Learn About the Cloud Roadmap Stages
The goal of this cloud-adoption roadmap is to help you migrate your on-premises access management system to Oracle Identity Cloud Service, and integrate your cloud and on-premises applications with the single sign-on provided by Oracle Identity Cloud Service.
This roadmap has four stages. The process of migrating from one stage to another is unique because you have your own business priorities and timelines. The roadmap contains the minimal requirements that you must meet for each stage to be able to migrate to the next stage.
Understand Stage 1
In this stage, you have segregated environments for your on-premises and cloud applications. These applications aren't integrated for authentication purposes. Users must sign in to access the on-premises applications, and then sign in again to access the cloud applications, through different authentication flows.
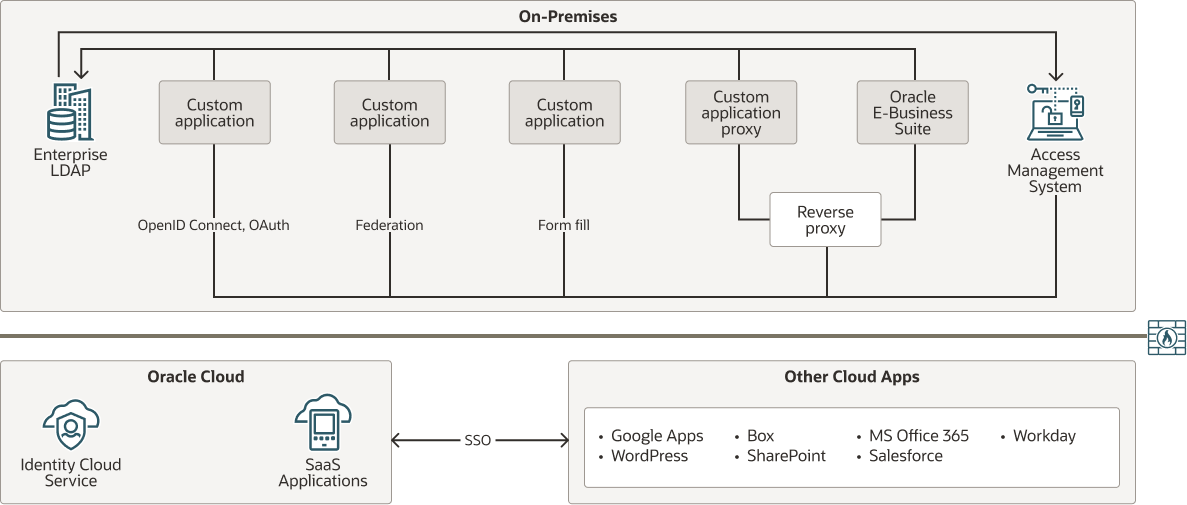
Description of the illustration cloud-roadmap-stage-1.png
Understand Stage 2
In this stage, you use Oracle Identity Cloud Service to establish single sign-on (SSO) between the on-premises and cloud applications.
If you don't want to affect your users by changing how they sign in to their on-premises applications, then you can use Security Assertion Markup Language (SAML) to integrate your on-premises access management system with Oracle Identity Cloud Service. The access management system acts as the identity provider and Oracle Identity Cloud Service functions as the service provider.
When users try to access a cloud application that was integrated with Oracle Identity Cloud Service, Oracle Identity Cloud Service delegates authentication to the on-premises access management system. The access management system presents its sign-in page, and users submit their credentials to the system.
