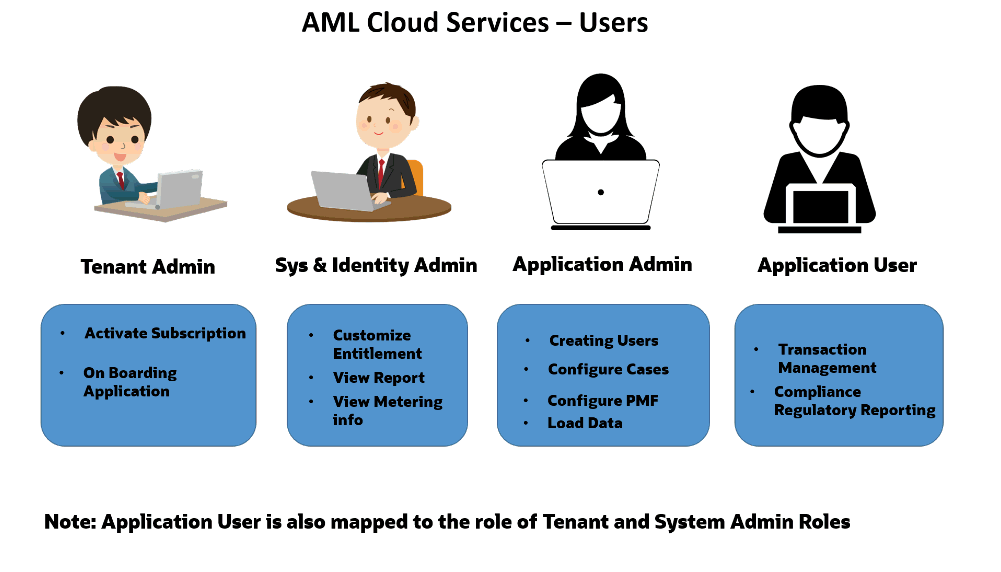
In Oracle AML Cloud, users have roles through which they gain access to functions and data. Users can have any number of roles.

Role-based security in Oracle AML controls who can do what on which data.
This table summarizes role-based access.
Component |
Description |
| Who | Is a role assigned to a user |
| What | Is a function that users with the role can perform |
| Which Data | Is the set of data that users with the role can access when performing the function |
This table provides some examples of role-based access.
Who |
What | Which Data |
| Data Administrator | can perform Data Preparation/ Ingestion | Business Data |
| Case Analyst | can view cases | For themselves |
Many job and abstract roles are predefined in Oracle AML Cloud. The predefined AML roles are:
User |
User Group |
Privileges |
| System/Tenant Admin |
|
Customer Onboarding · User setup (IDCS) § Map users to OOB user groups · User setup (OFSAA Id. Mgmt.) § Map users to user groups § Create new user roles § Map user roles to functions § Map user roles to user groups · Application security setup § Map security attributes for case management – Might be Business System Admin Ongoing User Administration · Create and setup new users · Deactivate old users |
| Data Administrator |
|
Data Preparation/ Ingestion · Take Data download specification · Review Scenario data map · Based on scenarios selected by business system admin, finalize data elements required. · Prepare CSVs according to download specification and sample CSV files. · Schedule the scripts daily basis Pipeline Tasks: outlined in Excel for user steps Setup Jobs & Batches · Create jobs · Create batch or edit batch for including the jobs. · Schedule the batch of ingestion and scenarios and case generation Configure Case System Parameters |
| Business System Admin | Setup Scenarios & thresholds · Decide Scenarios to be executed · Set thresholds/set for each scenarios · Run simulator to decide the thresholds. · Discuss with Technical team to take these scenarios and threshold for setting up the batch. Setup Workflow · Setup Actions and Statuses · Define non-status changing actions · Create workflow Configure Master data · Jurisdiction · Business Domain · Risk Event Decisions Setup Case · Setup Case Type · Establish access control/security mapping. · Scoring Setting up Configure Case System Parameters |
|
| Business Users | FC Analyst · Review Cases · Make determination of false positive or needing investigation FC Investigator · Review Cases determined to need investigation FC Team Supervisor · Oversees analyst and investigator queues to ensure backlog is going down · (Re)Allocates cases to other individuals · Creates reports for upper management FC QA/QC · Defines sample set of cases for QC review · Pulls sample set · Reviews sample set cases · Reopens, Reassigns or completes sample cases |
Following are the user roles that needs to be mapped to a user group to access various functionalities within the scheduler service.
Role Code |
Role Name |
Description |
BATCH_READ |
Batch Read |
This role provides access to batch definition screens with view permission. |
BATCH_WRITE |
Batch Write |
This role provides access to batch definition screens with view, write and modify permissions. |
BATCH_MAINT |
Batch Maintenance |
This role provides access to batch definition screens with view and modify permissions. |
BATCH_OPER |
Batch Operation |
This role provides access to batch definition screens with view, schedule and execute permissions. |
BATCH_ADV |
Batch Advanced |
This role provides access to batch definition screens with write, modify, delete, schedule and execute permissions. |
Privileges |
Case Analyst |
Case Supervisor |
Access Cases |
X |
X |
Search for Cases |
X |
X |
View Case List |
X |
X |
View Dashboard |
X |
X |
Edit Case Context |
X |
X |
View Event Details |
X |
X |
Set Event Decision |
|
X |
Add/Delete/View Accounts |
X |
X |
Add/ Delete /View Customers |
X |
X |
Add/ Delete /View Transactions |
X |
X |
Add/ Delete /View External Entities |
X |
X |
View Related Case |
X |
X |
View Related Events |
X |
X |
Clear Due Date |
X |
X |
Set Due Date |
X |
X |
Set Case Owner |
X |
X |
Set Case Assignee |
X |
X |
Recommend a Case for Closure as False Positive |
X |
|
Recommend a Case for Closure as True Positive |
X |
|
Reject Recommendation |
|
X |
Close a Case as False Positive |
|
X |
Close a Case as True Positive |
|
X |
View Evidence (Attachment and Comment list) |
X |
X |
Add Document |
X |
X |
Remove Document |
X |
X |
View Attachments |
X |
X |
Remove Attachments |
X |
X |
Add Narrative |
X |
X |
View Narrative |
X |
X |
View Audit History |
X |
X |
Add Investigation Comments |
X |
X |
Own a Case |
X |
X |
Generate CRR Reports |
|
X |
Viewing Case Reports |
X |
X |
Save Case Search Criteria of Report |
X |
X |
Update Case Search Criteria of Report |
X |
X |
Delete Case Search Criteria of Report |
X |
X |
Export the Report in Excel |
X |
X |
Privileges |
Case Admin |
Configuring Case Status (Add/Edit Case Status) |
X |
Configuring Case Action (Add/Edit Case Action) |
X |
Mapping the Action to Status |
X |
Mapping the Action to Case Type |
X |
Mapping the Action to User Role |
X |
Configuring System Parameters |
X |
Configuring Business Domains (Add/Edit Business Domains) |
X |
Configuring Jurisdictions (Add/Edit Jurisdictions ) |
X |
Configuring Case Types (Add/Edit Case Types) |
X |
Configuring Case Security Mappings |
X |
PMF |
X |
|
|