3 Architecture
Important:
The software described in this documentation is either in Extended Support or Sustaining Support. See Oracle Open Source Support Policies for more information.
We recommend that you upgrade the software described by this documentation as soon as possible.
Oracle Cloud Native Environment is built from several discrete components. You interact with the environment directly using the Platform CLI. The Platform API Server interacts with the Platform Agent on each Kubernetes node. The Platform Agent is responsible for handling host-level operations on behalf of the Platform API Server.
Figure 3-1 Architecture
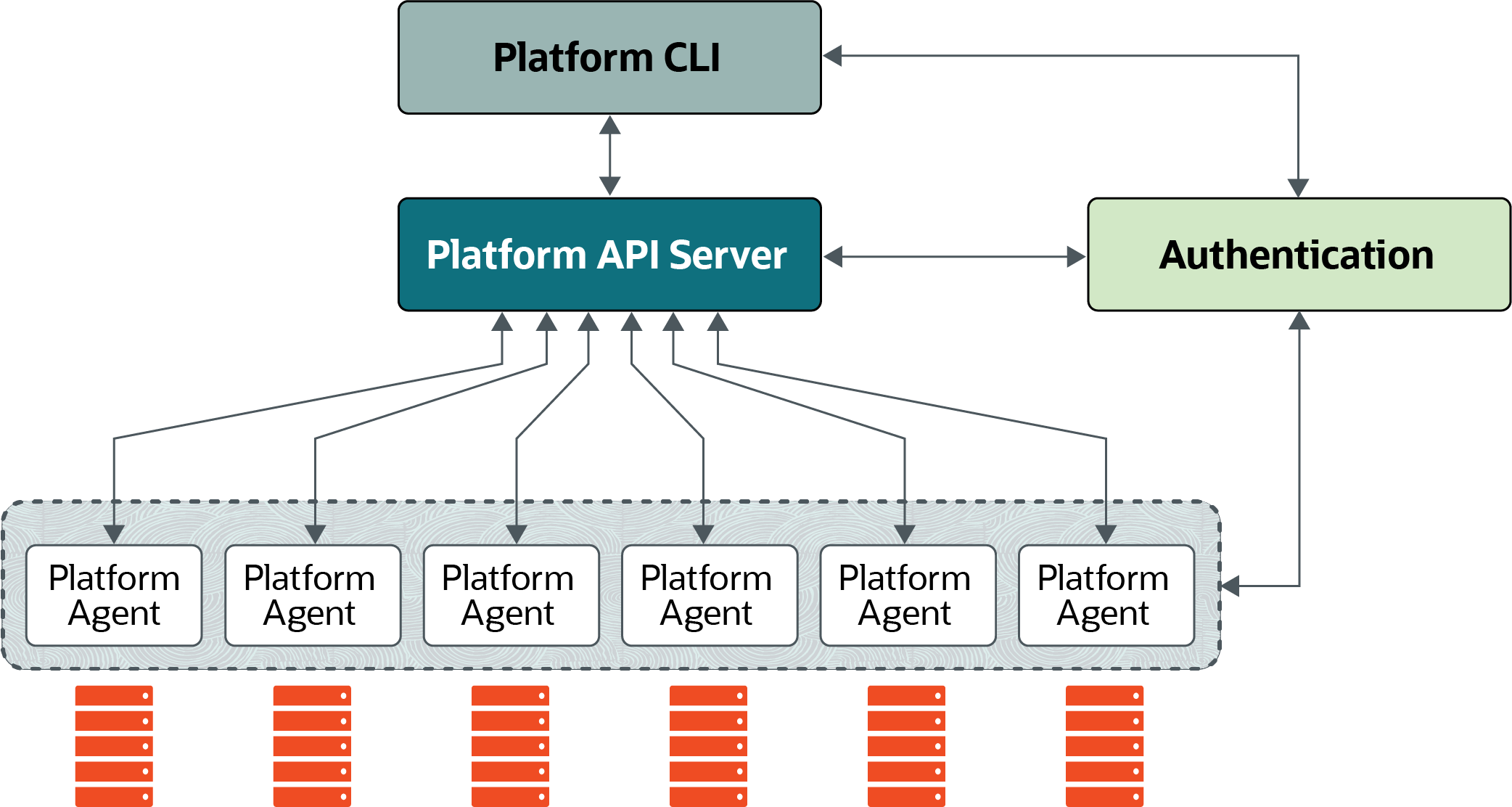
Platform API Server
The Platform API Server performs the business logic and manages all entities, from hosts to microservices. The Platform API Server is responsible for managing the state of the environment, including the deployment, and configuration of modules to one or more nodes in a cluster.
Platform Agent
The Platform Agent runs on each host to proxy requests from the Platform API Server to small worker applications. The primary reason for this is to ensure the Platform Agent process uses as little memory as possible. The Platform Agent refers to the union of the Platform Agent process and associated worker applications.
The Platform Agent knows how to gather the state of resources on its host and to change the state of those resources. The Platform Agent knows if a firewall port is open or closed, or if a package is installed and at which version. It also knows how to close that port if it's open, upgrade the package if it's old, or install the package if it's not installed.
Platform CLI
The Platform CLI is used to communicate with the Platform API Server. The Platform CLI is an
application (the olcnectl command) that converts the input to Platform API
Server calls. No business logic takes place in the Platform CLI. Parsing of the commands
entered into the Platform CLI takes place in the Platform API Server.
The Platform CLI must be installed on an operator node.
Authentication
Standard X.509 certificates are used to establish node identity and authentication. The Platform API Server, Platform CLI, and the Platform Agent on Kubernetes nodes require a valid certificate chain for each component to mutually authenticate. Without these certificates, connections between the components and nodes are rejected.
X.509 certificates can be created and distributed manually, or using an authentication server such as Vault by HashiCorp.