7 Customizing Security for Oracle ADF Application Artifacts
Security customization in the production environment is typically restricted to the security administrator using Oracle Authorization Policy Manager; however, during the development phase of application customization, you can perform similar security customization tasks using Oracle Authorization Policy Manager and JDeveloper.
This chapter includes the following sections:
7.1 About the Oracle Fusion Security Approach
Oracle Fusion Applications is secure as delivered. The Oracle Fusion security approach tightly coordinates various security concerns of the enterprise, including:
-
The ability to define security policies to specify the allowed operations on application resources, including viewing and editing data and invoking functions of the application.
-
The ability to enforce security policies by using roles assigned to end users, and not by directly enforcing those policies on the end users of the system.
A role is an identity that end users are anticipated to fill when interacting with Oracle Fusion Applications that specifically determines the user's permitted access to data and application functions. For example, when an end user attempts to access a task flow, whether or not the end user has the right to enter the task flow and view the contained web pages is specified by the roles provisioned to the end user and the security policies defined for those roles.
In the enterprise, the security administrator ensures end users are provisioned with the permissions to perform the duties of their various jobs. A permission determines the user right to access data and application functions of Oracle Fusion applications. The provisioning tasks involve Oracle Fusion Middleware tools that integrate with Oracle Fusion Applications and allow IT personnel to extend the security reference implementation. These tools directly update a copy of the security reference implementation in the deployed application's security policy store and identity store. The security reference implementation provides role-based access control in Oracle Fusion Applications, and is composed of predefined security policies that protect functions, data, and segregation of duties.
From the standpoint of application developers who seek to apply the Oracle Fusion security approach to an Oracle Fusion application that they extend, the security implementation process overlaps with tasks performed by IT personnel. You may or may not need to extend the Oracle Fusion Applications security reference implementation, depending upon how end users will interact with the new resource. At the end of the process, you must ensure that any new resource you create, such as a business object, such as an invoice or purchase order, in the data model project or a task flow in the user interface project, has sufficient security policies to grant access permission and suitable roles to receive the access permissions.
7.1.1 What You Need to Know Before Proceeding with This Chapter
Customizing security is a complex process that involves working with several tools, familiarity with diverse technologies, and coordination between the application developer and security administrator. For a concise summary of the security customization scenarios and corresponding tasks, see Table 7-1 in Oracle Fusion Security Customization Scenarios.
After familiarizing yourself with the types of security customizations performed by the application developer, read the following sections to gather a more complete understanding of the security customization process:
-
For an overview of the Oracle Fusion Applications security reference implementation, see About Extending the Security Reference Implementation.
-
For a list of security guidelines that dictate which security artifacts in the Oracle Fusion Applications security reference implementation you may or may not modify, see Oracle Fusion Security Customization Guidelines for New Functionality.
-
For an overview of the steps you follow to secure a new resource, see Oracle Fusion Security Customization Process Overview.
-
For additional background about the type of resource customizations that require customizing security, see Scenarios Related to Extending and Securing Data Model Components and Scenarios Related to Extending and Securing User Interface Artifacts.
-
For details about the security artifacts that you create to define security policies, see What You Can Customize in the Data Security Policy Store at Design Time through What You Can Customize in the Application Security Policy Store at Design Time.
-
For a list of tasks that may be performed only by a security administrator, see What You Cannot Do with Security Policies at Design Time.
-
For a list of prerequisite tasks to be completed before customizing security, see Before You Start Customizing Security.
-
For information about the tools involved in customizing security, see Defining Data Security Policies on Custom Business Objects through About Defining Function Security Policies for the User Interface Project.
7.1.2 Learning More About Technologies Used to Secure Oracle Fusion Applications
The following resources provide additional information about Oracle Fusion Applications key security technologies and features used by Oracle Fusion Applications. References to these documents appear throughout this chapter within Related Links subsections.
-
For information about the processes, procedures, and tasks required to implement and maintain the components of application security common to all Oracle Fusion Applications, see the
Oracle Fusion Applications security guides
-
For information about the segregation of duties in the Oracle Fusion Applications security reference implementation (each Oracle Fusion application has its own reference manual), see:
Oracle Fusion Applications security reference manuals
-
For information about the tools used to create database objects using JDeveloper, see the
JDeveloper online help topics
7.2 About Extending the Oracle Fusion Applications Security Reference Implementation
The Oracle Fusion Applications security approach is embodied in the security reference implementation, which delivers predefined roles and security policies that address the common business needs of the enterprise. The reference implementation can be extended to adjust to the needs of a specific enterprise. The predefined security policies implement role-based access control: a set of roles recognizable as jobs, a role hierarchy that contains the duties for those jobs, and a set of role provisioning events and workflows. The Oracle Fusion Applications security reference implementation represents what Oracle considers to be the general security guidelines for jobs, roles, duties, and segregation of duties.
