Understand SSO Authentication and Oracle Analytics Server
Integrating a single sign-on (SSO) solution enables a user to log on (sign-on) and be authenticated once. Thereafter, the authenticated user is given access to system components or resources according to the permissions and privileges granted to that user.
You can configure Oracle Analytics Server to trust incoming HTTP requests authenticated by a SSO solution that is configured for use with Oracle Fusion Middleware and Oracle WebLogic Server.
When Oracle Analytics Server is configured to use SSO authentication, it accepts authenticated users from whatever SSO solution Oracle Fusion Middleware is configured to use. If SSO is not enabled, then Oracle Analytics Server challenges each user for authentication credentials. When Oracle Analytics Server is configured to use SSO, a user is first redirected to the SSO solution's login page for authentication. After the user is authenticated the SSO solution forwards the user name to Presentation Services where this name is extracted. Next a session with the BI Server is established using the impersonation feature, a connection string between the Presentation Server and the BI Server using credentials that act on behalf of a user being impersonated.
After successfully logging in using SSO, users are still required to have the oracle.bi.server.manageRepositories permission to log in to the Model Administration Tool using a valid user name and password combination.
Configuring Oracle Analytics Server to work with SSO authentication requires minimally that the following be done:
- Oracle Fusion Middleware and Oracle WebLogic Server are configured to accept SSO authentication. Oracle Access Manager is recommended in production environments.
- Oracle Analytics Server Presentation Services is configured to trust incoming messages.
- The HTTP header information required for identity propagation with SSO configurations, the user identity and SSO cookie, is specified and configured.
How an Identity Asserter Works
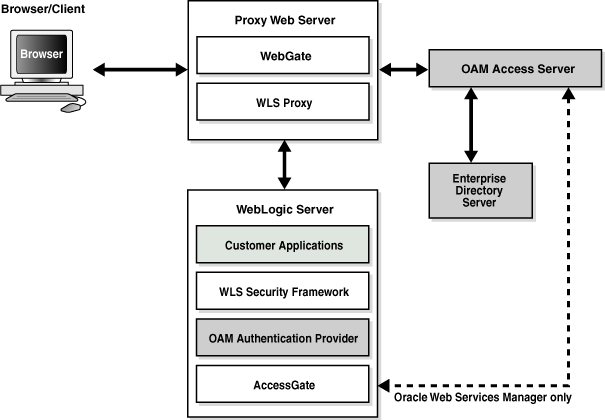
This section describes how Oracle Access Manager authentication provider works with Oracle WebLogic Server using Identity Asserter for single sign-on, providing the following features:
- Identity Asserter for Single Sign-on
This feature uses the Oracle Access Manager authentication services and validates already-authenticated Oracle Access Manager users through a suitable token and creates a WebLogic-authenticated session. It also provides single sign-on between WebGate and portals. WebGate is a plug-in that intercepts web resource (HTTP) requests and forwards them to the Access Server for authentication and authorization.
- Authenticator
This feature uses Oracle Access Manager authentication services to authenticate users who access an application deployed in Oracle WebLogic Server. Users are authenticated based on their credentials, for example a user name and password.
After the authentication provider for Oracle Access Manager is configured as the Identity Asserter for single sign-on, the web resources are protected. Perimeter authentication is performed by WebGate on the web tier and by the appropriate token to assert the identity of users who attempt access to the protected WebLogic resources.
All access requests are routed to a reverse proxy web server. These requests are in turn intercepted by WebGate. The user is challenged for credentials based on the authentication scheme configured within Oracle Access Manager (form-based login recommended).
After successful authentication, WebGate generates a token and the web server forwards the request to Oracle WebLogic Server, which in turn invokes Oracle Access Manager Identity Asserter for single sign-on validation. Oracle Access Manager is able to pass various types of heading token, the simplest being an HTTP header called OAM_REMOTE_USER containing the user ID that has been authenticated by Oracle Access Manager. The WebLogic Security Service invokes Oracle Access Manager Identity Asserter for single sign-on, which next gets the token from the incoming request and populates the subject with the WLSUserImpl principal. The Identity Asserter for single sign-on adds the WLSGroupImpl principal corresponding to the groups the user is a member of. Oracle Access Manager then validates the cookie.
The diagram depicts the distribution of components and the flow of information when the Oracle Access Manager Authentication Provider is configured as an Identity Asserter for SSO with Oracle Fusion Middleware.
How Oracle Analytics Server Operates with SSO Authentication
After SSO authorization has been implemented, Presentation Services operates as if the incoming web request is from a user authenticated by the SSO solution. Presentation Services next creates a connection to the BI Server using the impersonation feature and establishes the connection to the BI Server on behalf of the user. User personalization and access controls such as data-level security are maintained in this environment.