5 Working with Oracle HTTP Server
This chapter describes some common tasks you might be required to perform when working with an installed version of Oracle HTTP Server. It contains the following sections:
5.1 About Editing Configuration Files
For instances that are part of a WebLogic Server Domain, Fusion Middleware Control and the management infrastructure manages the Oracle HTTP Server configuration. Direct editing of the configuration in the staging directory is subject to being overwritten after subsequent management operations, including modifying the configuration in Fusion Middleware Control. For such instances, direct editing should only be performed when the administration server is stopped. When the administration server is subsequently started (or restarted), the results of any manual edits will be replicated to the run-time directory on the node of the managed instance.
For more information, see Section 1.6, "Understanding Configuration Files."
The following sections provide more information on modifying configuration files.
-
Section 5.1.1, "Editing a Configuration File for a Standalone Domain."
-
Section 5.1.2, "Editing a Configuration File for a WebLogic Server Domain."
5.1.1 Editing a Configuration File for a Standalone Domain
For standalone instances, you can edit the configuration directly within the staging directory at any time. The runtime config files are updated on start, restart or stopping of the OHS instance.
5.1.2 Editing a Configuration File for a WebLogic Server Domain
You can open and edit configuration files from within Fusion Middleware Control. Follow these steps to modify the files.
-
Select Administration from the HTTP Server menu.
-
Select Advanced Configuration from the Administration menu item.
-
In the Advanced Server Configuration page, select the configuration file from the Select File drop-down list, such as the
httpd.conffile, then click Go. -
Edit the file, as needed.
-
Review the settings. If the settings are correct, click Apply to apply the changes. If the settings are incorrect, or you decide to not apply the changes, click Revert to return to the original settings.
-
Restart Oracle HTTP Server as described in Section 4.3.5, "Restarting Oracle HTTP Server Instances".
The file is saved and displayed on the Advanced Server Configuration page.
5.2 Specifying Server Properties
You can set Oracle HTTP Server properties only by using Fusion Middleware Control or by directly editing the Oracle HTTP Server configuration files. You cannot use WLST commands to specify the server properties.
-
Section 5.2.1, "Specifying Server Properties Using Fusion Middleware Control"
-
Section 5.2.2, "Specify Server Properties by Editing the httpd.conf File"
5.2.1 Specifying Server Properties Using Fusion Middleware Control
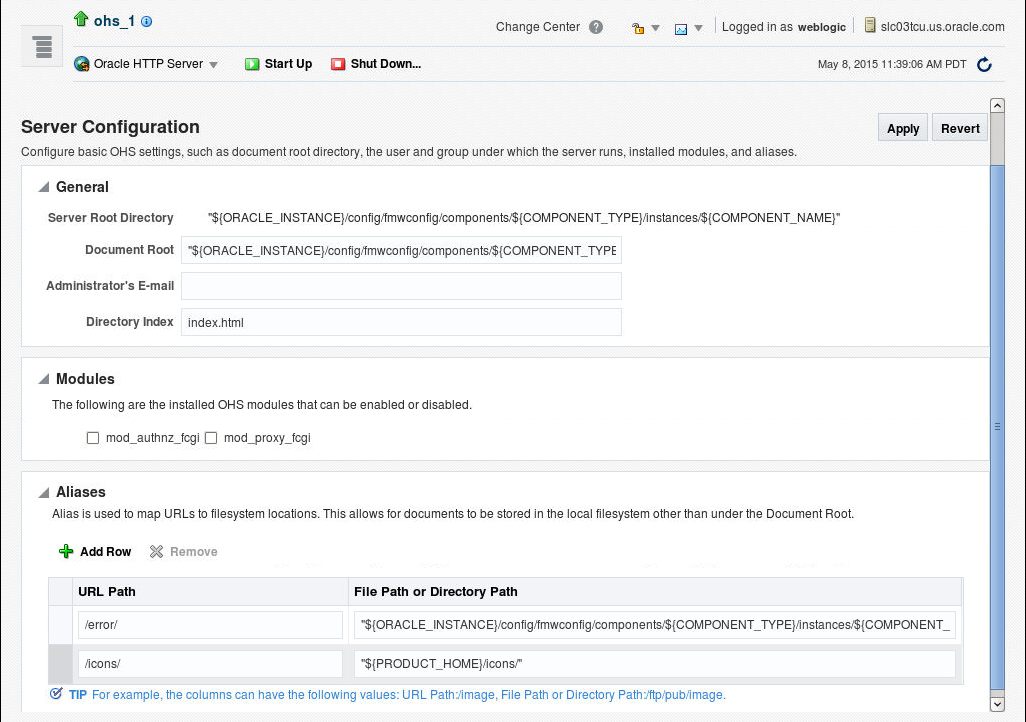
Server properties include items like the document root, the administrator's e-mail address, the directory index and operating system details. Follow these steps to specify the server properties by using Fusion Middleware Control.
-
Select Administration from the Oracle HTTP Server menu.
-
Select Server Configuration from the Administration menu.
Description of the illustration ''srv_prop3.png''
-
In the Server Configuration page, enter the server properties.
-
Enter the documentation root directory in the Document Root field that forms the main document tree visible from the website.
-
Enter the e-mail address in the Administrator's E-mail field that the server will include in error messages sent to the client.
-
Enter the directory index in the Directory Index field. The is the main (index) page that will be displayed when a client first accesses the website.
-
Use the Modules region to enable or disable modules. The available modules are mod_authnz_fcgi and mod_proxy_fcgi. See also Section 5.3.7, "About Configuring mod_proxy_fcgi."
-
Create an alias, if necessary in the Aliases table. An alias maps to a specified directory. For example, to use a specific set of content pages for a group you can create an alias to the directory that has the content pages.
-
-
Review the settings. If the settings are correct, click Apply to apply the changes. If the settings are incorrect, or you decide to not apply the changes, click Revert to return to the original settings.
-
Restart Oracle HTTP Server as described in Section 4.3.5, "Restarting Oracle HTTP Server Instances".
The server properties are saved, and shown on the Server Configuration page.
5.2.2 Specify Server Properties by Editing the httpd.conf File
You can specify server properties by manually editing the httpd.conf file. Follow these steps to edit the httpd.conf file.
