17.2 Configuring Single Sign-On
To run a report, you must login with a valid SSO userid and password. The Oracle Internet Directory instance installed with Oracle Fusion Middleware is used as the default repository for user and group information. If you want to configure the Reports Server to use a different Oracle Internet Directory instance or disable security, refer to Section 17.3, "Administering Single Sign-On". For information on how to add users to Oracle Internet Directory, refer to Oracle Fusion Middleware Administrator's Guide for Oracle Internet Directory. In addition, for each Oracle Fusion Middleware installation, the Reports Server instances connect to Oracle Internet Directory as an application entity that is unique to the Oracle Fusion Middleware installation. For more information on this behavior, refer to Section 17.3.4, "Connecting to Oracle Internet Directory".
If a user is not already logged in to Single Sign-On, they are prompted to log in when they attempt to run a report to the Reports Server through rwservlet. If the user parameters for a report include SSOCONN, OracleAS Single Sign-On server will search for the user's data source credentials in Oracle Internet Directory. If none are found, then OracleAS Single Sign-On server prompts the user to create a new resource. For more information on rwservlet, refer to Section A.2.5, "rwservlet". For more information on SSOCONN, refer to Section 17.3.3.1, "SSOCONN". In case of OAM server, if the user's data source credentials do not exist in Oracle Internet Directory, then Oracle Reports raises a "key does not exist" error message. You must create a new resource in Oracle Internet Directory using the LDIF samples located on OTN at http://www.oracle.com/technetwork/middleware/reports/overview/index.htmlor see Section 17.3.3.2.2, "Batch Loading". For more information, see Oracle Fusion Middleware Administrator's guide for Oracle Internet Directory.
The Reports Server is also configured to operate with Oracle Portal by default if Oracle Portal is configured. You can optionally add reports to the portal and enable users to launch them from the portal. Since users must login to the portal in this case, they are not prompted to login again when they launch their reports because they have already been identified to Single Sign-On mode by logging in to the portal.
You can also optionally define access controls for resources associated with the Reports Server (for example, reports, printers, Reports Servers, and calendars) in Oracle Portal. To control access to resources, you must add them to the portal and specify their access options. The resource access controls you specify in Oracle Portal apply to reports that you run outside of the portal as well. For example, if a user tries to run a report through rwservlet, it will be subject to any access controls you have put in place through Oracle Portal.
See Also:
Chapter 16, "Deploying Reports in Oracle Portal" for more information about the integration between Oracle Portal and Oracle Reports Services.Note:
In case of OSSO server, it is recommended that you use Single Sign-on to hide authid in URLs. For more information see, Section 7.3.1.1.18, "allowauthid".17.2.1 Single Sign-On Components used by Oracle Reports
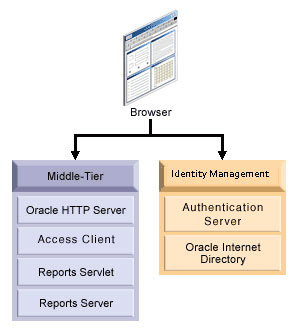
Figure 17-1 provides an overview of the Single Sign-On component architecture.
The components of the Single Sign-On environment include:
-
A client Web browser
-
The Oracle HTTP Server processes requests from the client browser.
Note:
At the highest level, all communication to and from Oracle HTTP Server may be configured to use SSL. The Oracle HTTP Server incorporates an OpenSSL module to provide support for Secure Sockets Layer (SSL) and HTTP Secure Sockets Layer (HTTPS). Once this is set up in the Oracle HTTP Server (see Administrator's Guide for Oracle HTTP Server),rwservletautomatically detects the SSL port number. -
Oracle Reports Servlet (
rwservlet) is a component of Oracle Reports Services that runs inside Oracle WebLogic Server. When a report request comes to the Oracle HTTP Server, Oracle Reports Servlet (rwservlet) passes the job request to Reports Server. -
Reports Server (
rwserver) processes client requests, which includes ushering them through authentication and authorization checking, scheduling, caching, and distribution. -
-
It verifies login credentials by looking them up in Oracle Internet Directory.
-
Oracle Access Manager (OAM server) - It is an Oracle FMW 11g authentication server that provides a full range of security functions that include Web single sign-on, authentication and authorization. When running Reports Services, it uses Oracle Internet Directory as the Identity Store. Oracle Access Manager can use either
mod_ossoorwebgateas the access client configured with Oracle HTTP Server.
-
-
Access Client
-
webgate- WebGate provides single sign-on support. It intercepts incoming HTTP requests and forwards them to the Access Server for authentication. Oracle Forms Services and Oracle Reports Services can usewebgateas an access client with the authentication server.
-
-
Oracle Internet Directory is Oracle's highly scalable, native LDAP version 3 service and hosts the Oracle common user identity. OracleAS Single Sign-On authenticates users against the information stored in Oracle Internet Directory. As noted in earlier sections, when Single Sign-On is enabled for Oracle Reports Services, it checks Oracle Internet Directory for user and group privilege information. It also retrieves data source connection information from Oracle Internet Directory.
-
Oracle Delegated Administration Services
The Delegated Administration Service provides a comprehensive interface for making updates to Oracle Internet Directory. Oracle Reports Services displays Oracle Delegated Administration Services when it encounters a Single Sign-On key that does not already have a data source connection string associated with it in Oracle Internet Directory.
For more information, refer to Chapter 17, "Configuring and Administering Oracle Single Sign-On".