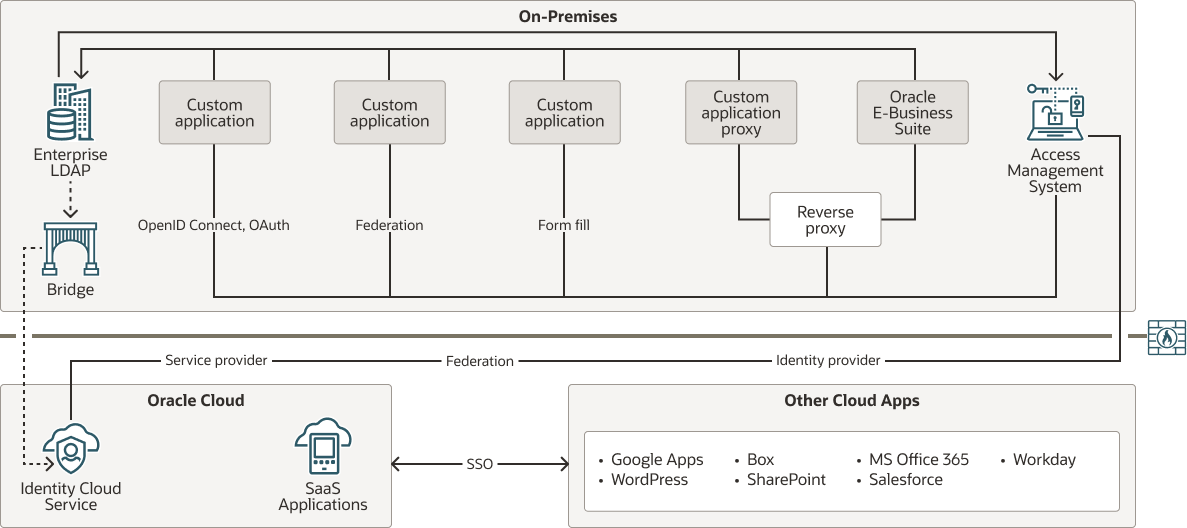
Description of the illustration cloud-roadmap-stage-2.png
Alternatively, if you want your users to access their on-premises applications by signing in to Oracle Identity Cloud Service, then you change the trust relationship between the on-premises access management system and Oracle Identity Cloud Service. That way, Oracle Identity Cloud Service functions as the identity provider and the access management system acts as the service provider. When users try to access a cloud application that was integrated with Oracle Identity Cloud Service, Oracle Identity Cloud Service authenticates the user. If the user then tries to access an on-premises application that was integrated with the on-premises access management system, the system delegates authentication to Oracle Identity Cloud Service.
By using Oracle Identity Cloud Service as an identity provider, you can leverage its features, such as those listed in stage 4. You can also customize the Oracle Identity Cloud Service Sign In page or brand this page to follow your company's standards. This way, you minimize the effect of the changes in the authentication flow for the users.
Understand Stage 3
In this stage, you directly integrate your on-premises applications with Oracle Identity Cloud Service.
You should identify the integration methods that Oracle Identity Cloud Service supports to integrate your applications for single sign-on purpose, such as the following:
- App Templates, for applications that are listed in the App Catalog.
- Federation, for a Security Assertion Markup Language (SAML) application, where your application is a service provider and Oracle Identity Cloud Service is an identity provider.
- OpenID Connect, for an application that supports OpenID Connect.
- EBS Asserter, for an Oracle E-Business Suite application.
- Software Development Kit (SDK), for an application in which you have access to the source code.
- WebGate, for a WebGate-protected application.
- Secure Form Fill, when OpenID Connect, OAuth, SDKs, or SAML don't apply to your application.
- App Gateway, for an enterprise application that's supported by the gateway.
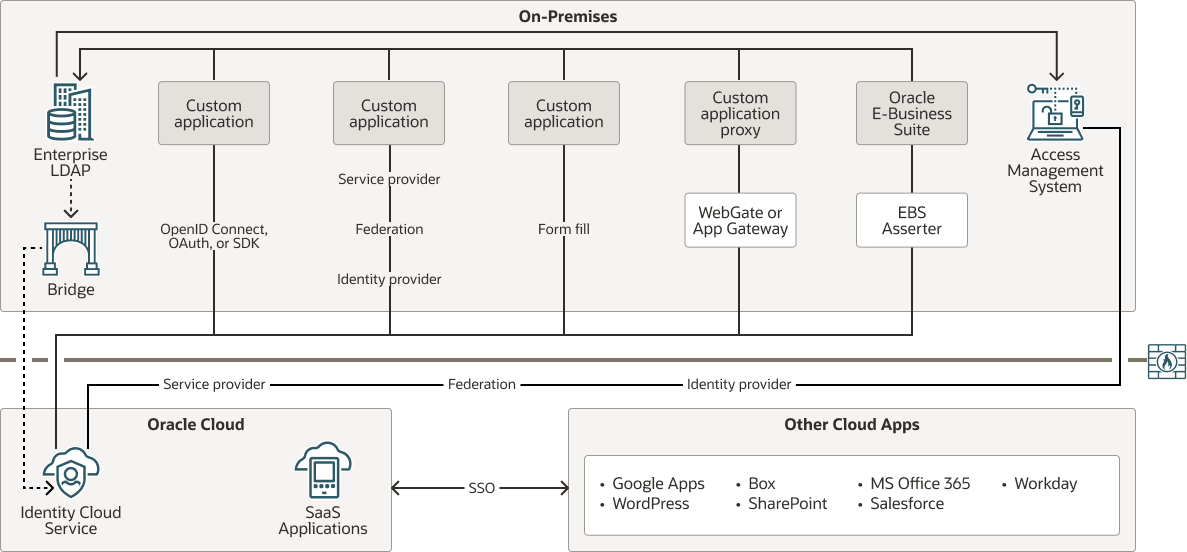
Description of the illustration cloud-roadmap-stage-3.png
You should evaluate the effort required to migrate your applications from an on-premises access management system to Oracle Identity Cloud Service. Also, you may not be able to migrate some of your applications, so these applications remain dependent upon your access management system.
