Learn About the Cyber-Security Pillar in OCI
Use the OCI CIS Secure Landing Zone as a starting point to quickly get up and running with the Cyber-Security pillar's components, designs, and best practices.
The following diagram illustrates this reference architecture.
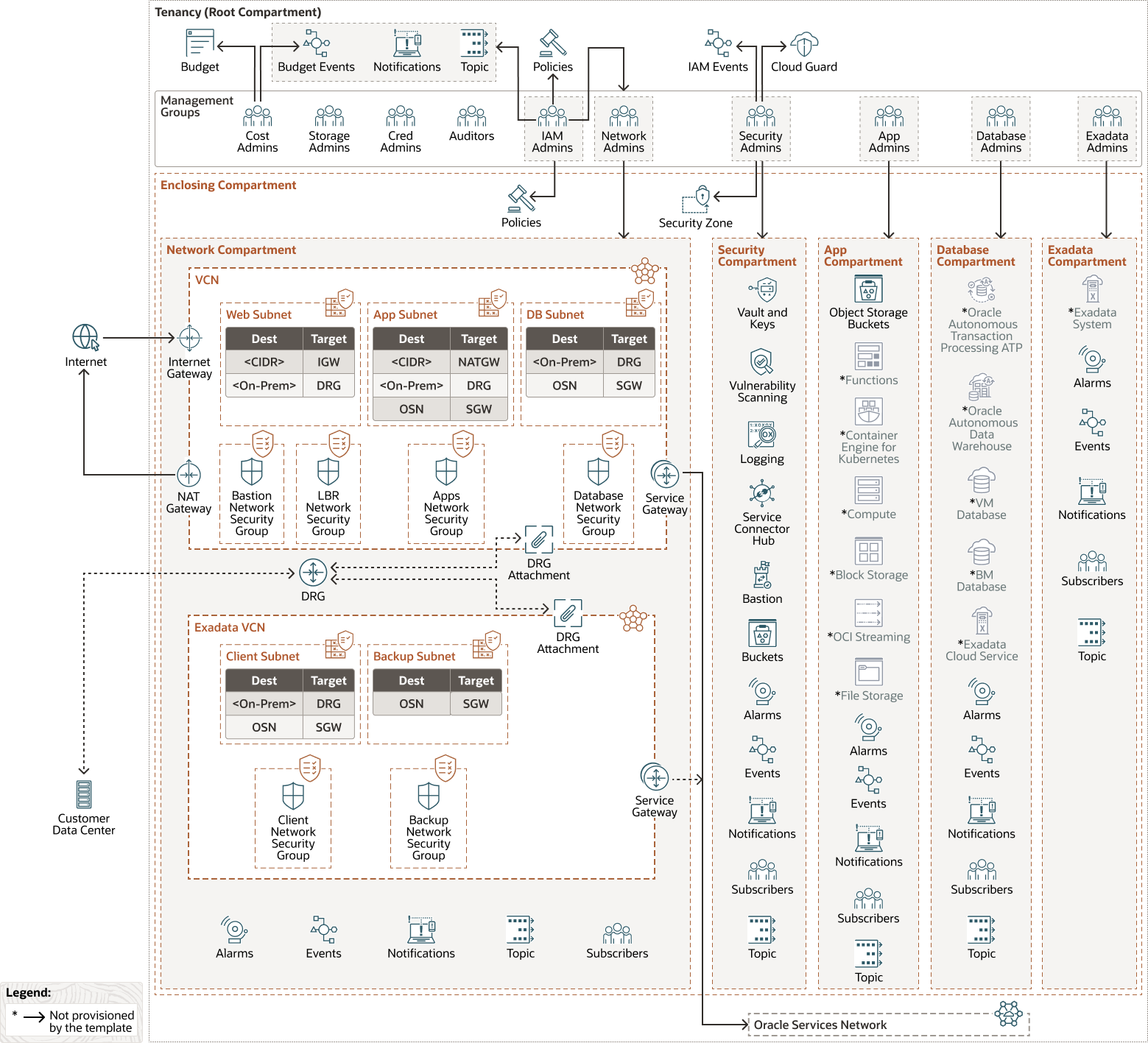
Description of the illustration oci-cis-landingzone.png
oci-cis-landingzone-oracle.zip
See the Deploy a secure landing zone that meets the CIS Foundations Benchmark for Oracle Cloud solution linked in the Before You Begin section to deploy a new tenancy in OCI which includes the mechanisms, structures, and protections largely outlined using various services described in this solution.
Setting up cyber security includes setting up preventative and detective controls.
