4 Enabling SSO Authentication
This chapter provides some general guidelines for configuring single sign-on (SSO) authentication for Oracle Business Intelligence.
Note:
For a detailed list of security setup steps, see Section 1.7, "Detailed List of Steps for Setting Up Security in Oracle Business Intelligence".
This chapter contains the following topics:
-
Section 4.1, "SSO Configuration Tasks for Oracle Business Intelligence"
-
Section 4.2, "Understanding SSO Authentication and Oracle Business Intelligence"
-
Section 4.4, "Configuring SSO in an Oracle Access Manager Environment"
-
Section 4.5, "Enabling SSO for Oracle BI Enterprise Edition Using Oracle Single Sign-On (OSSO)"
-
Section 4.7, "Enabling SSO Authentication Using Fusion Middleware Control"
-
Section 4.8, "Enabling the Online Catalog Manager to Connect"
Note:
Oracle recommends using Oracle Access Manager as an enterprise-level SSO authentication provider with Oracle Fusion Middleware 11g. Section 4.2, Section 4.3, and Section 4.4 assume that Oracle Access Manager is the SSO authentication provider. Section 4.6 references alternative authentication providers in custom SSO environment solutions.
For more information about configuring and managing Oracle Access Manager with Oracle Fusion Middleware, see "Introduction to Single Sign-On in Oracle Fusion Middleware" in Oracle Fusion Middleware Application Security Guide.
For more information about supported SSO providers, see "System Requirements and Certification".
4.1 SSO Configuration Tasks for Oracle Business Intelligence
Table 4-1 contains SSO authentication configuration tasks and provides links for obtaining more information.
Table 4-1 Task Map: Configuring SSO Authentication for Oracle Business Intelligence
| Task | Description | For More Information |
|---|---|---|
|
Configure Oracle Access Manager as the SSO authentication provider. |
Configure Oracle Access Manager to protect the Oracle Business Intelligence URL entry points. |
Section 4.4, "Configuring SSO in an Oracle Access Manager Environment" "Configuring Single Sign-On in Oracle Fusion Middleware" in Oracle Fusion Middleware Application Security Guide |
|
Configure the HTTP proxy. |
Configure the web proxy to forward requests from Presentation Services to the SSO provider. |
"Configuring Single Sign-On in Oracle Fusion Middleware" in Oracle Fusion Middleware Application Security Guide |
|
Configure a new authenticator for Oracle WebLogic Server. |
Configure the Oracle WebLogic Server domain in which Oracle Business Intelligence is installed to use the new identity store. |
Section 4.4.1, "Configuring a New Authenticator for Oracle WebLogic Server" Section 3.4, "Configuring Alternative Authentication Providers" Oracle Fusion Middleware Oracle WebLogic Server Administration Console Online Help |
|
Configure a new identity asserter for Oracle WebLogic Server. |
Configure the Oracle WebLogic Server domain in which Oracle Business Intelligence is installed to use the SSO provider as an asserter. |
Section 3.4, "Configuring Alternative Authentication Providers" Oracle Fusion Middleware Oracle WebLogic Server Administration Console Online Help |
|
Configure the new trusted system user to replace the default BISystemUser. |
Add the new trusted system user name from Oracle Internet Directory to become a member of the BISystem application role. |
Section 3.7, "Configuring a New Trusted User (BISystemUser)" |
|
Refresh the user and group GUIDs. |
Refresh the GUIDs of users and groups which migrated from the original identity store to the new identity store (authentication source). |
|
|
Configure custom SSO solutions. |
Configure alternative custom SSO solutions to protect the Oracle Business Intelligence URL entry points. |
|
|
Enable Oracle Business Intelligence to accept SSO authentication. |
Enable the SSO provider configured to work with Oracle Business Intelligence using Fusion Middleware Control. |
Section 4.7, "Enabling SSO Authentication Using Fusion Middleware Control" |
Note:
For an example of an Oracle Business Intelligence SSO installation scenario, see Oracle Fusion Middleware Enterprise Deployment Guide for Oracle Business Intelligence.
