Configure SSO Between Oracle Integration and Fusion Applications
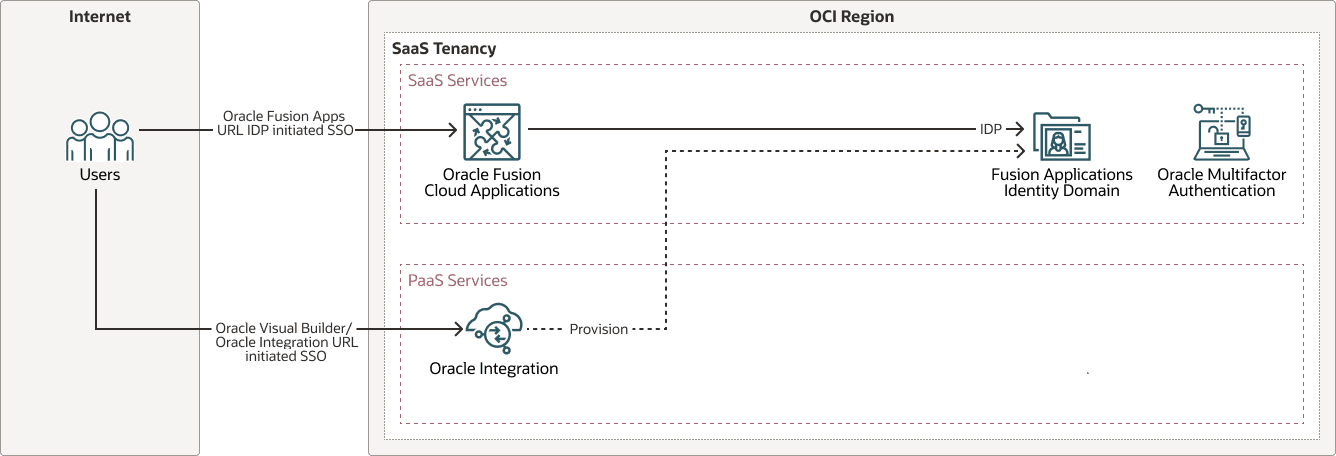
Configure SSO with Oracle Fusion Cloud Applications Identity Domain
As the Oracle Fusion Cloud Applications identity domain is an Oracle App type, it supports extension use cases at no extra cost and simplifies operations and governance. This approach removes the need for additional OCI IAM identity domains, reducing licensing costs and administrative overhead. The Fusion Applications identity domain is designated as the identity provider (IdP).
Once provisioned, all Fusion Applications users are automatically available for assignment to the Oracle Integration instance. SSO is enabled between Oracle Fusion Cloud Applications and Oracle Integration, and Oracle Integration can be configured to securely call Fusion Applications APIs using OAuth.
To create an Oracle Integration instance, log in to the OCI console using this identity domain. When users access the Oracle Integration URL, they are redirected to the Fusion Applications identity domain for authentication.
The following diagram illustrates the authentication flow:
For instructions on provisioning Oracle Integration within the Fusion Applications identity domain, see Provision a Oracle Cloud Integration Service into the Fusion Applications Identity Domain in the Explore More section.
