29 Supporting Multiple Split SSO Domains Using ECC
OAM supports multi-domain SSO by default, where SSO can be achieved across multiple internet domains. Also, OAM supports split-domain authentication, where SSO will be available for applications in a specific domain and there will be no cross-domain SSO between domains.
The following two scenarios are supported.
Scenario 1: Using different policies for the same application in each domain
In this case, if the user wants to apply different authentication policies and schemas to each application based on the web domain, they need to create separate application domains for each application and web domain. For each web domain, all the user interaction with the OAM server must happen in the same domain. Application Webgate in a domain must interact with a reverse proxy in the same domain, and the OAM credential collector pages must be served from the reverse proxy in the same domain.
- Define separate application domains and policies for each web domain and application.
- Use separate WebGate for each application domain.
- Use separate reverse proxies per domain.
- Configure an optional load balancer to support multiple web domains and their reverse proxies.
- Update challenge redirects URL in the authentication schemes used in policies to point
to the domain load balancer/reverse proxy.
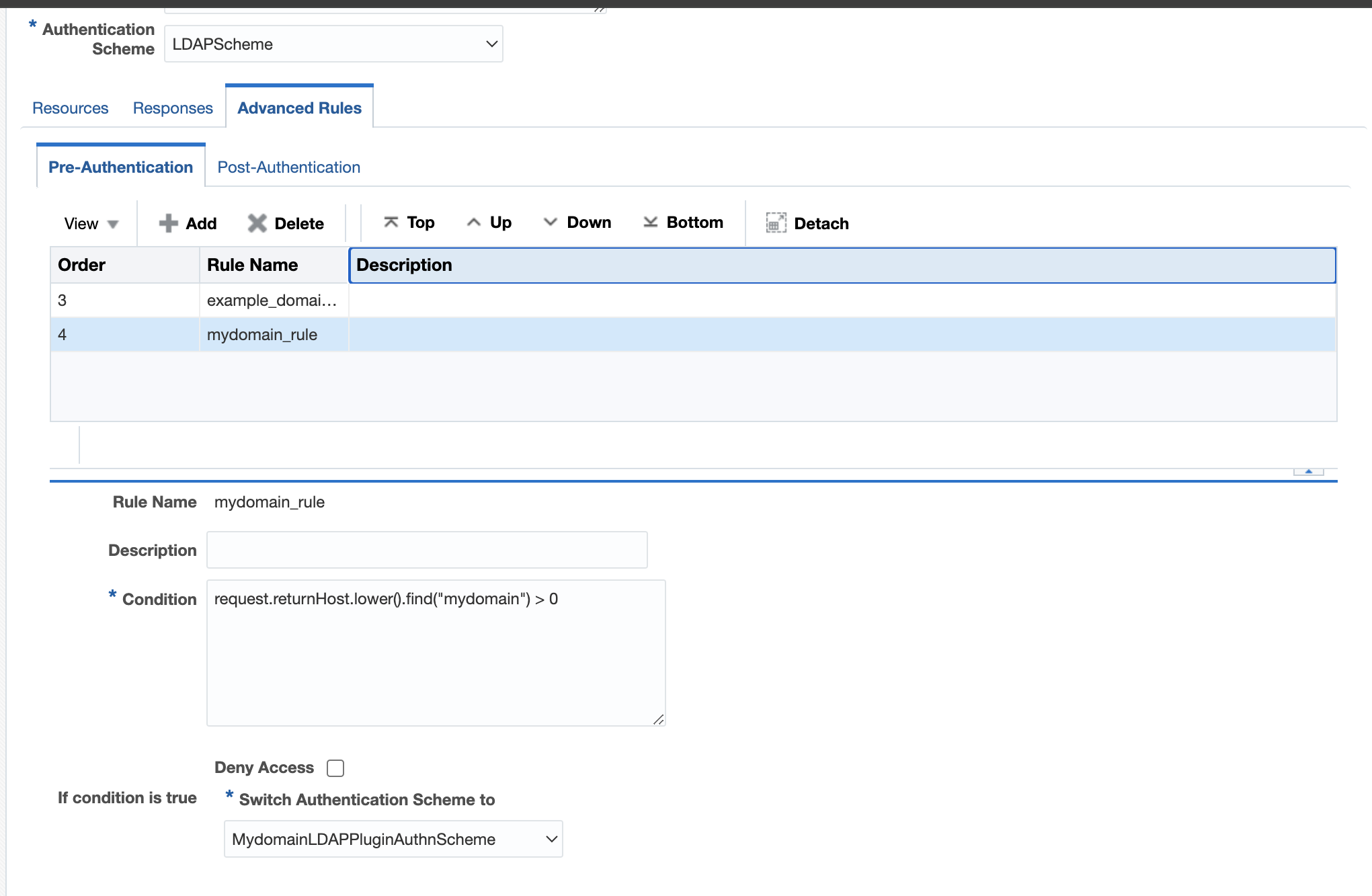
For example, Domain1: mydomain.com
Figure 29-1 Mydomain example
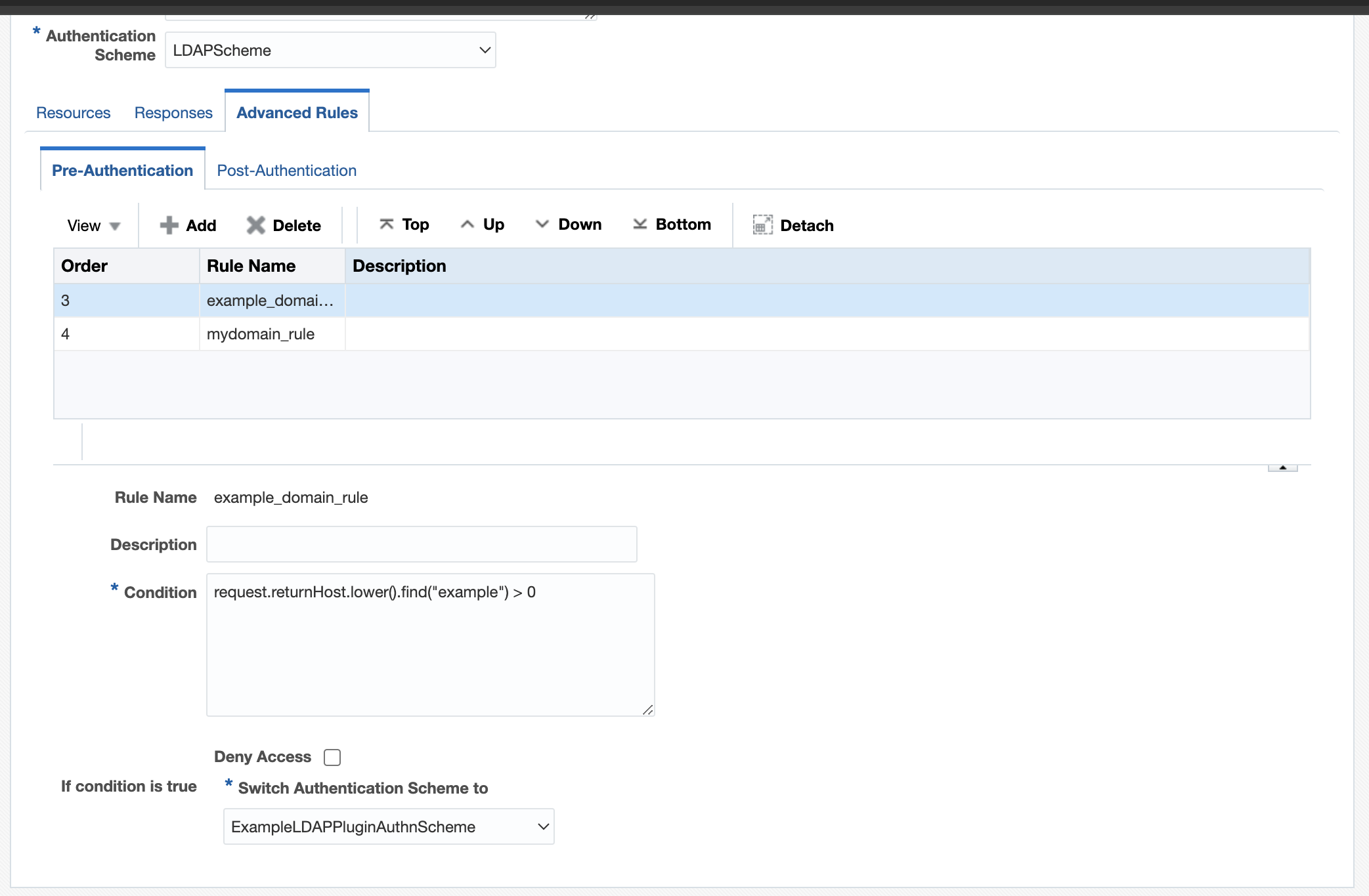
 Domain2: example.com
Domain2: example.comFigure 29-2 Example Domain
Scenario 2: Using the same policies for the same application in both the domains
In this case, all the policies are the same across domains but the login URLs must stay in the same domain. All the user interactions with the OAM server remain in the same web domain. Application WebGate in a domain must interact with a reverse proxy in the same domain, and the OAM credential collector pages must be served from the reverse proxy in the same domain.