4.2 Understanding SSO Authentication and Oracle Business Intelligence
Integrating a single sign-on (SSO) solution enables a user to log on (sign-on) and be authenticated once. Thereafter, the authenticated user is given access to system components or resources according to the permissions and privileges granted to that user. Oracle Business Intelligence can be configured to trust incoming HTTP requests authenticated by a SSO solution that is configured for use with Oracle Fusion Middleware and Oracle WebLogic Server. For more information about configuring SSO for Oracle Fusion Middleware, see "Configuring Single Sign-On in Oracle Fusion Middleware" in Oracle Fusion Middleware Application Security Guide.
When Oracle Business Intelligence is configured to use SSO authentication, it accepts authenticated users from whatever SSO solution Oracle Fusion Middleware is configured to use. If SSO is not enabled, then Oracle Business Intelligence challenges each user for authentication credentials. When Oracle Business Intelligence is configured to use SSO, a user is first redirected to the SSO solution's login page for authentication. After the user is authenticated the SSO solution forwards the user name to Presentation Services where this name is extracted. Next a session with the BI Server is established using the impersonation feature (a connection string between the Oracle BI Presentation Server and the BI Server using credentials that act on behalf of a user being impersonated).
After successfully logging in using SSO, users are still required to have the oracle.bi.server.manageRepositories permission to log in to the Administration Tool using a valid user name and password combination. After installation, the oracle.bi.server.manageRepositories permission is granted by being a member of the default BIAdministration application role.
Configuring Oracle Business Intelligence to work with SSO authentication requires minimally that the following be done:
-
Oracle Fusion Middleware and Oracle WebLogic Server are configured to accept SSO authentication. Oracle Access Manager is recommended in production environments.
-
Oracle BI Presentation Services is configured to trust incoming messages.
-
The HTTP header information required for identity propagation with SSO configurations (namely, user identity and SSO cookie) is specified and configured.
4.2.1 How an Identity Asserter Works
This section describes how Oracle Access Manager authentication provider works with Oracle WebLogic Server using Identity Asserter for single sign-on, providing the following features:
-
Identity Asserter for Single Sign-on
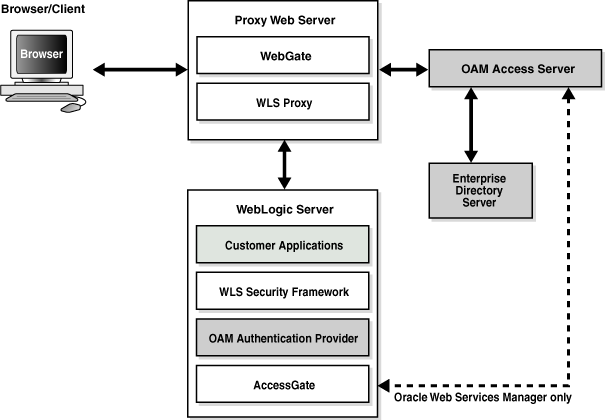
This feature uses the Oracle Access Manager authentication services and validates already-authenticated Oracle Access Manager users through a suitable token and creates a WebLogic-authenticated session. It also provides single sign-on between WebGate and portals. WebGate is a plug-in that intercepts web resource (HTTP) requests and forwards them to the Access Server for authentication and authorization.
-
Authenticator
This feature uses Oracle Access Manager authentication services to authenticate users who access an application deployed in Oracle WebLogic Server. Users are authenticated based on their credentials, for example a user name and password.
After the authentication provider for Oracle Access Manager is configured as the Identity Asserter for single sign-on, the web resources are protected. Perimeter authentication is performed by WebGate on the web tier and by the appropriate token to assert the identity of users who attempt access to the protected WebLogic resources.
All access requests are routed to a reverse proxy web server. These requests are in turn intercepted by WebGate. The user is challenged for credentials based on the authentication scheme configured within Oracle Access Manager (form-based login recommended).