In general, the Oracle Fusion Applications security reference implementation is designed to require only small changes to adjust Oracle Fusion security for a specific enterprise. The security reference implementation provides a comprehensive set of predefined security policies and predetermined data role templates that may be customized to generate security policies. From the standpoint of security administrators who address the specific security concerns of their organizations, typical tasks include changing or extending role definitions and role hierarchies, and managing security policies and data role templates. For example, enterprise IT security administrators eventually review the duties and access defined in the security reference implementation and specify how that matches with the job titles and tasks the enterprise expects to be performed in the deployed Oracle Fusion application.
A security administrator provisions end users with role membership, and defines the provisioning in the application's identity store. This configuration task is performed independent of security customization. The Oracle Fusion Applications security reference implementation contains four types of roles: duty, job, data, and abstract, and implements hierarchies between these roles to streamline provisioning access to end users. Each of the Oracle Fusion Applications roles is implemented in Oracle Fusion Middleware as one of the following roles:
-
Internal roles are roles that are not assigned directly to end users. An internal role is also called an application role because it is specific to an application.
Note that, in Oracle Fusion Applications, application roles are called duty roles. The security reference implementation defines a large number of duty roles that correspond to the duties of individual job roles. Duty roles are application specific and encapsulate all of the permissions necessary to accomplish a particular task. Job roles then consist of the various duties necessary to accomplish a particular job. For example, in your enterprise, the job of an application developer may also include project management duties. The duty role is a role that corresponds to a line on a job description for that job.
-
External roles are roles associated with a collection of end users and other groups. They are also called enterprise roles because they are shared across the enterprise.
In Oracle Fusion Applications, enterprise roles include:
-
The job role is a role that corresponds to a job title defined in human resources (HR).
-
The data role is a role that authorizes a person with a job to a particular dimension of data on which they can work. For example, the data role Accounts Payables (AP) Manager - US Commercial Business Unit identifies who may access the accounts specific to the US division of the enterprise.
-
The abstract role is a role that is not a job title, but is a means to group end users without respect to specific jobs, for example, Employee and Line Manager are both abstract roles.
-
The division between internal roles and external roles is an important principle of the Oracle Fusion security approach. The principle, called least privilege, ensures that the end user acquires permissions specific only to the job they perform rather than to a variety of miscellaneous duties. Therefore, in adherence to the principle of least privilege, duty roles are defined by Oracle Platform Security Services (OPSS) as internal roles and cannot be assigned directly to end users.
Related Links
For further information about the Oracle Fusion security approach and the Oracle Fusion security infrastructure, see Oracle Fusion Applications security guides.
7.3 About Extending and Securing Oracle Fusion Applications
Oracle Fusion Applications is configured by default to deny end users access to the data of the application domain and the web pages that display the data. An important principle of Oracle Fusion security ensures that end users do not have unintended access to data and application artifacts exposed in the extended application.
To enable access to custom resources in the extended application, you may define security policies to specify "who can perform what operations on what specific data and on what specific application artifacts."
Note:
The term protected in this chapter refers to the default Oracle Fusion Applications condition that denies end users access to database resources and application artifacts. In contrast, the term secured refers to resources that have been made accessible to end users through security policies created for this purpose. Therefore, a security policy specifically enables access to the resource based on the permissions it confers to the end user.
To define the security policy, you must consider the additional duties the end users of the extended application will perform, and then grant the required roles the specific permissions to:
-
Access the web pages of a custom task flow that supports the duty
-
Access the specific data records, or instances of a custom business object, required to complete the duty
-
Perform only those operations on that data required by the duty
When you need to secure new resources, you can expect to work with two different types of security policies: data security policies that control access to the data records of database tables or views in the Oracle Fusion Applications schema, and function security policies that control access to the Oracle Fusion application artifacts used to display the data. Because the representation of data security policies and function security policies differs, the environment you will use to define security policies depends on whether data security or function security is being implemented.
In the case of access to data records, a custom business object may be secured either explicitly or implicitly. For example, the AP Manager is authorized to an explicit list of business units specified by a data role, whereas the Project Manager is implicitly authorized to the projects that he manages. When you need to secure data records, then you can:
-
Implicitly grant data access to abstract and job roles through data security policies you define on custom duty roles inherited by the abstract or job role.
You can create custom duty roles to support a new duty introduced by a custom application resource.
-
Explicitly grant data access to a data role through a data security policy you apply directly to the inherited job or abstract role using a data role template.
You can customize the data role template before running the template to generate the data roles.
7.3.1 Oracle Fusion Security Customization Guidelines for New Functionality
In general, when you create new functionality, not supported by Oracle Fusion Applications, do not include authorization to that functionality from within the security artifacts that Oracle Fusion Applications delivers in the security reference implementation.
Specifically, Oracle Fusion security guidelines suggest customization developers and security administrators must not modify the following security artifacts in the security reference implementation when introducing new functionality, through custom or extended business objects:
-
Predefined duty roles, specifically:
-
Do not change the role hierarchy by removing member duty roles assigned to parent duty roles or job roles.
