Learn About Network Topologies for Oracle Database@Google Cloud
- Single VPC connectivity
- VPC peering connectivity
- Shared VPC peering connectivity
- Hub-and-spoke connectivity
- Multiple VPC connectivity
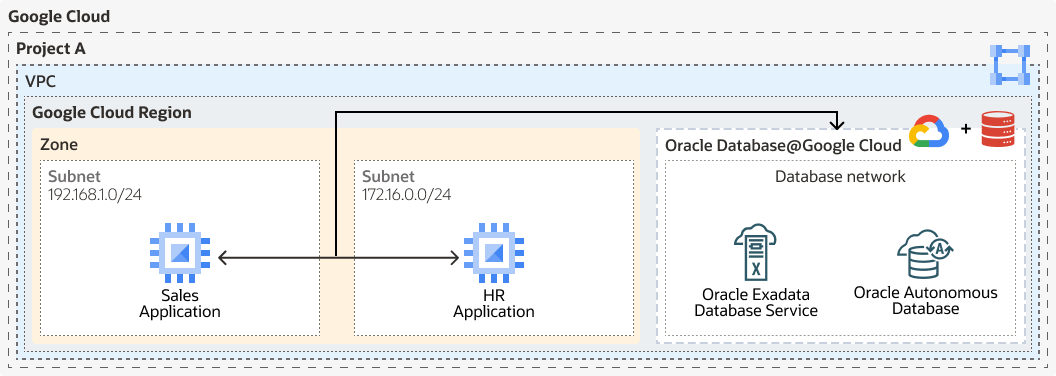
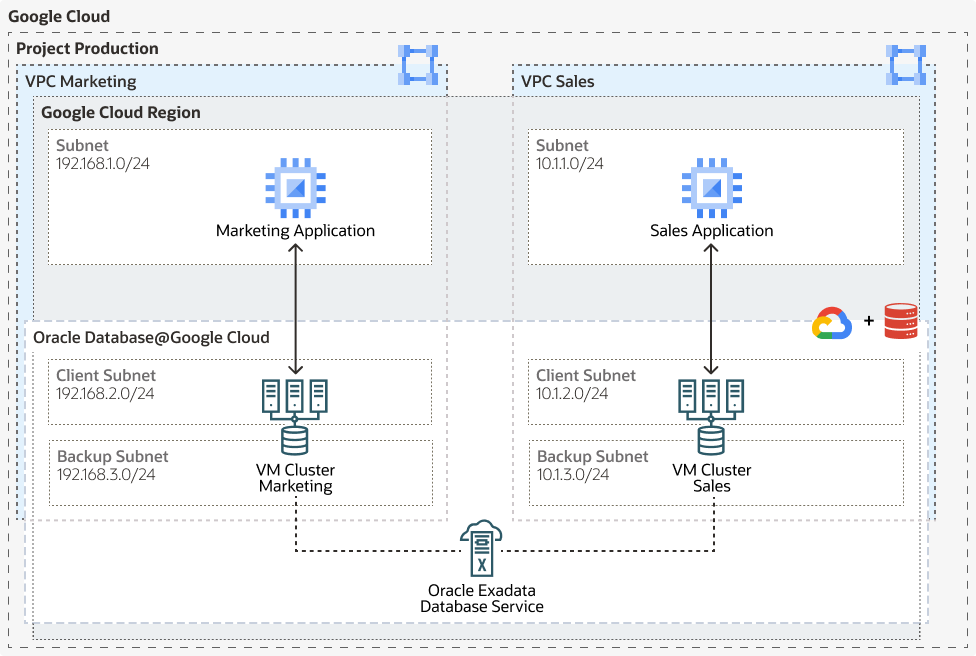
About Single VPC Topology
The following architecture shows a single VPC topology:
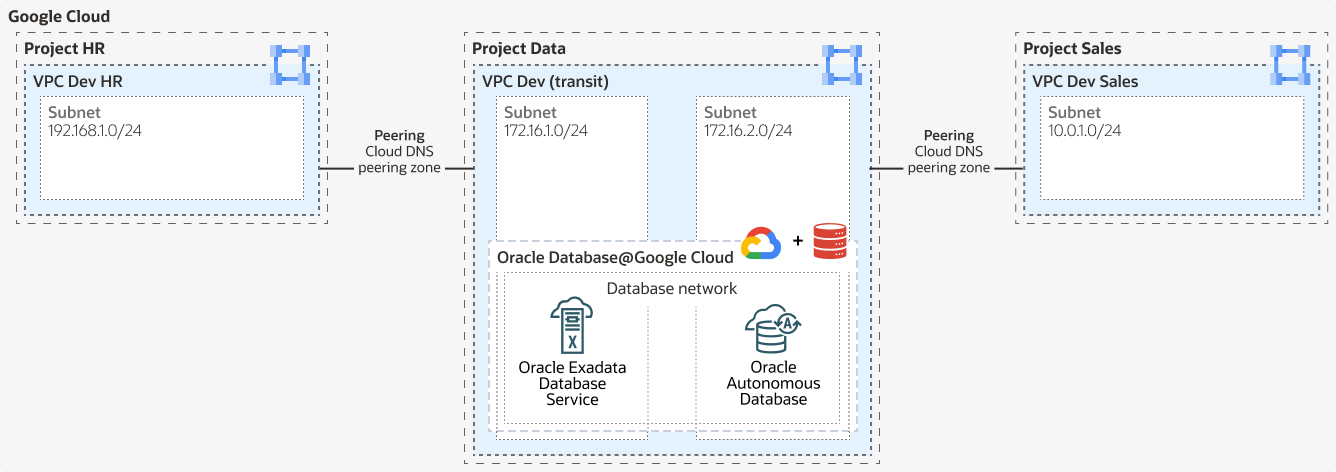
About VPC Peering Topology
VPC peering topology connects your applications in one VPC to the database in another VPC. VPC peering connects two VPCs so that resources in each network can communicate with each other in the same project, a different project of the same organization, or even different projects of different organizations.
Tip:
If you choose this topology, consider that VPC peering incurs costs.About Shared VPC Topology
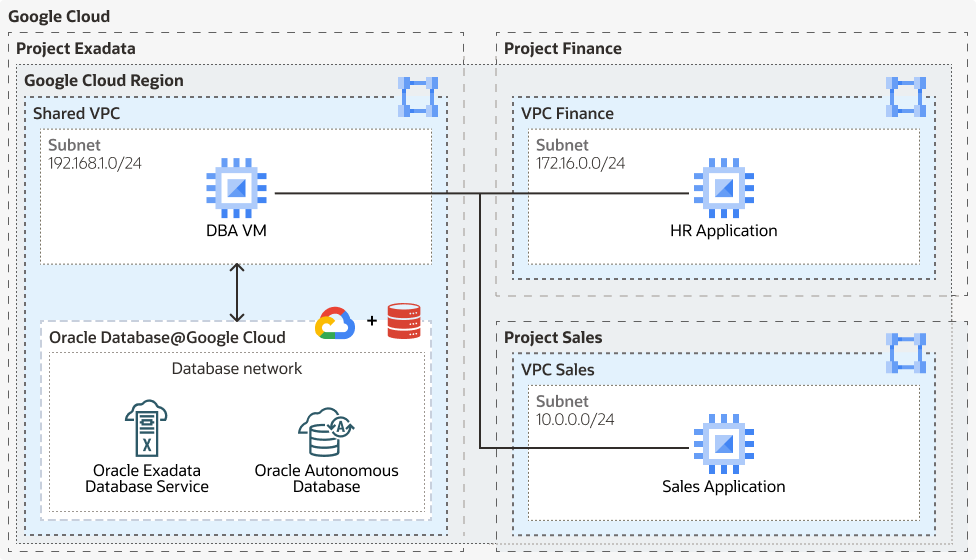
Shared VPCs simplify networking configuration in Google Cloud. Service owners, like database users, use the network configuration defined by their network teams, instead of manually configuring the networks between different resources. It reduces the need to enable and configure VPC Peering and associated configurations.
Shared VPC allows you to manage a single, centralized VPC in a host project, while granting each team controlled access to deploy their Oracle Databases in isolated service projects. This enables secure, consistent networking policies (firewalls, routes, DNS) across all environments, simplifies inter-service communication, and avoids VPC sprawl or duplicated configurations.
