Authentication and Authorization
Learn about the authentication and authorization features on the Oracle GoldenGate side and on the Database side when working with Oracle GoldenGate.
Oracle GoldenGate Authentication and Authorization
-
Using credentials (username, passwords): The credentials information is stored in a credential store, which is used to set up USERIDALIAS while setting up database connections. This is the most common method for authentication. Credential store can only be modified from REST API, Admin Client or Web Interface only.
-
Using Certificates: If a client is authenticated by a certificate, the server stores the signing CA certificate in a trust store so that the server can validate the identity of the client. This is commonly used when using Distribution Paths.
-
Using external Identify Providers: Oracle uses IDCS, IAM (Cloud) , and OAM (On-premise) for external Identity Management, using OAuth2 as the communication protocol.
Authorization (AZ) includes Oracle GoldenGate to Oracle GoldenGate communication, and tasks for network and server configuration.
All the security configurations and services are common to MA-based servers. These servers authenticate, authorize, and secure access to command and control, monitoring, data conveyance, and information service interfaces for Oracle GoldenGate.
Oracle GoldenGate Microservices provides an infrastructure for building service-aware applications to operate and integrate into global, cloud-based deployment environments
Oracle GoldenGate Authentication
The goal of an authenticated identity in Oracle GoldenGate is to establish identity authentication between users, applications, and Oracle GoldenGate Microservices deployments. The authentication design provides the option to either validate users and applications with certificates or user credentials stored as credential aliases (username and password pair).
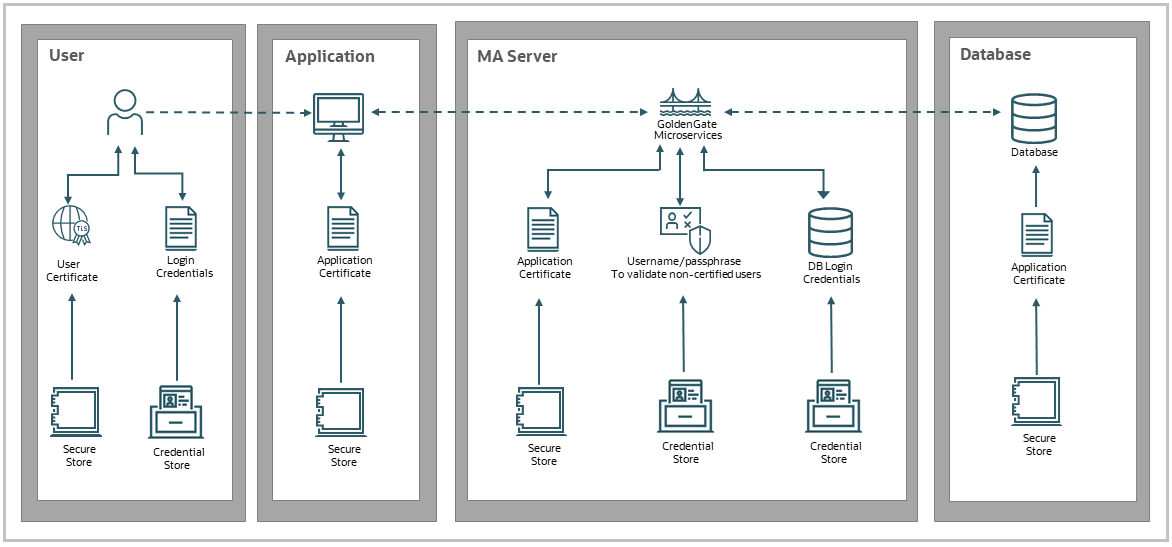
Authentication with User Credentials
User credentials (username, password) combination is stored in the credential store and is accessible using credential aliases, allowing users to keep the user ID and password ensconced in the credential store and only the alias to connect to an Oracle GoldenGate deployment or another application.
Strong password policy is implemented with guidelines to have 1 uppercase, 1 lowercase, 1 numeric, and 1 special character.
The maximum password length in Oracle GoldenGate 23ai and higher releases is 1024 bytes.
Certificate Management
When a client attempts to connect to a source or target database through a TCPS (Secure TCP) database connection service, Oracle GoldenGate uses TLS certificate-based authentication to verify the connection, as shown in the following diagram.
