Configure
- DNS resolution from OCI to Google Cloud
- DNS zone peering to resolve from a different Google Cloud VPCs
- DNS CNAME record to resolve from Google Cloud to OCI
Identify and configure the use case most relevant to your organization.
Use a Private DNS from OCI to Google Cloud
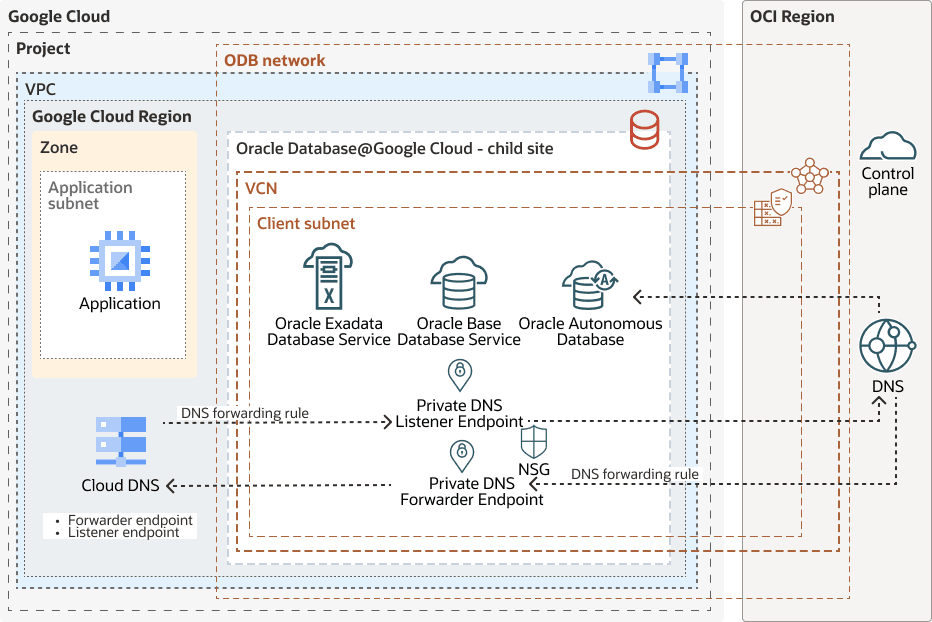
The following diagram shows DNS queries being resolved both from OCI to Google Cloud and from Google Cloud to OCI:
google-dns-forward-oci-dns-oracle.zip
This architecture enables private, policy-controlled connectivity from a Google Cloud application to Oracle database services, with DNS resolution handled using private listener and forwarder endpoints that integrate with OCI DNS and the service control plane.
- DNS private endpoint forwarder
To forward the request from the database service to a Google Cloud DNS listener endpoint, do the following:
- Create an OCI DNS forwarder endpoint.
- Associate an NSG with the DNS forwarder endpoint.
- Create the ingress and egress stateless rules.
- Resolver rules
Create domain rules in a private resolver DNS that forwards all requests to the Google Cloud DNS listener endpoint's IP address.
For more information, see the OCI DNS Resolver Endpoints and Rules documentation linked in Explore More.
Use DNS Zone Peering to Resolve from Google Cloud VPCs
The Cloud DNS forwarding zone is configured when an Oracle Database@Google Cloud is deployed. To resolve Oracle Database from multiple VPCs, create a private DNS zone with DNS peering to query the same resolver for a forwarding zone in a different VPC.
Follow these steps to configure a private Cloud DNS peering zone:
- In the Google Cloud console, go to the Create a DNS zone page.
- In Zone type, select Private.
- Enter a Zone name such as my-new-zone.
- Enter a DNS name suffix for the private zone. All records in the zone share this suffix, for example: example.private. Optionally add a description.
- Under Options, select DNS peering.
- Select the networks where the private zone must be visible.
- In Peer project, select a peer project.
- In Peer network, select a peer network.
- Click Create.
This creates an additional DNS peering zone in the peered VPC that allows it to forward queries to the OCI VCN resolver.
For more information, review the Google Cloud DNS peering documentation linked in Explore More.
Use a CNAME Record to Resolve DNS from Google Cloud to OCI
The DNS forwarder is created for Oracle Database resource names. You can create a CNAME record in your Google Cloud DNS private zone pointing to the database's FQDN resources.
For example, to create a www subdomain name
such as mydomain.com in a Google Cloud DNS, create a record set type CNAME to the canonical
name of the database (*.oraclevcn.com).
- In the Google Cloud console, go to the Cloud DNS page.
- Click the zone where you want to add a record set.
- Click Add standard.
- In DNS Name, enter www.
- For Resource Record Type, select CNAME.
- For Canonical name, enter the domain name,
followed by a period. For example,
example.com. - Click Create.
These different DNS use cases enable secure, automated, and scalable resolution across the Oracle Database@Google Cloud environments, and ensure minimal manual overhead while supporting complex enterprise topologies.
For more information, review the Google Cloud DNS create CNAME record documentation in Explore More.