-
Do not remove (also called revoke) existing permissions granted to duty roles.
-
Do not add (also called grant) new permissions to duty roles.
-
-
Predefined security policies (including data and function), specifically:
-
Do not remove existing instance sets from predefined data security policies.
-
Do not remove existing member resources from predefined function security policies.
-
Do not revoke existing actions (mapped by Oracle Fusion security to resource operations) granted on each resource or instance set.
-
Customization developers and security administrators may modify security artifacts in the security reference implementation in the following ways:
-
Do modify job roles to add a custom duty role (permissible by security administrator only).
-
Do modify data role templates to add a new job role as the base role or to add access permissions to a custom business object.
Customization developers and security administrators may create the following security artifacts and add them to the security reference implementation:
-
Do create custom duty roles when a custom application resource requires a new duty role to support the segregation of duties or when a custom application resource introduces new permissions to a predefined business object.
-
Do create data role templates when a custom business object is used as a data stripe and when explicit data security policies grant access to the data stripe. A data stripe is a dimensional subset of the data granted by a data security policy and associated with a data role. For example, create a data role template when you need to grant data roles access to a specific business unit or organization.
Note:
You must not modify predefined duty roles, and you must always add custom duty roles to grant access permissions. Only the security administrator can add or remove duty roles associated with an existing job role. If a predefined job role that adequately describes the duties performed by a job does not exist, then the security administrator can also create a new job role.
7.3.2 Oracle Fusion Security Customization Process Overview
Creating a new, custom business object and exposing it in the extended application is one of the main customization tasks that you may perform. Although you may also extend existing business objects to introduce new functionality or to introduce additional data, the security customization process for new and existing business objects follows a similar pattern.
7.3.2.1 Se curing a New Business Object in the Extended Oracle Fusion Application
To secure a new business object in the extended Oracle Fusion application, do the following:
-
Create a custom duty role to serve as the grantee of the security policy permissions.
-
Define a database resource in the Oracle Fusion Data Security repository for the data records of a database table that you intend to expose in the application.
For details about registering a database table as a database resource, see What You Can Customize in the Data Security Policy Store at Design Time.
-
Define data security policies for the previously defined database resource to grant access to specific data records for a given role.
This step alone does not cause Oracle Fusion security to enforce security policies. To enforce data security policies, requires the developer to enable OPSS authorization checking in the data model project, as described in step 4 and 5 below. For details about securing data, see What You Can Customize in the Data Security Policy Store at Design Time.
-
Extend the data model project (in the extended application) with a new ADF entity object to expose the database table that you defined as an Oracle Fusion Data Security database resource.
For details about creating custom ADF business components to represent a database table, see Customizing and Extending Application Artifacts.
-
Enforce the previously defined data security policies by enabling OPSS authorization checking on the data operations of individual data model objects in the data model project.
For details about enabling security, see What You Can Customize in the Data Model Project at Design Time.
This step causes Oracle Fusion security to make the data records of the backing database resource inaccessible to all users unless a data security policy grants access to the data defined by the database resource and a function security policy grants access to the application artifacts that display the data in the extended application.
-
Consult a security administrator to export all predefined function security policies of the application that you are customizing into a
jazn-data.xmlfile. -
Copy the exported
jazn-data.xmlfile into your application workspace. -
Customize the Oracle ADF application artifacts in the user interface project to display the data records exposed by the extended data model.
For details about creating securable custom application artifacts, see Customizing and Extending Application Artifacts.
-
Define function security policies for the custom Oracle ADF application artifacts to specify the access permissions of end users.
For details about securing application functions, see What You Can Customize in the Application Security Policy Store at Design Time.
-
Enforce the previously defined function security policies by running the ADF Security wizard to enable OPSS authorization checking.
For details about enabling security on the user interface project, see What You Can Customize in the User Interface Project at Design Time.
After you complete these steps, provide the updated jazn-data.xml file to the security administrator to merge the file-based policy store with the application policy store in the staging environment.
Related Links
The following documents provide additional information related to subjects discussed in this section:
-
For further information about creating duty roles, see "Managing Policy Objects in an Application" in the online help for Oracle Authorization Policy Manager, where they are known as application roles.
-
For further information about how the security administrator exports the application policy store, see the "Extracting Data from an OID Store to a File" section in the Administrator's Guide.
-
For further details about adding the exported policy store file (
jazn-data.xml) to your application, see the "Implementing Function Security" chapter of the Developer's Guide.
7.3.3 Oracle Fusion Security Customization Scenarios
You do not need to customize security for every type of customization that you may make in the extended application. Whether or not a security policy is needed will depend on the application resource and the type of customization performed.
The following table summarizes the security customization scenarios that Oracle Fusion security supports. The "Application Developer Tasks" column of the table provides a brief description of the security artifacts involved in each scenario, but presumes some familiarity with the Oracle Fusion security approach (for guidance see What You Need to Know Before Proceeding with This Chapter).
