Deploy a scalable remote access VPN architecture by using Cisco ASAv on Oracle Cloud Infrastructure
Virtual firewalls seamlessly extend Cisco's industry-leading on-premise security to the cloud. Ideal for remote workers and multi-tenant environments. Cisco ASAv provides Oracle Cloud Infrastructure (OCI) a scalable VPN solution with multiple feature options, such as remote-access, site-to-site, client less, and more.
Architecture
This reference architecture illustrates how organizations can deploy scalable remote access VPN architecture to access Oracle applications, like Oracle E-Business Suite and PeopleSoft, or applications deployed in OCI using Cisco ASA Virtual Firewall with flexible network load balancer.
To access these applications, Cisco recommends segmenting the network using a hub and spoke topology, where traffic is routed through a transit hub (Outside/Inside VCN) and is connected to multiple distinct networks (spokes). Ensure that you have deployed multiple ASA Virtual Firewall between flexible network load balancers. All traffic between spokes, is routed through the Outside/Inside VCN with Cisco ASA Virtual Firewall.
Deploy each tier of your application in its own virtual cloud network (VCN), which acts as a spoke. The Hub VCN/Mgmt VCN contains two Cisco ASAv Firewall behind the Network Load Balancer.
The Inside VCN connects to the spoke VCNs through LPGs/DRG. All spoke traffic uses route table rules to route traffic through the LPGs/DRG to the inside VCN to ensure traffic returns to VPN end users.
You can manage and monitor the ASAv using ASDM or CLI. Other management options are available such as Cisco Defense Orchestrator (CDO). The following diagram illustrates this reference architecture.
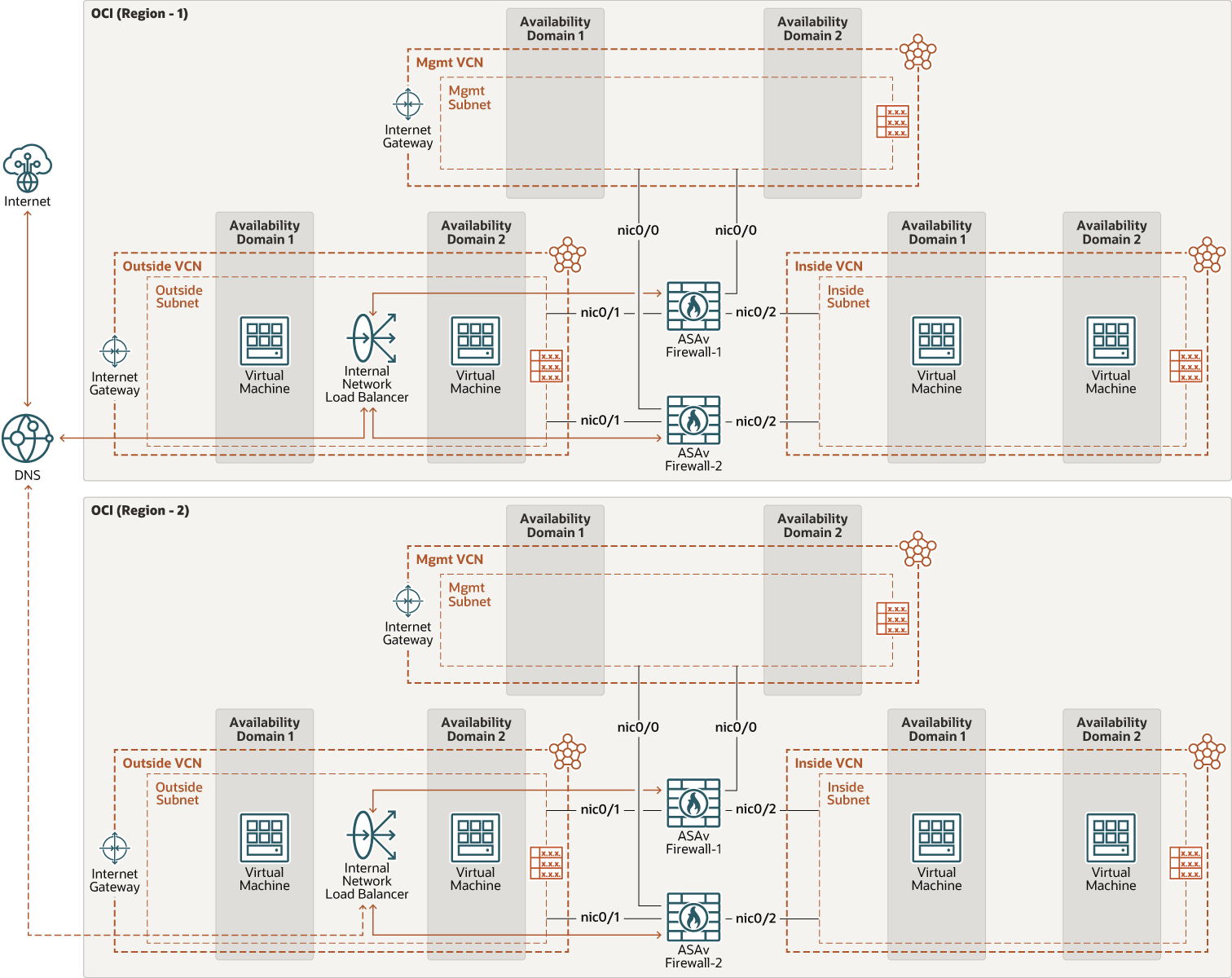
Description of the illustration ravpn_arch_cisco_asa_vfirewall.png
ravpn_arch_cisco_asa_vfirewall-oracle.zip
- Cisco ASA Virtual Firewall
The Cisco Adaptive Security Virtual Appliance (ASAv) brings full firewall functionality to virtualized environments to secure data center traffic and multi-tenant environments.to consistently protect public and private clouds.