Note:
Before attempting to edit any.conf file, you should familiarize yourself with the layout of the configuration file directories, mechanisms for editing the files, and learn more about the files themselves. For this information, see Section 1.6, "Understanding Configuration Files".-
Open the
httpd.conffile (the "master" or "staging" copy: $DOMAIN_HOME/config/fmwconfig/components/OHS/ohs1/httpd.conf)by using either a text editor or the Advanced Server Configuration page in Fusion Middleware Control. (See Section 1.6.3, "Modifying an Oracle HTTP Server Configuration File.") -
In the
DocumentRootsection of the file, enter the directory that stores the main content for the website. The following is an example of the syntax:DocumentRoot "${ORACLE_INSTANCE}/config/fmwconfig/components/${COMPONENT_TYPE}/instances/${COMPONENT_NAME}/htdocs" -
In the ServerAdmin section of the file, enter the administrator's email address. This is the e-mail address that will appear on client pages. The following is an example of the syntax:
ServerAdmin WebMaster@example.com
-
In the DirectoryIndex section of the file, enter the directory index. This is the main (index) page that will be displayed when a client first accesses the website. The following is an example of the syntax:
DirectoryIndex index.html index.html.var
-
Create aliases, if needed. An alias maps to a specified directory. For example, to use a specific set of icons, you can create an alias to the directory that has the icons for the Web pages. The following is an example of the syntax:
Alias /icons/ "${PRODUCT_HOME}/icons/"<Directory "${PRODUCT_HOME}/icons"> Options Indexes MultiViews AllowOverride None Require all granted</Directory> -
Save the file.
-
Restart Oracle HTTP Server as described in Section 4.3.5, "Restarting Oracle HTTP Server Instances".
5.3 Configuring Oracle HTTP Server Instances
This section describes some of the common Oracle HTTP Server instance configuration procedures, such as secure sockets, MIME settings, Oracle WebLogic Server Proxy Plug-In (mod_wl_ohs), mod_proxy_fcgi and others.
Note:
This section does not include initial system configuration information; for those configuration instructions, see Installing and Configuring Oracle HTTP Server.This section includes the following information:
-
Section 5.3.2, "Configuring Secure Sockets Layer in Standalone Mode"
-
Section 5.3.3, "Exporting the Keystore to an Oracle HTTP Server Instance Using WLST"
-
Section 5.3.4, "Importing Wallets to the KSS Database after an Upgrade Using WLST"
-
Section 5.3.5, "Associating Oracle HTTP Server Instances With a Keystore Using WLST"
-
Section 5.3.6, "Configuring MIME Settings using Fusion Middleware Control"
-
Section 5.3.8, "About Configuring the Oracle WebLogic Server Proxy Plug-In (mod_wl_ohs)"
-
Section 5.3.10, "Using the apxs Command to Install Extension Modules"
-
Section 5.3.12, "Updating Oracle HTTP Server Component Configurations on a Shared Filesystem"
Note:
Fusion Middleware Control and other Oracle software which manage the Oracle HTTP Server configuration might save configuration files in a different, equivalent format. After using the software to make a configuration change, multiple configuration files might be rewritten.5.3.1 Secure Sockets Layer Configuration
Secure Sockets Layer (SSL) is an encrypted communication protocol that is designed to securely send messages across the Internet. It resides between Oracle HTTP Server on the application layer and the TCP/IP layer, transparently handling encryption and decryption when a secure connection is made by a client.
One common use of SSL is to secure Web HTTP communication between a browser and a Web server. This case does not preclude the use of non-secured HTTP. The secure version is simply HTTP over SSL (HTTPS). The differences are that HTTPS uses the URL scheme https:// rather than http://. The default communication port is 4443 in Oracle HTTP Server. Oracle HTTP Server does not use the 443 standard https:// privileged port because of security implications. For information about running Oracle HTTP Server on privileged ports see Section 4.3.3.4, "Starting Oracle HTTP Server Instances on a Privileged Port (UNIX Only)."
By default, an SSL listen port is configured and enabled using a default wallet during installation. Wallets store your credentials, such as certificate requests, certificates, and private keys.
The default wallet that is automatically installed with Oracle HTTP Server is for testing purposes only. A real wallet must be created for your production server. The default wallet is located in the DOMAIN_HOME/config/fmwconfig/components/OHS/instances/componentName/keystores/default directory. You can either place the new wallet in this location, or change the SSLWallet directive in DOMAIN_HOME/config/fmwconfig/components/OHS/componentName/ssl.conf to point to the location of your real wallet.
For the changes to take effect, restart Oracle HTTP Server, as described in Section 4.3.5, "Restarting Oracle HTTP Server Instances".
For information about configuring wallets and SSL by using Fusion Middleware Control, see "Enabling SSL for Oracle HTTP Server Virtual Hosts" in the Administering Oracle Fusion Middleware.
5.3.2 Configuring Secure Sockets Layer in Standalone Mode
The following sections contain information about how to enable and configure SSL for Oracle HTTP Server in standalone mode. These instructions use the mod_ossl module to Oracle HTTP Server which enables the server to use SSL.
-
Section 5.3.2.2, "Specify SSLVerifyClient on the Server Side"
-
Section 5.3.2.3, "Enable SSL Between Oracle HTTP Server and Oracle WebLogic Server"
5.3.2.1 Configure SSL
By default, SSL is enabled when you install Oracle HTTP Server. Perform these tasks to modify and configure SSL:
5.3.2.1.1 Task 1: Create a Real Wallet
To configure Oracle HTTP Server for SSL, you need a wallet that contains the certificate for the server. Wallets store your credentials, such as certificate requests, certificates, and private keys.
The default wallet that is automatically installed with Oracle HTTP Server is for testing purposes only. A real wallet must be created for your production server. The default wallet is located in $ORACLE_INSTANCE/config/fmwconfig/components/$COMPONENT_TYPE/instances/$COMPONENT_NAME/keystores/default. You can either place the new wallet in that location, or change the SSLWallet directive in $ORACLE_INSTANCE/config/fmwconfig/components/$COMPONENT_TYPE/$COMPONENT_NAME/ssl.conf (the pre-installation location) to point to the location of your real wallet.
See Also:
"orapki" in Administering Oracle Fusion Middleware for instructions on creating a wallet. It is important that you do the following:Generate a certificate request: For the Common Name, specify the name or alias of the site you are configuring. Make sure that you enable this auto_login_only feature.
5.3.2.1.2 Task 2: (Optional) Customize Your Configuration
Optionally, you can further customize your configuration using mod_ossl directives.
See Also:
-
Section G.3, "mod_ossl Module" for a list and descriptions of directives accepted by
mod_ossl. -
Section G.3.5, "SSLFIPS Directive" for information on how to configure the
SSLFIPSdirective and a list of the cipher suites it accepts.