After successful authentication, WebGate generates a token and the web server forwards the request to Oracle WebLogic Server, which in turn invokes Oracle Access Manager Identity Asserter for single sign-on validation. Oracle Access Manager is able to pass various types of heading token, the simplest being an HTTP header called OAM_REMOTE_USER containing the user ID that has been authenticated by Oracle Access Manager. The WebLogic Security Service invokes Oracle Access Manager Identity Asserter for single sign-on, which next gets the token from the incoming request and populates the subject with the WLSUserImpl principal. The Identity Asserter for single sign-on adds the WLSGroupImpl principal corresponding to the groups the user is a member of. Oracle Access Manager then validates the cookie.
Figure 4-1 depicts the distribution of components and the flow of information when the Oracle Access Manager Authentication Provider is configured as an Identity Asserter for SSO with Oracle Fusion Middleware.
4.2.2 How Oracle Business Intelligence Operates with SSO Authentication
After SSO authorization has been implemented, Presentation Services operates as if the incoming web request is from a user authenticated by the SSO solution. Presentation Services next creates a connection to the BI Server using the impersonation feature and establishes the connection to the BI Server on behalf of the user. User personalization and access controls such as data-level security are maintained in this environment.
4.3 SSO Implementation Considerations
When implementing a SSO solution with Oracle Business Intelligence you should consider the following:
-
When accepting trusted information from the HTTP server or servlet container, it is essential to secure the machines that communicate directly with Presentation Services. This can be done by setting the Listener\Firewall node in the instanceconfig.xml file with the list of HTTP Server or servlet container IP addresses. Additionally, the Firewall node must include the IP addresses of all Oracle Business Intelligence Scheduler instances, Oracle BI Presentation Services Plug-in instances, and Oracle Business Intelligence JavaHost instances. If any of these components are co-located with Oracle BI Presentation Services, then address 127.0.0.1 must be added in this list as well. This setting does not control end-user browser IP addresses.
-
When using mutually-authenticated SSL, you must specify the Distinguished Names (DNs) of all trusted hosts in the Listener\TrustedPeers node.
4.4 Configuring SSO in an Oracle Access Manager Environment
For information about how to configure Oracle Access Manager as the SSO authentication provider for Oracle Fusion Middleware with WebLogic Server, see "Configuring Single Sign-On in Oracle Fusion Middleware" in Oracle Fusion Middleware Application Security Guide. For more information about managing Oracle Access Manager, see Oracle Fusion Middleware Administrator's Guide for Oracle Access Manager.
For information about how to configure Oracle BI Publisher to use Oracle Access Manager as the SSO authentication provider, see "Configuring BI Publisher to Use Oracle Access Manager (OAM) Single Sign-On" in Oracle Fusion Middleware Administrator's and Developer's Guide for Oracle Business Intelligence Publisher.
After the Oracle Fusion Middleware environment is configured, in general the following must be done to configure Oracle Business Intelligence:
-
Configure the SSO provider to protect the Oracle Business Intelligence URL entry points.
-
Configure the web server to forward requests from Presentation Services to the SSO provider.
-
Configure the new identity store as the main authentication source for the Oracle WebLogic Server domain in which Oracle Business Intelligence has been installed. For more information, see Section 4.4.1, "Configuring a New Authenticator for Oracle WebLogic Server".
-
Configure the Oracle WebLogic Server domain in which Oracle Business Intelligence is installed to use an Oracle Access Manager asserter. For more information, see Section 4.4.2, "Configuring Oracle Access Manager as a New Identity Asserter for Oracle WebLogic Server".
-
After configuration of the SSO environment is complete, enable SSO authentication for Oracle Business Intelligence. For more information, see Section 4.7, "Enabling SSO Authentication Using Fusion Middleware Control".
4.4.1 Configuring a New Authenticator for Oracle WebLogic Server
After installing Oracle Business Intelligence, the Oracle WebLogic Server embedded LDAP server is the default authentication source (identity store). To use a new identity store (for example, OID), as the main authentication source, you must configure the Oracle WebLogic Server domain (where Oracle Business Intelligence is installed).