- Region
An Oracle Cloud Infrastructure region is a localized geographic area that contains one or more data centers, called availability domains. Regions are independent of other regions, and vast distances can separate them (across countries or even continents).
- Availability domain
Availability domains are standalone, independent data centers within a region. The physical resources in each availability domain are isolated from the resources in the other availability domains, which provides fault tolerance. Availability domains don’t share infrastructure such as power or cooling, or the internal availability domain network. So, a failure at one availability domain is unlikely to affect the other availability domains in the region.
- Fault domain
A fault domain is a grouping of hardware and infrastructure within an availability domain. Each availability domain has three fault domains with independent power and hardware. When you distribute resources across multiple fault domains, your applications can tolerate physical server failure, system maintenance, and power failures inside a fault domain.
- Virtual cloud network (VCN) and subnet
A VCN is a customizable, software-defined network that you set up in an OCI region. Like traditional data center networks, VCNs give you complete control over your network environment. A VCN can have multiple non-overlapping CIDR blocks that you can change after you create the VCN. You can segment a VCN into subnets, which can be scoped to a region or to an availability domain. Each subnet consists of a contiguous range of addresses that don't overlap with the other subnets in the VCN. You can change the size of a subnet after creation. A subnet can be public or private.
- Management VCN
The Mgmt VCN is a centralized network where Cisco ASA Virtual Firewall are deployed. It provides secure connectivity to Inside VCN/all spoke VCNs, OCI services, public endpoints and clients, and on-premises data center networks.
- Outside VCN
The outside VCN contains a public subnet to host Flexible Network Load Balancer which end users use to connect as VPN headend. Each Cisco ASA Virtual Firewall also has an interface within this VCN’s subnet.
- Inside VCN
The inside VCN contains a private subnet to ensure end users can connect to application running within this VCN or have a route to Spoke VCNs via this VCN. Each Cisco ASA Virtual Firewall also has an interface within this VCN’s subnet.
- Spoke VCNs
The application/database tier spoke VCN contains a private subnet for hosting Oracle databases/Application.
- Flexible Network Load balancer
OCI Flexible Network Load Balancer provides automated traffic distribution from one entry point to multiple backend servers in your virtual cloud networks. It operates at the connection level and load balancers incoming client connections to healthy backend servers based on Layer3/Layer4 (IP protocol) data.
- Security list
For each subnet, you can create security rules that specify the source, destination, and type of traffic that must be allowed in and out of the subnet.
- Route table
Virtual route tables contain rules to route traffic from subnets to destinations outside a VCN, typically through gateways.
- In the Management VCN, you have the following route tables: Management route table attached to the management subnet which has a default route connected to internet gateway.
- In the Outside VCN, you have the following route tables: Outside route table attached to the outside subnet or default VCN for routing traffic from the Outside VCN to internet or on-premises targets.
- In the Inside VCN, you have the following route tables: Each VPN pool CIDR associated with Firewall goes to Inside interface via this route table
Note:
You can also deploy management/inside/outside subnet as part of single VCN and route traffic accordingly. - Internet gateway
The internet gateway allows traffic between the public subnets in a VCN and the public internet.
- NAT gateway
The NAT gateway enables private resources in a VCN to access hosts on the internet, without exposing those resources to incoming internet connections.
- Dynamic routing gateway (DRG)
The DRG is a virtual router that provides a path for private network traffic between a VCN and a network outside the region, such as a VCN in another OCI region, an on-premises network, or a network in another cloud provider.
- Service gateway
The service gateway provides access from a VCN to other services, such as OCI Object Storage. The traffic from the VCN to the Oracle service travels over the Oracle network fabric and never traverses the internet.
- Virtual network interface card (VNIC)
The services in OCI data centers have physical network interface cards (NICs). VM instances communicate using virtual NICs (VNICs) associated with the physical NICs. Each instance has a primary VNIC that's automatically created and attached during launch and is available during the instance's lifetime. DHCP is offered to the primary VNIC only. You can add secondary VNICs after instance launch. Set static IPs for each interface.
- Private IPs
A private IPv4 address and related information for addressing an instance. Each VNIC has a primary private IP, and you can add and remove secondary private IPs. The primary private IP address on an instance is attached during instance launch and doesn’t change during the instance’s lifetime.