- Define a single application domain per application for all the web domains.
- Use a separate reverse proxy and WebGate for each web domain or use a separate virtual host configuration for each web domain.
- Configure a load balancer to support all domains to the front end of the OAM server or create a separate reverse proxy for each domain.
- Create separate authentication schemes for each web domain. Update the challenge
redirect URL to the domain URL.
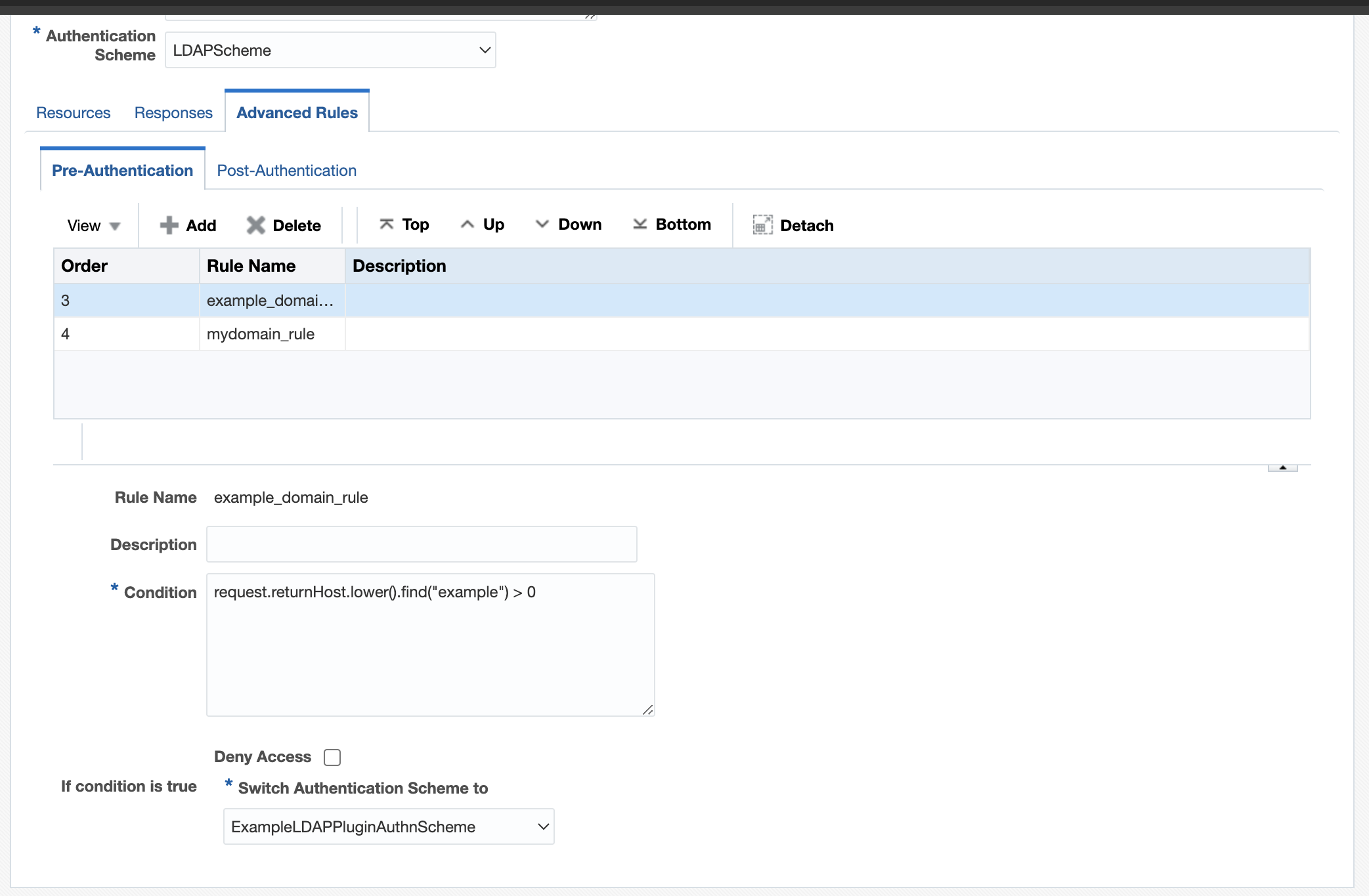
Domain1: example.com
Figure 29-3 Example Domain Schema
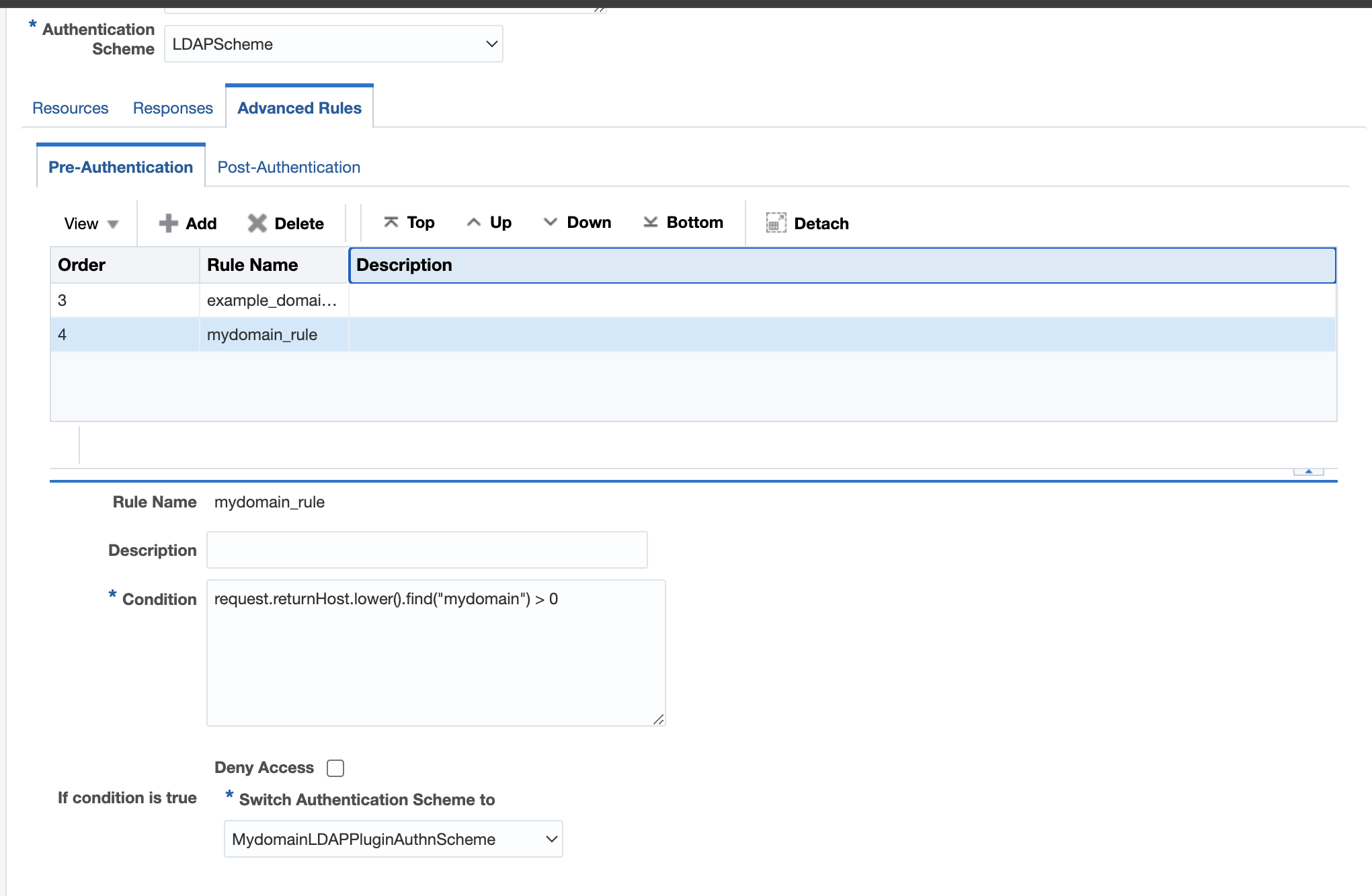
 Domain2: mydomain.com
Domain2: mydomain.comFigure 29-4 MyDomain Schema
- Update the policy to define pre-authentication rules.