Note:
For simplicity, the following table does not make a distinction between explicit and implicit data security policies. You may also need to customize data role templates when a custom business object is used as a data stripe and explicit data security policies grant access to that data stripe. For more information about customizing data role templates, see What You Can Customize in the Data Security Policy Store at Design Time.
Table 7-1 Oracle Fusion Applications Security Customization Scenarios
| Security Customization Goal | Security Policy Requirement | Application Developer Tasks |
|---|---|---|
|
Control whether the end user associated with a particular role may access a new task flow and view all the web pages of the flow. OR Control whether the end user associated with a particular role may access a new top-level web page. In Oracle Fusion Applications, a top-level web page is one that is not contained by a task flow. |
Define a new security policy. The new task flow or new top-level web page will be inaccessible by default (also called protected) and will require a new function security policy to grant end users access. The ability to secure individual web pages in Oracle Fusion Applications is reserved for top-level web pages backed by an ADF page definition file only. |
Enable ADF Security on the user interface project to protect all task flows (and the web pages they contain) and all top-level web pages. Then, in the file-based policy store, create a resource definition for the task flow/top-level web page and assign the definition as a member of an entitlement (defined in the policy store as a permission set) that you name. Then, define the security policy by granting the entitlement to a custom application role that you either created or consulted with a security administrator to create for you. As a security guideline, do not modify a predefined function security policy by granting additional entitlements to a predefined duty role. |
|
Control whether the end user associated with a particular role may access a customized task flow and view the new or customized web pages of the flow. OR Control whether the end user associated with a particular role may access a customized top-level web page. |
Do not define a security policy. The customized Oracle Fusion application task flow or customized top-level web page will already have a function security policy defined by the security reference implementation; because this type of change does not require new duties, there is no need to grant access to a new duty role. |
Consult the security administrator who can make a customized task flow or customized top-level web page accessible to additional end users through role provisioning (with already defined function security grants). If the same group of end users requires access to the customized task flow/web page, then no change to the provisioned end users is required. |
|
Decide whether the end user associated with a particular role has the view UI components, such as buttons that initiate create, update, or delete operations in the displayed web page. |
Do not define a security policy. Access to user interface components, such as buttons, is not controlled by a security policy, but can be controlled by rendering the button in the user interface based on the end user's role. |
Conditionally render the component by entering an Expression Language (EL) expression on the |
|
Control whether the end user associated with a particular role may view or update a specific set of data records for an all new business object in the displayed web page. |
Define a new security policy. After an Oracle Fusion Data Security database resource is defined for the data, the data records exposed by the new business object will be inaccessible by default (also called protected) and will require a new data security policy to grant end users read or update access on one or more specific sets of data records. |
Enable authorization checking on the appropriate operations of the ADF entity object ( As a security guideline, do not modify a predefined data security policy by granting additional permissions to a predefined duty role. |
|
Control whether the end user associated with a particular role may view or update a new set of data records for an existing business object in the customized web page. |
Define a new security policy. Although an existing Oracle Fusion business object will have an existing data security policy, you must not modify permissions granted to predefined duty roles (those defined by the security reference implementation) and you must instead grant permissions only to custom duty roles that they define. |
In the Oracle Fusion Data Security repository, add a custom duty role as the grantee of access permissions and create a named instance set for the new data records. Then, define the security policy by granting Oracle Fusion Data Security view or update permissions to the custom duty role for the data records. As a security guideline, do not modify a predefined data security policy by granting additional permissions to a predefined duty role. |
|
Control whether the end user associated with a particular role may view or update new sensitive data exposed on a new attribute of an existing business object in the customized web page. Sensitive data is defined as any personally identifiable information (PII) that is considered "public within the enterprise" (also called "internally public"). Internally public PII data is secured from access external to the enterprise. |
Define a new security policy. Sensitive PII data exposed by a new attribute that is added to an existing Oracle Fusion application business object will be secured by the business object's data security policies and will require a new data security policy to grant end users read or update access on a specific column of data. |
Column-level Oracle Platform Security Services (OPSS) authorization checking is not supported for ADF entity objects. Instead in JDeveloper create a custom OPSS permission using the Create JAAS Permission dialog that you select in the New Gallery. Then display the Last, conditionally render the attribute by testing whether the end user has the custom permission either 1.) by entering an EL expression on the user interface component that displays the attribute or 2.) by entering a Groovy expression on the ADF view object to which the user interface component is bound. |
|
Control whether the end user associated with a particular role may view or update new confidential data exposed on a new business object that the customized web page displays. Confidential data is defined as any personally identifiable information (PII) that is considered "private within the enterprise." Exposure of such information outside the enterprise could result in harm, such as loss of business, benefit to a competitor, legal liability, or damaged reputation. Confidential PII data is secured from access external to the enterprise and is secured additionally to prevent access within the enterprise even by highly privileged end users (such as database administrators). |
Define a new security policy. In Oracle Database, the Virtual Private Database (VPD) feature only supports securing a set of data records and therefore will require a new table in a custom schema that you create for Oracle Fusion Applications. The confidential PII data exposed by the new business object will be inaccessible by default (also called protected) and will require a new data security policy to grant end users read or update access on a specific set of data records. |
Column-level policies are not supported by Virtual Private Database (VPD). Instead, the database administrator must create a new table in your custom schema for Oracle Fusion Applications, then define a VPD policy to filter the PII data records by associating a PL/SQL function with that table. Then, in the Oracle Fusion Data Security repository, create an action with the same name as the database table and define the security policy by granting Oracle Fusion Data Security view or update permissions to the custom duty role for the confidential data records. Last, in the data model project, enable OPSS authorization checking on the appropriate operations of the ADF entity object ( |
7.3.4 Scenarios Related to Extending and Securing Data Model Components
In Oracle Fusion Applications, when you want to extend the application to expose additional data, you create an ADF entity object and implement the operations that may be performed over a particular set of data records. The ADF entity object you create encapsulates the data as business object instances, corresponding to data records from a database table or view, such as an invoice or a purchase order. Typical operations are business functions like viewing, editing, or creating an instance of the business object.