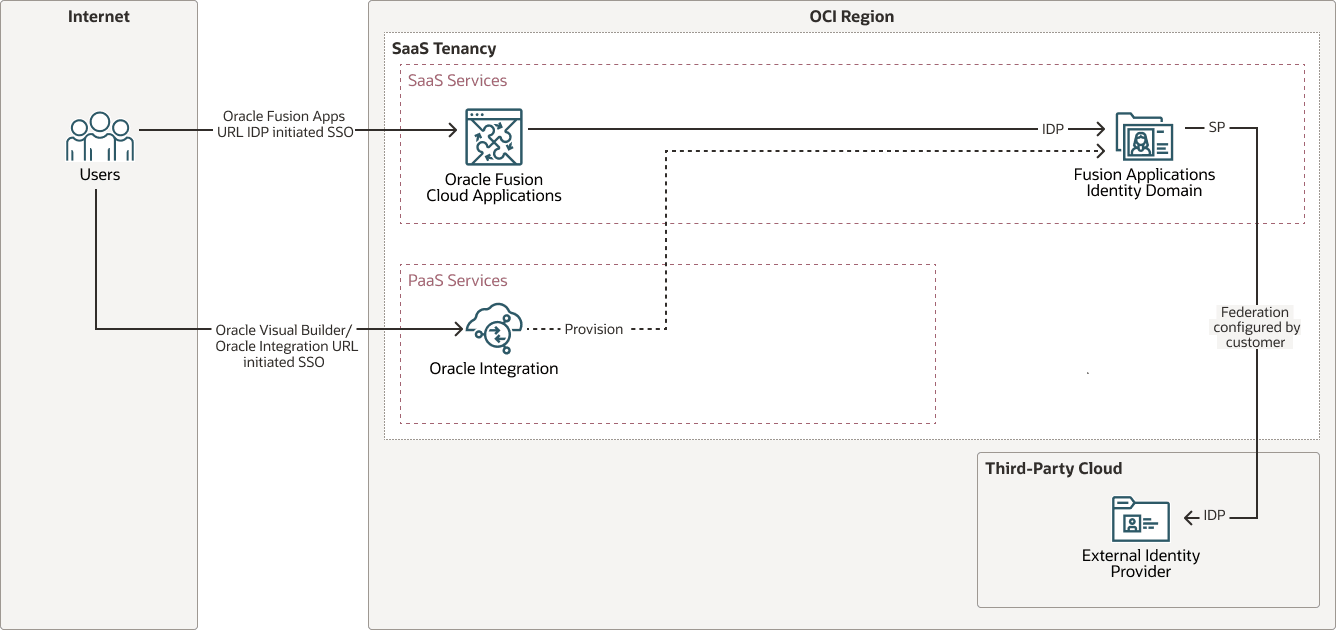
Configure SSO with Oracle Fusion Cloud Applications Identity Domain and an External Identity Provider
Other external identity providers can also be configured as the IdP for the Fusion Applications identity domain (as the service provider or "SP") using standard SAML-based integration.
The following diagram illustrates the authentication flow:
Configure Oracle Fusion Cloud Applications as a Service Provider and Microsoft Entra ID as External Identity Provider
The following steps show you how to configure Fusion Cloud Applications identity domain as the service provider and Microsoft Entra ID as the external identity provider.
- Download the metadata from the Oracle Fusion Cloud Applications identity domain configured as the service provider. You require metadata to configure the SAML application in Entra ID.
- Create an Enterprise Application in Microsoft Entra ID specifically for OCI Console access. This will register a new enterprise application in Entra ID.
- Configure SSO for the Microsoft Entra ID enterprise app using the metadata from Oracle Fusion Cloud Applications identity domain and update the application's attributes and claims to use the user's email address as the identifier. Finally, download the federation metadata XML from Microsoft Entra ID.
- Register Entra ID as an IdP in the Fusion Applications identity domain by
importing the federation metadata XML from Entra ID into the identity provider
configuration. Then, update the IDP policy rules to include Entra ID.
- In the OCI console, click Identity and Security, then click Domains.
- Select your Oracle Fusion Cloud Applications identity domain.
- Navigate to Federation, then click the Actions menu.
- Click Add SAML IDP.
- Enter a name, description, and upload an identity provider icon.
- Upload the Microsoft Entra ID metadata XML file (downloaded earlier).
- Define the user attribute mappings, such as mapping NameID to UserName or Email.
- On the Review and Create page, verify the configuration details.
- Click Activate to enable the new identity provider.
- Create a new identity provider policy rule, or edit an existing one to assign the newly created SAML IDP to the appropriate rule to enable federated authentication.
- Test the SSO configuration to verify successful federated authentication between Microsoft Entra ID and the Oracle Fusion Cloud Applications identity domain.