About Traditional Cyber Security
Traditional disaster recovery ensures the "Availability" portion of the CIA Triad and assumes that data integrity is "as intended". For example, transaction replication of unstructured data and databases within a single region or across multiple regions. The typical use case for traditional disaster recovery is a general regional or physical hardware outage of some sort. Like-for-like hardware (physical or virtual) are set up in a different location and like-for-like replicated data is matched to the redundant version of hardware with the assumption that the data integrity was not compromised. The OCI Maximum Availability Architecture (MAA) is a great example of how Oracle can help you achieve any level of RPO or RTO objectives relative to Oracle Database technologies. Often traditional disaster recovery is not designed in such a manner that is intended to address purposeful threat actors. A traditional disaster recovery architecture addresses failure associated with physical hardware in some capacity.
Traditional backup and recovery primarily focuses on maintaining data integrity and facilitating the availability of data with "as-intended" integrity. You can't expect hardware availability or data integrity maintenance without intervention. By storing multiple copies of data in various states at different points-in-time, RPOs can be surgically addressed. A limitation of traditional backup and recovery is that it assumes that data that was backed up is good data and was backed up in an "as intended" state.
Recommendations for Preventative Controls
Logical Protection
Carefully design your tenancy's compartment structure to provide isolation of critical workloads and data. This allows for distributed administration of your cloud resources and creates a solid foundation for enforcing "least-privilege" access and "separation of duties". Group your cloud resources to align with your operational model to distribute and limit role-based administrative privileges and also limit full tenancy administrative rights to a break-glass model.- For instance, only allow your networking team to manage the networking components while limiting database management to a DBA team.
- Restrict the tenancy administrator privilege to a very few accounts that are vaulted, highly-restricted, closely-monitored, and not used in regular daily activities.
The Oracle Cloud Infrastructure Identity
and Access Management (OCI IAM) policy engine allows you to create extremely granular policies to limit access. For example, you can allow a group the ability to create and manage Object Storage buckets that are commonly used to store backups, but not allow them to delete objects or buckets. You can allow Storage_Admins to manage buckets in {tenancy OCID} where request.permission != ‘DELETE’.
You can then assign separate identity domains to control access to specific compartments. For example, you can create a vault compartment to store copies of buckets, block volumes, and manual database backups and assign a separate identity domain to control access. This restricts anyone who has access to the main environment to use the same credentials to access the vaulted compartment, providing isolation and protection of these assets.
Next, secure all accounts that have access to OCI using multi-factor authentication (MFA), including both federated and local OCI accounts in the following ways:
- Federated accounts are typically controlled through identity providers including Microsoft-Azure Active Directory, Ping, or Okta all of whom have multiple methods for enforcing MFA.
- OCI IAM also supports multiple methods for enabling MFA including security questions, mobile app passcode, mobile app notification, text message (SMS), email, bypass code, and duo security.
You can define policies to control how MFA is enabled with multiple conditions, risk factors and actions to further strengthen user authentication. Enabling MFA for all federated and local OCI accounts makes it significantly more difficult for an attacker to compromise an account and access your tenancy. The sample IAM policies configured in the Deploy a secure landing zone that meets the CIS Foundations Benchmark for Oracle Cloud solution has specific examples.
Network Protection
OCI provides multiple capabilities to do help you implement controls to achieve a secure network. The VCN provides the foundation for all networking in OCI. By default, there is no network access to your tenancy. You must implement services to allow for ingress and egress, specify the direction, ports, and protocols that are allowed. Follow these recommendations to configure network protection to prevent an attacker from gaining access to your network and disrupt them from moving laterally if they happen to gain access:
- Separate systems containing sensitive information, including databases, into their own VCNs. You can granularly control access between and within a VCN and achieve the first layer of segmentation.
- You can achieve further segmentation and isolation between subnets and cloud resources using Security Lists (SL) and Network Security Groups (NSGs). Security lists operate at the subnet level and control ingress and egress for the subnet. NSGs provide isolation at the VNIC layer and allow you to implement micro-segmentation between individual VNIC equipped resources.
- When you create a VCN, determine the number of CIDR blocks required and the size of each block based on the number of resources that you plan to attach to subnets in the VCN. Use CIDR blocks that are within the standard private IP address space and don't overlap with any other network (in OCI, your on-premises data center, or another cloud provider) to which you intend to set up private connections. After you create a VCN, you can change, add, and remove it's CIDR blocks.
When you design the subnets, consider your traffic flow and security requirements. Attach all the resources within a specific tier or role to the same subnet, which can serve as a security boundary. Use regional subnets whenever possible to be able to take advantage of the multiple availability domains within a region.