Security concerned with controlling the operations that can be performed against specific data is called data security. Data security policies involve granting an end user, by means of the end user's membership in a role, the ability to perform operations on specific sets of data. For example, an accounts payable manager in the enterprise's western regional office may be expected to view and edit invoice data records, but only for the customers in the western region. The Accounts Payable Manager role provisioned to the accounts payable manager authorizes access to the business functions required to view and edit invoice instances, and, in this case, the specific instances of the invoice business object that is striped for the western region.
Data security policies are implemented using Oracle Fusion Data Security, which is the technology that implements the security repository for data security policies. Oracle Fusion Data Security is implemented as a series of Oracle Fusion Applications database tables, sometimes referred to as FND tables (note that FND refers to resources in foundation tables) and includes tables like FND_OBJECTS that defines the database resource and FND_GRANTS that defines the access permissions for those database resources.
To secure the business object in the extended application, where it has been exposed as an ADF entity object, is a multi-step process: 1.) A database resource definition must be created in the FND_OBJECTS table to identify the same table or view backing the ADF entity object. The database resource in Oracle Fusion Data Security is the data resource on which data security is enforced. 2.) After the business object is defined as an Oracle Fusion Data Security database resource, then a security policy must be created to grant access to the data records. The security policies for the database resource specify access permissions such as read, update, and delete permissions on specific sets of data records exposed by the business object. 3.) Finally, to enforce the newly created data security policy, the entity object in the data model project must enforce authorization checking on the data operations that access the protected data records exposed by the business object.
Note:
When an ADF entity object exposes a business object that does not require security, then no database resource for that business object needs to be defined in the Oracle Fusion Data Security repository.
As an Oracle Fusion Applications security guideline, a new data security policy must be created instead of modifying predefined data security policies of the security reference implementation. For example, a new data security policy is required to expose additional data records or operations for an existing business object. Additionally, a custom duty role must be created as the recipient of the new data security access permissions because granting permissions to a predefined duty role would alter the segregation of duties defined by the security reference implementation.
Note:
Developers are not entitled to modify the role hierarchy defined by the Oracle Fusion Applications security reference implementation. Therefore, whenever you create a new duty role, you must consult the security administrator to assign the custom duty role to a job role or data role.
Additionally, the security reference implementation uses database-level security policies to protect most of the confidential personally identifiable information (PII), also called internally private data, that exists in the Oracle Fusion Applications schema. This type of security is implemented in Virtual Private Database (VPD) policies directly on the PII tables. In general, database administrators and other personnel with access to the database must not modify VPD policies implemented for Oracle Fusion Applications. However, when you create a business object that introduces confidential data and that data needs to be treated as internally private within the enterprise, then certain roles may be granted access to the confidential data for valid business reasons. For example, a human resources representative may require access to the employee's home addresses, while a dispatcher may require access to the home telephone numbers of on-call staff.
Whether or not you will need to define a data security policy to grant access to data records depends on the type of customization, as summarized in Table 7-1. The scenarios for defining data security policies include the following.
When a new business object is introduced and it needs to be secured:
When you seek to secure additional data records in the extended application because a new ADF entity object is introduced in the data model project, then OPSS authorization checking must be enabled on the data operations that access the data associated with the ADF entity object, as described in What You Can Customize in the Data Model Project at Design Time.
After you enable OPSS authorization checking on the ADF entity object, the data records exposed by the business object with be inaccessible to all end users of the user interface until an Oracle Fusion Data Security database resource is defined and a new data security policy is created to grant end users access to the data records. Note that defining a database resource for a business object and a data security policy to grant access to those records alone does not protect data records (they will remain accessible to all users).
When a new business object attribute is introduced and it maps to sensitive data:
When you modify an existing ADF entity object to include a new attribute that maps to data that not all end users need to view, then a new data security policy must be defined to grant end users access to the sensitive data. This is accomplished through a combination of a data security policy that grants a custom permission and enforcement of the permission in the application source.