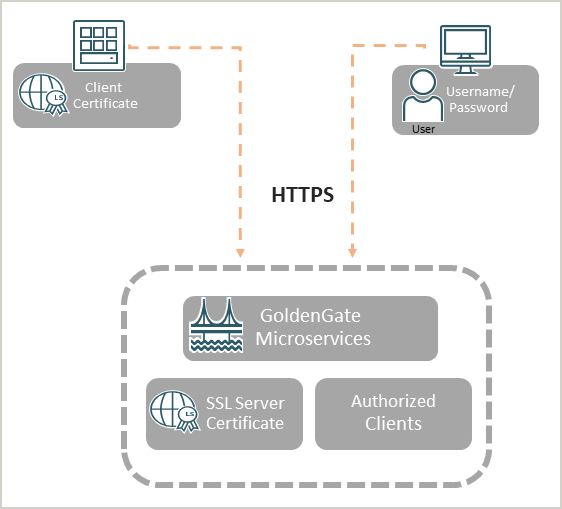
Notice that secure network communication within Oracle GoldenGate is done with TLS (HTTPS underneath REST-API calls and WSS for the Distribution Path).
Oracle GoldenGate supports mutual TLS (mTLS). See the Secure Communication Using TLS and mTLS Support to learn about how mTLS can be used as an additional layer of authentication during the client-server handshake.
You can create self-signed client and server certificates or you can install CA-signed server-side certificates for authentication. These certificates can be managed for checking certificate validity, expiry, and usage from Oracle GoldenGate Service Manager.
To learn about managing certificates from the Service Manager web interface, see Manage Certificates for Deployments.
For steps to create certificates, see Create Certificates for Secure Deployments.
To learn about implementing external rootCA certificates for connecting secure deployments host of different servers, see Connecting Two Deployments Using External RootCA Certificate
Authentication with Certificates
User authentication can be done with certificates when connecting between deployments. This authentication method is an alternative to using credential aliases (user ID, password) for authentication.
You can set up Certificate authentication when configuring a distribution path to connect the source deployment to a target deployment that is on a different network. This scenario is most common different organizations need to communicate over a secure network for data transfer. In this case, a distribution client (distclient) user with Operator role is created on the target deployment and the client certificate is stored on the source deployment. The distclient user presents the client certificate when connecting to the source deployment. This certificate is verified by the trusted rootCA certificate available on the target deployment and m-TLS is used by the source to validate the target server certificate. To learn more about setting up certificates for user authentication, see the Connecting Two Deployments Using External RootCA Certificate and Connecting Two Deployments Using External RootCA Certificate.
Also see the Add a Distribution Path section for steps used when configuring certificates for two separate deployments.
Authorization in Oracle GoldenGate
Authorization in Oracle GoldenGate relies on user roles. Actions performed in Oracle GoldenGate depend on the user role applied to a user. Use the REST API Service Endpoints for details on determining the required user role for performing different actions.
You can choose and assign from the following user roles when creating Oracle GoldenGate users.
Table 4-1 Oracle GoldenGate User Roles and Privileges
| Role ID | Privilege Level |
|---|---|
|
User |
Allows information-only service requests, which do not alter or effect the operation of either the MA. Examples of Query/Read-Only information include performance metric information and resource status and monitoring information. |
|
Operator |
Allows users to perform only operational actions, such as creating, starting and stopping resources. Operators cannot alter the operational parameters or profiles of the MA server. |
| Administrator |
Grants full access to the user, including the ability to alter general, non-security related operational parameters and profiles of the server. |
|
Security |
Grants administration of security related objects and invoke security related service requests. This role has full privileges. |
Oracle GoldenGate User Management
Oracle GoldenGate users that are created at different stages of deployment configuration, have different access functions for Oracle GoldenGate Microservices.
The first user for Oracle GoldenGate is set up from the Oracle GoldenGate Configuration (OGGCA) utility. This user can access the Service Manager and all Microservices for all deployments associated with the Service Manager on the host.
After you access the Service Manager using the first user, you can create users from the
User Administration web page of the Service Manager. Depending on the user role, you can
enable users to access Oracle GoldenGate Microservices. The following image shows the User
Administration page in Service Manager with the different users.