- Use OCI IAM policies to give permission to security lists to ensure that only those parties with responsibility for maintaining the lists based on their separation of duties can administer them.
Tip:
As a best practice, restrict ingress and egress traffic to only source and destination ports required for a given application and to exercise the principle of least privilege. Generally, world access to sensitive ports such as RDP and SSH should be tightly restricted. - Use NSGs to define a set of ingress and egress rules that apply to specific VNICs. Oracle recommends using NSGs over security lists because NSGs enable you to separate the VCN's subnet architecture from the security requirements of your application.
- Consider deploying an OCI Network Firewall using a hub-and-spoke topology by using a DRG to control, restrict, and monitor traffic between VCNs and on-premises networks.
- Use OCI gateways to enable internet ingress and egress as well as allow private access to OCI services in the following ways:
- An Internet Gateway allows ingress traffic with the NAT gateway enabling egress. Both can be locked down in a variety of ways to restrict traffic and provide a more secure perimeter.
- A Service Gateway is used to connect your cloud resources to OCI services privately; ensuring all traffic stays within the OCI network.
- Use FastConnect to provide a high-speed, low-latency, private connection between your tenancy and your internal network. You can configure all traffic to and from the tenancy to pass over this connection such that it traverses your existing network security stack. This effectively converts your OCI tenancy into a private enclave where you control all network access using a single connection. FastConnect uses a layer-2 connection and can be configured with MACsec encryption to provide additional security.
- If you're not using a self-deployed Bastion host, consider using OCI's Managed Bastion Host Services as ephemeral hardened images instantiated to broker access to OCI compute resources.
Infrastructure and Application Protection
OCI provides several capabilities for protecting the infrastructure resources in your tenancy including:
- DDoS Protection: OCI provides default protection of the network against volumetric attacks, and Oracle also has solutions for providing layer-3 and 4 protection at the tenancy level.
- Web Application Firewall (WAF): Fronting your public-facing applications with the OCI WAF provides protection against many web-based attacks. OCI WAF should be deployed using OCI Load Balancers to inspect and protect web based traffic against OWASP attacks such as SQL Injection. Also consider restricting traffic by country based on usage and access requirements.
- Vulnerability management can be achieved through the combination of the Vulnerability Scanning (VSS) and OS Management (OSM) services.
- VSS can scan all your compute nodes and containers for both open ports and CVSS based vulnerabilities.
- OSM provides a way to identify missing OS and security patches and to automate patching across your Oracle Linux and Windows compute nodes.
- OCI IAM Policies: Configure policies to remove specific abilities even from administrative accounts. For example, you can remove the ability to delete storage (Object, Block, and File) and backups and limit tenancy administrative rights to a break-glass account that can be vaulted. Enabling versioning renders your Object Storage buckets immutable and therefore resistant to ransomware. Oracle-managed backups for Block Volumes and Oracle Database services renders these immutable. They are stored in a separate, Oracle-controlled enclaves that allow no direct connectivity from your tenancy. You learn more about enclaves in the cyber-resilience pillar section that follows.
- OCI Vault: Vault provides an HSM backed, full lifecycle management service for keys and secrets if you want to manage your own encryption keys and other critical credentials. There is an option for a virtual private vault that provides you with a dedicated HSM partition.
- Security Zones: Use security zones to provide guardrails for the creation and movement of cloud resources that include preventing the creation of public buckets, assignment of public IP addresses, and require that customer-managed encryption keys are used to secure all storage and many more. Define Custom Security Zones to meet your specific security posture and regulatory compliance requirements. Select the policy statements that are relevant for your needs and the target compartment. Policies can be specified through the OCI Console UI, CLI, API, or Terraform.
- Oracle Database Vault: A mandatory access control mechanism that can be enabled within Oracle Database deployments both on-premise and in the cloud. Configure Oracle Database Vault Realms so that database administrators don't have access to production data unnecessarily.
- Oracle Audit Vault and Database Firewall: Consider using the Oracle Audit Vault and Database Firewall to protect on-premises Oracle Database installations from SQL injection attacks and to centralize and protect audit data for Oracle Database installations.
- Oracle Database Transparent Data Encryption (TDE): To enable TDE, configure a software keystore and encrypt columns and tablespaces based on security requirements.
OCI provides several services and capabilities that can assist you in properly securing your tenancy against these threat vectors. However, using these services and capabilities can't guarantee that your tenancy is immune from compromise as there is no such thing as perfect security. Cyber criminals are constantly improving their tactics and techniques. They only need to get it right once to get in, while you have to be perfect all the time to keep them out.
Recommendations for Detective Controls
You can use OCI's services and capabilities to detect signs of ransomware-style threats in your tenancy. The OCI CIS Landing Zone is the quickest way to lay down a tenancy with a quickstart secure foundation which adheres to the OCI CIS Security Benchmarks and a majority of the best practices for cyber security as outlined in this document.
Logging and Analytics
The OCI Logging service is a highly scalable and fully-managed single pane of glass for all the logs in your tenancy. Logging provides access to logs from OCI resources and includes critical diagnostic information that describe how resources perform and are accessed. There are three kinds of logs:
Audit logs: Logs related to events emitted by the OCI Audit service and are available from the Logging Audit page or are searchable on the Search page alongside the rest of your logs. OCI Audit logs all actions taken within your tenancy whether using the console, command line, or the API. The contents of the audit log are not directly available and can't be altered or deleted. You can search the audit log from the console and turn entries into events that can then be sent using the Notifications service to your security teams.
Service logs: Emitted by OCI-native services, such as API Gateway, Events, Functions, Load Balancer, Object Storage, and VCN flow logs have predefined logging categories that you can enable or disable on your respective resources.
Custom Logs: Logs that contain diagnostic information from custom applications, other cloud providers, or on-premises environments. Custom logs can be ingested through the API, or by configuring the Unified Monitoring Agent. You can configure an OCI compute instance or resource to directly upload Custom Logs through the Unified Monitoring Agent. Custom logs are supported in both a virtual machine and bare metal scenario.
Logs are indexed in the system, and searchable through the Console, API, and CLI. You can view and search logs on the Logging Search page. When searching logs, you can correlate across many logs simultaneously. For example, you can view results from multiple logs, multiple log groups, or even an entire compartment with one query. You can filter, aggregate, and visualize your logs.
All logs are encrypted both in-flight and at-rest and also when they are archived or transferred to storage such as Object Storage. Logging integrates with the Service Connector Hub which can be used to forward logs to Object Storage for longer or archive storage, or to the Streaming service for ingestion by your SIEM and other security analytics tools.
Consider using the OCI Logging Analytics service, if you don't have a SIEM and want to perform analytics on your logs. The Logging Analytics service is an OCI-native solution that lets you index, enrich, aggregate, explore, search, analyze, correlate, visualize, and monitor all log data from your applications and system infrastructure on cloud or on-premises. The service provides multiple ways of gaining operational insights from your logs. You can:
- Use the log explorer UI
- Aggregate log information into dashboards
- Use the APIs to ingest and analyze data
- Integrate with other OCI services
The interactive visualizations provide several possibilities to slice and dice the data. Use the Cluster feature to reduce millions of log entries down to a small set of interesting log signatures and make it easy to review. The Link feature enables you to analyze logs in a transaction or identify anomalous patterns using the grouped view.
Security Posture Management
While logging is an important control to understanding what is occurring within your environment, it only provides disparate data points about the activity within it. Having the ability to obtain contextual information about the potential threats is critical to being able to protect your environment from ransomware and other threats. Traditional SIEM platforms provide the correlation and analysis that many security operations teams rely on. However, these systems can be difficult to use and expensive to implement and maintain. OCI has a cloud-native service that addresses many of the capabilities of these solutions.Cloud Guard
A cloud-native service that helps you monitor, identify, achieve, and maintain a strong security posture on OCI. Use the service to examine your resources for configuration-related security weakness, and your operators and users for risky activities. Upon detection, Cloud Guard can suggest, assist, or take corrective actions, based on your configuration.
Cloud Guard distills the audit log and configuration information into actionable security-related events; reducing the number of raw events that you would normally have to sift through. You can take action on these events within the Cloud Guard console and forward them to the Streaming service to send to your SIEM service.
Clone and customize the default recipes provided by Oracle to create custom detector and responder recipes. These recipes enable you to specify what type of security violations generate a warning and what actions are allowed to be performed on them. For example, you might want to detect Object Storage buckets that have visibility set to public.
Apply Cloud Guard at the tenancy level to have the broadest scope and to reduce the administrative burden of maintaining multiple configurations. You can also use the Managed List feature to include or exclude certain configurations from detectors.
Cloud Guard Threat Detector
Automatically triages user behavior using machine learning, data science, and threat intelligence to reduce alert noise. It uses Oracle's threat intelligence data, monitors targeted behavior models aligned with MITRE ATT&CK techniques, and applies data science to help discover compromised environments quickly. It uses known attacker behaviors and motivations to identify threat markers and then combines those markers into a scoring algorithm based on attack progression.
Threat Detector also analyzes the OCI administrator's actions using machine learning and other techniques to help alert security operators of rogue users—someone whose credentials have been stolen or their allegiance compromised. Ensure that this detector is enabled and that the Rogue User alert is being sent to the proper people on your team.
Log Insight Detector
To extend Cloud Guard to cover other potential security issues beyond the default detectors, you can compose custom detection rules using the flexible query language from the OCI Logging service. These custom detector recipes support searching of and correlation across security signals in Logging service data. Search covers multiple log sources, such as audit logs, application logs, Fusion Apps logs, and other custom logs. When configured thresholds are met, the Logging service sends alerts to Cloud Guard. Those alerts then appear in Cloud Guard as problems.
Database Security
Databases are the primary target of most ransomware attacks since they typically contain the information most important to the operation of your organization. Having real-time insights into the security posture of your databases is critical to protecting them from ransomware and other attacks.Data Safe is a unified control center for your Oracle Databases which helps you understand the sensitivity of your data, evaluate risks to data, mask sensitive data, implement and monitor security controls, assess user security, monitor user activity, and address data security compliance requirements.
Data Safe provides the following set of features for protecting sensitive and regulated data in Oracle Databases with a single, easy-to-use management console:
- Security Assessment
- User Assessment
- Activity Auditing
- Data Discovery
- Data Masking
Tip:
Oracle recommends that you register all your Oracle Databases in OCI with Data Safe to identify, categorize, and prioritize risks, and generate comprehensive assessment reports on security parameters, security controls in use, and user roles and privileges.Database Vault
Oracle Database Vault implements data security controls within an Oracle Database to restrict access to application data by privileged users. Reduce the risk of insider and outsider threats and address compliance requirements, including separation of duties.
Secure new and existing Oracle Database environments without the need for costly and time-consuming application changes. Database Vault is compatible with enterprise architectures, including Oracle Real Application Clusters (Oracle RAC), Oracle GoldenGate, and Oracle Data Guard, all without the need to deploy additional servers and agents. Oracle recommends that you implement Database Vault for all of your OCI databases. Oracle Database Vault offers the following features:
- Realms: Block unauthorized access to sensitive data by creating restricted application environments within your Oracle Database. Oracle Database Vault security controls also help organizations address compliance with data privacy laws and standards such as the European Union General Data Protection Regulation (EU GDPR), Payment Card Industry Data Security Standard (PCI-DSS), and numerous other regulations that require strong internal controls on access, disclosure, or modifications to sensitive information.
- Command Rules: Prevent malicious or accidental changes that disrupt operations by privileged user accounts. Command controls prevent unauthorized commands such as
DROP TABLEorALTER SYSTEMoutside of specific maintenance windows. - Trusted Paths: Use factors like client IP address, program, username, and time of day to enforce zero-trust access to data and data operations. Since an attacker can't easily use a stolen account to access sensitive data, Oracle Database Vault can block unauthorized access to sensitive data and generate high value alerts notifying administrators of suspicious data access activity and help stop data theft before it happens.
- Separation of Duties: Enforce checks and balances on privileged users, preventing attackers from disabling security controls, creating rogue users, and accessing sensitive data by leveraging credentials from a single privileged account.
Events and Notifications
You may want to be alerted to additional events that occur within your OCI tenancy that aren't covered by the described services. The Events and Notifications services allow you to identity these events and send notifications to your team when the event occurs.OCI Events
Enables you to create automated notifications based on the state changes of resources throughout your tenancy. OCI services emit events, which are structured messages that indicate changes in resources.
You work with events by creating rules. Rules include a filter you define to specify events produced by the resources in your tenancy. Rules must also specify an action to trigger when the filter finds a matching event. Actions are responses you define for event matches. When the filter in the rule finds a match, the Events service delivers the matching event to one or more of the destinations you identified in the rule. Destination services for events are Notifications, Streaming, and Functions.
OCI Notifications
Notifies you when an event is triggered with your OCI resources. You can configure alarms, event rules, and service connectors, to send you human-readable messages through supported endpoints, including email and text messages (SMS). You can also automate tasks through custom HTTPS endpoints and OCI Functions. You can also directly publish messages.
The OCI Audit, Logging, Cloud Guard, and Data Safe services are all integrated with Events and Notifications to enable you to notify your operations and security teams of security-related issues in your tenancy.
See the Deploy a secure landing zone that meets the CIS Foundations Benchmark for Oracle Cloud solution linked in the Before You Begin section to deploy a new tenancy in OCI which includes the mechanisms, structures, and protections largely outlined using various services described here.