For more information about configuring authentication providers in Oracle WebLogic Server, see Oracle Fusion Middleware Securing Oracle WebLogic Server.
To configure a new authenticator in Oracle WebLogic Server:
-
Log in to Oracle WebLogic Server Administration Console and click Lock & Edit in the Change Center.
For more information, see Section 1.6.1, "Using Oracle WebLogic Server Administration Console".
-
Select Security Realms from the left pane and click myrealm.
The default Security Realm is named myrealm.
-
Display the Providers tab, then display the Authentication sub-tab.
-
Click New to launch the Create a New Authentication Provider page.
Complete the fields as follows:
-
Name: OID Provider, or a name of your choosing.
-
Type: OracleInternetDirectoryAuthenticator
-
Click OK to save the changes and display the authentication providers list updated with the new authentication provider.
-
-
Click the newly added authenticator in the authentication providers table.
-
Navigate to Settings, then select the Configuration\Common tab:
-
Select SUFFICIENT from the Control Flag list.
-
Click Save.
-
-
Display the Provider Specific tab and specify the following settings using appropriate values for your environment:
Section Name Field Name Description Connection
Host
The LDAP host name. For example, <localhost>.
Connection
Port
The LDAP host listening port number. For example, 6050.
Connection
Principal
The distinguished name (DN) of the user that connects to the LDAP server. For example, cn=orcladmin.
Connection
Credential
The password for the LDAP administrative user entered as the Principal.
Users
User Base DN
The base distinguished name (DN) of the LDAP server tree that contains users. For example, use the same value as in Oracle Access Manager.
Users
All Users Filter
The LDAP search filter. For example, (&(uid=*) (objectclass=person)). The asterix (*) filters for all users. Click More Info... for details.
Users
User From Name Filter
The LDAP search filter. Click More Info... for details.
Users
User Name Attribute
The attribute that you want to use to authenticate (for example, cn, uid, or mail). Set as the default attribute for user name in the directory server. For example, uid .
Note: The value that you specify here must match the User Name Attribute that you are using in the authentication provider, as described in the next task Section 3.5.1, "Configuring User Name Attributes".
Groups
Group Base DN
The base distinguished name (DN) of the LDAP server tree that contains groups (same as User Base DN).
General
GUID attribute
The attribute used to define object GUIDs in LDAP.
orclguid
Note: You should not normally change this default value, however, if you do, you must also specify the changed value in Fusion Middleware Control, as described in the task Section 3.6, "Configuring the GUID Attribute in the Identity Store".
For more information about configuring authentication providers in Oracle WebLogic Server, see Oracle Fusion Middleware Securing Oracle WebLogic Server.
-
Click Save.
-
Perform the following steps to set up the default authenticator for use with the Identity Asserter:
-
At the main Settings for myrealm page, display the Providers tab, then display the Authentication sub-tab, then select DefaultAuthenticator to display its configuration page.
-
Display the Configuration\Common tab and select 'SUFFICIENT' from the Control Flag list.
For more information, see Section 3.4.7, "Setting the JAAS Control Flag Option".
-
Click Save.
-
-
Perform the following steps to reorder Providers:
-
Display the Providers tab.
-
Click Reorder to display the Reorder Authentication Providers page
-
Select a provider name and use the arrow buttons to order the list of providers as follows:
-
OID Authenticator (SUFFICIENT)
-
OAM Identity Asserter (REQUIRED)
-
Default Authenticator (SUFFICIENT)
-
-
Click OK to save your changes.
-
-
In the Change Center, click Activate Changes.
-
Restart Oracle WebLogic Server.
4.4.2 Configuring Oracle Access Manager as a New Identity Asserter for Oracle WebLogic Server
The Oracle WebLogic Server domain in which Oracle Business Intelligence is installed must be configured to use an Oracle Access Manager asserter.
For more information about creating a new asserter in Oracle WebLogic Server, see Oracle Fusion Middleware Oracle WebLogic Server Administration Console Online Help.
