3 Alternative Security Options
This chapter describes alternative security options for BI Publisher, including Single Sign-on (SSO), LDAP options, Oracle Access Manager (OAM), and Microsoft Active Directory.
It covers the following topics:
-
Section 3.3, "Understanding BI Publisher's Users, Roles, and Permissions"
-
Section 3.6, "How Functional Privileges and Permissions Work Together"
-
Section 3.12, "Configuring BI Publisher with Single Sign-on (SSO)"
-
Section 3.13, "Configuring SSO in an Oracle Access Manager Environment"
3.1 About Alternative Security Options
This chapter describes security concepts and options for a standalone implementation of Oracle BI Publisher, that is, not installed as part of the Oracle Business Intelligence Enterprise Edition. Note the following:
-
If you have installed the Oracle BI Enterprise Edition, then see Oracle Fusion Middleware Security Guide for Oracle Business Intelligence Enterprise Edition for information about security.
-
If you have installed BI Publisher on its own and you plan to use Oracle Fusion Middleware Security, then see Section 2.1, "Understanding the Security Model." The following topics will be of interest in this chapter:
-
To configure BI Publisher with these other Oracle security models:
-
Oracle BI Server security
-
Oracle E-Business Suite security
-
Oracle Database security
-
Siebel CRM security
See Chapter 5, "Integrating with Other Oracle Security Models."
-
Use the information in this chapter to configure the following:
-
BI Publisher Security
-
Integration with an LDAP provider
Note:
Any identity store provider that is supported by Oracle WebLogic Server can be configured to be used with BI Publisher. Configuring BI Publisher to use an alternative external identity store is performed using the Oracle WebLogic Server Administration Console. For this configuration, see Section 2.8, "Customizing the Default Security Configuration."
-
Integration with a Single Sign-On provider
3.2 Authentication and Authorization Options
BI Publisher supports several options for authentication and authorization. You can choose a single security model to handle both authentication and authorization; or, you can configure BI Publisher to use a Single Sign-On provider or LDAP provider for authentication with another security model to handle authorization.
3.3 Understanding BI Publisher's Users, Roles, and Permissions
A user is assigned one or multiple Roles. A Role can grant any or all of the following:
-
Privileges to use functionality
-
Permissions to perform actions on catalog objects
-
Access to data sources
You can create a hierarchy of roles by assigning roles to other roles. In this way the privileges and permissions of multiple roles can roll up to higher level roles. Figure 3-1 shows an example of the hierarchy structure of User, Role, and Folder.
Figure 3-1 Hierarchy Structure of User, Role, and Folder
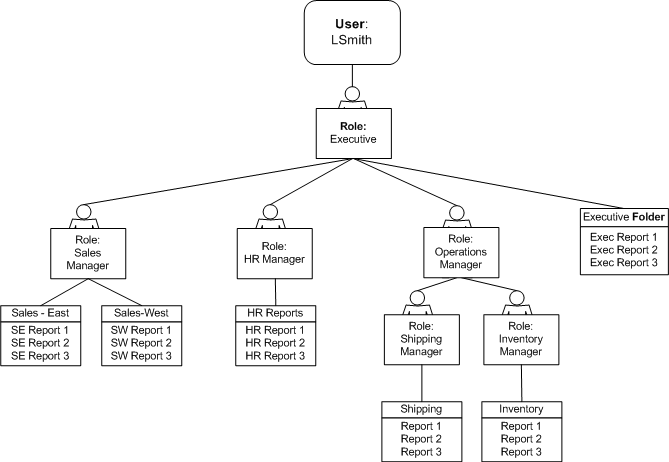
Description of "Figure 3-1 Hierarchy Structure of User, Role, and Folder"
3.3.1 Options for Configuring Users and Roles
There are three options for setting up users and roles:
-
Set up users and roles in the BI Publisher Security Center
For this option, follow the instructions in this section.
-
Configure BI Publisher with your LDAP server
For this option, see Section 3.10.2, "Configuring BI Publisher to Use an LDAP Provider for Authentication and Authorization."
-
Set up users and roles in a supported Oracle security model. For this option, see Chapter 5, "Integrating with Other Oracle Security Models."
3.4 About Privileges to Use Functionality
BI Publisher provides a set of functional roles to grant access to specific functionality within the application. Assign these roles to users based on their need to perform the associated tasks. These roles cannot be updated or deleted.
Table 3-1 shows the privileges granted to each functional role.
Table 3-1 Privileges Granted to Functional Roles
| Role | Privilege |
|---|---|
|
BI Publisher Scheduler |
View Export History Schedule |
|
BI Publisher Template Designer |
View Export History (public reports only) Enables access to Layout Editor Enables log on from Template Builder |
|
BI Publisher Developer |
View Export Schedule History Edit Report Enables access to Layout Editor Enables log on from the Template Builder Enables access to the Data Model Editor |
|
BI Publisher Administrator |
Enables the privileges of all other roles Grants access to the Administration page and all administration tasks |
Roles assigned these privileges cannot perform any actions on objects in the catalog until they are also granted permissions on the catalog objects.
3.5 About Catalog Permissions
To perform the actions allowed by the functional roles above, a role must also be granted permissions to access the objects in the catalog. Table 3-2 describes permissions for roles.
Each of these permissions can be granted at the folder level to enable the operations on all items within a folder.
Table 3-2 Permissions for Roles
| Permission | Description |
|---|---|
|
Read |
Enables a role to display an object in the catalog. If the object resides within a folder, a role must be granted the Read permission on the object and its parent Folder. |
|
Write |
|
|
Delete |
Enables a role to delete an object. |
|
Run Report Online |
Enables a role to run a report and view it in the report viewer. |
|
Schedule Report |
Enables a role to schedule a report. |
|
View Report Output |
Enables a role to access the Report Job History for a report. |
It is important to note that for a report consumer to successfully run a report, his role must have read access to every object that is referenced by the report.
For example, a report consumer must run a report in a folder named Reports. The data model for this report, resides in a folder named Data Models. This report references a Sub Template stored in a folder named Sub Templates, and also references a Style Template stored in a folder named Style Templates. The report consumer's role must be granted Read access to all of these folders and the appropriate objects within.
