Configure the Terraform Execution Environment
The Terraform execution environment includes the layout of the folders and Terraform configuration files required to build the multitier network topology.
About the Terraform Execution Environment
The layout of the Terraform execution environment is designed for modularity and future growth.
The directories and files that contain your Terraform configuration constitute the execution environment. Each subdirectory represents a Terraform module. Together, the subdirectories make up a reusable library of resources.
The following directory structure represents the execution environment that you build in this solution.
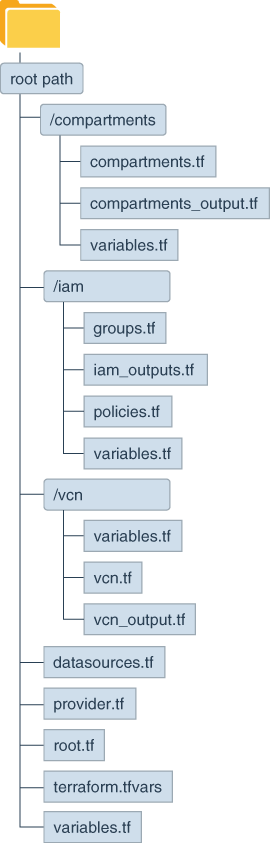
Description of the illustration local_directory_structure.png
The entire configuration is within a root directory that has a name of your choice. This directory must be empty when you begin.
After you create the configuration, the root directory contains the following directories and files:
- The
compartmentsdirectory contains the configuration parameters for the compartments. - The
iamdirectory contains the configuration parameters for the policies and groups. - The
vcndirectory contains the configuration parameters for the virtual cloud network and the gateways. - The following files are in the root directory:
datasources.tfdetermines the number of availability domains in the region and gets their names.provider.tfdefines the parameters of the Terraform providers to be used.root.tfdefines the modules that Terraform should execute.terraform.tvarsdefines the values of the variables that you pass to Terraform.variables.tfdeclares the variables that the modules in the configuration use.