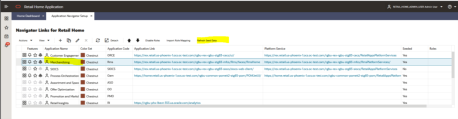
Click the Refresh Seed Data button on top right corner of the menu.
-
Wait for some time and refresh the screen.
-
RICS should reflect now.
-
-
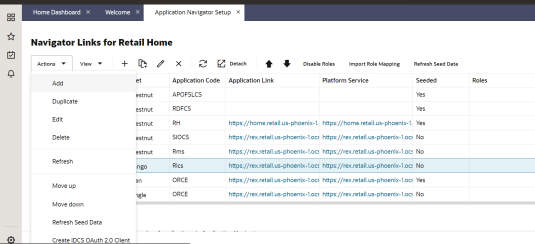
If RICS application is not reflecting even after following step 4. Select the row with the application code as RMS and click on the Actions menu on top left. Select Create IDCS OAuth 2.0 Client. A dialog will open for entering oauth2 client details.
Note:
Create IDCS OAuth 2.0 Client option is available only for applications those have platform service URL mentioned. RICS is making use of Merch platform service as both the apps are sharing same IDCS tenancy.
-
Skip this step if RICS application is not showing up. One of either Step 5 or Step 6 needs to be followed.
Select a row with application code as RICS. Click on the Actions menu on top left and select Create IDCS OAuth 2.0 Client. A dialog will open for entering oauth2 client details.
-
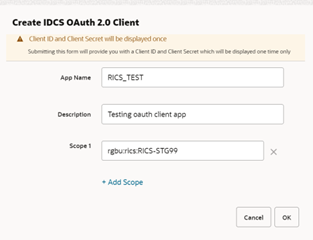
This dialog takes the following values:
-
App Name is 2-100 characters and will be used as the name in IDCS. Provide unique application name.
-
Description is a detailed description of the application.
-
Scope: <Custom environment-specific scope>
The scope pattern that is used in the RICS IDCS app creation template is rgbu:rics:<SERVICETYPE>-<ENVIRONMENT> where SERVICETYPE is RICS and EN-VIRONMENT is the environment type (STG, PRD, UAT, DEV1, DEV2, and so on).
For example:
"scope": "rgbu:rics:RICS-PRD""scope": "rgbu:rics:RICS-STG"
-
-
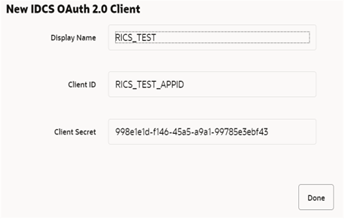
When the application is created, another dialog will open to show the client ID and client secret of the new application. These values should be copied down to a safe location, as they will only be shown once. Retail Home cannot retrieve the credentials again after the dialog is closed.
-
The Client ID and Client Secret from previous step will be used for generating access token.
Sample code for generating Access Token:
clientId=RICS_TEST_APPID clientSecret=998e1e1d-f146-45a5-a9a1-99785e3ebf43 idcsUrl=https://idcs-234e8f7334564936aa0ed93f2c39e9ca.identity.pint.oc9qadev.com scope=rgbu:rics:RICS-STG99 ec=$(echo -n "$clientId:$clientSecret" | base64 -w 0) AccessToken=$(curl -iv \ -H "Authorization: Basic $ec" \ -H "Content-Type: application/x-www-form-urlencoded;charset=UTF-8" \ --request POST $idcsUrl/oauth2/v1/token \ -d "grant_type=client_credentials&scope=$scope" | grep -o -P '(?<=access_token":").*(?=","token_type)') echo $AccessToken
-
Now a service call can be made by passing along the access token generated in previous step.
Here is sample curl command with Bearer token and the DDS get schemas endpoint:
ddsGetSchema-sUrl=https://rex.retail.us-phoenix-1.ocs.oc-test.com:443/rgbu-rex-eit-stg99-rics/dynamic-data-service-web/resources/dds/schemas curl -ivkL --noproxy '*' -H "Authorization: Bearer $AccessToken" -H "Con-tent-Type: application/xml" -X GET $ddsGetSchemasUrl
Sample Response:
{ "schemas": [ "DDS_RIBEH", "RFI_TEST" ], "userInRoles": [ "AdminRole" ] }