To configure Oracle Access Manager as the new asserter for Oracle WebLogic Server:
-
Log in to Oracle WebLogic Server Administration Console.
For more information, see Section 1.6.1, "Using Oracle WebLogic Server Administration Console".
-
In Oracle WebLogic Server Administration Console, select Security Realms from the left pane and click the realm you are configuring. For example, myrealm. Select Providers.
-
Click New. Complete the fields as follows:
-
Name: OAM Provider, or a name of your choosing.
-
Type: OAMIdentityAsserter.
-
-
Click OK.
-
Click Save.
-
In the Providers tab, perform the following steps to reorder Providers:
-
Click Reorder
-
In the Reorder Authentication Providers page, select a provider name, and use the arrows beside the list to order the providers as follows:
-
OID Authenticator (SUFFICIENT)
-
OAM Identity Asserter (REQUIRED)
-
Default Authenticator (SUFFICIENT)
-
-
Click OK to save your changes.
-
-
In the Change Center, click Activate Changes.
-
Restart Oracle WebLogic Server.
You can verify that Oracle Internet Directory is the new identity store (default authenticator) by logging back into Oracle WebLogic Server and verifying the users and groups stored in the LDAP server appear in the console.
-
Use Fusion Middleware Control to enable SSO authentication.
For more information, see Section 4.7, "Enabling SSO Authentication Using Fusion Middleware Control".
4.5 Enabling SSO for Oracle BI Enterprise Edition Using Oracle Single Sign-On (OSSO)
This section describes how to configure Single Sign-On for Oracle BI Enterprise Edition using Oracle SSO (OSSO).
This section is intended for administrators and advanced users. Before attempting to complete the steps in this section, you must have a good understanding of Oracle BI Enterprise Edition and Single Sign-On features.
This section contains the following topics:
4.5.1 Installing and Configuring Oracle HTTP Server to Redirect Requests for Oracle Business Intelligence to WebLogic Server
To install and configure Oracle HTTP Server to redirect requests for Oracle Business Intelligence to WebLogic Server:
-
Install a supported Oracle HTTP Server (OHS).
For more information see Oracle Fusion Middleware Installation Guide for Oracle Web Tier.
Refer the System Requirements and Supported Platforms documentation for supported OHS version for Oracle BI EE 11g.
http://www.oracle.com/technetwork/middleware/ias/downloads/fusion-certification-100350.htmlLook for 'System Requirements and Supported Platforms for Oracle Business Intelligence Suite Enterprise Edition 11gR1.xls'
-
Log in to Fusion Middleware Control.
For information, see Section 1.6.2, "Using Oracle Fusion Middleware Control".
-
Expand Web Tier and select ohs1.
-
Display the Oracle HTTP Server menu and select Administration, and the mod_wl_ohs Configuration option.
-
In the mod_wl_ohs Configuration page, enter the name of the WebLogic computer in the WebLogic Host field.
-
Enter the port number in the WebLogic Port field.
For example, enter
9704. -
Restart OHS.
-
Test the configuration by accessing Oracle Business Intelligence through the OHS host.
For example, http://ohscomputer.example/analytics
4.5.2 Creating and Configuring an OSSO Asserter and OID Authenticator
To create and configure an OSSO asserter and OID authenticator:
-
Log in to Oracle WebLogic Server Administration Console and click Lock & Edit in the Change Center.
For more information, see Section 1.6.1, "Using Oracle WebLogic Server Administration Console".
-
Select Security Realms from the left pane and click myrealm.
The default Security Realm is named myrealm.
-
Display the Providers tab, then display the Authentication page.
-
Click New to launch the Create a New Authentication Provider page.
Complete the fields as follows:
-
Name: MySSO, or a name of your choosing.
-
Type: OSSOIdentityAsserter
-
Click OK to save the changes and display the authentication providers list updated with the new authentication provider.
-
-
Click the newly added authenticator in the authentication providers table.
-
Navigate to Settings, then select the Common page from the Configuration tab:
-
Select REQUIRED from the Control Flag list.
-
Click Save.
