About Cloud Security
Cloud security includes the following components: Oracle Cloud Infrastructure Identity and Access Management (OCI IAM), Identity Provider (IdP), Cloud Access Security Broker (CASB), Next Gen Firewall, Web Application Firewall (WAF), and Distributed Denial-of-Service (DDoS).
The following diagram shows the security model for OCI:
OCI provides a flexible cloud security model that you can integrate with on-premises or other CSP's IdP services. You can configure WAF policies for protection within OCI, while building multicloud solutions and hosting applications in OCI. OCI also provides authoritative DNS which can be applied across clouds. In multicloud solution architectures, having option to choose an IdP which is more flexible and adaptable with applications and CSPs allows you to architect the best multicloud solution.
About Cloud Interoperability
Migrate and run mission-critical enterprise workloads across Microsoft Azure and OCI to benefit from cross-cloud single sign on (SSO) and enable interoperability.
Oracle and Microsoft Azure have built more integration around identity for customers. Azure centric customers can not only benefit from low latency high bandwidth connectivity, but they can also enable cross-cloud SSO by federating users across Azure and OCI. For example, customers wanting to move business critical application like enterprise resource planning. Packaged and cloud-native applications can run in split-stack architecture with Azure Active Directory as the identity provider, with the application stack in Azure and database in OCI with Oracle Exadata Database Service.
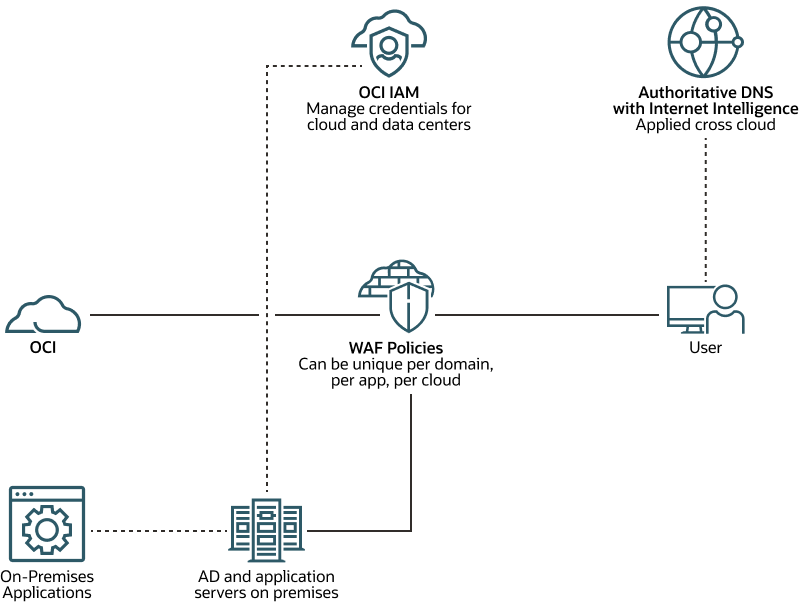
Cloud Security Landscape
The cloud security landscape includes the customer enclave and customer estate.
Whether a solution is on-premises, cloud, or multicloud, security controls remain the center of every architecture design. OCI provides customers with the flexibility to build multicloud and hybrid cloud solution architectures. You can deploy different security vendor solutions within the customer cloud enclave as well as in the whole customer estate.
OCI allows you to do the following:
- Use any third-party firewalls in your tenancy
- Use Local or Federated Authenticators with OCI IAM
- Use different services whether it's an external identity provider or a third-party SIEM solution
- Build secure and easily deployed multicloud architecture designs
- Send logs (Control Plane, Sign-on, WAF Data plane, and so on) to any SIEM solution