Note:
The files installed during configuration contain all of the necessary SSL configuration directives and a default setup for SSL.5.3.2.1.3 Basic SSL Configuration Example
Your SSL configuration must contain, at minimum, the directives in the following example.
LoadModule ossl_module "${PRODUCT_HOME}/modules/mod_ossl.so"
Listen 4443
ServerName www.testohs.com
SSLEngine on
# SSL Protocol Support:
# List the supported protocols.
SSLProtocol TLSv1.2 TLSv1.1 TLSv1
# SSL Cipher Suite:
# List the ciphers that the client is permitted to negotiate.
SSLCipherSuite SSL_RSA_WITH_RC4_128_MD5,SSL_RSA_WITH_RC4_128_SHA,SSL_RSA_WITH_3DES_EDE_CBC_SHA,TLS_RSA_WITH_AES_128_CBC_SHA,TLS_RSA_WITH_AES_256_CBC_SHA
SSLWallet "${ORACLE_INSTANCE}/config/fmwconfig/components/${COMPONENT_TYPE}/instances/${COMPONENT_NAME}/keystores/default"
</VirtualHost>To enable client authentication, do the following:
5.3.2.2 Specify SSLVerifyClient on the Server Side
There are different ways of using the SSLVerifyClient directive to authenticate and authorize access. Use the appropriate client certificate on your client side for the HTTPS connection. See your client documentation for information on getting and using a client certificate. Be sure that your client certificate is trusted by the server wallet.
-
Section 5.3.2.2.1, "Forcing Clients to Authenticate Using Certificates"
-
Section 5.3.2.2.2, "Forcing a Client to Authenticate for a Particular URL"
-
Section 5.3.2.2.3, "Authorizing a Client for a Particular URL"
See Also:
"Importing a Certificate or a Trusted Certificate Using WLST" in Administering Oracle Fusion Middleware Guide for instructions on how to import a trusted certificate into your wallet.5.3.2.2.1 Forcing Clients to Authenticate Using Certificates
You can force the client to validate its client certificate and allow access to the server using SSLVerifyClient. This scenario is valid for all clients having a client certificate supplied by the server Certificate Authority (CA). The server can validate client's supplied certificates against its CA for additional permission.
# require a client certificate which has to be directly
# signed by our CA certificate
SSLVerifyClient require
SSLWallet "${ORACLE_INSTANCE}/config/fmwconfig/components/${COMPONENT_TYPE}/instances/${COMPONENT_NAME}/keystores/default"
5.3.2.2.2 Forcing a Client to Authenticate for a Particular URL
To force a client to authenticate using certificates for a particular URL, you can use the per-directory reconfiguration features of mod_ossl. In this case, the SSLVerifyClient appears in a Location block.
SSLVerifyClient none
SSLWallet "${ORACLE_INSTANCE}/config/fmwconfig/components/${COMPONENT_TYPE}/instances/${COMPONENT_NAME}/keystores/default"
<Location /secure/area>
SSLVerifyClient require
</Location>
5.3.2.2.3 Authorizing a Client for a Particular URL
To authorize a client for a particular URL, check that part of the client certificate matches what you expect. Usually, this means checking all or part of the Distinguished Name (DN), to see if it contains some known string. There are two ways to do this, using either mod_auth_basic or SSLRequire.
The mod_auth_basic method is generally required when the certificates are completely arbitrary, or when their DNs have no common fields (usually the organization, and so on). In this case, you should establish a password database containing all of the clients allowed, for example:
SSLVerifyClient none
<Directory /access/required>
SSLVerifyClient require
SSLOptions +FakeBasicAuth
SSLRequireSSL
AuthName "Oracle Auth"
AuthType Basic
AuthBasicProvider file
AuthUserFile httpd.passwd
Require valid-user
</Directory>
The password used in this example is the DES encrypted string password. For more information on this directive, see Section G.3.8, "SSLOptions Directive" which describes the SSLOptions directive of the mod_ossl module.
httpd.passwd Subject: OU=Class 3 Public Primary Certification Authority,O=VeriSign\, Inc.,C=US Subject: CN=GTE CyberTrust Global Root,OU=GTE CyberTrust Solutions\, Inc.,O=GTE Corporation,C=US Subject: CN=localhost,OU=FOR TESTING ONLY,O=FOR TESTING ONLY Subject: OU=Class 2 Public Primary Certification Authority,O=VeriSign\, Inc.,C=US Subject: OU=Class 1 Public Primary Certification Authority,O=VeriSign\, Inc.,C=US
When your clients are all part of a common hierarchy, which is encoded into the DN, you can match them more easily using SSLRequire, for example:
SSLVerifyClient none
SSLWallet "${ORACLE_INSTANCE}/config/fmwconfig/components/${COMPONENT_TYPE}/instances/${COMPONENT_NAME}/keystores/default"
<Directory /access/required>
SSLVerifyClient require
SSLOptions +FakeBasicAuth
SSLRequireSSL
SSLRequire %{SSL_CLIENT_S_DN_O} eq "VeriSign\, Inc." \
and %{SSL_CLIENT_S_DN_OU} in {"Class", "Public", "Primary"}
</Directory>
5.3.2.2.4 Allowing Clients with Strong Ciphers and CA Client Certificate or Basic Authentication
The following examples presume that clients on the Intranet have IPs in the range 192.168.1.0/24, and that the part of the Intranet website you want to allow Internet access to is /access/required. This configuration should remain outside of your HTTPS virtual host, so that it applies to both HTTPS and HTTP.
SSLWallet "$ORACLE_INSTANCE/config/fmwconfig/components/$COMPONENT_TYPE/instances/$COMPONENT_NAME/keystores/default"
<Directory /access/required>
# Outside the subarea only Intranet access is granted
Require ip 192.168.1.0/24
</Directory>
<Directory /access/required>
# Inside the subarea any Intranet access is allowed
# but from the Internet only HTTPS + Strong-Cipher + Password
# or the alternative HTTPS + Strong-Cipher + Client-Certificate
# If HTTPS is used, make sure a strong cipher is used.
# Additionally allow client certs as alternative to basic auth.
SSLVerifyClient optional
SSLOptions +FakeBasicAuth +StrictRequire
SSLRequire %{SSL_CIPHER_USEKEYSIZE}>= 128
# Force clients from the Internet to use HTTPS
RewriteEngine on
RewriteCond %{REMOTE_ADDR} !^192\.168\.1\.[0-9]+$
RewriteCond %{HTTPS} !=on
RewriteRule . - [F]
# Allow Network Access and/or Basic Auth
Satisfy any
# Network Access Control
Require ip 192.168.1.0/24
# HTTP Basic Authentication
AuthType basic
AuthName "Protected Intranet Area"
AuthBasicProvider file
AuthUserFile htpasswd
Require valid-user
</Directory>
5.3.2.3 Enable SSL Between Oracle HTTP Server and Oracle WebLogic Server
Use the Oracle WebLogic Server Proxy Plug-In to enable SSL between Oracle HTTP Server and Oracle WebLogic Server. The plug-ins allow you to configure SSL libraries and configure one-way and two-way SSL communications. For more information, see "Use SSL with Plug-Ins" and "Parameters for Oracle WebLogic Server Proxy Plug-In" in Using Oracle WebLogic Server Proxy Plug-Ins 12.2.1.
5.3.3 Exporting the Keystore to an Oracle HTTP Server Instance Using WLST
Use the WLST custom command ohs_exportKeyStore to export the keystore to a specified Oracle HTTP Server instance location. For more information on this command, see Section A.3.5, "ohs_exportKeyStore."
Note:
There are conventions governing keystore names. For more information, see "Naming Conventions for Keystores."-
Launch WLST from the command line.
Linux or UNIX:
$ORACLE_HOME/oracle_common/common/bin/wlst.shWindows:
$ORACLE_HOME\oracle_common\common\bin\wlst.cmd -
Connect to the Administration Server instance:
connect('<userName', '<password>', '<host>:<port>') -
Issue the
ohs_exportKeyStoreWLST custom command:ohs_exportKeyStore(keyStoreName = '<keystore_name>', instanceName = '<name_of_the_OHS_instance>')
For example, to export the
ohs1_myKeystorekeystore to theohs1Oracle HTTP Server instance:ohs_exportKeyStore(keyStoreName = 'ohs1_myKeystore', instanceName = 'ohs1')
5.3.4 Importing Wallets to the KSS Database after an Upgrade Using WLST
When you use Upgrade Assistant to upgrade from a previous version of Oracle HTTP Server to release 12c (12.2.1), you must perform some additional wallet management. Use the ohs_postUpgrade command to import the wallets for Oracle HTTP Server instances to the KSS database.
This command will parse across all of the Oracle HTTP Server instances in the domain and import the wallets to the KSS database if an entry does not already exist in the database for the same keystore name. For more information on this command, see Section A.3.6, "ohs_postUpgrade."
-
Launch WLST from the command line.
Linux or UNIX:
$ORACLE_HOME/oracle_common/common/bin/wlst.shWindows:
$ORACLE_HOME\oracle_common\common\bin\wlst.cmd -
Connect to the Administration Server instance:
connect('<userName', '<password>', '<host>:<port>') -
Issue the
ohs_postUpgradeWLST custom command, for example:ohs_postUpgrade()
5.3.5 Associating Oracle HTTP Server Instances With a Keystore Using WLST
After using the Configuration Wizard to create Oracle HTTP Server instances in collocated mode, use the ohs_updateInstances WLST custom command to associate the instances with a keystore.
This command will parse across all of the Oracle HTTP Server instances in the domain and perform the following tasks:
-
Create a new keystore with the name
<instanceName>_defaultif one does not exist. -
Put a demonstration certificate,
demoCASignedCertificate, in the newly created keystore. -
Export the keystore to the instance location.
For more information on this command, see Section A.3.7, "ohs_updateInstances."
To associate Oracle HTTP Server instances with a keystore:
-
Launch WLST from the command line.
Linux or UNIX:
$ORACLE_HOME/oracle_common/common/bin/wlst.shWindows:
$ORACLE_HOME\oracle_common\common\bin\wlst.cmd -
Connect to the Administration Server instance:
connect('<userName', '<password>', '<host>:<port>') -
Issue the
ohs_updateInstancesWLST custom command, for example:ohs_updateInstances()
5.3.6 Configuring MIME Settings using Fusion Middleware Control
Oracle HTTP Server uses Multipurpose Internet Mail Extension (MIME) settings to interpret file types, encodings, and languages. MIME settings for Oracle HTTP Server can only be set using Fusion Middleware Control. You cannot use WLST commands to specify the MIME settings.
The following tasks can be completed on the MIME Configuration page:
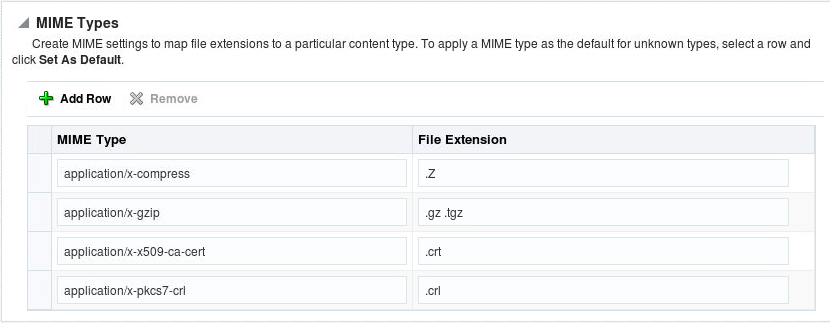
5.3.6.1 Configuring MIME Types
MIME type maps a given file extension to a specified content type. The MIME type is used for filenames containing an extension.
To configure a MIME type using Fusion Middleware Control, do the following:
-
Select Administration from the Oracle HTTP Server menu.
-
Select MIME Configuration from the Administration menu. The MIME configuration page appears. Scroll to the MIME Types region.
Description of the illustration ''mime_type.png''
-
Click Add Row in MIME Configuration region. A new, blank row is added to the list.
-
Enter the MIME type and its associated file extension.
-
Review the settings. If the settings are correct, click Apply to apply the changes. If the settings are incorrect, or you decide to not apply the changes, click Revert to return to the original settings.
-
Restart Oracle HTTP Server, as described in Section 4.3.5, "Restarting Oracle HTTP Server Instances".
The MIME configuration is saved, and shown on the MIME Configuration page.
5.3.6.2 Configuring MIME Encoding
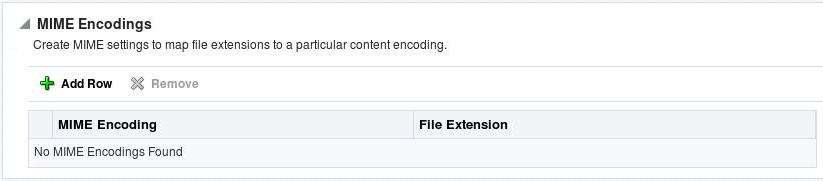
MIME encoding enables Oracle HTTP Server to determine the file type based on the file extension. You can add and remove MIME encodings. The encoding directive maps the file extension to a specified encoding type.
-
Select Administration from the Oracle HTTP Server menu.
-
Select MIME Configuration from the Administration menu. The MIME configuration page appears. Scroll to the MIME Encoding region.
Description of the illustration ''mime_encoding.png''
-
Expand the MIME Encoding region, if necessary, by clicking the plus sign (+) next to MIME Encoding.
-
Click Add Row in MIME Encoding region. A new, blank row is added to the list.
-
Enter the MIME encoding, such as
x-gzip. -
Enter the file extension, such as .gx.
-
Review the settings. If the settings are correct, click Apply to apply the changes. If the settings are incorrect, or you decide to not apply the changes, click Revert to return to the original settings.
-
Restart Oracle HTTP Server as described in Section 4.3.5, "Restarting Oracle HTTP Server Instances".
5.3.6.3 Configuring MIME Languages
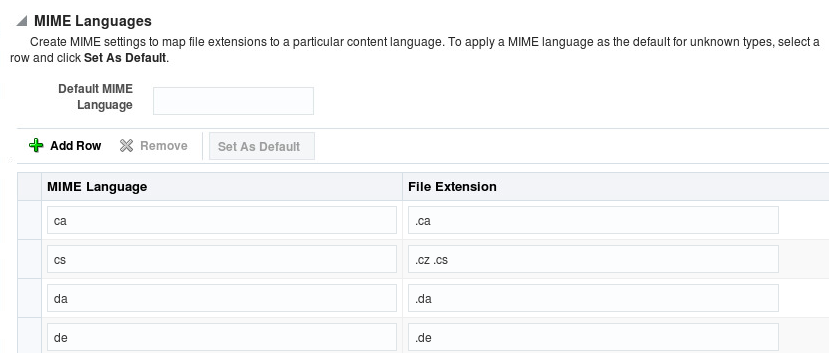
The MIME language setting maps file extensions to a particular language. This directive is commonly used for content negotiation, in which Oracle HTTP Server returns the document that most closely matched the preferences set by the client.
-
Select Administration from the Oracle HTTP Server menu.
-
Select MIME Configuration from the Administration menu. The MIME configuration page appears. Scroll to the MIME Languages region.
Description of the illustration ''mime_lang.png''
-
Expand the MIME Languages region, if necessary, by clicking the plus sign (+) next to MIME Languages.
-
Click Add Row in MIME Languages region. A new, blank row is added to the list.
-
Enter the MIME language, such as en-US.
-
Enter the file extension, such as en-us.
-
To choose a default MIME language, select the desired row, then click Set As Default. The default language will appear in the Default MIME Language field.
-
Review the settings. If the settings are correct, click Apply to apply the changes. If the settings are incorrect, or you decide to not apply the changes, click Revert to return to the original settings.
-
Restart Oracle HTTP Server as described in Section 4.3.5, "Restarting Oracle HTTP Server Instances".
5.3.7 About Configuring mod_proxy_fcgi
The mod_proxy_fcgi module does not have configuration directives. Instead, it uses the directives set on the mod_proxy module. Unlike the mod_fcgid and mod_fastcgi modules, the mod_proxy_fcgi module has no provision for starting the application process. The purpose of mod_proxy_fcgi is to move this functionality outside of the web server for faster performance. So, mod_proxy_fcgi simply will act as a reverse proxy to an external FastCGI server.
For more information on configuring the mod_proxy_fcgi module, see Section B.3, "Task 3: Configure mod_proxy_fcgi to Act as a Reverse Proxy to an External FastCGI Server" and Section B.4, "Task 4: Setup an External FastCGI Server."
5.3.8 About Configuring the Oracle WebLogic Server Proxy Plug-In (mod_wl_ohs)
You can configure the Oracle WebLogic Server Proxy Plug-In (mod_wl_ohs) either by using Fusion Middleware Control or by manually editing the mod_wl_ohs.conf configuration file.
For information about the prerequisites and procedure for configuring the Oracle WebLogic Server Proxy Plug-In to proxy requests from Oracle HTTP Server to Oracle WebLogic Server, see "Configuring the WebLogic Proxy Plug-In for Oracle HTTP Server" in Using Oracle WebLogic Server Proxy Plug-Ins 12.2.1.
5.3.8.1 Configuring SSL for mod_wl_ohs
You can use the Secure Sockets Layer (SSL) protocol to protect the connection between the plug-in and Oracle WebLogic Server. The SSL protocol provides confidentiality and integrity to the data passed between the plug-in and WebLogic Server. For more information, see "Using SSL with Plug-Ins" in Using Oracle WebLogic Server Proxy Plug-Ins 12.2.1.
5.3.9 Removing Access to Unneeded Content
By default, the httpd.conf file allows server access to extra content such as documentation and sample scripts. This access might present a low-level security risk. Starting with the Oracle HTTP Server 12c (12.2.1) release, some of these sections are commented out.
You might want to tailor this extra content in your own environment to suit your use cases. To access the httpd.conf file, see Section 5.1, "About Editing Configuration Files" to access the file.
5.3.9.1 Edit the cgi-bin Section
Examine the contents of the cgi-bin directory. You can either remove the code from the httpd.conf file that you do not need, or change the following Directory directive to point to your own CGI script directory.
...
#
# "${ORACLE_INSTANCE}/config/fmwconfig/components/${COMPONENT_TYPE}/instances/${COMPONENT_NAME}/cgi-bin" should be changed to whatever your ScriptAliased
# CGI directory exists, if you have that configured.
#
<Directory "${ORACLE_INSTANCE}/config/fmwconfig/components/${COMPONENT_TYPE}/instances/${COMPONENT_NAME}/cgi-bin">
AllowOverride None
Options None
Require all granted
</Directory>
...
5.3.9.2 Edit the Fancy Indexing Section
Edit the following sections pertaining to fancy indexing in the httpd.conf file for your use cases.
...
# Uncomment the following line to enable the fancy indexing configuration
# below.
# Define ENABLE_FANCYINDEXING
<IfDefine ENABLE_FANCYINDEXING>
# IndexOptions: Controls the appearance of server-generated directory
# listings.
#
IndexOptions FancyIndexing HTMLTable VersionSort
# We include the /icons/ alias for FancyIndexed directory listings. If
# you do not use FancyIndexing, you may comment this out.
#
Alias /icons/ "${PRODUCT_HOME}/icons/"
<Directory "${PRODUCT_HOME}/icons">
Options Indexes MultiViews
AllowOverride None
Require all granted
</Directory>
#
# AddIcon* directives tell the server which icon to show for different
# files or filename extensions. These are only displayed for
# FancyIndexed directories.
#
AddIconByEncoding (CMP,/icons/compressed.gif) x-compress x-gzip
AddIconByType (TXT,/icons/text.gif) text/*
AddIconByType (IMG,/icons/image2.gif) image/*
AddIconByType (SND,/icons/sound2.gif) audio/*
AddIconByType (VID,/icons/movie.gif) video/*
AddIcon /icons/binary.gif .bin .exe
AddIcon /icons/binhex.gif .hqx
AddIcon /icons/tar.gif .tar
AddIcon /icons/world2.gif .wrl .wrl.gz .vrml .vrm .iv
AddIcon /icons/compressed.gif .Z .z .tgz .gz .zip
AddIcon /icons/a.gif .ps .ai .eps
AddIcon /icons/layout.gif .html .shtml .htm .pdf
AddIcon /icons/text.gif .txt
AddIcon /icons/c.gif .c
AddIcon /icons/p.gif .pl .py
AddIcon /icons/f.gif .for
AddIcon /icons/dvi.gif .dvi
AddIcon /icons/uuencoded.gif .uu
AddIcon /icons/script.gif .conf .sh .shar .csh .ksh .tcl
AddIcon /icons/tex.gif .tex
AddIcon /icons/bomb.gif core
AddIcon /icons/back.gif ..
AddIcon /icons/hand.right.gif README
AddIcon /icons/folder.gif ^^DIRECTORY^^
AddIcon /icons/blank.gif ^^BLANKICON^^
#
# DefaultIcon is which icon to show for files which do not have an icon
# explicitly set.
#
DefaultIcon /icons/unknown.gif
#
# AddDescription allows you to place a short description after a file in
# server-generated indexes. These are only displayed for FancyIndexed
# directories.
# Format: AddDescription "description" filename
#
#AddDescription "GZIP compressed document" .gz
#AddDescription "tar archive" .tar
#AddDescription "GZIP compressed tar archive" .tgz
...
#
# ReadmeName is the name of the README file the server will look for by
# default, and append to directory listings.
#
# HeaderName is the name of a file which should be prepended to
# directory indexes.
ReadmeName README.html
HeaderName HEADER.html
#
# IndexIgnore is a set of filenames which directory indexing should ignore
# and not include in the listing. Shell-style wildcarding is permitted.
#
IndexIgnore .??* *~ *# HEADER* README* RCS CVS *,v *,t
</IfDefine>
5.3.9.3 Edit the Product Documentation Section
Uncomment the Define MANUAL_ENABLE line to enable the manual configuration of product documentation.
...
#
# Uncomment the following line to enable the manual configuration below.
# Define ENABLE_MANUAL
<IfDefine ENABLE_MANUAL>
AliasMatch ^/manual(?:/(?:de|en|es|fr|ja|ko|pt-br|ru|tr))?(/.*)?$ "${PRODUCT_HOME}/manual$1"
<Directory "${PRODUCT_HOME}/manual">
Options Indexes
AllowOverride None
Require all granted
<Files *.html>
SetHandler type-map
</Files>
# .tr is text/troff in mime.types!
<Files *.html.tr.utf8>
ForceType text/html
</Files>
SetEnvIf Request_URI ^/manual/(de|en|es|fr|ja|ko|pt-br|ru|tr)/ prefer-language=$1
RedirectMatch 301 ^/manual(?:/(de|en|es|fr|ja|ko|pt-br|ru|tr)){2,}(/.*)?$ /manual/$1$2
LanguagePriority en de es fr ja ko pt-br ru tr
ForceLanguagePriority Prefer Fallback
</Directory>
</IfDefine>
5.3.10 Using the apxs Command to Install Extension Modules
Note:
This command is only for UNIX and Linux and is necessary only for modules which are supplied in source code form. Follow the installation instructions for modules supplied in binary form.For more information about the apxs command, see the Apache HTTP Server documentation at:
The Apache Extension Tool (apxs) can build and install Apache HTTP Server extension modules for Oracle HTTP Server. apxs installs modules in the ORACLE_HOME/ohs/modules directory for access by any Oracle HTTP Server instances which run from this installation.
Note:
Once any third-party module is created and loaded, it falls under the third-party criteria specified in the Oracle HTTP Server support policy. Before continuing with this procedure, you should be aware of this policy. For more information, see Section 1.8, "Oracle HTTP Server Support".Recommended apxs options for use with Oracle HTTP Server are:
| Option | Purpose | Example Command |
|---|---|---|
| -c | Compile module source |
$ORACLE_HOME/ohs/bin/apxs -c mod_example.c |
| -i | Install module binary into ORACLE_HOME |
$ORACLE_HOME/ohs/bin/apxs -ci mod_example.c |
When the module binary has been installed into ORACLE_HOME, a LoadModule directive in httpd.conf or other configuration file loads the module into the server processes; for example:
LoadModule example_module "${ORACLE_HOME}/ohs/modules/mod_example.so"
The directive is required in the configurations for all instances which must load the module.
When the -a or -A option is specified, apxs will edit httpd.conf to add a LoadModule directive for the module. Do not use the -a and -A options with Oracle HTTP Server instances that are part of a WebLogic Server Domain. Instead, use Fusion Middleware Control to update the configuration, as described in Section 1.6.3, "Modifying an Oracle HTTP Server Configuration File".
You can use the -a or -A option with Oracle HTTP Server instances that are part of a standalone domain if the CONFIG_FILE_PATH environment variable is set to the staging directory for the instance before invoking apxs; for example:
CONFIG_FILE_PATH=$ORACLE_HOME/user_projects/domains/base_domain/config/fmwconfig/components/OHS/ohs1 export CONFIG_FILE_PATH $ORACLE_HOME/ohs/bin/apxs -cia mod_example.c
By default, apxs uses the Perl interpreter in /usr/bin. If apxs cannot locate the product install or encounters other operational errors when using /usr/bin/perl, use the Perl interpreter within the Middleware home by invoking apxs as follows:
$ORACLE_HOME/perl/bin/perl $ORACLE_HOME/ohs/bin/apxs -c mod_example.c
Modules often require directives besides LoadModule to properly function. After the module has been installed and loaded using the LoadModule directive, refer to the documentation for the module for any additional configuration requirements.
5.3.11 Disabling the Options Method
The Options method enables clients to determine which methods are supported by a web server. If enabled, it appears in the Allow line of HTTP response headers.
For example, if you send a request such as:
---- Request ------- OPTIONS / HTTP/1.0 Content-Length: 0 Accept: */* Accept-Language: en-US User-Agent: Mozilla/4.0 (compatible; MSIE 6.0; Win32) Host: host123:80
you might get the following response from the web server:
---- Response --------
HTTP/1.1 200 OK
Date: Wed, 23 Apr 2008 20:20:49 GMT
Server: Oracle-Application-Server-11g/11.1.1.0.0 Oracle-HTTP-Server
Allow: GET,HEAD,POST,OPTIONS
Content-Length: 0
Connection: close
Content-Type: text/html
Some sources consider exposing the Options method a low security risk because malicious clients could use it to determine the methods supported by a web server. However, because web servers support only a limited number of methods, disabling this method will just slow down malicious clients, not stop them. In addition, the Options method may be used by legitimate clients.
If your Oracle Fusion Middleware environment does not have clients that require the Options method, you can disable it by including the following lines in the httpd.conf file:
<IfModule mod_rewrite.c>
RewriteEngine on
RewriteCond %{REQUEST_METHOD} ^OPTIONS
RewriteRule .* – [F]
</IfModule>
5.3.12 Updating Oracle HTTP Server Component Configurations on a Shared Filesystem
You might encounter functional or performance issues when an Oracle HTTP Server component is created on a shared filesystem, such as NFS (Network File System). In particular, lock files or UNIX sockets used by Oracle HTTP Server might not work or may have severe performance degradation; Oracle WebLogic Server requests routed by mod_wl_ohs may have severe performance degradation due to filesystem accesses in the default configuration.
Table 5-1 provides information about the Lock file issues and the suggested changes in the httpd.conf file specific to the operating systems.
| Operating System | Description | httpd.conf changes |
|---|---|---|
|
Linux |
Lock files are not required. The Sys V semaphore is the preferred cross-process mutex implementation. |
Change |
|
Solaris |
Lock files are not required. The cross-process pthread mutex is the preferred cross-process mutex implementation. |
Change |
|
Other UNIX platforms |
Change the file location specified in the |
|
|
UNIX socket issues |
mod_cgid is not enabled by default. If enabled, use the |
5.4 Configuring the mod_security Module
You can use the open-source mod_security module to detect and prevent intrusion attacks against Oracle HTTP Server. For example, you can specify a mod_security rule to screen all incoming requests and deny requests that match the conditions specified in the rule. The mod_security module (version 2.8.0) and its prerequisites are included in the Oracle HTTP Server installation as a shared object named mod_security2.so in the ORACLE_HOME/ohs/modules directory.
This release of Oracle HTTP Server supports only mod_security (version 2.8.0) directives, variables, action, phases and functions. It will not be supported if you replace this module with a later version.
For more information, see:
http://www.modsecurity.org/documentation/
Section 5.4.3, "Sample mod_secuirity.conf File" provides a usable example of the mod_security.conf file, including the LoadModule statement.
Notes:
Be aware of the following:-
mod_security was removed from earlier versions of Oracle HTTP Server but was reintroduced in version 11.1.1.7. This version follows the recommendations and practices prescribed for open source mod_security 2.8.0. Only documentation applicable to open source mod_security 2.8.0 is applicable to the Oracle HTTP Server implementation of the module.
-
In Oracle HTTP Server 11.1.1.7 and later, mod_security is not loaded or configured by default; however, if you have an installation patched from 11.1.1.6, implementing the patch might have already loaded and configured the module.
-
Oracle only supports the Oracle-supplied version of mod_security. Newer versions from modsecurity.org will not be supported.
The mod_security configuration can be added to the httpd.conf configuration file, or it can appear in a separate mod_security.conf configuration file.
This section contains the following information:
-
Section 5.4.1, "Configuring mod_security in the httpd.conf File"
-
Section 5.4.2, "Configuring mod_security in a mod_security.conf File"
5.4.1 Configuring mod_security in the httpd.conf File
You can configure the mod_security module by entering mod_security directives in the httpd.conf file in an IfModule container. To make the mod_security module available when Oracle HTTP Server is running, ensure that the mod_security configuration begins with the following lines:
...
#Load module
LoadModule security2_module "${PRODUCT_HOME}/modules/mod_security2.so"
...
5.4.2 Configuring mod_security in a mod_security.conf File
You can specify the mod_security directives in a separate mod_security.conf file and include that file in the httpd.conf file by using the Include directive.
-
You must create the mod_security.conf file yourself, preferably by using the template in Section 5.4.3, "Sample mod_secuirity.conf File".
Copy and paste the sample into a text editor, then edit it for your system.
-
To make the mod_security module available when Oracle HTTP Server is running, ensure that mod_security.conf begins with the following lines:
#Load module LoadModule security2_module "${PRODUCT_HOME}/modules/mod_security2.so" -
Save the file with the name "mod_security.conf" and include it in your httpd.conf file by using the
Includedirective.If you implement mod_security.conf file as described, it will use the
LoadModuledirective to load mod_security2.so into the run time environment.
5.4.3 Sample mod_secuirity.conf File
The following code illustrates a sample mod_security.conf configuration file.
Example 5-1 mod_security.conf Sample
#Load module
LoadModule security2_module "${PRODUCT_HOME}/modules/mod_security2.so"
# -- Rule engine initialization ----------------------------------------------
# Enable ModSecurity, attaching it to every transaction. Use detection
# only to start with, because that minimises the chances of post-installation
# disruption.
#
SecRuleEngine DetectionOnly
# -- Request body handling ---------------------------------------------------
# Allow ModSecurity to access request bodies. If you don't, ModSecurity
# won't be able to see any POST parameters, which opens a large security
# hole for attackers to exploit.
#
SecRequestBodyAccess On
# Enable XML request body parser.
# Initiate XML Processor in case of xml content-type
#
SecRule REQUEST_HEADERS:Content-Type "text/xml" "id:'200000',phase:1,t:none,t:lowercase,pass,nolog,ctl:requestBodyProcessor=XML"
# Maximum request body size we will accept for buffering. If you support
# file uploads then the value given on the first line has to be as large
# as the largest file you are willing to accept. The second value refers
# to the size of data, with files excluded. You want to keep that value as
# low as practical.
#
SecRequestBodyLimit 13107200
SecRequestBodyNoFilesLimit 131072
# Store up to 128 KB of request body data in memory. When the multipart
# parser reachers this limit, it will start using your hard disk for
# storage. That is slow, but unavoidable.
#
SecRequestBodyInMemoryLimit 131072
# What do do if the request body size is above our configured limit.
# Keep in mind that this setting will automatically be set to ProcessPartial
# when SecRuleEngine is set to DetectionOnly mode in order to minimize
# disruptions when initially deploying ModSecurity.
#
SecRequestBodyLimitAction Reject
# Verify that we've correctly processed the request body.
# As a rule of thumb, when failing to process a request body
# you should reject the request (when deployed in blocking mode)
# or log a high-severity alert (when deployed in detection-only mode).
#
SecRule REQBODY_ERROR "!@eq 0" \
"id:'200001', phase:2,t:none,log,deny,status:400,msg:'Failed to parse request
body.',logdata:'%{reqbody_error_msg}',severity:2"
# By default be strict with what we accept in the multipart/form-data
# request body. If the rule below proves to be too strict for your
# environment consider changing it to detection-only. You are encouraged
# _not_ to remove it altogether.
#
SecRule MULTIPART_STRICT_ERROR "!@eq 0" \
"id:'200002',phase:2,t:none,log,deny,status:44, \
msg:'Multipart request body failed strict validation: \
PE %{REQBODY_PROCESSOR_ERROR}, \
BQ %{MULTIPART_BOUNDARY_QUOTED}, \
BW %{MULTIPART_BOUNDARY_WHITESPACE}, \
DB %{MULTIPART_DATA_BEFORE}, \
DA %{MULTIPART_DATA_AFTER}, \
HF %{MULTIPART_HEADER_FOLDING}, \
LF %{MULTIPART_LF_LINE}, \
SM %{MULTIPART_MISSING_SEMICOLON}, \
IQ %{MULTIPART_INVALID_QUOTING}, \
IP %{MULTIPART_INVALID_PART}, \
IH %{MULTIPART_INVALID_HEADER_FOLDING}, \
FL %{MULTIPART_FILE_LIMIT_EXCEEDED}'"
# Did we see anything that might be a boundary?
#
SecRule MULTIPART_UNMATCHED_BOUNDARY "!@eq 0" \
"id:'200003',phase:2,t:none,log,deny,status:44,msg:'Multipart parser detected a possible unmatched boundary.'"
# PCRE Tuning
# We want to avoid a potential RegEx DoS condition
#
SecPcreMatchLimit 1000
SecPcreMatchLimitRecursion 1000
# Some internal errors will set flags in TX and we will need to look for these.
# All of these are prefixed with "MSC_". The following flags currently exist:
#
# MSC_PCRE_LIMITS_EXCEEDED: PCRE match limits were exceeded.
#
SecRule TX:/^MSC_/ "!@streq 0" \
"id:'200004',phase:2,t:none,deny,msg:'ModSecurity internal error flagged: %{MATCHED_VAR_NAME}'"
# -- Response body handling --------------------------------------------------
# Allow ModSecurity to access response bodies.
# You should have this directive enabled in order to identify errors
# and data leakage issues.
#
# Do keep in mind that enabling this directive does increases both
# memory consumption and response latency.
#
SecResponseBodyAccess On
# Which response MIME types do you want to inspect? You should adjust the
# configuration below to catch documents but avoid static files
# (e.g., images and archives).
#
SecResponseBodyMimeType text/plain text/html text/xml
# Buffer response bodies of up to 512 KB in length.
SecResponseBodyLimit 524288
# What happens when we encounter a response body larger than the configured
# limit? By default, we process what we have and let the rest through.
# That's somewhat less secure, but does not break any legitimate pages.
#
SecResponseBodyLimitAction ProcessPartial
# -- Filesystem configuration ------------------------------------------------
# The location where ModSecurity stores temporary files (for example, when
# it needs to handle a file upload that is larger than the configured limit).
#
# This default setting is chosen due to all systems have /tmp available however,
# this is less than ideal. It is recommended that you specify a location that's private.
#
SecTmpDir /tmp/
# The location where ModSecurity will keep its persistent data. This default setting
# is chosen due to all systems have /tmp available however, it
# too should be updated to a place that other users can't access.
#
SecDataDir /tmp/
# -- File uploads handling configuration -------------------------------------
# The location where ModSecurity stores intercepted uploaded files. This
# location must be private to ModSecurity. You don't want other users on
# the server to access the files, do you?
#
#SecUploadDir /opt/modsecurity/var/upload/
# By default, only keep the files that were determined to be unusual
# in some way (by an external inspection script). For this to work you
# will also need at least one file inspection rule.
#
#SecUploadKeepFiles RelevantOnly
# Uploaded files are by default created with permissions that do not allow
# any other user to access them. You may need to relax that if you want to
# interface ModSecurity to an external program (e.g., an anti-virus).
#
#SecUploadFileMode 0600
# -- Debug log configuration -------------------------------------------------
# The default debug log configuration is to duplicate the error, warning
# and notice messages from the error log.
#
#SecDebugLog /opt/modsecurity/var/log/debug.log
#SecDebugLogLevel 3
# -- Audit log configuration -------------------------------------------------
# Log the transactions that are marked by a rule, as well as those that
# trigger a server error (determined by a 5xx or 4xx, excluding 404,
# level response status codes).
#
SecAuditEngine RelevantOnly
SecAuditLogRelevantStatus "^(?:5|4(?!04))"
# Log everything we know about a transaction.
SecAuditLogParts ABIJDEFHZ
# Use a single file for logging. This is much easier to look at, but
# assumes that you will use the audit log only ocassionally.
#
SecAuditLogType Serial
SecAuditLog "${ORACLE_INSTANCE}/servers/${COMPONENT_NAME}/logs/modsec_audit.log"
# Specify the path for concurrent audit logging.
SecAuditLogStorageDir "${ORACLE_INSTANCE}/servers/${COMPONENT_NAME}/logs"
#Simple test
SecRule ARGS "\.\./" "t:normalisePathWin,id:99999,severity:4,msg:'Drive Access'"
# -- Miscellaneous -----------------------------------------------------------
# Use the most commonly used application/x-www-form-urlencoded parameter
# separator. There's probably only one application somewhere that uses
# something else so don't expect to change this value.
#
SecArgumentSeparator &
# Settle on version 0 (zero) cookies, as that is what most applications
# use. Using an incorrect cookie version may open your installation to
# evasion attacks (against the rules that examine named cookies).
#
SecCookieFormat 0
# Specify your Unicode Code Point.
# This mapping is used by the t:urlDecodeUni transformation function
# to properly map encoded data to your language. Properly setting
# these directives helps to reduce false positives and negatives.
#
#SecUnicodeCodePage 20127
#SecUnicodeMapFile unicode.mapping