-
-
Click New again, to launch the Create a New Authentication Provider page to create a new authenticator for OID.
Complete the fields as follows:
-
Name: MyOID, or a name of your choosing.
-
Type: OracleInternetDirectoryAuthenticator
-
Click OK to save the changes and display the authentication providers list updated with the new authentication provider.
-
-
Click the newly added authenticator in the Authentication Providers table.
-
Navigate to Settings, then select the Configuration and Common tab:
-
Select SUFFICIENT from the Control Flag list.
-
Click Save.
-
-
Display the Provider Specific tab and specify the settings using appropriate values for the OID server (for more information, see the table in Section 4.4.1, "Configuring a New Authenticator for Oracle WebLogic Server" )
For more information about configuring authentication providers in Oracle WebLogic Server, see Oracle Fusion Middleware Securing Oracle WebLogic Server.
-
In the Providers tab, perform the following steps to reorder Providers:
-
Click Reorder
-
In the Reorder Authentication Providers page, select a provider name, and use the arrows beside the list to order the providers as follows:
-
MySSO (REQUIRED)
-
MyOID (SUFFICIENT)
-
Default Authenticator (SUFFICIENT)
-
-
Click OK to save your changes.
-
-
In the Change Center, click Activate Changes.
-
Restart Oracle WebLogic Server.
You can verify that Oracle Internet Directory is the new identity store (default authenticator) by logging back into Oracle WebLogic Server and verifying that the users and groups stored in the LDAP server appear in the console.
-
Configure OID user account as BISystemUser.
Oracle Business Intelligence requires an OID user account to be defined as BISystemUser. You can either create an account BISystemUser in the OID server or create or use any other account to be used as BISystemUser.
-
Update the Credentials in Fusion Middleware Control with the OID user account which is used as BISystemUser.
For more information, see Section 3.7, "Configuring a New Trusted User (BISystemUser)".
-
Restart Oracle WebLogic Server.
4.5.3 Registering a Partner Application in Oracle Single Sign-On and Protecting the Oracle Business Intelligence Resource in Oracle HTTP Server
To register a partner application in Oracle Single Sign-On (OSSO) and protect the Oracle Business Intelligence resource in Oracle HTTP Server (OHS):
-
Ensure that OSSO is running.
-
On the machine that hosts the Oracle Single Sign-On server, set the ORACLE_HOME environment variable to point to the directory where Oracle Single Sign-On server is installed.
-
To register the partner application in OSSO run the following command syntax:
ssoreg.sh or ssoreg.bat -oracle_home_path <ORACLE_HOME_path> -site_name <site_name> -config_mod_osso TRUE -mod_osso_url <mod_osso_url> [-virtualhost] [-update_mode CREATE | DELETE | MODIFY] [-remote_midtier] [-config_file <config_file_path>]
For example, on UNIX enter:
./ssoreg.sh -oracle_home_path /mw_home/OracleBI1 -site_name testserver -config_mod_osso TRUE -mod_osso_url http://testserver.example:7777 -update_mode CREATE -remote_midtier -config_file /mw_home/OracleBI1/sso/conf/osso.conf
-
Copy the sso configuration file (for example, osso.conf) to the directory:
ORACLE_INSTANCE/config/COMPONENT_TYPE/COMPONENT_NAME
-
Copy the sample mod_osso.conf file from the folder:
ORACLE_INSTANCE/config/COMPONENT_TYPE/COMPONENT_NAME/disabled
to the folder:
ORACLE_INSTANCE/config/COMPONENT_TYPE/COMPONENT_NAME/moduleconf
-
Update the mod_osso.conf file using Fusion Middleware Control.
-
Log in to Fusion Middleware Control.
For information, see Section 1.6.2, "Using Oracle Fusion Middleware Control".
-
Expand Web Tier and select ohs1.
-
Choose Administration and Advanced Configuration from the menu.
