Understand the DDoS Layers
OCI services provide DDoS attack detection and mitigation for the different DDoS layers. Before designing your DDoS solution, review the DDoS layers and prevention services OCI provides.
Network Transport Layer (3 and 4) Protection (TCP, UDP, ICMP)
Today, all Oracle Cloud data centers have DDoS attack detection and mitigation for high volume layer 3 or 4 DDoS attacks. These DDoS protection services from Oracle Cloud help ensure the availability of Oracle network resources even under sustained layer 3 or 4 attacks.
Application Layer (7) Protection (HTTP/HTTPS)
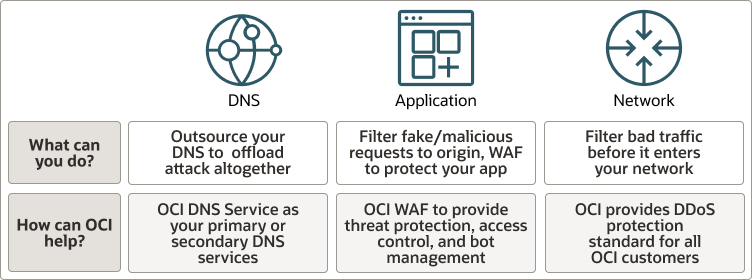
Layer 7 attacks (HTTP/HTTPS) target applications exploiting vulnerabilities and misconfigurations. The size and sophistication of these attacks are growing exponentially. Therefore, protecting applications from cyber threats, including malicious bots, cross-site scripting, SQL injection, and other vulnerabilities defined by the Open Web Application Security Project (OWASP), is vital.
About Oracle DDoS Protection
DDoS protection services on OCI applies to the network-based attack (layer 3 and 4 of the OSI Model) or what many people think of as a volume-based attack. Oracle monitors its entire address space, including Bring Your IP Address (BYOIP) for all Oracle Cloud customers. If it sees high-volume-based attacks, it has the tools and processes to mitigate and scrub the malicious traffic. Oracle is fully managing this protection for OCI customers.
DNS-based attacks are prevalent as they exist at the transport layer as part of the UDP protocol and can attack through many avenues. To help detect and mitigate these attacks, DNS Services can be deployed in OCI as a customer-owned entity behind a network load balancer, for example, to support public DNS services.
Because OCI DNS is a global anycast network of multiple data centers strategically located across various continents, it uses a mix of redundant internet transit providers for ultimate resilience and protection against DDoS attacks.
DDoS attack types and mitigations are summarized in the diagram below.
Description of the illustration ddos-attack-types-and-oci-mitigations.png
Understand the Function of OCI DDoS Prevention Services
The following services are required for OCI DDoS prevention:
- Web Application Firewalls (WAF) - Oracle Cloud
Infrastructure Web Application Firewall (WAF) is a regional-based and edge enforcement service is attached to an enforcement point, such as a load balancer or a web application domain name. WAF protects applications from malicious and unwanted internet traffic. WAF can protect any internet facing endpoint, providing consistent rule enforcement across a customer's applications.
There are two types of OCI WAF solutions: WAF Edge Policy and WAF Firewall Policy. The WAF Edge Policy is used for enforcing policies at the edge, whereas a WAF Firewall Policy is associated to Application Load Balancers (ALBs). WAF Edge enforces WAF policies prior to entering an organization’s VCN.
-
Network Load Balancer (NLB) - The Oracle Cloud Infrastructure Flexible Network Load Balancing service (Network Load Balancer) provides automated traffic distribution from one entry point to multiple backend servers in your virtual cloud network (VCN). It operates at the connection level and load balances incoming client connections to healthy backend servers based on layer 3 and layer 4 (IP protocol) data. The service offers a load balancer with your choice of a regional public or private IP address that is elastically scalable and scales up or down based on client traffic with no bandwidth configuration requirement. In OCI, the NLBs work in an asymmetrical hashing manner. This hashing approach would require a unique designation for NGFW deployed with them using source and destination NAT. Symmetric hashing would remove the requirement for NAT on NGFW behind NLBs.
- Flexible Load Balancer (FLB) - The Oracle Cloud Infrastructure Load Balancing service provides automated traffic distribution from one entry point to multiple servers reachable from your virtual cloud network (VCN). The service offers a load balancer with your choice of a public or private IP address, and provisioned bandwidth.
- Next Generation Firewalls (NGFW) - A next-generation firewall is the latest generation of firewall technology, leveraging traditional firewall services coupled with advanced layer 7 filtering, threat detection/prevention (DDoS), deep packet inspection, and intrusion detection/prevention features.
- TLS/SSL Certificate - A TLS/SSL certificate is a digital certificate that authenticates a website's identity and enables an encrypted connection.
There are two main types of certificates: standard certificates and wildcard certificates. A standard single domain SSL certificate secures one domain name. A. wildcard SSL certificate secures your domain and an unlimited number of first-level subdomains. In general, wildcard certificates are considered less secure since the compromise of the certificate will lead to a larger set of resources impacted whereas a standard single domain certificate is more secure because if there is a compromise, only the resources using the certificate are impacted.