About Transparent Data Encryption (TDE)
Transparent Data Encryption (TDE), a feature of Oracle Database 11gR2 and higher, provides database encryption and decryption services.
TDE supports the following products:
- Oracle Database
- Oracle Real Application Clusters (Oracle RAC)
- Oracle Data Guard
- Oracle Exadata Database Machine
- Oracle Recovery Manager (RMAN)
- Oracle Data Pump
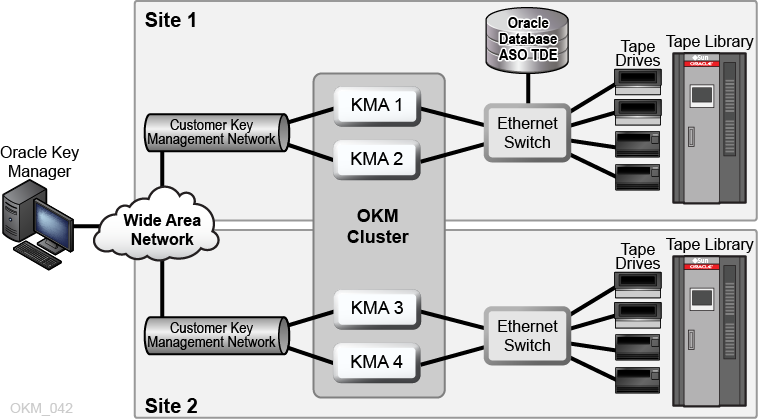
The figure below shows an OKM cluster featuring an Oracle database with Transparent Data Encryption (TDE). See About Oracle Key Manager for more information about the basic components of the OKM cluster.
TDE provides encryption services using a two-tiered key approach for TDE column encryption and TDE tablespace encryption. The first tier uses a master encryption key to encrypt the second tier table or tablespace data encryption keys that are stored within the database.
TDE stores the master encryption key in an external security module (Oracle Wallet or hardware security module). This is a recommended security practice and is crucial to maintaining the highest level of security from various threats. Use of OKM for the secure storage of the TDE master encryption keys is the recommended approach.
With TDE configured to use OKM, OKM creates and safely protects the AES256 master encryption key. OKM protects keys through replication (multiple copies across the cluster) and through backups of OKM itself.
Refer to Disaster Recovery for information about disaster recovery planning.
The following minimum versions are supported when using OKM with TDE:
Oracle Key Manager
- Oracle Key Manager 2.4.1 operating with Replication Schema version 13
- Supported OKM management platforms for the GUI and CLI are documented in the OKM product release notes, which include specific considerations for Oracle Solaris and Microsoft Windows platforms.
pkcs11_kms
- Oracle Solaris 11 Express with SRU 12
- Oracle Solaris 11 with x86 or SPARC, 32 bit or 64 bit
- Oracle Solaris 10 Update 10 pkcs11_kms patch 147441-03 for x86 or patch 147159-02 for SPARC, 32 bit or 64 bit
- Oracle Linux Server release 5.5 or higher.
Oracle Database
OKM can be integrated with TDE as the following versions of the Oracle Database server on a supported pkcs11_kms platform:
- Oracle Database 11.2.0.2 with patch 12626642
- Oracle Database 11.2.0.4
- Oracle Database 12.1 and 12.2
OKM PKCS#11 Provider
The pkcs11_kms provider interacts with OKM for key creation and key retrieval operations.
You can configure TDE to use the pkcs11_kms provider through its built-in support for hardware security modules. TDE uses the pkcs11_kms provider to acquire keys to use for encryption and decryption functions. TDE identifies key objects using a unique label that they define. TDE generates this label when the master key is created. The pkcs11_kms provider passes this label to OKM where it is maintained as metadata on the data unit. In OKM, keys are associated with data units and for the pkcs11_kms provider, this relationship should always be 1:1. Each time a new master key is created, a data unit with the key's label is created along with the corresponding key object. The key label name space in OKM is cluster-wide.
Key label naming conflicts can arise with other clients of OKM. Consequently, users of the pkcs11_kms provider should devise a key label naming scheme that insures uniqueness of key labels.
See Locate TDE Master Keys in OKM for more information.
TDE Authentication with OKM
TDE authenticates with OKM through the specific token configured to use the pkcs11_kms provider.
The token uses password-based authentication and X.509 certificates for mutual authentication of each party in the session, specifically the Oracle database instance and the OKM cluster node. You must configure TDE to properly pass these credentials to the PKCS#11 token. The TDE password should be the passphrase of the OKM agent (see Configure Database for TDE), not the AgentID:AgentPassword as suggested in the Oracle TDE documentation. For configuration instructions, refer to the document Oracle Advanced Security Transparent Data Encryption Best Practices, referenced at the beginning of this appendix.
Manage Authentication Credentials
OKM allows you to manage authentication credentials for agents using the pkcs11_kms provider. You can reset agent passphrases, and enable, disable or delete agents as your policies dictate. If a security breach is detected, you may disable the specific agent so that key retrievals are denied, while allowing other agents servicing other applications or devices to maintain their access. If you reset an agent passphrase, then remove the profile directory in the directory where the pkcs11_kms provider stores its slot configuration (for example, the location identified by the KMSTOKEN_DIR directory).