Security Model Overview
The security rules are defined as policies and policy sets, in XML files, grouped by these policy types:
- Tasks - for controlling access to menu options.
- Filters - for applying filters to data.
- Fields - for controlling access to list view columns and form fields.
- Actions - for controlling access to list view and form actions.
- Redactions - for forming subsets of data, such as to remove associated child data that is not required.
- Decisions - for controlling whether a UI component is shown or hidden.
A predefined set of combining algorithms determine how the policies are applied and whether the rule is to permit or deny access:
- PermitPreferred - If any rules in the policy generate a PERMIT result, then PERMIT is the result. If any rules in the policy generate a DENY result and no rule generates a PERMIT result, then DENY is the result. If no rules are matched, then the result is NO_MATCH. Used for Tasks and Actions.
- DenyPreferred - If any rules in the policy generate a DENY result, then DENY is the result. If any rules in the policy generate a PERMIT result and no rule generates a DENY result, then PERMIT is the result. If no rules are matched, then the result is NO_MATCH. Used for Tasks and Actions.
- LastMatch - The last rule to match is chosen as the result. If there are no matches, the result is NO_MATCH. Used for Tasks and Actions.
- CombineAnd - If one rule is matched, the expression from that rule is the result in a singleton list. If multiple rules are matched, then the expressions from those rules are ANDed together as the result in a singleton list. If no matches are generated, then the result is an empty list. Used for Filters.
- CombineOr - If one rule is matched, the expression from that rule is the result in a singleton list. If multiple rules are matched, then the expressions from those rules are ORed together as the result in a singleton list. If no matches are generated, then the result is an empty list. Used for Filters.
- AllMatch - If any rules are matched, then all are returned as the result list. If no rules are matched, then an empty list is the result. Used for Redactions.
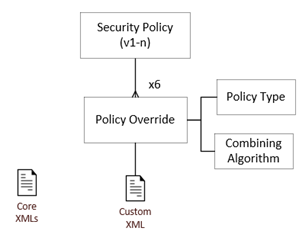
The Security Policy comprises a set of Policy Override records per Policy Type (so up to six sets of Policy Overrides). Each Policy Override record is associated to a single Policy Type and Combining Algorithm, and has a single XML file attachment.