Plan the Deployment
Plan an architecture that aggregates multiregion log data and streams it to a security information and event management (SIEM) platform.
Design the Deployment
Use the following basic steps to deploy an architecture that aggregates log data from Oracle Cloud Infrastructure (OCI).
- Design the regional architecture
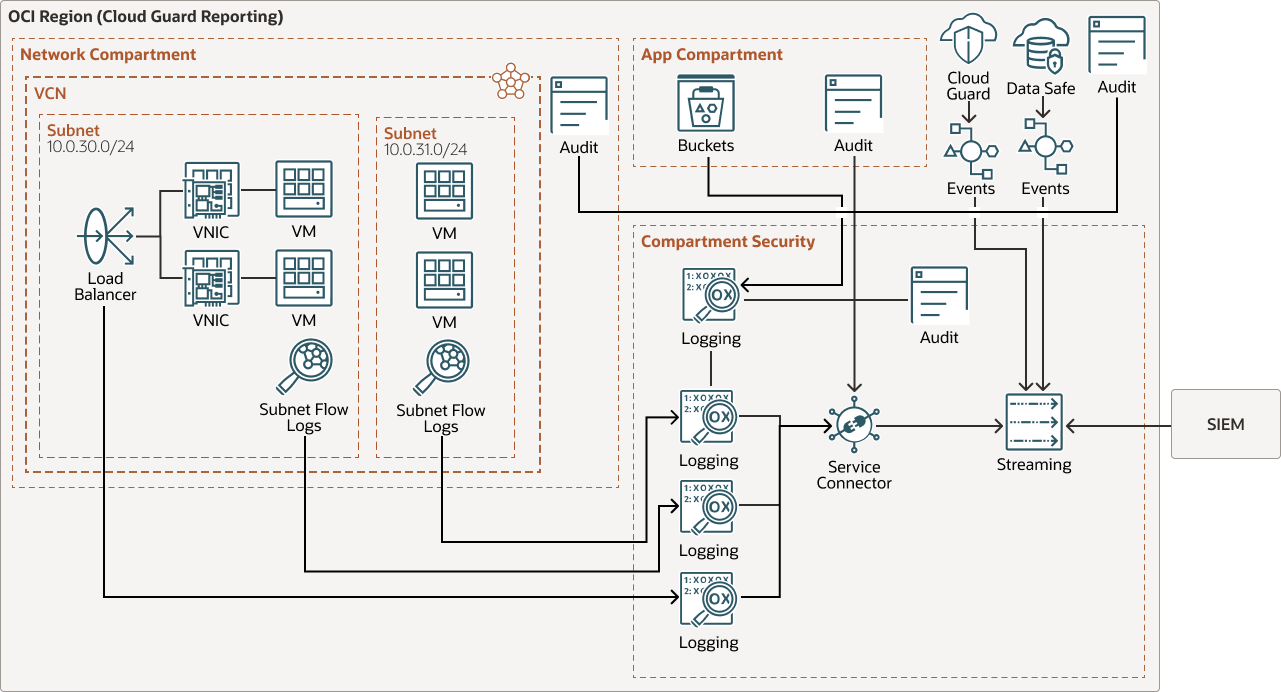
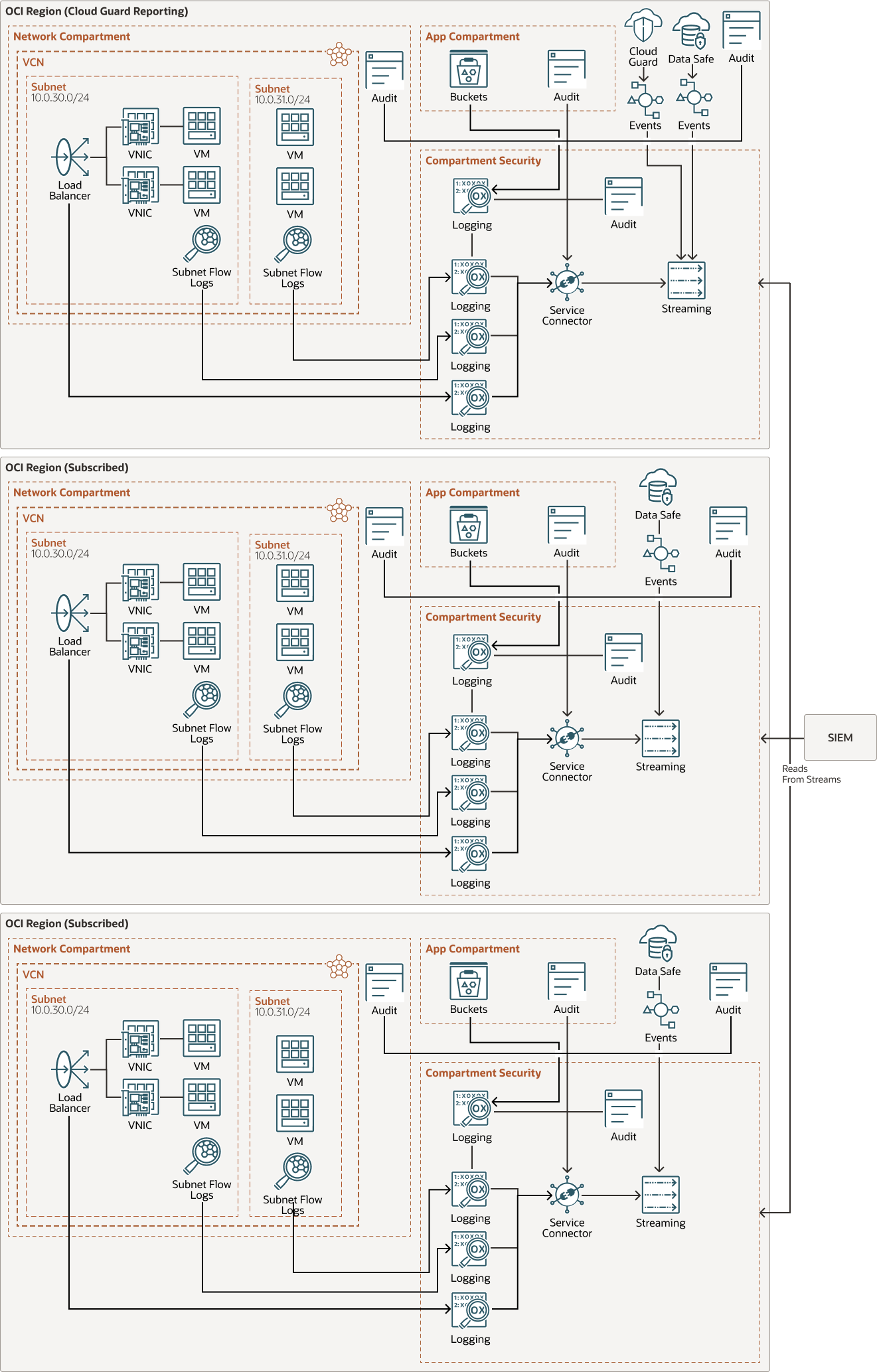
The architecture below aggregates Oracle Cloud Infrastructure Audit logs, service logs, and security events from Oracle Cloud Guard and Oracle Data Safe by using Oracle Cloud Infrastructure Events in the Cloud Guard reporting region.
- Deploy the architecture across regions
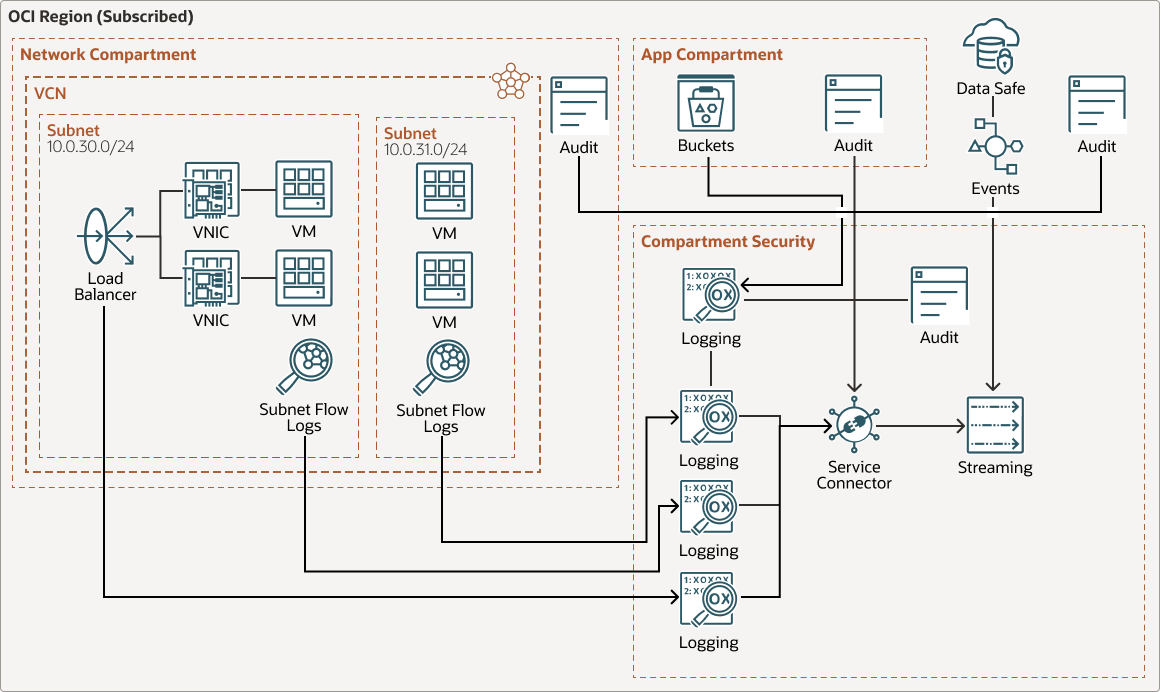
To ensure that you’re aggregating all logs and security events, deploy a similar architecture in all regions that your tenancy is subscribed to. While Oracle Cloud Guard consolidates problems in the Cloud Guard reporting region, Oracle Cloud Infrastructure Logging and Oracle Data Safe are regional services that report in from a specific region.
Below is the architecture for a region that is not in the Oracle Cloud Guard reporting region.
- Configure your SIEM to read the data stream in each region
After each region is set up, you’ll need to configure your SIEM solution to read from the OCI stream in each region.