Because Oracle Fusion Data Security does not support automatic enforcement of custom data security permissions, column-level security is not supported by default. You enforce the custom permission in the application source by enabling OPSS authorization checking at the level of the user interface component or its databound ADF view object. Otherwise, without the custom data security permission and custom permission check, the data records (including the sensitive fields) exposed by the business object would be secured by the data security policy that already exists for the business object.
Note:
Oracle Fusion Data Security alone will not prevent sensitive data from being accessed by highly privileged end users, such as database administrators. If the data needs to be treated as internally private (confidential data), then consider implementing additional security using Virtual Private Database (VPD) policies. However, do not implement column-level VPD policies to protect sensitive data exposed by attributes, because security for attributes is not supported by VPD in Oracle Fusion Applications.
When a new business object attribute is introduced and it maps to confidential data:
When you create an ADF entity object that introduces data that is to be treated as confidential to the enterprise, then define row-level VPD policies to control access to PII data by privileged users, including database administrators. Implementing VPD policies requires saving the confidential information in a new table in a custom schema for Oracle Fusion Applications.
In this case, the database administrator first creates the database table and the VPD policy to secure the PII data records. The VPD policy the database administrator creates associates a policy function (a PL/SQL function) with the table in the database. The policy function filters the rows for any query made against the PII data. Finally, you can define the actual data security policies by granting to an action that has been created with same name as the database table where the policy is defined.
For information about creating tables in a custom schema for Oracle Fusion Applications, see About Customizing and Extending the Schemas.
When new operations or new data records are introduced from an already secured business object:
When you introduce new operations or additional data records exposed by an existing ADF entity object into the extended application, you must not modify the predefined data security policies or data role templates that already exist for that business object. Instead, define a new data security policy to grant end users access to the operations or data records that had previously remained protected.
Note that the operations to be secured on the business object may also require enabling OPSS authorization checking for those operations on the ADF entity object in the data model project, as described in What You Can Customize in the Data Model Project at Design Time.
When already exposed operations or data records need to be accessible to additional end users:
When you introduce functionality into the extended application that changes the access requirements of the operations and data records exposed by an existing business object, then those end users may be provisioned by existing job roles or data roles. Consult the security administrator to make the data accessible to additional end users through role provisioning. This type of customization does not require modifying the access permissions or the duty roles of an associated data security policy.
Related Links
The following documents provide additional information related to subjects discussed in this section:
-
For further information about Oracle Fusion Data Security, see the "Implementing Oracle Fusion Data Security" chapter of the Developer's Guide.
-
For further information about creating VPD policies, see the "Using Oracle Virtual Private Database to Control Data Access" chapter of the Oracle Database Security Guide.
7.3.5 Scenarios Related to Extending and Securing User Interface Artifacts
When you want to extend an Oracle Fusion application user interface to support particular end user duties, you may either create a new ADF bounded task flow or customize an existing bounded task flow. The bounded task flow specifies the control flow that the end user is expected to follow when interacting with the web pages contained by the task flow. Similarly, top-level web pages (ones that are not contained by a bounded task flow) may be introduced or customized.
Security concerned with controlling access to a bounded task flow or top-level web page is called function security. Function security policies involve granting an end user, by means of the end user's membership in a role, the ability to access task flows and perform operations in the contained web pages. For example, the accounts payable manager must be granted access permissions to the task flow that provides the functions to manage the invoice data records. If the manager is authorized to access the task flow, then a data security policy governing the invoice records will specify the manager's right to access the actual data.
Function security is implemented at the most fundamental level as resource/action pairs that may be granted to secure specific application artifacts. Oracle ADF defines the actions needed to secure certain Oracle ADF application artifacts, including ADF bounded task flows and, in the case of top-level web pages, ADF page definitions files.
In the Oracle Fusion Applications environment, function security policies aggregate one or more resource/action pairs into an entitlement definition. The entitlement is the entity that is granted to a duty role. The function security policy for the Oracle ADF application artifact, confers the end user with function access permissions, such as view or manage, through a specific duty role.
The function security policies for all the resources of the Oracle Fusion application form the function security repository, which is implemented as an OPSS application policy store. The OPSS policy store in a test or production environment is an LDAP server running Oracle Internet Directory. At runtime, OPSS performs authorization checks against the application policy store to determine the end user's access permissions.
The security administrator for the enterprise exports the LDAP-based application policy store for a particular Oracle Fusion application into an XML file-based policy store that allows you to add security policies using the tools provided by JDeveloper. As an Oracle Fusion security guideline, you must define a new function security policy rather than modify the predefined function security policies of the security reference implementation. Additionally, a custom duty role must be created as the recipient (also called the grantee) of the new function security access permissions because granting permissions to a predefined duty role would alter the segregation of duties defined by the security reference implementation.
