Row-Level Security
Oracle Business Intelligence requires row-level security in the database.
You can configure your connection pools so that the Oracle BI Server passes the credentials for each user to the database.
The database uses the credentials to apply the database’s row-level security rules to user queries.
Row-level database security is different from database authentication. See About Authentication in the Security Guide for Oracle Business Intelligence Enterprise Edition. Row-level database security provides database authorization and applies access security to specific rows in the database.
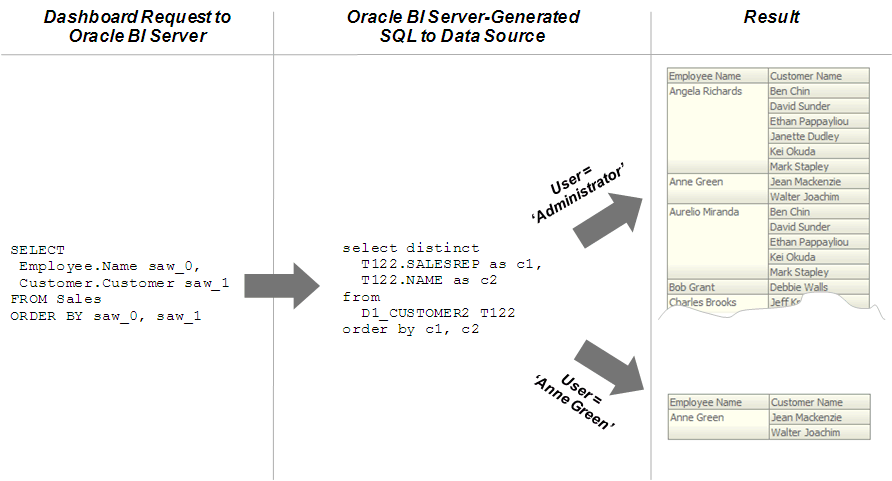
The image shows how row-level security is enforced in the database for Oracle Business Intelligence queries. The security rules are applied to all incoming clients and cannot be breached, even when the Logical SQL query is modified. In this example, the results returned are different depending on the user that generated the query, even though the SQL query generated by the Oracle BI Server is the same. The returned results are based on rules created and enforced in the database.
You must define the users, permissions, and security policies in the database. Refer to your database documentation for more information.
When setting up row-level security consider the following configuration information:
-
Row-level security does not work when SSO is used, or for any cases that involve impersonation such as Delivers, because the password for the end user is not available to the Oracle BI Server.
-
A connection script can be used to achieve the same functionality for Oracle Database data sources.
-
For Essbase or Hyperion Financial Management data sources, the connection pool displays an additional option to implement SSO.