- Create access management policies for your SIEMs
You can read data from an OCI stream by using the OCI APIs or by using Oracle Cloud Infrastructure Streaming’s Kafka compliant APIs. Each API has a specific authentication method:
Authentication Type OCI API Kafka Compliant API API Signing Key: an RSA key pair in the PEM format (min 2048 bits) Yes Auth Tokens: Oracle-generated token strings to authenticate with 3rd party APIs Yes Instance Principal: IAM service feature that enables instances to be authorized actors (or principals) to perform actions on service resources Yes Oracle recommends using an instance principal, where applicable, to avoid storing long-lived tokens to your SIEM.
The SIEM needs the following Oracle Cloud Infrastructure Identity and Access Management (IAM) permissions to read from the OCI stream. To follow a least-privilege model, use the policy shown in the following examples:
- The first policy is for an OCI IAM user:
Allow group SIEM to use stream-pull in compartment <compartment> - The second policy is for an instance principal:
Allow dynamic-group SIEMInstances to use stream-pull in compartment <compartment>
- The first policy is for an OCI IAM user:
Considerations
When implementing this architecture design, consider the following:
- If your SIEM doesn’t have native Kafka support or a native plugin, you can push logs to the SIEM’s HTTPS API Endpoint by using Oracle Functions. To do this, add another regional Oracle Cloud Infrastructure Service Connector Hub that reads from the regional stream and whose target is a function.
- To ensure collection for all Oracle Cloud Infrastructure Audit compartment logs, use the
Include _Audit in subcompartmentsflag on your root compartment in the OCI Service Connector Hub. - To collect Oracle Cloud Guard findings across the entire tenancy, attach an Oracle Cloud Guard target to the root compartment. Then, create an Oracle Cloud Guard OCI event at the root compartment to capture all Oracle Cloud Guard findings in the tenancy.
- For long-term OCI log retention (cold storage), create a second OCI Service Connector Hub to read from the regional stream with an Oracle Cloud Infrastructure Object Storage bucket as the target. By using Object Lifecycle Management to manage your object storage and archive storage data, you can reduce your storage costs and the amount of time you spend manually managing data.
- Use Oracle Cloud Infrastructure Monitoring and Alarms to monitor logging ingestion up-time.
- The table below shows some common tools and their pattern:
Tooling OCI APIs (Plugin) Kafka Compliant Function Code Splunk Yes QRadar Yes Microsoft Sentinel Yes Google Chronicle Yes Datadog Yes ELK Yes LogStash Yes