Learn About Network Connectivity Design Options
The following topics show architecture diagrams for each option and then compares their pros and cons.
FastConnect
FastConnect offers high-speed (1 Gbps or 10 Gbps) connectivity into Oracle Cloud Infrastructure.
- Through a FastConnect provider
- Through a non-FastConnect provider, also known as a third-party provider
- Through a direct fiber handoff, if you’re colocated in the same data center campus as Oracle
Unlike our competitors, Oracle Cloud Infrastructure has a flat fee per FastConnect connection. We don’t charge an incremental fee for data being transferred across the connection. For details about FastConnect, including a step-by-step guide, see the FastConnect documentation.
To achieve redundancy, we recommend that you have at least two FastConnect connections to avoid a single point of failure on the Oracle side. The highest availability option is to also have two wide area network (WAN) routers deployed in your on-premises location.These routers are generically referred to as customer-premise equipment (CPE) .
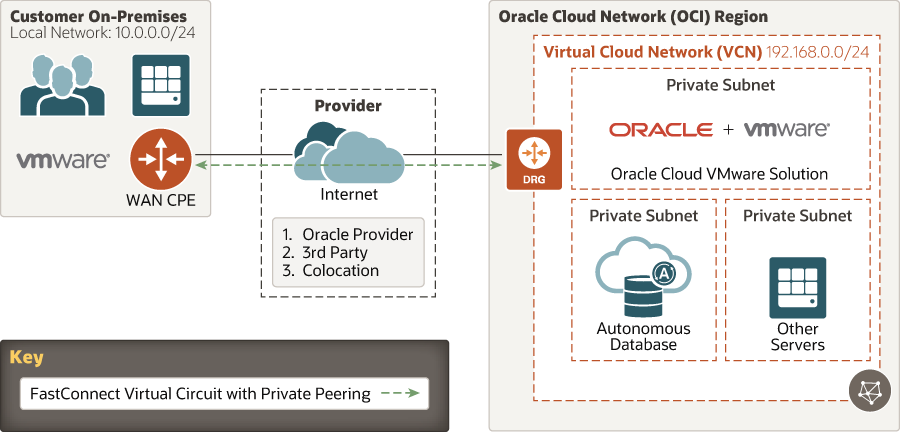
Description of the illustration fastconnect_w_priv_peering.png
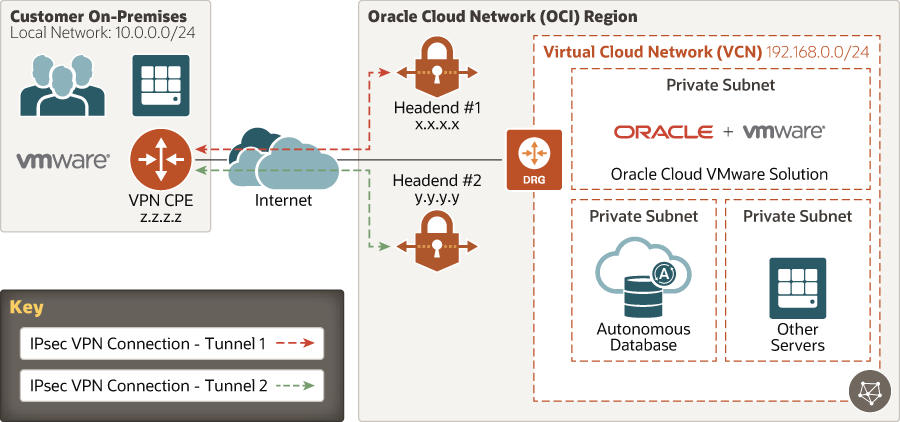
Oracle Cloud Infrastructure-Based IPSec VPN
Oracle Cloud provides the VPN Connect service. A single IPSec connection automatically provides two diverse IPSec tunnels.
It’s your responsibility to ensure that both tunnels come up, or deploy two different VPN CPEs to achieve diversity on both the on-premises and Oracle sides of the connection. VPN Connect is free of charge, and goes over the public internet. As a result, your connection could be subject to jitter and variability based on current internet conditions outside of Oracle’s control.
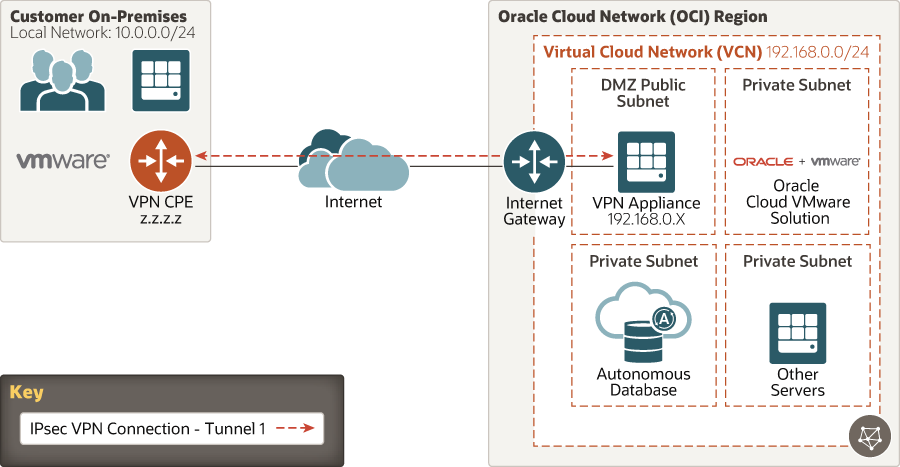
NVA-Based IPSec VPN
To have more control over both ends of the IPSec VPN connection, you might want to deploy your own network virtual appliance (NVA).