-
Configure mod_osso.conf file settings as follows:
<IfModule osso_module> OssoIpCheck off OssoIdleTimeout off OssoSecureCookies off OssoSendCacheHeaders off OssoConfigFile "${ORACLE_INSTANCE}/config/${COMPONENT_TYPE}/${COMPONENT_NAME}/osso.conf" <Location /analytics> require valid-user AuthType Osso </Location> </IfModule>
-
-
Enable SSO authentication by following the steps in Section 4.7, "Enabling SSO Authentication Using Fusion Middleware Control".
When following the steps in Section 4.7, you must:
-
Select "Oracle SSO" from the drop down list in the SSO Provider field.
-
Enter appropriate URL values in the The SSO Provider Logon and The SSO Provider Logoff URL fields, for example:
http://mycomputer.example:7777/pls/orasso/orasso.wwsso_app_admin.ls_login
http://mycomputer.example:7777/pls/orasso/orasso.wwsso_app_admin.ls_logout
-
-
Test the OHS SSO configuration by displaying Oracle Business Intelligence.
http://<OHS_computer_name>/analytics
This should display a Single Sign-On window where you enter user credentials.
Note:
Oracle recommends that when Oracle Business Intelligence is configured with SSO and you integrate BI Publisher, you must also configure SSO for BI Publisher. For more information, see "Configuring BI Publisher to Use Oracle Access Manager (OAM) Single Sign-On" in Oracle Fusion Middleware Administrator's and Developer's Guide for Oracle Business Intelligence Publisher.
4.6 Configuring Custom SSO Environments
For information about configuring Oracle Business Intelligence to participate in custom SSO environments (for example, setting up SSO using Active Directory or SiteMinder), see articles 1274953.1 and 1287479.1 on My Oracle Support at:
4.7 Enabling SSO Authentication Using Fusion Middleware Control
After Oracle Business Intelligence has been configured to use the SSO solution configured for use by Oracle Fusion Middleware, you must enable SSO authentication for Oracle Business Intelligence in Fusion Middleware Control from the Security tab.
To enable Oracle Business Intelligence to use SSO authentication:
-
Log in to Fusion Middleware Control.
For information, see Section 1.6.2, "Using Oracle Fusion Middleware Control".
-
Go to the Security page and display the Single Sign On tab.
Click the Help button on the page to access the page-level help for its elements.
-
Click Lock and Edit Configuration.
-
Select Enable SSO.
When selected, this checkbox enables SSO to be the method of authentication into Oracle Business Intelligence. The appropriate form of SSO is determined by the configuration settings made for the chosen SSO provider.
-
Select the configured SSO provider from the list.
The SSO Provider list becomes active when you select the Enable SSO checkbox.
If you select 'Custom' from the SSO Provider list, then the system will not overwrite the changes you make to the <Authentication> section of the instanceconfig.xml file. Instead, you can manually edit this section of the instanceconfig.xml file.
-
If required, enter logon and logoff URLs for the configured SSO provider.
The logoff URL (specified by the SSO provider) must be outside the domain and port that the SSO provider protects, because the system does not log users out.
-
Click Apply, then Activate Changes.
-
Restart the Oracle Business Intelligence components using Fusion Middleware Control.
For more information, see "Starting and Stopping the Oracle Business Intelligence Components" in Oracle Fusion Middleware System Administrator's Guide for Oracle Business Intelligence Enterprise Edition.
4.8 Enabling the Online Catalog Manager to Connect
The online Catalog Manager might fail to connect to Oracle BI Presentation Services when the HTTP web server for Oracle Business Intelligence is enabled for SSO. When you enable SSO in Section 4.7, "Enabling SSO Authentication Using Fusion Middleware Control", the Oracle Business Intelligence URL http://hostname:port_number/analytics becomes protected, and you must point the online Catalog Manager to the URL http://hostname:port_number/analytics-ws instead. The URL should remain unprotected. It is configured only to accept SOAP access as used by Oracle BI Publisher, Oracle BI Add-in for Microsoft Office, and the online Catalog Manager.
To log in to the online Catalog Manager when SSO is enabled you must change the URL suffix to point to analytics-ws/saw.dll.