Note:
Developers are not entitled to modify the role hierarchy defined by the Oracle Fusion Applications security reference implementation. Therefore, whenever you create a new duty role, you must consult the security administrator to assign the custom duty role to a job role.
Whether or not you will need to define a function security policy to grant access to a task flow or top-level web page depends on the type of customization, as summarized in Table 7-1. The scenarios for defining function security policies include the following.
When a new task flow or top-level web page is introduced:
When you expose new functionality in the extended application through a new ADF bounded task flow or top-level web page that you create, then a new function security policy must be defined to grant end users access to the application artifact.
The new ADF bounded task flow and top-level web page are the only scenarios that require a new function security policy for the extended application.
When a new web page is introduced into an existing task flow:
When you modify an existing task flow to include new web pages, those web pages will be secured by the containing task flow's existing security policy. In this case, because all web pages contained by a bounded task flow are secured at the level of the task flow, there is no need to grant more function security permissions specifically for the new page. You will, however, need to define a new data security policy to grant end users access to any new data records that were introduced by the customization.
When a web page is modified to display a new field of sensitive data:
When you modify a web page to display sensitive data for a single data record field (for example, by adding a column to a table component to display salary information), access to the field displayed by the user interface component cannot be controlled by a function security policy. Authorization checking is not implemented by OPSS at the level of ADF Faces user interface components in the web page. Instead, you enter an Expression Language (EL) expression on that part of the databound ADF Faces component responsible for rendering the field and test whether the end user has the necessary permission grant.
Note that using EL expressions to conditionally render a portion of a user interface component does not control access to the actual data; truly sensitive data must be secured on the business object with a data security policy and secured with a VPN security policy on the database, as described in Scenarios Related to Extending and Securing Data Model Components.
When a web page is modified to display UI components that must not be viewable by all end users:
When you modify a web page to display user interface components that not all end users need to view (for example, a button that deletes data records), access to the components cannot be controlled with a function security policy. Authorization checking is not implemented by OPSS at the level of ADF Faces user interface components in the web page. Instead, you enter an EL expression using ADF Security utility methods on the rendered property of the ADF Faces component to hide or render the entire component based on whether the end user has the necessary permission grant.
Note that using EL expressions to conditionally render a user interface component does not control access to the actual data (if that component displays data). Truly sensitive data must be secured on the business object with a data security policy, as described in Scenarios Related to Extending and Securing Data Model Components.
When existing task flows or top-level web pages must be accessible by additional end users:
When you introduce functionality into the extended application that changes the access requirements of an existing bounded task flow or top-level web page, then consult the security administrator to make the resource accessible to additional end users through role provisioning. This type of customization does not require changing the access permissions associated with the resource or the duties it defines.
Related Links
For information about how Oracle Platform Security Services implements function security, see the "Understanding Security Concepts" part in the Oracle Fusion Middleware Applications Security Guide.
7.3.6 What You Can Customize in the Data Security Policy Store at Design Time
Data security policies are stored in the Oracle Fusion Data Security repository and are defined and edited using Oracle Authorization Policy Manager. You have access to this tool through Oracle Fusion Functional Setup Manager, from the Manage Data Security task available in the Setup and Maintenance work area of any Oracle Fusion Setup application.
Note:
After you select the Manage Data Security task in Oracle Fusion Functional Setup Manager, the environment redirects to the data security customization user interface provided by Oracle Authorization Policy Manager. In this guide, although the data security customization tool is identified as Oracle Authorization Policy Manager, be aware that the tool must be accessed through Oracle Fusion Functional Setup Manager.
Data security policies control access to the database resources of an enterprise. Database resources in the security reference implementation include database tables and views and are predefined standard business objects that must not be changed. However, for cases where custom database resources must be secured business objects (defined by ADF entity objects in the data model project), you can be entitled to create custom duty roles, manage database resources, and define new data security policies using Oracle Authorization Policy Manager.
Note:
As an Oracle Fusion Applications security guideline, the permissions granted by predefined data security policies assigned to duty roles of the Oracle Fusion Applications security reference implementation must not be changed by customization developers. Always define new data security policies to confer additional access permissions. Details about the security reference implementation can be found in the Oracle Fusion Applications security reference manuals.
The data security policy consists of permissions conditionally granted to a role to control access to instance sets of the business object. A permission is a single action corresponding to an end user's intended operation on a single business object. A data security policy therefore is a grant of a set of permissions to a role on a business object for a given instance set. You can define the instance sets as a single row of data, multiple rows of a single table, or all rows of a single table.
The following security artifacts are recorded in the Oracle Fusion Data Security repository for a new data security policy:
-
A database resource that references a primary key corresponding to the database table or view of the business object on which data security will be enforced.
-
One or more roles that will be assigned to the end users who can perform the granted actions.
For more information about the roles used by Oracle Fusion Applications, see About Extending the Security Reference Implementation.
-
A rule (also called a named condition) to define the available row instance sets in the form of a SQL predicate or simple filter (stored as XML) defined on the rows of the database resource.
