Configuring Resource Permission Definitions for Essbase Filters
Resource permission definitions combine with Essbase filters in the policy store, and you grant them to an application role. This enables users associated with an application role to secure the data that is defined by one or more combinations of resource permission definitions for Essbase filters.
Before you can grant resource permission definitions for Essbase filters to an application role (see Enabling Users to Perform Specific Actions in Essbase and Associated Tools), the appropriate resource permission definitions must first exist in the policy store. Use the examples in this section to understand how to configure resource permission definitions so that users can use Essbase filters.
An application role requires at least two policy store permission grants to access to a specific filter. You must give an application role permission to use filters within a specific scope.
See Resource Permissions Reference for Essbase and Associated Tools.
Use the following examples to understand how to configure resource permission definitions for Essbase filters:
Example 1 - Configuring resource permissions to enable the use of filters within the Demo application:
This example configures resource permission definitions to enable the use of filters within the Demo application. In this example you must ensure that one of the following resource permission definitions exists in the policy store. For example:
-
oracle.essbase.application, /EssbaseCluster-1, use_filter
where:
- oracle.essbase.application, - is the resource type (in this case, an application)
- /EssbaseCluster-1, - is the cluster name
- use_filter - is the action permission (in this case it enables the use of filters)
In this example, the use_filter action permission configures the oracle.essbase.application resource type such that a user associated with this definition in the policy store can use filters in any application in EssbaseCluster-1 (including the Demo application).
OR
-
oracle.essbase.application, /EssbaseCluster-1/Demo, use_filter
In this example, the use_filter action permission configures the oracle.essbase.application resource type such that a user associated with this definition in the policy store can use filters in the Demo application in the EssbaseCluster-1.
Example 2 - Configuring resource permissions for specific filters:
This example configures resource permission definitions that enable the use of a specific filter. You must specify additional resource permission definitions that name the filter in scope of the first grant.
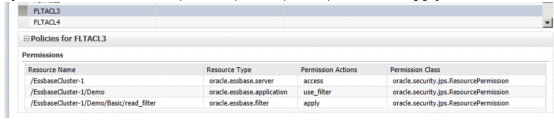
For example, to restrict a user's dimensional access in a database called Basic to members defined by the filter called read_filter, the following resource permission definitions are required:
-
oracle.essbase.application, /EssbaseCluster-1, use_filter
OR
-
oracle.essbase.application, ./EssbaseCluster-1/Demo, use_filter
AND
-
oracle.essbase.filter, /EssbaseCluster-1/Demo/Basic/read_filter, apply
In this example, the read_filter action permission configures the oracle.essbase.application resource type such that a user that is associated with this definition in the policy store is restricted to read filters in the Basic database in the Demo application in the EssbaseCluster-1.
Example 3 - Configuring resource permissions for multiple filters:
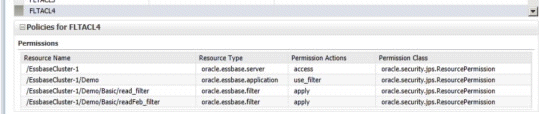
This example activates multiple filters with multiple resource permission definitions to restrict a user's dimensional access in database Basic to members that are defined either by filters "read_filter" or "readFeb_filter." The following resource permission definitions are required:
Note:
This differs from EPM installations where users and groups are limited to a single active filter.
-
oracle.essbase.application, /EssbaseCluster-1, use_filter
OR
-
oracle.essbase.application, ./EssbaseCluster-1/Demo, use_filter
AND
-
oracle.essbase.filter, /EssbaseCluster-1/Demo/Basic/read_filter, apply
AND
-
oracle.essbase.filter, /EssbaseCluster-1/Demo/Basic/readFeb_filter apply
Example 4 - Configuring resource permissions for filters to extend or restrict data access at database level:
This example uses an active filter to extend or restrict data access at the database level.
For example, a user that is associated with the following resource permission definitions cannot read from Demo where noAccess1 restricts access to all dimensions:
- oracle.essbase.application, /EssbaseCluster-1/Demo, read
- oracle.essbase.filter,/EssbaseCluster-1/Demo/Basic/noAccess1, apply