About Configuring SSO Between Azure AD and Oracle Access Manager for Oracle E-Business Suite
Now, you will complete the steps necessary to register a new federated service provider in Azure AD, register a new identity provider (E-Business Suite) in Oracle Access Manager, and make any required configuration changes to accomplish federated SSO authentication with Azure AD and E-Business Suite using Oracle Access Manager.
Understand the Azure AD and E-Business Suite Federation Flow
Before proceeding with configuration, you should understand the Azure AD and E-Business Suite Federation Flow.
Description of the illustration ebiz-federation-flow.png
In this scenario, users access E-Business Suite with credentials stored in Azure AD. This access is achieved through a federated authentication setup with the SAML 2.0 protocol, in which Azure AD is the identity provider (IDP) and E-Business Suite is the service provider (SP). Because Oracle Access Manager is deployed in front of E-Business Suite for SSO, it’s also the component that provides the federation capabilities to E-Business Suite. This section provides the required steps for implementing identity federation between Azure AD and Oracle Access Manager.
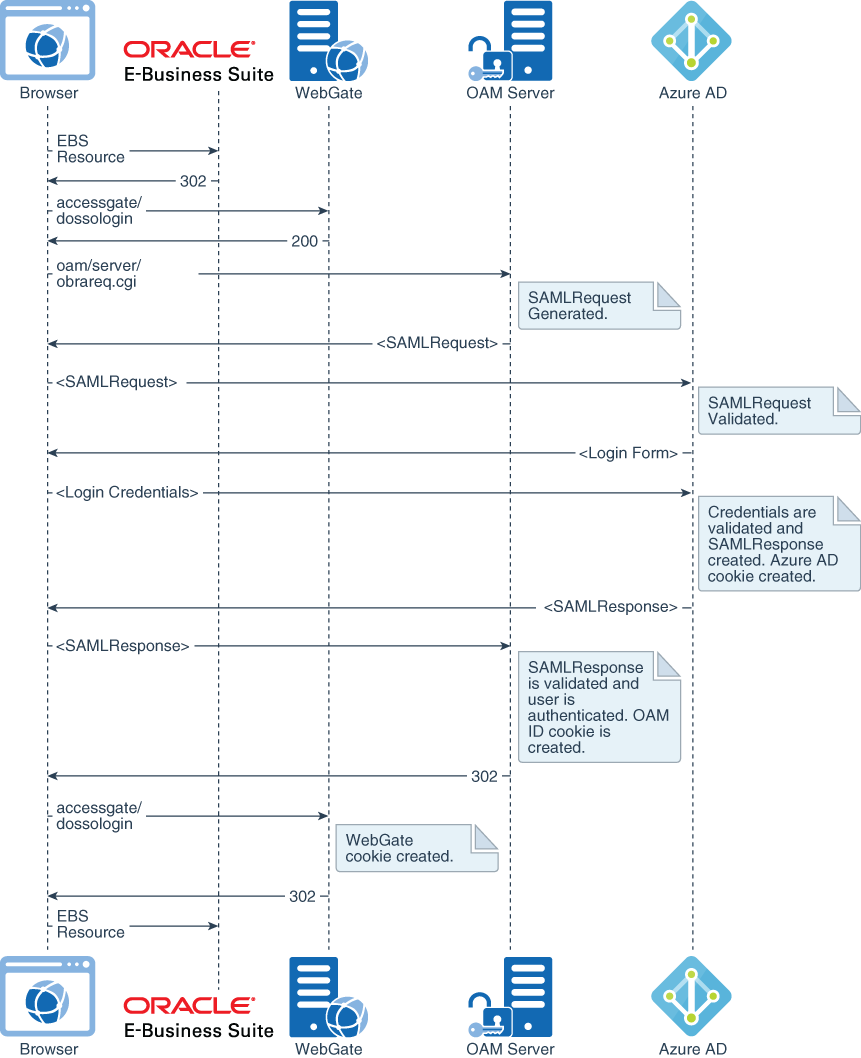
Note that we are mostly interested in a federation flow that’s initiated on access to an E-Business Suite-protected endpoint. In SAML protocol terms, this is known as a service-provider-initiated (SP-initiated) flow, and is illustrated in Figure 2. In that flow, Oracle Access Manager (OAM) Server detects access to an E-Business Suite-protected resource, creates an authentication request (SAMLRequest), and redirects the browser to Azure AD for authentication. Azure AD challenges the user for credentials, validates them, creates a SAMLResponse as a response to the received authentication request, and sends it to Oracle Access Manager. In turn, Oracle Access Manager validates the assertion and asserts the user identification information embedded in the assertion, granting access to the protected resource.
Note that the configuration presented in this section also accounts for identity-provider-initiated (IdP-initiated) flow, where a request is initially made to Azure AD SAML intersite URL, which in turn sends an unsolicited SAMLResponse to the Oracle Access Manager Server.
SP-initiated single logout (where the logout flow is initiated by E-Business Suite) is also supported by the presented configuration. At the time this paper was initially published, IDP-initiated single logout (where the logout flow is initiated by the Azure portal) is not supported. See the “Known Issue” section at the end of this document for details.
Configure Azure AD as the Identity Provider
First, you need to configure Azure AD as the Identity Provider.
Assign Users to the Application
Next, assign users to the application. After Azure AD receives an authentication request from the application, only those users that you assign to the application can log in.