- Public IPs
The networking services define a public IPv4 address chosen by Oracle that's mapped to a private IP. Public IPs have the following types: Ephemeral: This address is temporary and exists for the lifetime of the instance. Reserved: This address persists beyond the lifetime of the instance. It can be unassigned and reassigned to another instance.
- Source and destination check
Every VNIC performs the source and destination check on its network traffic. Disabling this flag enables Cisco ASA Virtual Firewall to handle network traffic that's not targeted for the firewall.
- Compute shape
The shape of a compute instance specifies the number of CPUs and amount of memory allocated to the instance. The compute shape also determines the number of VNICs and maximum bandwidth available for the compute instance.
Recommendations
- VCN
- When you create a VCN, determine the number of CIDR blocks required and the size of each block based on the number of resources that you plan to attach to subnets in the VCN. Use CIDR blocks that are within the standard private IP address space.
- Select CIDR blocks that don't overlap with any other network (in OCI, your on-premises data center, or another cloud provider) to which you intend to set up private connections.
- After you create a VCN, you can change, add, and remove its CIDR blocks.
- When you design the subnets, consider your traffic flow and security requirements. Attach all the resources within a specific tier or role to the same subnet, which can serve as a security boundary.
- Use regional subnets.
- Cisco ASA Virtual Firewall
- This architecture has standalone Firewall instances; in case of Firewall failure end user would need to re-authenticate.
- Whenever possible, deploy in distinct fault domains at a minimum or different availability domains.
- Cisco ASA Virtual Firewall Management
- If you’re creating a deployment hosted in Oracle Cloud Infrastructure, create a dedicated subnet for management.
- Use security lists or NSGs to restrict inbound access to ports 443 and 22 sourced from the internet for administration of the security policy and to view logs and events.
Considerations
When deploying Remote Access VPN architecture to access Oracle E-Business Suite or PeopleSoft workloads on OCI using Cisco ASA Virtual Firewall, consider the following factors:
- Performace
- Selecting the proper instance size, which is determined by the Compute shape, determines the maximum available throughput, CPU, RAM, and number of interfaces.
- Organizations need to know what types of traffic traverses the environment, determine the appropriate risk levels, and apply proper security controls as needed. Different combinations of enabled security controls impact performance.
- Consider adding dedicated interfaces for FastConnect or VPN services.
- Consider using large compute shapes for higher throughput and access to more network interfaces.
- Run performance tests to validate the design can sustain the required performance and throughput.
- Use these metrics as guideline:
OCI Performance specifications for 9.16 and later.
License Type 100M (ASAv5) 1GB (ASAv10) 2GB (ASAv30) 10GB (ASAv50) 20GB (ASAv100) OCI Shape Type VM.Standard2.4 VM.Standard2.4 VM.Standard2.4 VM.Standard2.8 VM.Standard2.8 Stateful inspection throughput 100 Mbps 1 Gbps 2 Gbps Coming soon Coming soon Stateful inspection throughput (multiprotocol) 100 Mbps 1Gbps 2 Gbps 2.3 Gbps 3 Gbps IPsec VPN throughput (AES 450B UDP test) 100 Mbps 550 Mbps 550 Mbps 550 Mbps 620 Mbps Connections per second 12,500 26,600 26,600 26,600 38,200 Concurrent sessions 50,000 100,000 500,000 2,000,000 4,000,000 IPSEC VPN peers 50 250 750 10,000 20,000 Cisco AnyConnect or clientless VPN user sessions 50 250 750 10,000 20,000
- Security
Deploying Cisco ASA Virtual Firewall in OCI allows full firewall services to secure data center traffic and remote workers.
- Availability
- Deploy your architecture to distinct geographic regions for greatest redundancy.
- Configure site-to-site VPNs with relevant organizational networks for redundant connectivity with on-premises networks.
- Cost
- Cisco ASA Virtual Firewall is available in bring-your-own-license (BYOL)
- For more information about how to manage licenses, see Cisco Adaptive Security Virtual Appliance (ASAv) Data Sheet and Smart Licensing for ASAv, referenced in the Explore More topic, below.
Deploy
To deploy a Remote Access VPN architecture on Oracle Cloud Infrastructure by using the Cisco ASA Virtual Firewall, perform the following steps:
Oracle recommends deploying the architecture from Oracle Cloud Marketplace.
- Deploy by using the stack in Oracle Cloud Marketplace:
- Deploy using the stack in Oracle Cloud Marketplace: Set up the required networking infrastructure as shown in the architecture diagram. See this example: Set up a hub-and-spoke network topology.
- Deploy the application (Oracle E-Business Suite or PeopleSoft or Intended Applications) on your environment.
- Oracle Cloud Marketplace has multiple listings for different configurations and licensing requirements. For example, the following listings feature bring your own licensing (BYOL). For each listing you choose, click Get App and follow the on-screen prompts:
- Deploy using the Terraform code in GitHub:
- Go to GitHub.
- Clone or download the repository to your local computer.
- Follow the instructions in the
READMEdocument.