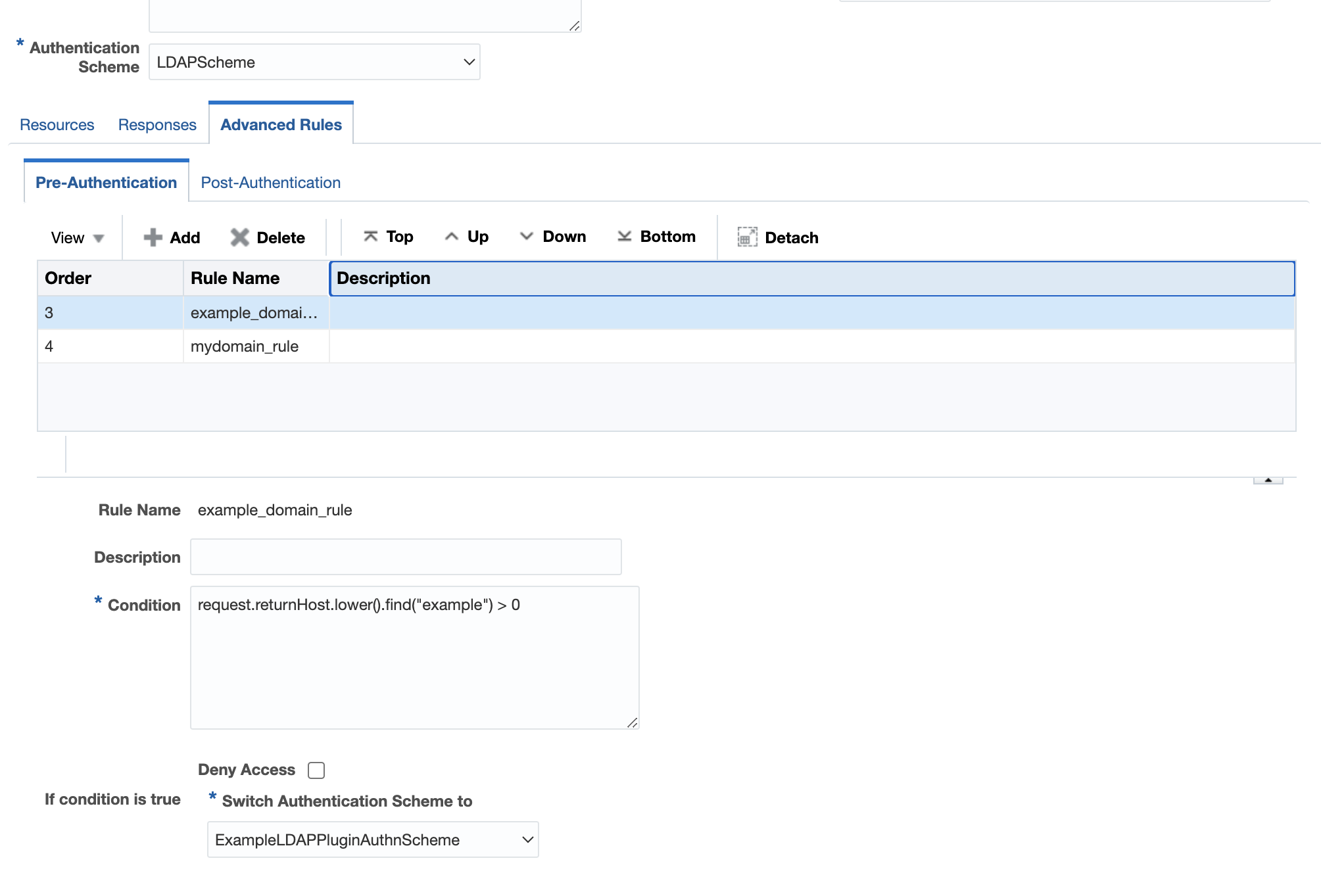
- Define a pre-authentication rule in the authentication policy for each domain like
request.returnHost.lower().find("mydomain") > 0and assign the authentication scheme defined for that (my domain) to it. - Add pre-authentication rules for each domain that needs to be
supported.