Understand Stage 4
In this stage, the on-premises applications no longer depend upon the access management system.
You can disconnect Oracle Identity Cloud Service from the on-premises access management system, and start to leverage Oracle Identity Cloud Service features. Here are a few such features:
- Adaptive Security: Provides strong authentication capabilities based on your users’ behavior within Oracle Identity Cloud Service. When it’s activated, Adaptive Security can analyze a user’s risk profile based on historical behavior, such as too many unsuccessful sign-in and Multi-Factor Authentication (MFA) attempts.
- Sign-in policies: Administrator-defined criteria that allow sign-on or prevent a user from signing in to Oracle Identity Cloud Service.
- MFA: Requires two factors to verify a user’s identity. The first factor is a prompt for user name and password. The second factor is another verification consisting of either additional information or a second device to verify the user’s identity and complete the sign-in process. The two factors work together to add another layer of security.
- Account recovery: Helps users access their accounts if they have trouble signing in, they’re locked out, or they forget their passwords. Administrators can configure three account recovery factors: security questions, email, and text messages.
- Social sign-on: Users can use their social accounts to sign in to Oracle Identity Cloud Service.
Because Oracle Identity Cloud Service now functions as your access management system, it's important that you evaluate your on-premises enterprise directories. If you need the directories, then continue synchronizing your users from your Active Directory (AD) enterprise directory or your enterprise Lightweight Directory Access Protocol (LDAP) to Oracle Identity Cloud Service. To do this, use one of the following bridges:
- AD Bridge: Provides a link between your AD enterprise directory structure and Oracle Identity Cloud Service. Oracle Identity Cloud Service can synchronize this directory structure so that any new, updated, or deleted user records are transferred into Oracle Identity Cloud Service. The bridge polls AD for any changes to these records and brings these changes into Oracle Identity Cloud Service. So, if a user is deleted in AD, then this change is propagated into Oracle Identity Cloud Service.
- Provisioning Bridge: Provides a link between your enterprise LDAP, such as Oracle Internet Directory, and Oracle Identity Cloud Service. Through synchronization, account data that’s created and updated directly on the LDAP is pulled into Oracle Identity Cloud Service and stored for the corresponding users. Any changes to these records are transferred into Oracle Identity Cloud Service.
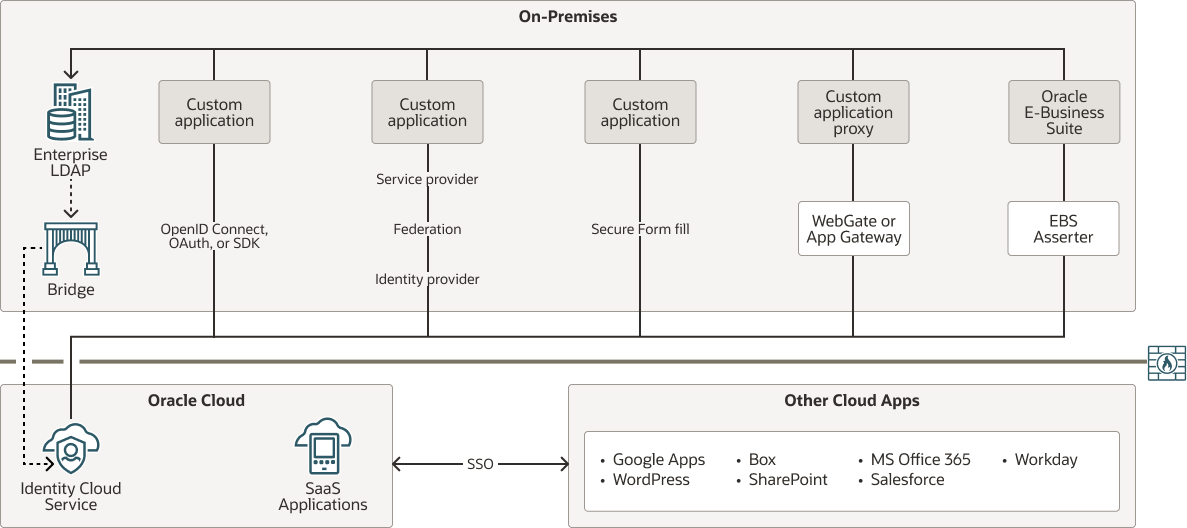
Description of the illustration cloud-roadmap-stage-4.png
For applications that can't be migrated and remain dependent upon your on-premises access management system, change the trust relationship between the access management system and Oracle Identity Cloud Service. That way, Oracle Identity Cloud Service functions as the identity provider and the access management system acts as the service provider.