In this model, you deploy one or more virtual machines (VMs) to build a highly available firewall. Examples include Palo Alto Networks, Fortinet, and Check Point. For the complete list of firewall solutions, see the Oracle Cloud Marketplace. For an example, see a step-by-step guide for Palo Alto networks.
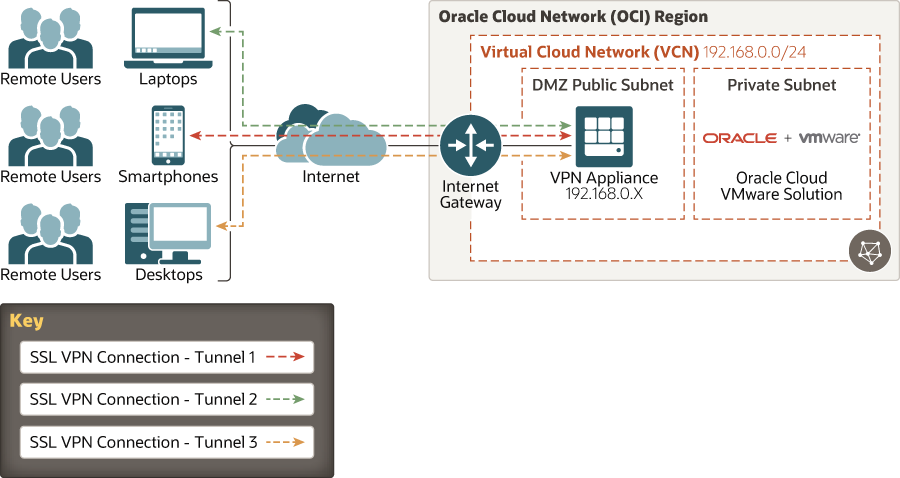
NVA-Based SSL VPN
SSL VPN could be a requirement for some applications. SSL VPN could be accomplished and deployed as an NVA in Oracle Cloud Infrastructure, or potentially as an appliance within Oracle Cloud VMware Solution.
An example that uses the Oracle Cloud Marketplace and the OpenVPN appliance was shared earlier in this solution.
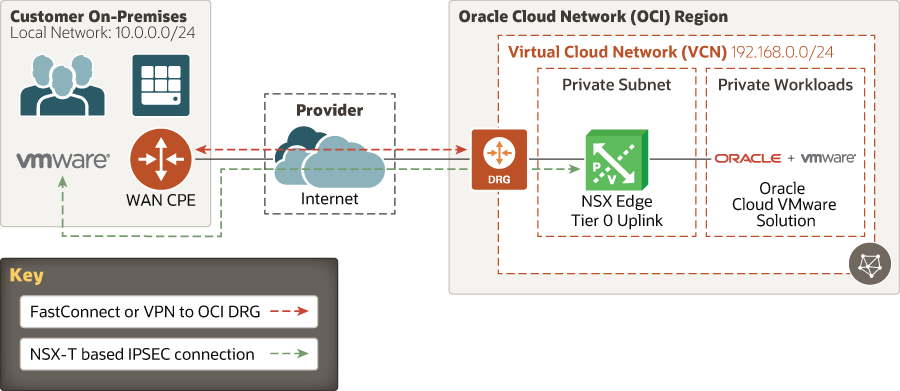
NSX-Based IPSec VPN
Another model of deployment is to establish an IPSec tunnel directly into Oracle Cloud VMware Solution. NSX-T supports layer 3 and layer 2 IPSec tunnels, but SSL VPN is not supported.
When the communication is over long-distance links, latency can dramatically slow down applications. We recommend layer 3 IPSec tunnels to keep the traffic cleanly segmented between on-premises and Oracle Cloud VMware Solution workloads. If you attempt to stretch layer 2 VLANs across the internet or dedicated links, chatty applications can dramatically slow down your connections.
Network Connectivity Technology Pros and Cons
The following table describes the pros and cons of each of the preceding technologies.
| Network Connectivity | PROs | CONs |
|---|---|---|
| FastConnect (DRG) | High speed, low latency links |
Need to deploy more than one FastConnect connection to avoid a single point of failure Depending on the model, it could take several weeks or months to deploy |
| VPN Connect (DRG) |
It's free Uses an existing internet connection Low lead time to set up Can be a software-only solution |
Subject to internet variability, jitter, and delay |
| IPSec or SSL VPN with an NVA |
Customer can control the VPN appliance in the cloud and on premises Flexibility to choose IPSec or SSL VPN network parameters |
Subject to internet variability, jitter, and delay Customer is responsible for managing the VM appliance Additional license costs to the VPN/firewall appliance vendor |
| IPSec VPN to NSX (over a private network) |
Uses an existing connection to access private subnets in Oracle Cloud Software-defined connectivity and ease of use for VMware administrators |
Assumes that private subnets are reachable from on-premises networks |
| FastConnect (DRG) plus IPSec VPN to an Oracle Cloud NVA |
High speed, low latency Encryption to Oracle Cloud Could also offer SSL VPN services (if supported by the VM appliance vendor) |
Customer is responsible for managing the VM
appliance
Additional license costs to the VPN/firewall appliance vendor |
| FastConnect (DRG) plus IPSec VPN to NSX Edge |
High speed, low latency Encryption to the Oracle Cloud VMware Solution environment Uses NSX technology |
VPN tunnel would be limited to the VMware environment Customer might not be able to access IaaS, PaaS, or SaaS services in Oracle Cloud Infrastructure |