example domain rule
Figure 29-5 Example Domain Rule
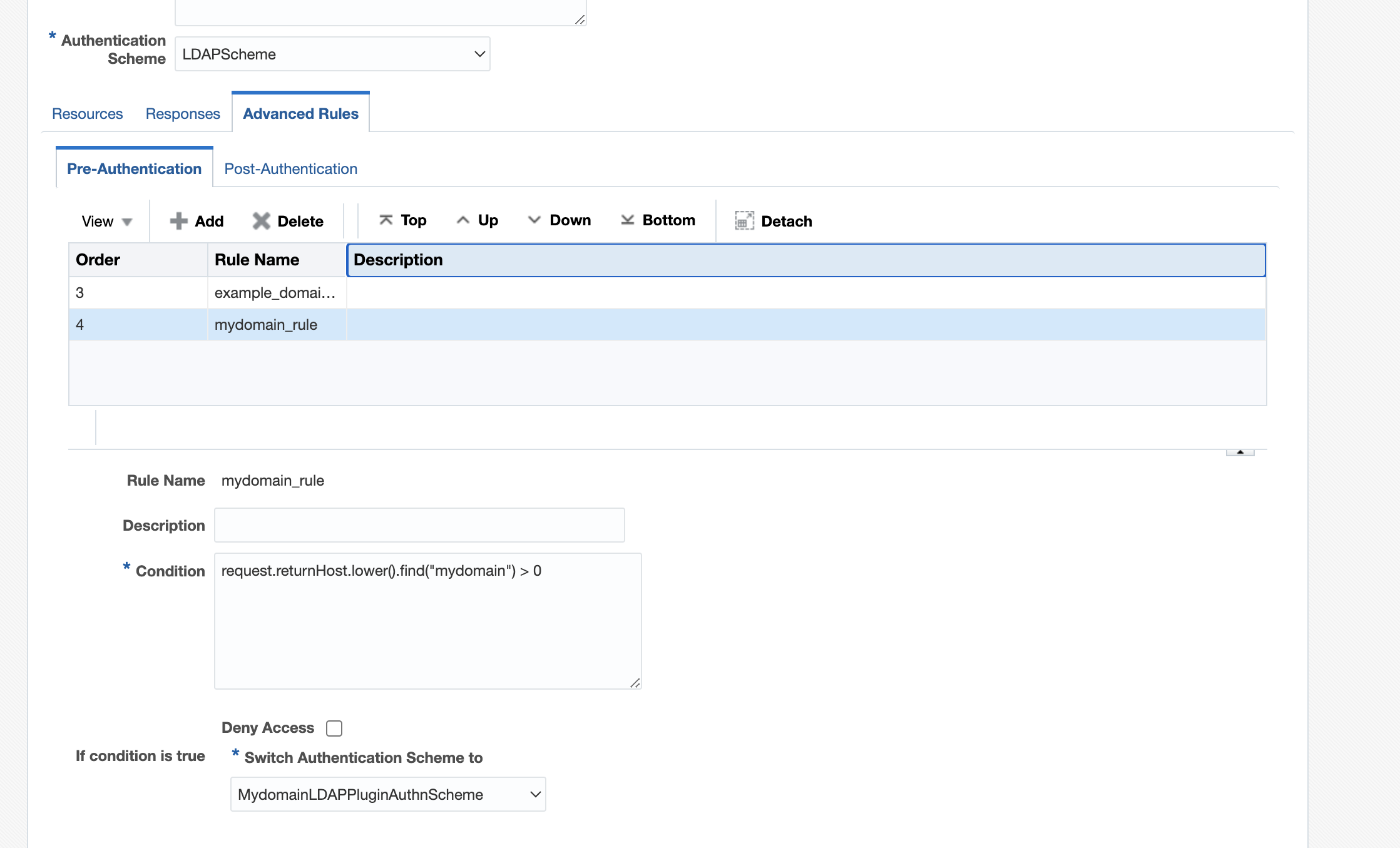
 mydomain rule
mydomain ruleFigure 29-6 MyDomain Rule
- Define a pre-authentication rule in the authentication policy for each domain like
- Run the WLST command
disableSkipAuthnRuleEval()to enable rule evaluation.