The following image shows the User Administration page in Administration Service with the
different users.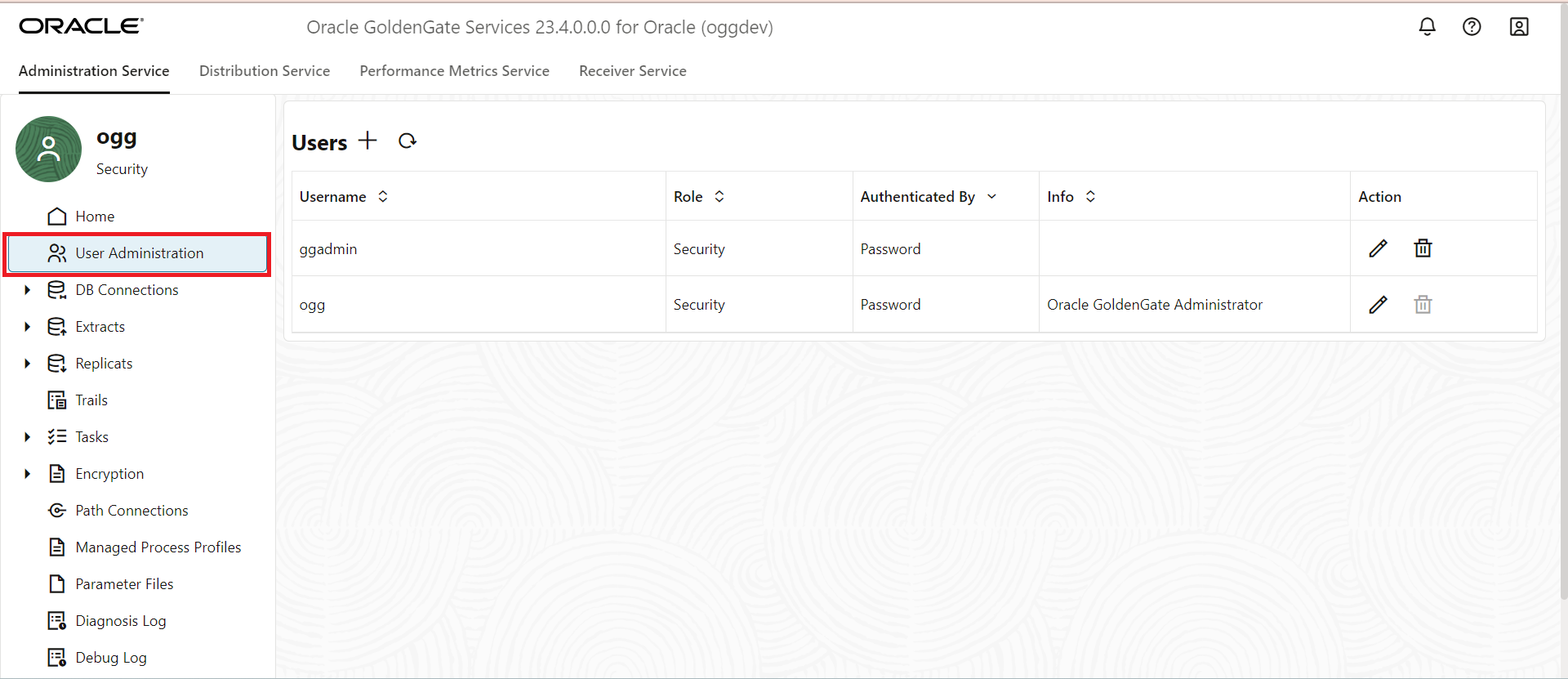
Here are some examples of accessing Oracle GoldenGate Microservices with different user roles:
-
Example 1: If you create a user with the Operator role in Administration Service, you cannot access the Service Manager with these credentials.
-
Example 2: If you create a user with the Operator role in the Service Manager, you cannot access the Administration Service with these credentials.
Oracle GoldenGate also allows you to integrate with external identity providers including IAM, OAM, IDCS. Starting with Oracle GoldenGate 23.9, Microsoft EntraID is also supported for external authorization set up. See Delegate User Management to an External Identity Provider to learn about configuring these external IdPs with Oracle GoldenGate for client authentication.
Database Authentication and Authorization
Learn about database authentication and authorization configurations required when setting up the database to work with Oracle GoldenGate.
Database Authentication
Database connections are managed with the
USERIDALIAS parameter in Oracle
GoldenGate. You cannot directly connect to the
database from Oracle GoldenGate. The DBLOGIN
USERIDALIAS,
FETCHUSERIDALIAS, and
MINNINGDBUSERIDALIAS contains
username and password for any supported database,
which is stored in Oracle GoldenGate
credentialstore.
Oracle GoldenGate 23ai and higher support a maximum password length of 1024 bytes.
Kerberos Authentication
Oracle GoldenGate supports operating system level login for Oracle database. The support of Kerberos authentication is enabled on top of the existing OS level, as an external authentication feature.
For implementation details regarding Kerberos Authentication, see Configure Kerberos Authentication.