Determine the Integration Method
You can integrate your applications with Oracle Identity Cloud Service for authentication by using several methods. Most methods rely on open standards such as Security Assertion Markup Language (SAML) and OpenID Connect (OIDC) as authentication protocols. Some of these methods are recommended for cloud-based applications, some are best for on-premises applications, and others can be used in both cases.
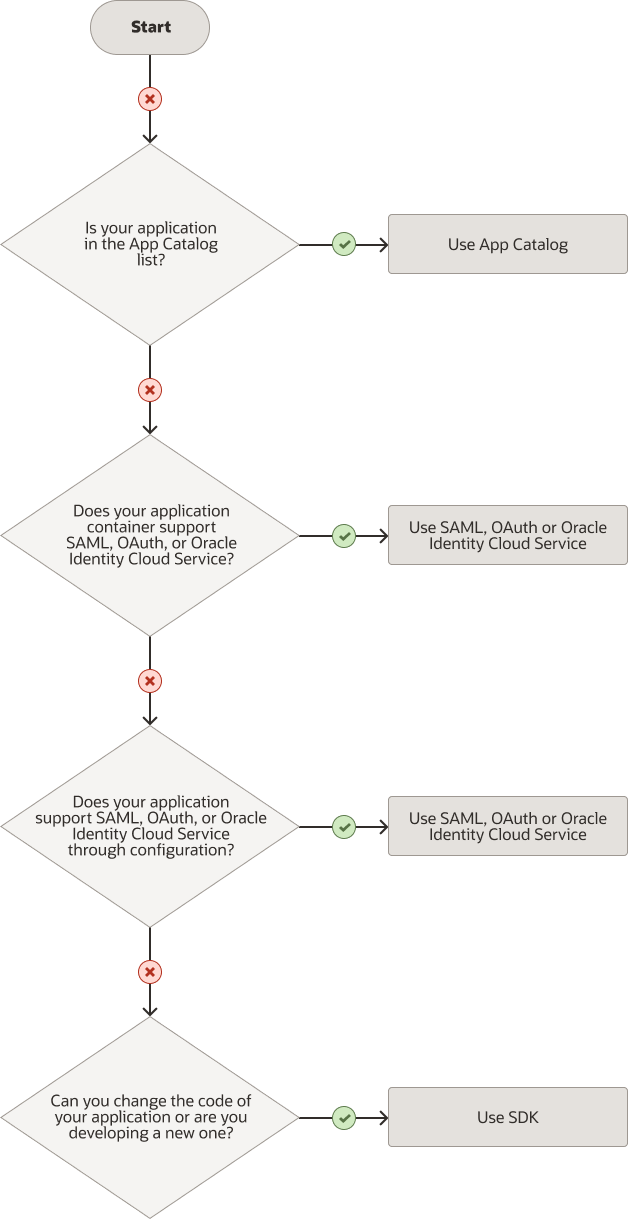
Your options depend on the type of application that you’re trying to integrate with Oracle Identity Cloud Service. Use the decision tree to help you decide what to do. You can choose from these methods:
-
App Catalog: Oracle creates and maintains the App Catalog, a collection of application templates, and provides step-by-step instructions for configuring most of the popular SaaS applications, such as Amazon Web Services and Google Suite.
-
Container or web server methods: The methods use the middle-tier or web-tier layer to integrate your application with Oracle Identity Cloud Service for authentication. These methods don’t usually require any change to the application source code or configuration. You can integrate your applications by using options such as WebLogic SAML Federation, Oracle App Gateway, and Apache HTTP Server.
Container security is most widely used for J2EE applications. This method relies on configuring the container itself to handle authentication. After the user has authenticated to the container, the application trusts the user identity and does not need to do additional work.
You implement the App Gateway solution within your own infrastructure, regardless of whether it’s in the cloud, on-premises, or uses a hybrid solution. App Gateway is a high-performance appliance that you install in the hosting solution of your choice. It leverages your DNS and networking solutions to provide services.
You can use App Gateway when you want to:
-
Integrate with applications that don’t support federation
-
Access your internal business applications (such as Oracle E-Business Suite) from the internet
-
Restrict unauthorized network access to your applications or apply multi-factor authentication to enhance security
-
Comply with industry regulations, such as Sarbanes-Oxley (SOX) or the Health Insurance Portability and Accountability Act (HIPAA)
-
Integrate with web applications that lack a native authentication mechanism
Just as with container security, if the application supports HTTP header based integration, you can use Apache HTTP Server acting as a reverse proxy web server to protect or redirect your application.
-
-
Methods that involve configuring the application: Oracle Identity Cloud Service supports standards such as OAuth 2.0, OpenID Connect 1.0, and SAML 2.0. If your application natively supports one of these protocols, you can choose this option just by configuring the application. This method is a quick and simple way to integrate your application with Oracle Identity Cloud Service.
Most modern web application development frameworks support OpenID Connect 1.0 integration with OpenID Connect providers by using out-of-the-box modules or libraries. The application uses these libraries to send and receive HTTP requests to Oracle Identity Cloud Service REST API endpoints to exchange the authorization code for a user access token.
-
Methods that use SDK to develop new applications: If you’re a developer, you can use programming language-specific libraries provided by Oracle Identity Cloud Service in the application source code, and then recompile and redeploy the application. SDKs are available for programming languages such as Java, Node.js, and Python.
If you're developing a Java, Node.js, or Python web application, and you want to use Oracle Identity Cloud Service as your application's authentication mechanism, then use the SDK that's associated with the language of your application. Oracle Identity Cloud Service's SDKs are based on industry-standard protocols and layers, such as OAuth 2.0 and OpenID Connect 1.0.
-
Secure Form Fill: Suppose your application requires users to provide their sign-on credentials, but the application doesn't support OAuth, SAML, or any other federated sign-on method. Oracle Identity Cloud Service provides Secure Form Fill as an alternative to configure SSO for such applications. With Secure Form Fill, Oracle Identity Cloud Service can automatically fill out the sign-on form and submit the credentials. This option requires a browser plug-in, and we recommend it only when none of the other options are available.
Use this decision tree to select the integration option that best fits your requirements on Oracle Identity Cloud Service: