Set Up the Infrastructure to Deploy Oracle Modern Risk and Finance Applications
Oracle’s suite of Modern Risk and Finance applications enable you to proactively manage compliance, risk, treasury, finance, and the front office. They offer a unified platform based on a common data model that combines regulatory, compliance, risk, balance sheet management, and customer data to help you focus on profitability.
- Move your infrastructure to the cloud with minimal-to-zero need to change your application architecture.
- Lower the total cost of ownership by reducing over-provisioning and moving from fixed to variable costs.
- Reduce the risk of interruptions to business operations, and increase your responsiveness and customer satisfaction.
Architecture
This reference architecture shows the infrastructure required to deploy Oracle Modern Risk and Finance applications in the cloud.
The middleware tier, application tier, and database tier are in separate private subnets, which can be accessed through a bastion host. External access to the applications is through a public load balancer. Every tier has redundant resources distributed in different fault domains, ensuring a highly available application environment across the stack.
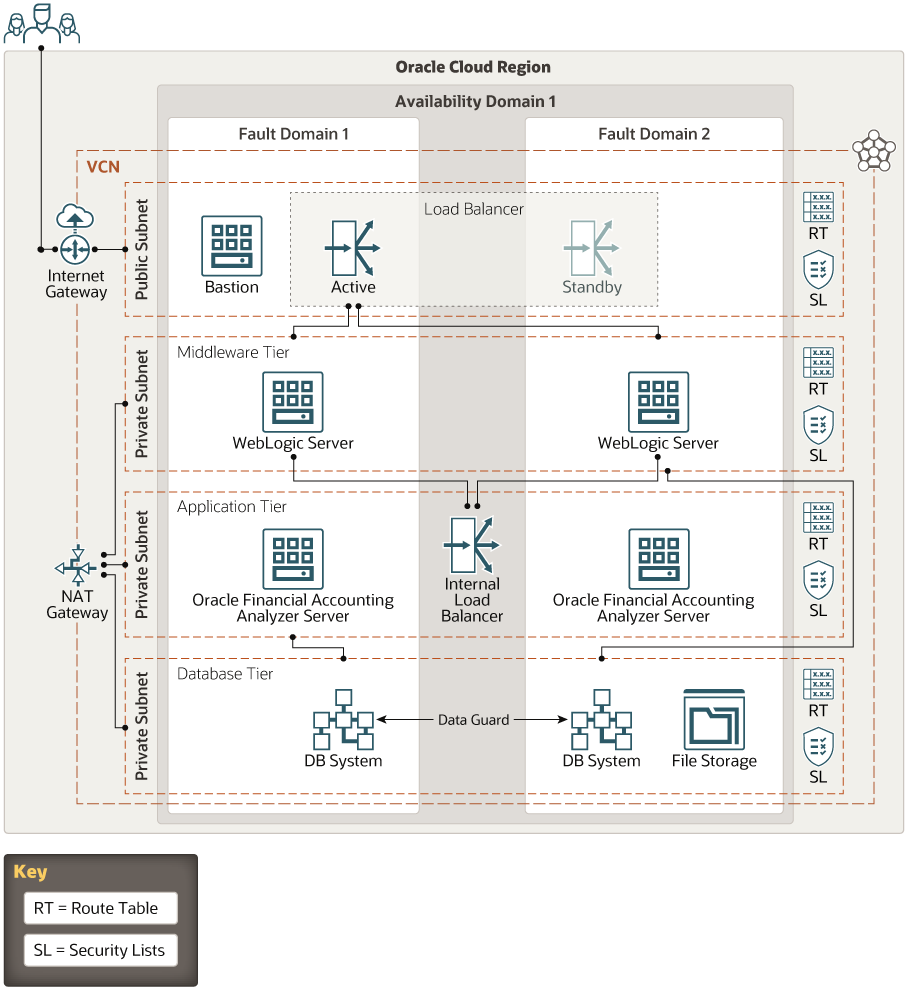
Description of the illustration ofsaa-oci-png.png
The architecture has the following components:
- Region
An Oracle Cloud Infrastructure region is a localized geographic area that contains one or more data centers, called availability domains. Regions are independent of other regions, and vast distances can separate them (across countries or even continents).
- Availability domain
Availability domains are standalone, independent data centers within a region. The physical resources in each availability domain are isolated from the resources in the other availability domains, which provides fault tolerance. Availability domains don’t share infrastructure such as power or cooling, or the internal availability domain network. So, a failure at one availability domain is unlikely to affect the other availability domains in the region.
- Fault domain
A fault domain is a grouping of hardware and infrastructure within an availability domain. Each availability domain has three fault domains with independent power and hardware. When you distribute resources across multiple fault domains, your applications can tolerate physical server failure, system maintenance, and power failures inside a fault domain.
- Virtual cloud network (VCN) and subnet
A VCN is a customizable, software-defined network that you set up in an Oracle Cloud Infrastructure region. Like traditional data center networks, VCNs give you complete control over your network environment. A VCN can have multiple non-overlapping CIDR blocks that you can change after you create the VCN. You can segment a VCN into subnets, which can be scoped to a region or to an availability domain. Each subnet consists of a contiguous range of addresses that don't overlap with the other subnets in the VCN. You can change the size of a subnet after creation. A subnet can be public or private.
- Load balancer
The Oracle Cloud Infrastructure Load Balancing service provides automated traffic distribution from one entry point to multiple application servers in the backend. The load balancer provides a front end to the application servers, isolating and preventing unnecessary or unauthorized access to the internal layers.
When you create the application layer in cluster mode, you can configure the load balancer to distribute traffic across the servers in your Oracle WebLogic Server domain.
- Bastion host
The bastion host is a compute instance that serves as a secure, controlled entry point to the topology from outside the cloud. The bastion host is provisioned typically in a demilitarized zone (DMZ). It enables you to protect sensitive resources by placing them in private networks that can't be accessed directly from outside the cloud. The topology has a single, known entry point that you can monitor and audit regularly. So, you can avoid exposing the more sensitive components of the topology without compromising access to them.
- Application tier
The Oracle Financial Accounting Analyzer server is the node that hosts the product binaries, multi-threaded services for metadata management, and batch-processing frameworks.
- Middleware tierThe middleware tier contains the following components:
- Oracle WebLogic Server
- Oracle Data Integrator: Required only if using Oracle Financial Services Data Integration Hub
- Database tierThe database (DB) system is an Oracle database with up to three pluggable databases (PDBs) for the following components:
- Configuration schema and application schema
- Oracle Analytics: Required if you want to deploy the repository for Oracle Analytics in the same database
- Oracle OLAP (Online Analytical Processing) and Oracle Hyperion Essbase: Required only for deployments that use the OLAP feature of Oracle Financial Services Analytical Applications
You can either install Oracle Database on compute instances, or provision Oracle Cloud Infrastructure Database systems as shown in the architecture. Use the high-performance edition.
- NAT gateway
The NAT gateway enables private resources in a VCN to access hosts on the internet, without exposing those resources to incoming internet connections.
- Internet gateway
The internet gateway allows traffic between the public subnets in a VCN and the public internet.
Recommendations
Your requirements might differ from the architecture described here. Use the following recommendations as a starting point.
- VCN
When you create a VCN, determine the number of CIDR blocks required and the size of each block based on the number of resources that you plan to attach to subnets in the VCN. Use CIDR blocks that are within the standard private IP address space.
Select CIDR blocks that don't overlap with any other network (in Oracle Cloud Infrastructure, your on-premises data center, or another cloud provider) to which you intend to set up private connections.
After you create a VCN, you can change, add, and remove its CIDR blocks.
When you design the subnets, consider your traffic flow and security requirements. Attach all the resources within a specific tier or role to the same subnet, which can serve as a security boundary.
Use regional subnets.
- Load balancer
The smallest shape for the load balancer is 100 Mbps. Depending on the number of simultaneous connections needed and the throughput, you can use larger shapes. We recommend that you use DNS names, because the load balancer’s IP address can’t be reserved.
- Compute instances
This architecture uses a single compute instance in each fault domain. But depending on your workload, you can choose to deploy the components of the application on different compute instances.
- DB systems
For a small deployment, a single DB instance with two OCPUs is sufficient. This architecture uses a deployment with two DB systems, one of which is a standby.
- Storage
The compute instances in this architecture use regular block storage; no extra performance is required.
- Network connectivity
To enable your administrators to manage the environment, you can connect the cloud topology to your existing on-premises infrastructure by using site-to-site IPSec VPN connections or dedicated FastConnect circuits.
If the cloud topology needs to be segregated from the on-premises infrastructure, you can deploy a bastion host to secure management access to the resources in the private subnets.
Considerations
- Performance
You can scale the performance of the architecture as needed. You can use larger shapes and add more instances to redistribute the load.
- Security
Except for the bastion host (if present) and load balancers, all the components should be placed in private subnets.
- Availability
In this architecture, redundant resources are provisioned in each layer, ensuring high availability. You can change the architecture to distribute resources across multiple regions. For added data protection, you can also use the database backup and volume backup features of Oracle Cloud Infrastructure.
- Cost
You can adjust the compute instances and database systems to use larger shapes when the load increases and shrink to smaller shapes when the load reduces.
More Information
- Oracle Financial Services Analytical Applications resources
- Oracle Financial Services Analytical Applications documentation
- Best practices framework for Oracle Cloud Infrastructure
- Learn about protecting your cloud topology against disasters
- Learn about architecting a highly available cloud topology