3.6 How Functional Privileges and Permissions Work Together
It is important to understand the following rules regarding the behavior of privileges and permissions:
-
A role assigned a functional privilege cannot perform any actions in the catalog until catalog permissions are also assigned
-
A role can be assigned a set of permissions on catalog objects without being assigned any functional privileges
-
If a role is assigned a functional privilege, when catalog permissions are assigned, some permissions are inherited
3.6.1 A Role Must Be Assigned Catalog Permissions
A role assigned a functional role cannot perform any actions in the catalog until catalog permissions are granted. Note that the functional roles themselves (BI Publisher Developer, BI Publisher Scheduler, and so on) cannot be directly assigned permissions in the catalog. The functional roles must first be assigned to a custom role and then the custom role is available in the catalog permissions table.
3.6.2 A Role Can Be Granted Catalog Permissions Only
The permissions available directly in the catalog enable running reports, scheduling reports, and viewing report output. Therefore if your enterprise includes report consumers who have no other reason to access BI Publisher except to run and view reports, then the roles for these users consist of catalog permissions only.
3.6.3 Inherited Permissions
When a role is assigned one of the functional roles, and that role is granted permissions on a particular folder in the catalog, then some permissions are granted automatically based on the functional role.
For example, assume that you create a role called Financial Report Developer. You assign this role the BI Publisher Developer role. For this role to create reports in the Financial Reports folder in the catalog, you grant this role Read, Write, and Delete permissions on the folder. Because the BI Publisher Developer role includes the run report, schedule report, and view report history privileges, these permissions are automatically granted on any folder to which a role assigned the BI Publisher Developer role is granted Read access.
3.7 About Access to Data Sources
A role must be granted access to a data source to view reports that run against the data source or to build and edit data models that use the data source. Add access to data sources in the Roles and Permissions page. See Section 3.8.4, "Granting Data Access."
3.8 Configuring Users, Roles, and Data Access
The following procedures describe:
3.8.1 Creating Roles
To create a new role in BI Publisher:
-
Navigate to the BI Publisher Administration page.
-
Under Security Center, click Roles and Permissions.
-
Click Create Role.
-
Enter a Name for the role and optionally, enter a Description.
-
Click Apply.
-
Click Assign Roles to assign roles to the user.
-
Use the shuttle buttons to move Available Roles to Assigned Roles. Click Apply.
-
To add a role to a role, click Add Roles.
-
Use the shuttle buttons to move Available Roles to Included Roles. Click Apply.
To add data sources to a role, see Section 3.8.4, "Granting Data Access."
3.8.2 Creating Users and Assigning Roles to a User
To create a new user in BI Publisher:
-
Navigate to the BI Publisher Administration page.
-
Under Security Center, click Users.
-
Click Create User.
-
Add the User Name and Password for the user.
-
Click Apply.
-
Click Assign Roles to assign roles to the user.
-
Use the shuttle buttons to move Available Roles to Assigned Roles. Click Apply.
3.8.3 Granting Catalog Permissions
For a role to access an object in the catalog, the role must be granted Read permissions on both the object and the folder in which the object resides. Permissions can be granted at the folder level and applied to all the objects and subfolders it contains, or applied to individual objects.
To grant catalog permissions to a role:
-
Navigate to the Catalog.
-
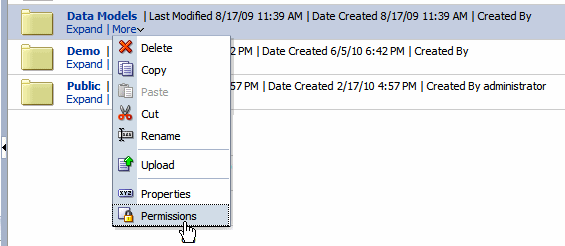
Locate the folder or object on which to grant permissions and click More. From the menu (shown in Figure 3-2), select Permissions. Alternatively, you can select the folder and click Permissions in the Tasks region.
Note:
Permissions cannot be granted on the root Shared folder.
-
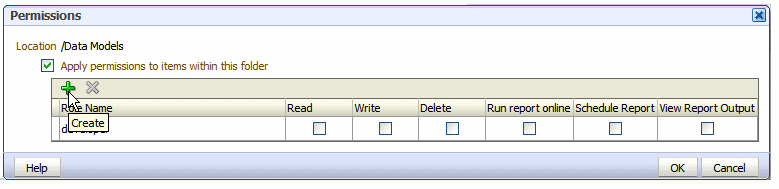
On the Permissions dialog (shown in Figure 3-3), click Create.
-
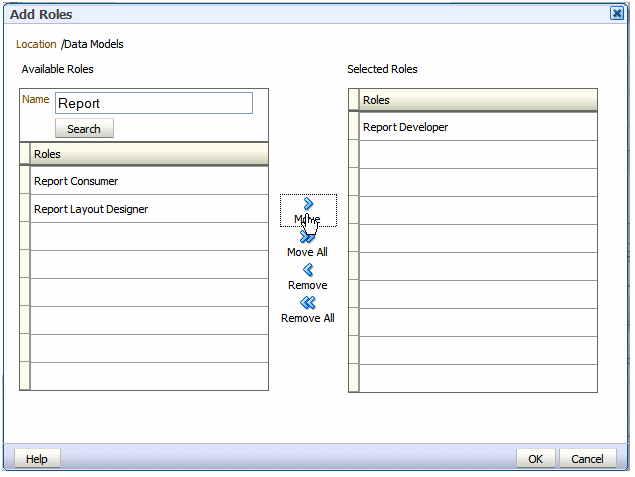
On the Add Roles dialog (shown in Figure 3-4), enter a search string to find a role, or simply click Search to display all roles. Use the shuttle buttons to move roles from the Available Roles list to the Selected Roles list.
-
When finished, click OK to return to the Permissions dialog.
-
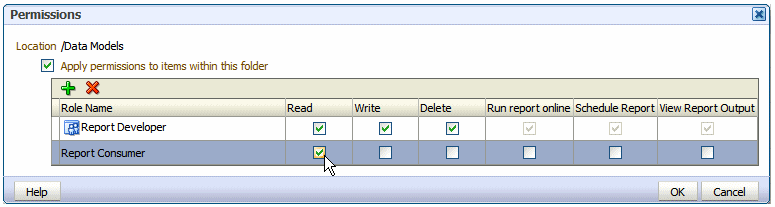
On the Permissions dialog (shown in Figure 3-5), configure the permissions required by the role.
Note the following:
-
The icon next to the Report Developer role indicates that this role is assigned one of the BI Publisher functional roles (in this case, the BI Publisher Developer role).
-
Once the Report Developer role is assigned access to this folder, the following permissions are automatically granted based on the privileges that comprise the BI Publisher Developer Role: Run report online, Scheduler Report, View Report Output.
-
-
If you are granting permissions on a Folder, select Apply permissions to items within this folder, if the permissions should apply to all objects.
3.8.4 Granting Data Access
A role must be granted access to a data source if the role must:
-
Run or schedule a report built on a data model that retrieves data from the data source
-
Create or edit a data model that retrieves data from the data source
To grant a role access to a data source:
-
Navigate to the BI Publisher Administration page.
-
Under Security Center, click Roles and Permissions.
-
On the Roles and Permissions page, locate the role, then click Add Data Sources.
-
On the Add Data Sources page you see a region for each of the following types of data sources:
-
Database Connections
-
File Directories
-
LDAP Connections
-
OLAP Connections
-
-
Use the shuttle buttons to move the required data sources from the Available Data Sources list to the Allowed Data Sources list.
-
When finished, click Apply.
3.9 Security and Catalog Organization
Because permissions are granted in the catalog, it is very important to be aware of this design when creating roles for your organization and when structuring the catalog.
For example, assume that your organization requires the roles that are described in Table 3-3.
Table 3-3 Example Role Requirements
| Role | Required Permissions |
|---|---|
|
Sales Report Consumer |
Needs to view and schedule Sales department reports. |
|
Financial Report Consumer |
Needs to view and schedule Financial department reports. |
|
Executive Report Consumer |
Needs to consume both Sales and Financial reports and executive level reports. |
|
Sales Report Developer |
Needs to create data models and reports for Sales department only. |
|
Financials Report Developer |
Needs to create data models and reports for Financials department only. |
|
Layout Designer |
Needs to design report layouts for all reports. |
You might consider setting up the catalog structure as described in Table 3-4.
Table 3-4 Example Catalog Setup
| Folder | Contents |
|---|---|
|
Sales Reports |
All reports for Sales Report Consumer. Also contains any Sub Templates and Style Templates associated with Sales reports. |
|
Sales Data Models |
All data models for Sales reports. |
|
Financials Reports |
All reports for Financials Report Consumer. Also contains any Sub Templates and Style Templates associated with Financials reports. |
|
Financials Data Models |
All data models for Financials reports |
|
Executive Reports |
All executive-level reports and data models. |
Set up the roles as follows:
Example Role Configuration
Sales Report Consumer:
Grant catalog permissions:
-
To the Sales Reports folder add the Sales Report Consumer and grant:
Read
Schedule Report
Run Report Online
View Report Online
Select Apply permissions to items within this folder
-
To the Sales Data Models folder add the Sales Report Consumer and grant:
Read
Grant Data Access:
On the Roles page, locate the role, then click Add Data Sources. Add all data sources used by Sales reports.
Financials Report Consumer
Grant catalog permissions:
-
To the Financials Reports folder add the Financials Report Consumer and grant:
Read
Schedule Report
Run Report Online
View Report Online
Select Apply permissions to items within this folder
-
To the Financials Data Models folder add the Financials Report Consumer and grant:
Read
Grant Data Access:
On the Roles page, locate the role, then click Add Data Sources. Add all data sources used by Financials reports.
Executive Report Consumer
Assign Roles:
On the Roles tab, assign the Executive Report Consumer the Sales Report Consumer and the Financials Report Consumer roles.
Grant catalog permissions:
-
To the Executive Reports folder add the Executive Report Consumer and grant:
Read
Schedule Report
Run Report Online
View Report Online
Select Apply permissions to items within this folder
Grant Data Access:
On the Roles tab, locate the role, then click Add Data Sources. Add all data sources used by Executive reports.
Sales Report Developer
Assign Roles:
On the Roles tab, assign the Sales Report Developer the BI Publisher Developer Role and the BI Publisher Template Designer Role.
Grant Data Access:
On the Roles tab, locate the Sales Report Developer and click Add Data Sources. Add all data sources from which Sales data models are built.
Grant Catalog Permissions:
-
In the catalog, to the Sales Data Models folder add the Sales Report Developer and grant:
Read, Write, Delete
-
To the Sales Reports folder, add the Sales Report Developer and grant:
Read, Write, Delete
Financials Report Developer
Assign Roles:
On the Roles tab, assign the Financials Report Developer the BI Publisher Developer Role, and the BI Publisher Template Designer Role.
Grant Data Access:
On the Roles tab, locate the Financials Report Developer and click Add Data Sources. Add all data sources from which Financials data models are built.
Grant Catalog Permissions:
-
In the catalog, to the Financials Data Models folder add the Financials Report Developer and grant:
Read, Write, Delete
-
To the Financials Reports folder, add the Financials Report Developer and grant:
Read, Write, Delete
Layout Designer
Assign Roles:
On the Roles tab, assign the Layout Designer the BI Publisher Template Designer Role and the BI Publisher Developer Role.
Grant Catalog Permissions:
-
In the catalog, to the Financials Data Models and the Sales Data Models folders add the Layout Designer Role and grant:
Read
-
To the Financials Reports and Sales Reports folders, add the Layout Designer and grant:
Read, Write, Delete
3.10 Using LDAP with BI Publisher
You can use BI Publisher with an LDAP provider for authentication only or for both authentication and authorization.
Important:
By default, BI Publisher allows every LDAP user to log in to the system even when no BI Publisher-specific roles are assigned to the user. Users cannot perform any functions that require roles, such as creating reports or data models; however if a user is assigned a role that is assigned permissions on catalog objects (such as traverse and open) the user will be able to perform those tasks.
To prevent users from logging in to BI Publisher unless they have a BI Publisher role assigned, see Section 3.10.3, "Disable Users Without BI Publisher-Specific Roles from Logging In."
3.10.1 Configuring BI Publisher to Use an LDAP Provider for Authentication Only
To use an LDAP provider for authentication in conjunction with another security model for authorization, perform the following in BI Publisher:
To configure BI Publisher to use LDAP for authentication only:
-
On the Administration page, under Security Center click Security Configuration.
-
Create a Local Superuser.
Enter a Superuser Name and Password and select Enable Local Superuser check box. Enabling a local superuser ensures that you can access the Administration page of BI Publisher in case of security model configuration errors.
-
Scroll down to the Authentication region. Select the Use LDAP check box.
-
Enter the following:
-
URL
For example: ldap://example.com:389/
If you are using LDAP over SSL, then note the following:
-
the protocol is "ldaps"
-
the default port is 636
An example URL would be: ldaps://example.com:636/
-
-
Administrator Username and Password for the LDAP server
The Administrator user entered here must also be a member of the XMLP_ADMIN group.
-
Distinguished Name for Users
For example: cn=Users,dc=example,dc=com
The distinguished name values are case-sensitive and must match the settings in the LDAP server.
-
JNDI Context Factory Class
The default value is com.sun.jndi.ldap.LdapCtxFactory
-
Attribute used for Login Username
Enter the attribute that supplies the value for the Login user name. This is also known as the Relative Distinguished Name (RDN). This value defaults to cn.
-
Attribute used for user matching with authorization system - enter the attribute that supplies the value to match users to the authorization system. For example, orcleguid.
-
-
Click Apply. Restart the BI Publisher server.
3.10.2 Configuring BI Publisher to Use an LDAP Provider for Authentication and Authorization
BI Publisher can be integrated with the LDAP provider to manage users and report access. Create the users and roles within the LDAP server, then configure the BI Publisher server to access the LDAP server.
In the BI Publisher security center module, assign folders to those roles. When users log in to the server, they have access to those folders and reports assigned to the LDAP roles.
Integrating the BI Publisher server with Oracle LDAP consists of three main tasks:
-
Set up users and roles in the LDAP provider
-
Configure BI Publisher to recognize the LDAP server
-
Assign catalog permissions and data access to roles
For information on supported LDAP servers, see "System Requirements and Certification" for the most up-to-date information on supported hardware and software.
3.10.2.1 Set Up Users and Roles in the LDAP Provider
The following steps must be performed in the LDAP provider. See the documentation for the provider for details on how to perform these tasks.
To set up users and roles:
-
In the Domain root node of the LDAP provider, create the roles that are described in Table 3-5 to integrate with BI Publisher. See Section 3.3, "Understanding BI Publisher's Users, Roles, and Permissions" for full descriptions of the required functional roles.
Table 3-5 Roles to Integrate with BI Publisher
BI Publisher System Group Description XMLP_ADMIN
The administrator role for the BI Publisher server. You must assign the Administrator account used to access your LDAP server the XMLP_ADMIN group.
XMLP_DEVELOPER
Allows users to create and edit reports and data models.
XMLP_SCHEDULER
Allows users to schedule reports.
XMLP_TEMPLATE_DESIGNER
Allows users to connect to the BI Publisher server from the Template Builder for Word and to upload and download templates. Allows users to design layouts using the BI Publisher Layout Editor.
-
Create other functional roles as required by your implementation (for example: HR Manager, Warehouse Clerk, or Sales Manager), and assign the appropriate BI Publisher functional roles.
-
Assign roles to users.
Note:
Ensure that you assign the Administrator account the XMLP_ADMIN role.
3.10.2.2 Configure the BI Publisher Server to Recognize the LDAP Server
To configure the BI Publisher server to recognize the LDAP server, update the Security properties in the BI Publisher Administration page.
Important:
Ensure that you understand your site's LDAP server configuration before entering values for the BI Publisher settings.
To configure the BI Publisher Server for the LDAP Server:
-
On the Administration page, under Security Center click Security Configuration.
-
Create a Local Superuser.
Enter a Superuser Name and Password and select Enable Local Superuser check box. Enabling a local superuser ensures that you can access the Administration page of BI Publisher in case of security model configuration errors.
-
Scroll down to the Authorization region. Select LDAP for the Security Model.
-
Enter the following:
-
URL
For example: ldap://example.com:389/
If you are using LDAP over SSL, then note the following:
-
the protocol is "ldaps"
-
the default port is 636
For example: ldaps://example.com:636/
-
-
Administrator Username and Password for the LDAP server
The Administrator user entered here must also be a member of the XMLP_ADMIN group.
-
Distinguished Name for Users
For example: cn=Users,dc=example,dc=com
The distinguished name values are case-sensitive and must match the settings in the LDAP server.
-
Distinguished Name for Groups
For example: cn=Groups,dc=us,dc=oracle,dc=com
The default value is cn=OracleDefaultDomain,cn=OracleDBSecurity,cn=Products,cn=OracleContext,dc=example,dc=com
-
Group Search Filter
The default value is (&(objectclass=groupofuniquenames)(cn=*))
-
Group Attribute Name
The default value is cn
-
Group Member Attribute Name
The default value is uniquemember
-
Member of Group Attribute Name
(Optional) Set this attribute only if memberOf attribute is available for User and Group. Group Member Attribute is not required when this attribute is available. Example: memberOf or wlsMemberOf
-
Group Description Attribute Name
The default value is description
-
JNDI Context Factory Class
The default value is com.sun.jndi.ldap.LdapCtxFactory
-
Group Retrieval Page Size
Setting this value enables support of the LDAPv3 control extension for simple paging of search results. By default, the BI Publisher server does not use pagination. This value determines the number of results to return on a page (for example, 200). Your LDAP server must support control type 1.2.840.113556.1.4.319 to support this feature, such as Oracle Internet Directory 10.1.4. Ensure that you check your LDAP server documentation for support of this control type before entering a value.
For more information about LDAP pagination and the required control type, see the article: RFC 2696 - LDAP Control Extension for Simple Paged Results Manipulation (
http://www.faqs.org/rfcs/rfc2696.html). -
Attribute used for Login Username
Enter the attribute that supplies the value for the Login user name. This is also known as the Relative Distinguished Name (RDN). This value defaults to cn.
-
Automatically clear LDAP cache - to schedule the automatic refresh of the LDAP cache the LDAP cache per a designated interval, select this box. After you select this box the following additional fields become enabled:
-
Enter an integer for Ldap Cache Interval. For example, to clear the LDAP cache once a day, enter 1.
-
Select the appropriate Ldap Cache Interval Unit: Day, Hour, or Minute.
-
-
Default User Group Name
(Optional) Use this option if your site has the requirement to allow all authenticated users access to a set of folders, reports, or other catalog objects. The user group name that you enter here is added to all authenticated users. Any catalog or data source permissions that you assign to this default user group are granted to all users.
-
Attribute Names for Data Query Bind Variables
(Optional) Use this property to set attribute values to be used as bind variables in a data query. Enter LDAP attribute names separated by a commas for example: memberOf, primaryGroupID,mail
See the section "Creating Bind Variables from LDAP User Attributes" in the Oracle Fusion Middleware Data Modeling Guide for Oracle Business Intelligence Publisher.
-
-
Click Apply. Restart the BI Publisher server.
Figure 3-6 shows a sample of the LDAP security model entry fields from the Security Configuration page.
Figure 3-6 Sample of LDAP Security Model Entry Fields
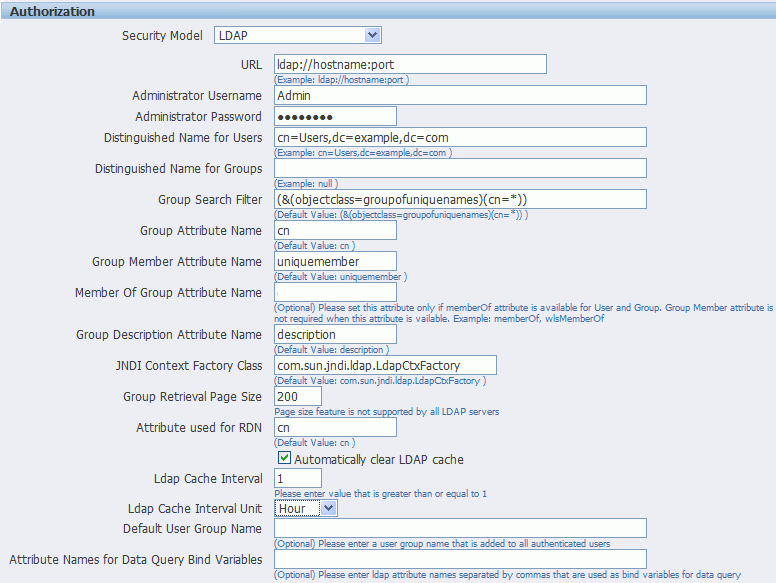
Description of "Figure 3-6 Sample of LDAP Security Model Entry Fields"
If you are configuring BI Publisher to use LDAP over SSL, then you must also configure Java keystore to add the server certificate to JVM. For more information, see Section 4.3, "Configuring BI Publisher for Secure Socket Layer (SSL) Communication."
3.10.2.3 Assign Data Access and Catalog Permissions to Roles
To assign data access and catalog permissions to roles:
-
Log in to BI Publisher as a user assigned the XMLP_ADMIN role in the LDAP provider.
-
On the Administration page click Roles and Permissions.
You see the roles that you created in the LDAP provider to which you assigned the XMLP_ roles. Note the following:
-
The XMLP_X roles are not shown because these are controlled through the LDAP interface.
-
The Users tab is no longer available under the Security Center because users are now managed through your LDAP interface.
-
Roles are not updatable in the BI Publisher interface, except for adding data sources.
-
-
Click Add Data Sources to add BI Publisher data sources to the role. A role must be assigned access to a data source to run reports from that data source or to build data models from the data source. For more information see Section 3.8.4, "Granting Data Access."
-
Grant catalog permissions to roles. See Section 3.5, "About Catalog Permissions" and Section 3.8.3, "Granting Catalog Permissions" for details on granting catalog permissions to roles.
Users can now log in using their LDAP username/password.
3.10.3 Disable Users Without BI Publisher-Specific Roles from Logging In
To disable users without BI Publisher-specific roles from logging in to the BI Publisher server, set a configuration property in the xmlp-server-config.xml file located at:
<repository>/Admin/Configuration/xmlp-server-config.xml
In the xmlp-server-config.xml file, add the following property and setting:
<property name="REQUIRE_XMLP_ROLE_FOR_LOGIN" value="true"/>
3.11 Integrating with Microsoft Active Directory
Microsoft Active Directory supports the LDAP interface and therefore can be configured with BI Publisher using LDAP Security.
3.11.1 Configuring the Active Directory
To configure the active directory:
-
Add users who must access BI Publisher.
Add the users under "Users" or any other organization unit in the Domain Root.
-
Add the BI Publisher system groups. The Scope of the groups must be Domain Local.
Table 3-6 describes the BI Publisher system groups that must be added.
Table 3-6 BI Publisher System Groups
BI Publisher System Group Description XMLP_ADMIN
The administrator role for the BI Publisher server. You must assign the Administrator account used to access your LDAP server the XMLP_ADMIN group.
XMLP_DEVELOPER
Allows users to create and edit reports and data models.
XMLP_SCHEDULER
Allows users to schedule reports.
XMLP_TEMPLATE_DESIGNER
Allows users to connect to the BI Publisher server from the Template Builder for Word and to upload and download templates. Allows users to design layouts using the BI Publisher Layout Editor.
-
Grant BI Publisher system groups to global groups or users.
You can grant BI Publisher system groups directly to users or through global groups.
Example 1: Grant Users the BI Publisher Administrator Role
-
Under the Active Directory User and Computers, open the XMLP_ADMIN group and click the Members tab.
-
Click Add to add users who need to BI Publisher Administrator privileges.
Example 2: Grant Users Access to Scheduling Reports
The "HR Manager" global group is defined under "Users".
All users in this group need to schedule reports.
To achieve this, add "HR Manager" as a Member of the XMLP_SCHEDULER group.
3.11.2 Configuring BI Publisher
To configure BI Publisher:
-
On the Administration page, click Security Configuration.
-
Set up a Local Superuser if one has not been configured. This is very important in case the security configuration fails, you must still be able to log in to BI Publisher using the Superuser credentials.
-
In the Authorization region of the page, select LDAP from the Security Model list.
-
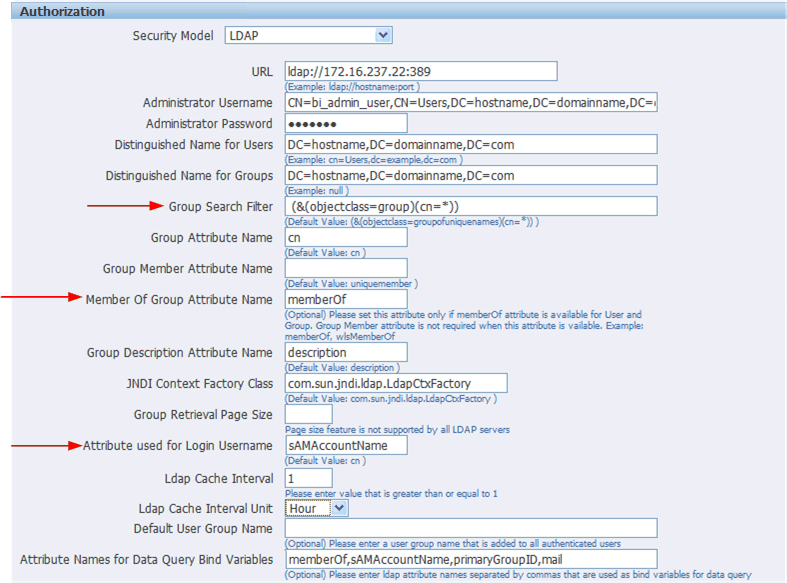
Enter the details for the Active Directory server, as described in Section 3.10.2.2, "Configure the BI Publisher Server to Recognize the LDAP Server," noting the following specific information for Active Directory:
-
Set Group Search Filter objectclass to "group"
-
Set Member of Group Member Attribute Name to "memberOf" (Group Member Attribute Name can be left blank).
-
Set Attribute used for Login Username to "sAMAccountName".
-
If your are using LDAP over SSL note the following:
-
the protocol is "ldaps"
-
the default port is 636
An example URL would be: ldaps://example.com:636/
-
Figure 3-7 shows an example configuration highlighting the recommendations stated above.
-
-
Click Apply. Restart the BI Publisher application.
If you are configuring BI Publisher to use LDAP over SSL, then you must also configure Java keystore to add the server certificate to JVM. For more information, see Section 4.3, "Configuring BI Publisher for Secure Socket Layer (SSL) Communication."
3.11.3 Logging In to BI Publisher Using the Active Directory Credentials
The User login name defined in Active Directory Users and Computers >User Properties >Account is used for the BI Publisher login name. Add the Domain to the user name to log in to BI Publisher. For example: "scott_tiger@domainname.com".
Note the following:
-
The Attribute used for Login Username can be sAMAccountName instead of userPrincipalName.
-
You must use sAMAccountName for the Attribute used for Login Username when the "User logon name (pre-Windows 2000)" is required to use for the BI Publisher login username.
-
User names must be unique across all organization units.
3.11.4 Assign Data Access and Catalog Permissions to Roles
To assign data access and catalog permissions to roles:
-
Log in to BI Publisher as a user assigned the XMLP_ADMIN role in Active Directory.
-
On the Administration page click Roles and Permissions.
You see the roles that you created in Active Directory to which you assigned the XMLP_ roles. Note the following:
-
The XMLP_X roles are not shown because these are controlled through the Active Directory interface.
-
The Users tab is no longer available under the Security Center because users are now managed through Active Directory.
-
Roles are not updatable in the BI Publisher interface, except for adding data sources.
-
-
Click Add Data Sources to add BI Publisher data sources to the role. A role must be assigned access to a data source to run reports from that data source or to build data models from the data source. For more information see Section 3.8.4, "Granting Data Access."
-
Grant catalog permissions to roles. See Section 3.5, "About Catalog Permissions" and Section 3.8.3, "Granting Catalog Permissions" for details on granting catalog permissions to roles.
3.12 Configuring BI Publisher with Single Sign-on (SSO)
Integrating a single sign-on (SSO) solution enables a user to log on (sign-on) and be authenticated once. Thereafter, the authenticated user is given access to system components or resources according to the permissions and privileges granted to that user. Oracle Business Intelligence can be configured to trust incoming HTTP requests authenticated by a SSO solution that is configured for use with Oracle Fusion Middleware and Oracle WebLogic Server. For more information about configuring SSO for Oracle Fusion Middleware, see "Configuring Single Sign-On in Oracle Fusion Middleware" in Oracle Fusion Middleware Application Security Guide.
When BI Publisher is configured to use SSO authentication, it accepts authenticated users from whatever SSO solution Oracle Fusion Middleware is configured to use. If SSO is not enabled, then BI Publisher challenges each user for authentication credentials. When BI Publisher is configured to use SSO, a user is first redirected to the SSO solution's login page for authentication.
Configuring BI Publisher to work with SSO authentication requires minimally that the following be done:
-
Oracle Fusion Middleware and Oracle WebLogic Server are configured to accept SSO authentication. Oracle Access Manager is recommended in production environments.
-
BI Publisher is configured to trust incoming messages.
-
The HTTP header information required for identity propagation with SSO configurations (namely, user identity and SSO cookie) is specified and configured.
3.12.1 How BI Publisher Operates with SSO Authentication
After SSO authorization has been implemented, BI Publisher operates as if the incoming web request is from a user authenticated by the SSO solution. User personalization and access controls such as data-level security are maintained in this environment.
3.12.2 Tasks for Setting Up SSO Authentication with BI Publisher
Table 3-7 contains SSO authentication configuration tasks and provides links for obtaining more information.
Table 3-7 Task Map: Configuring SSO Authentication for BI Publisher
| Task | Description | For More Information |
|---|---|---|
|
Configure Oracle Access Manager as the SSO authentication provider. |
Configure Oracle Access Manager to protect the BI Publisher URL entry points. |
Section 3.13, "Configuring SSO in an Oracle Access Manager Environment" Also see: "Configuring Single Sign-On in Oracle Fusion Middleware" in Oracle Fusion Middleware Application Security Guide |
|
Configure the HTTP proxy. |
Configure the web proxy to forward requests from BI Publisher to the SSO provider. |
"Configuring Single Sign-On in Oracle Fusion Middleware" in Oracle Fusion Middleware Application Security Guide |
|
Configure a new authenticator for Oracle WebLogic Server. |
Configure the Oracle WebLogic Server domain in which BI Publisher is installed to use the new identity store. |
Section 3.13.1, "Configuring a New Authenticator for Oracle WebLogic Server" Also see: Oracle Fusion Middleware Oracle WebLogic Server Administration Console Online Help |
|
Configure a new identity asserter for Oracle WebLogic Server. |
Configure the Oracle WebLogic Server domain in which BI Publisher is installed to use the SSO provider as an asserter. |
Section 3.13.2, "Configuring OAM as a New Identity Asserter for Oracle WebLogic Server" Also see: Oracle Fusion Middleware Oracle WebLogic Server Administration Console Online Help |
|
Configure the new trusted system user to replace the default BISystemUser. |
Add the new trusted system user name from Oracle Internet Directory to become a member of the BISystem application role. |
See "Configuring a New Trusted User (BISystem User)" in Oracle Fusion Middleware Security Guide for Oracle Business Intelligence Enterprise Edition |
|
Enable BI Publisher to accept SSO authentication. |
Enable the SSO provider configured to work with BI Publisher. |
Section 3.13.3, "Configuring BI Publisher for Oracle Fusion Middleware Security" |
Note:
For an example of an Oracle Business Intelligence SSO installation scenario, see Oracle Fusion Middleware Enterprise Deployment Guide for Oracle Business Intelligence.
3.13 Configuring SSO in an Oracle Access Manager Environment
For information about how to configure Oracle Access Manager as the SSO authentication provider for Oracle Fusion Middleware with WebLogic Server, see "Configuring Single Sign-On in Oracle Fusion Middleware" in Oracle Fusion Middleware Application Security Guide. For more information about managing Oracle Access Manager, see Oracle Fusion Middleware Administrator's Guide for Oracle Access Manager.
After the Oracle Fusion Middleware environment is configured, in general the following must be done to configure BI Publisher:
-
Configure the SSO provider to protect the BI Publisher URL entry points.
-
Configure the web server to forward requests from BI Publisher to the SSO provider.
-
Configure the new identity store as the main authentication source for the Oracle WebLogic Server domain in which BI Publisher has been installed. For more information, see Section 3.13.1, "Configuring a New Authenticator for Oracle WebLogic Server.".
-
Configure the Oracle WebLogic Server domain in which BI Publisher is installed to use an Oracle Access Manager asserter. For more information, see Section 3.13.2, "Configuring OAM as a New Identity Asserter for Oracle WebLogic Server.".
-
After configuration of the SSO environment is complete, enable SSO authentication for BI Publisher. For more information, see Section 3.13.3, "Configuring BI Publisher for Oracle Fusion Middleware Security.".
3.13.1 Configuring a New Authenticator for Oracle WebLogic Server
After installing BI Publisher, the Oracle WebLogic Server embedded LDAP server is the default authentication source (identity store). To use a new identity store (for example, OID), as the main authentication source, you must configure the Oracle WebLogic Server domain (where BI Publisher is installed).
For more information about configuring authentication providers in Oracle WebLogic Server, see Oracle Fusion Middleware Securing Oracle WebLogic Server.
To configure a new authenticator in Oracle WebLogic Server:
-
Log in to Oracle WebLogic Server Administration Console and click Lock & Edit in the Change Center.
-
Select Security Realms from the left pane and click myrealm.
The default Security Realm is named myrealm.
-
Display the Providers tab, then display the Authentication sub-tab.
-
Click New to launch the Create a New Authentication Provider page.
Complete the fields as follows:
-
Name: OID Provider, or a name of your choosing.
-
Type: OracleInternetDirectoryAuthenticator
-
Click OK to save the changes and display the authentication providers list updated with the new authentication provider.
-
-
Click the newly added authenticator in the authentication providers table.
-
Navigate to Settings, then select the Configuration\Common tab:
-
Select SUFFICIENT from the Control Flag list.
-
Click Save.
-
-
Display the Provider Specific tab and specify the following settings using appropriate values for your environment:
Section Name Field Name Description Connection
Host
The LDAP host name. For example, <localhost>.
Connection
Port
The LDAP host listening port number. For example, 6050.
Connection
Principal
The distinguished name (DN) of the user that connects to the LDAP server. For example, cn=orcladmin.
Connection
Credential
The password for the LDAP administrative user entered as the Principal.
Users
User Base DN
The base distinguished name (DN) of the LDAP server tree that contains users. For example, use the same value as in Oracle Access Manager.
Users
All Users Filter
The LDAP search filter. For example, (&(uid=*) (objectclass=person)). The asterisk (*) filters for all users. Click More Info... for details.
Users
User From Name Filter
The LDAP search filter. Click More Info... for details.
Users
User Name Attribute
The attribute that you want to use to authenticate (for example, cn, uid, or mail). Set as the default attribute for user name in the directory server. For example, uid.
Note: The value that you specify here must match the User Name Attribute that you are using in the authentication provider.
Groups
Group Base DN
The base distinguished name (DN) of the LDAP server tree that contains groups (same as User Base DN).
General
GUID attribute
The attribute used to define object GUIDs in LDAP.
orclguid
For more information about configuring authentication providers in Oracle WebLogic Server, see Oracle Fusion Middleware Securing Oracle WebLogic Server.
-
Click Save.
-
Perform the following steps to set up the default authenticator for use with the Identity Asserter:
-
At the main Settings for myrealm page, display the Providers tab, then display the Authentication sub-tab, then select DefaultAuthenticator to display its configuration page.
-
Display the Configuration\Common tab and select 'SUFFICIENT' from the Control Flag list.
-
Click Save.
-
-
Perform the following steps to reorder Providers:
-
Display the Providers tab.
-
Click Reorder to display the Reorder Authentication Providers page
-
Select a provider name and use the arrow buttons to order the list of providers as follows:
-
OID Authenticator (SUFFICIENT)
-
OAM Identity Asserter (REQUIRED)
-
Default Authenticator (SUFFICIENT)
-
-
Click OK to save your changes.
-
-
In the Change Center, click Activate Changes.
-
Restart Oracle WebLogic Server.
3.13.2 Configuring OAM as a New Identity Asserter for Oracle WebLogic Server
The Oracle WebLogic Server domain in which BI Publisher is installed must be configured to use an Oracle Access Manager asserter.
For more information about creating a new asserter in Oracle WebLogic Server, see Oracle Fusion Middleware Oracle WebLogic Server Administration Console Online Help.
To configure Oracle Access Manager as the new asserter for Oracle WebLogic Server:
-
Log in to Oracle WebLogic Server Administration Console.
-
In Oracle WebLogic Server Administration Console, select Security Realms from the left pane and click the realm you are configuring. For example, myrealm. Select Providers.
-
Click New. Complete the fields as follows:
-
Name: OAM Provider, or a name of your choosing.
-
Type: OAMIdentityAsserter.
-
-
Click OK.
-
Click Save.
-
In the Providers tab, perform the following steps to reorder Providers:
-
Click Reorder
-
In the Reorder Authentication Providers page, select a provider name, and use the arrows beside the list to order the providers as follows:
-
OID Authenticator (SUFFICIENT)
-
OAM Identity Asserter (REQUIRED)
-
Default Authenticator (SUFFICIENT)
-
-
Click OK to save your changes.
-
-
In the Change Center, click Activate Changes.
-
Restart Oracle WebLogic Server.
You can verify that Oracle Internet Directory is the new identity store (default authenticator) by logging back into Oracle WebLogic Server and verifying the users and groups stored in the LDAP server appear in the console.
-
Use Fusion Middleware Control to enable SSO authentication.
3.13.3 Configuring BI Publisher for Oracle Fusion Middleware Security
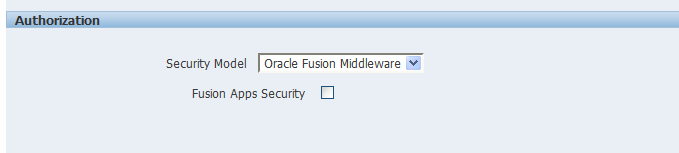
After Oracle WebLogic Server has been configured, navigate to the BI Publisher Administration Security Configuration page. In the Authorization region select Oracle Fusion Middleware as the Security Model as shown in the following figure:
3.14 Setting Up Oracle Single Sign-On
To set up Oracle Single Sign-On, first configure WebLogic Server using the instructions in the chapter, "Configuring Single Sign-On in Oracle Fusion Middleware" in Oracle Fusion Middleware Application Security Guide. BI Publisher must be configured to use Oracle Internet Directory as the default LDAP server.
Note:
When using Oracle SSO, BI Publisher assumes that a login user name can be derived from Osso-User-Dn, which is HTTP Header value. For example, if the Osso-User-Dn on HTTP Header looks like this:
cn=admin,cn=users, dc=us,dc=oracle,dc=com
Then BI Publisher assumes the value of first cn= is the login user name (that is, "admin" in this case).
Therefore if your Osso-User-Dn does not contain a login user name as the first cn value, then select "Other SSO Type" to configure the settings (even if you use Oracle SSO).
3.14.1 Setup Procedure
To set up SSO:
-
Modify the application server configuration file to protect the xmlpserver. See the section "Configuring mod_osso to Protect Web Resources" in Oracle Fusion Middleware Application Security Guide.
-
In the mod_osso.conf add a new "Location" directive as follows:
<!-- Protect xmlpserver --> <Location /xmlpserver> require valid-user AuthType Basic </Location> -
To allow Web service communication between BI Publisher and its client component (the Template Builder) you must make additional modifications to the mod_osso.conf file. To open up the xmlpserver to allow these Web services, enter the following directives:
<Location /xmlpserver/services/> require valid-user AuthType Basic Allow from All Satisfy any </Location> <Location /xmlpserver/report_service/> require valid-user AuthType Basic Allow from All Satisfy any </Location> Location /xmlpserver/ReportTemplateService.xls/> require valid-user AuthType Basic Allow from All Satisfy any </Location> -
For integration with Oracle BI Presentation Services, you must disable SSO for Web services between the BI Presentation Services server and the BI Publisher server. If you made this entry when performing the previous step, then you do not need to repeat this setup.
To open up the xmlpserver to allow the Web service, enter the following directive in the mod_osso.conf file:
<Location /xmlpserver/services/> require valid-user AuthType Basic Allow from All Satisfy any </Location>A sample mod_osso.conf file with the entries discussed in this section is shown below:
LoadModule osso_module libexec/mod_osso.so <IfModule mod_osso.c> OssoIpCheck off OssoIdleTimeout off OssoConfigFile /home/as1013/ohome/Apache/Apache/conf/osso/osso.conf <Location /xmlpserver> require valid-user AuthType Basic </Location> <Location /xmlpserver/services/> require valid-user AuthType Basic Allow from All Satisfy any </Location> <Location /xmlpserver/report_service/> require valid-user AuthType Basic Allow from All Satisfy any </Location> Location /xmlpserver/ReportTemplateService.xls/> require valid-user AuthType Basic Allow from All Satisfy any </Location> <Location /xmlpserver/Guest/> require valid-user AuthType Basic Allow from All Satisfy any </Location> # # Insert Protected Resources: (see Notes below for how to protect resources) # #______- # # Notes # #______- # # 1. Here's what you need to add to protect a resource, # e.g. <ApacheServerRoot>/htdocs/private: # # <Location /private> # require valid-user # AuthType Basic # </Location> # </IfModule> # # If you would like to have short hostnames redirected to # fully qualified hostnames to allow clients that need # authentication through mod_osso to be able to enter short # hostnames into their browsers uncomment out the following # lines # #PerlModule Apache::ShortHostnameRedirect #PerlHeaderParserHandler Apache::ShortHostnameRedirect -
Restart the HTTP server.
-
In BI Publisher: Set up the Single Sign-Off URL on the BI Publisher Security Configuration page.
On the Administration page, click Security Configuration. In the Authentication region:
-
Select Use Single Sign-On
-
From the Single Sign-On Type list, select Oracle Single Sign On
-
Enter the Single Sign-Off URL with the value you wrote down in the preceding step. The remaining fields are not applicable to Oracle SSO.
A sample BI Publisher Security Configuration page is shown in Figure 3-9.
Figure 3-9 Sample BI Publisher Security Configuration Page
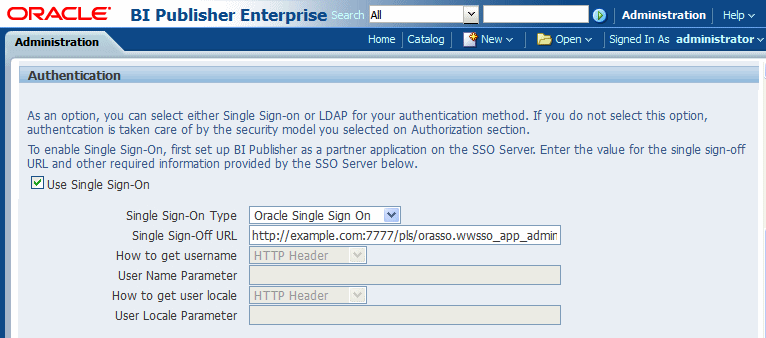
Description of "Figure 3-9 Sample BI Publisher Security Configuration Page"
-
-
Create a BI Publisher Local Superuser to ensure access to BI Publisher regardless of your selected security configuration. See Section 4.1, "Enabling a Local Superuser" for more information.
-
Click Apply. Restart the application through the Oracle Fusion Middleware Control page.
-
Enter the URL to access the BI Publisher Enterprise application, and you are redirected to the SSO login page.