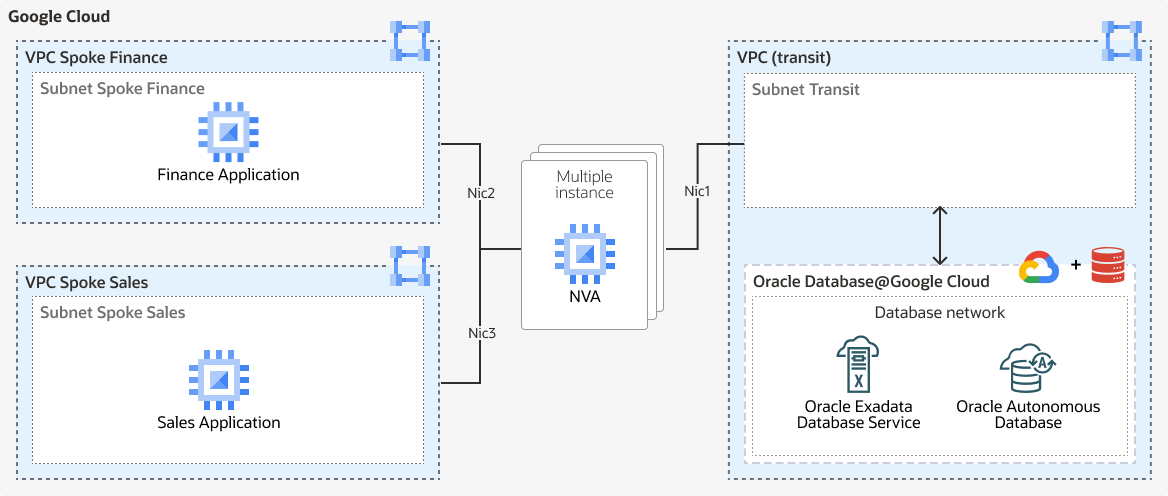
About Hub-and-Spoke Topology
To create the VNIC for Oracle Database@Google Cloud connectivity, you must create a transit subnet in the transit VPC. As a centralized point of connectivity, the NVA facilitates communication between applications and databases.
About Multiple VPC Topology
To isolate workloads on Oracle Exadata Database Service at the VM Cluster level, deploy multiple clusters in isolated Project VPCs.
google-multiple-vpc-arch-oracle.zip
You must ensure the following:
- Multiple VM clusters share the same Oracle Exadata Database Service infrastructure.
- Each VM cluster is connected to a different VPC.
- Oracle Exadata Database Service infrastructure and VM clusters are part of different projects.
Topology Components
- Google Cloud region
A Google Cloud region is a geographical area that contains data centers and infrastructure for hosting resources. Regions are made up of zones, which are isolated from each other within the region.
- Google Virtual Private Cloud
Google Virtual Private Cloud (VPC) provides networking functionality to Compute Engine virtual machine (VM) instances, Google Kubernetes Engine (GKE) containers, database services, and serverless workloads. VPC provides global, scalable, and flexible networking for your cloud-based service.
- Google Cloud zone
A zone in Google Cloud is a deployment area for resources within a region. Zones are isolated from each other within a region, and are treated as a single failure domain.
- Google Cloud project
A Google Cloud Project is required to use Google Workspace APIs and build Google Workspace add-ons or apps. A Cloud Project forms the basis for creating, enabling, and using all Google Cloud services, including managing APIs, enabling billing, adding and removing collaborators, and managing permissions.
- ODB network
The ODB network creates a metadata construct around the Google Virtual Private Cloud (VPC), serving as the foundation for all database provisioning. The ODB network enables support for Shared VPC by abstracting and centralizing network configuration - such as subnets, CIDR ranges, and routing. This allows network administrators to manage connectivity independently of database deployment workflows.
- Google Cloud Shared VPC
Shared Virtual Private Clouds (VPCs) allow organizations to connect resources from multiple projects to a common VPC network in a Host project. Organization administrators can delegate management of applications to Service Project administrators while maintaining centralized control over network resources. This simplifies the configuration and allows these resources to communicate securely and efficiently with each other using an internal IP address from the Shared VPC network.