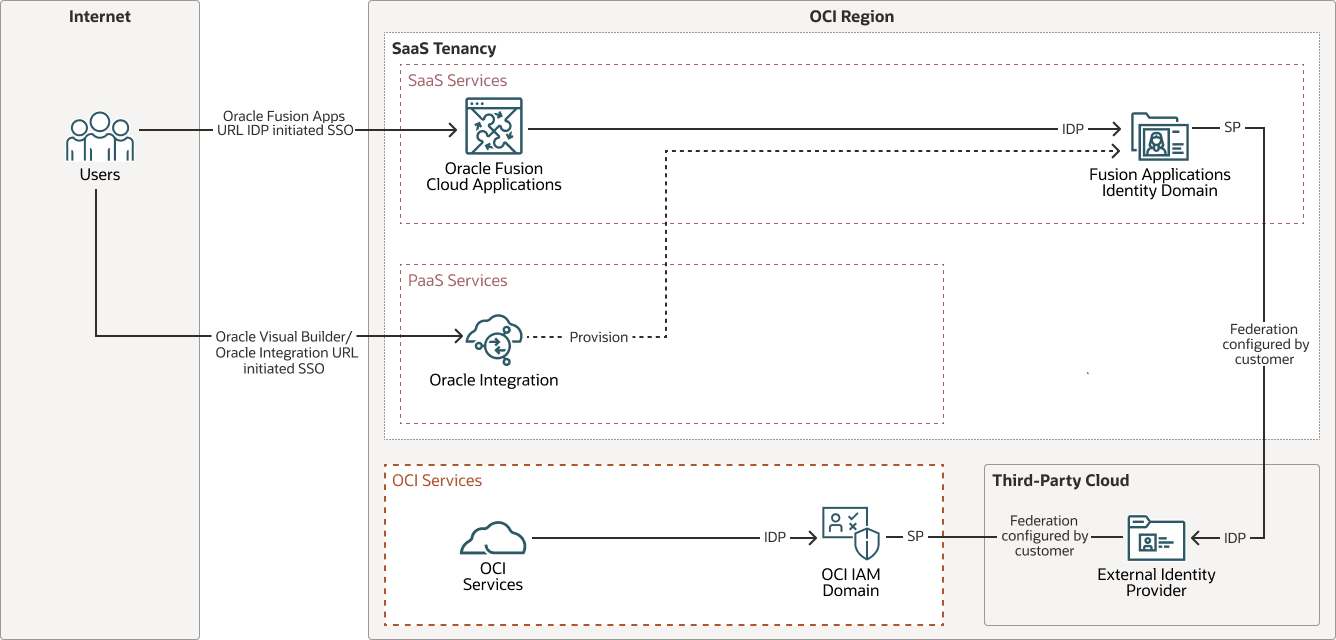
Configure SSO with Fusion Applications Identity Domain, OCI IAM Identity Domain, and an External Identity Provider
To further streamline authentication, a separate federation is established between the OCI Identity Domain (service provider) and Microsoft Entra ID (identity provider). This allows users to access OCI services with authentication routed through OCI IAM to Microsoft Entra ID, providing a unified SSO experience across Oracle and non-Oracle platforms.
OCI IAM identity domains offer comprehensive identity and access management, including authentication, SSO, and identity lifecycle management for SaaS, cloud-hosted, and on-premises applications—both Oracle and non-Oracle. In environments using OCI services, PaaS (such as Oracle Integration), and Oracle Fusion Cloud Applications, user groups may vary.
The Fusion Applications Identity Domain manages users and groups for Fusion Applications and Oracle Integration, while a separate OCI IAM Identity Domain centrally manages users who require access to OCI services like OCI Object Storage, OCI Logging, and OCI Functions.
The following diagram illustrates this authentication flow:
Configure OCI IAM Identity Domain as a Service Provider and Microsoft Entra ID as an Identity Provider
- Download metadata from the OCI IAM identity domain configured as the service provider. This metadata is required for configuring the SAML application in Entra ID.
- Create an Enterprise Application in Microsoft Entra ID specifically for OCI Console access. This will register a new enterprise application in Entra ID.
- Configure SSO for the Microsoft Entra ID enterprise app using the metadata from OCI IAM identity domain and update the application's attributes and claims to use the user's email address as the identifier. Finally, download the federation metadata XML from Microsoft Entra ID.
- Register Entra ID as an IdP in the OCI IAM identity domain by importing the
federation metadata XML from Entra ID into the identity provider configuration.
Then, update the IDP policy rules to include Entra ID.
- In the OCI console, click Identity and Security, then click Domains.
- Select your OCI IAM identity domain.
- Navigate to Federation, then click the Actions menu.
- Click Add SAML IDP.
- Enter a name, description, and upload an identity provider icon.
- Upload the Microsoft Entra ID metadata XML file (downloaded earlier).
- Define the user attribute mappings, such as mapping NameID to UserName or Email.
- On the Review and Create page, verify the configuration details.
- Click Activate to enable the new identity provider.
- Create a new identity provider policy rule, or edit an existing one to assign the newly created SAML IDP to the appropriate rule to enable federated authentication.
- Test the SSO configuration to verify successful federated authentication between Microsoft Entra ID and the OCI IAM identity domain.