Instance sets may be a single row of data, multiple rows of a single table, or all rows of a single table. Only instance sets with multiple rows require creating a named condition.
-
One or more actions (such as view, edit, and delete) performed on database records that correspond to the operations supported by the business object (which may include custom operations).
At runtime, data security policies make data available to end users based on their provisioned roles according to the following means:
-
Action grants that specify whether the end user has the necessary permission to perform the intended operation
-
Condition evaluation for individual actions (and its corresponding operation) that specify which data records from the database resource may be accessed
Note:
The application developer does not enforce data security policies when creating the policies. In the case of data security, you must enable OPSS authorization checking on each business object that needs data security. This enforcement is implemented in JDeveloper, as described in What You Can Customize in the Data Model Project at Design Time.
Related to data security is an Oracle Fusion security feature called the data role template. Oracle Fusion Applications supplies data role templates to anticipate typical Oracle Fusion security scenarios and to allow the enterprise to generate data security policies based on information that is specific to the enterprise, such as the names of business units on which to apply the data security policies. Typically, the implementation manager for Oracle Fusion Applications enters the template information and then runs the templates to generate data security policies and the supporting data roles.
When you create a new business object or expose a new set of data records in the extended application, you must confirm whether a data role template exists to generate data security policies for that business object. If a data role template exists, you can update the template to supply information pertaining to the business object, such as the data records to secure and the data dimensions to express data stripes, such as territorial or geographic information used to partition enterprise data. A data dimension is a stripe of data accessed by a data role, such as the data controlled by a business unit.
Using Oracle Authorization Policy Manager, you may perform the following data security-related customization tasks:
-
Manage database resources.
An existing database resource must not have its primary key altered, but you can define new named conditions and add new actions to map any new operations that you implement. If you create a new business object for a database table or view, you can create an all new database resource with named conditions (see the next list entry) and actions.
-
Create named conditions to filter the rows of the business object. (Optional)
The database resource conditions are specified as SQL queries that, when added to a security policy, filter the data and generate an instance set of available data records. Conditions specify the entitlements available to the end user for specific business objects. Conditions may be static or they may be parameterized to allow instance sets to be specified generically but granted specifically. Note a condition is required only when the data security policy does not secure either a single data record or all data records: Both of these cases may be defined without named conditions when creating the security policy.
Note that instance sets generated with parameters cannot be used for data security that is enforced declaratively. Instead, you must write code to enforce OPSS authorization checking.
-
Define data security policies consisting of permissions for a specific application role, named condition (optional), and business object.
A permission can map a standard action to a standard operation: read, update, and delete on a condition of a business object. The standard actions and the standard operations are named similarly.
Alternatively, a permission can map a custom action to a custom operation on a condition of a business object. The custom permission, for example
ApprovePO, is useful to secure a custom operation in the data model project or to secure any operation for row sets at the level of the individual ADF view object. The custom permission also supports securing operations on columns through an EL expression in the user interface project or Groovy scripting language expressions in the data model project.As an alternative to specifying a named condition, the data security policy can secure an instance set defined by a single data record or defined by all data records. Both of these cases may be selected when creating the data security policy.
-
Generate data security policies by updating a data role template with data dimensions and data sets required to support the business object.
A data role template generates data security policies for a business object based on supplied data dimensions to partition the data records into sets of data security policies. The template also maps instance sets for the data security policies it will generate to a particular data dimension. Instance sets are authored at the time the business object is registered as a database resource. Data dimensions and instance sets are specified as SQL clauses.
Note that the SQL clauses cannot be modified after running the template.
For an overview of these tasks, see Defining Data Security Policies on Custom Business Objects.
7.3.7 What You Can Customize in the Data Model Project at Design Time
You create a data model project in JDeveloper to map custom business objects to ADF entity objects. At runtime, the ADF entity object creates a row set of data records exposed by the business object and simplifies modifying the data by handling create, read, update, and delete operations. In the data model project, you then define one or more ADF view objects on top of the ADF entity object to shape the data to the row set required by the tasks of the application, such as populating a form that displays a customer's sales invoice.
Oracle Fusion security separates defining policies and enforcing policies. Thus, by default, data security policies for a business object will remain ineffective until you enable Oracle Platform Security Services (OPSS) authorization checking on the operations of the ADF business component. Enforcement of OPSS authorization checking can be specified either declaratively, at the level of ADF entity objects or ADF view objects, or programmatically, on any related code.
You can modify the data model project to opt into data security in two ways:
-
At the level of the ADF entity object, to enable OPSS authorization checking on standard operations. Standard operations supported by ADF entity objects include, read, update, and delete current row. In this case, all ADF view objects based on the ADF entity object will have the same level of authorization checking enabled. The applicable data security policies will filter the data for each row set produced by these ADF view objects in exactly the same way.
-
At the level of the ADF view object, to enable OPSS authorization checking on standard operations for a collection of rows. This provides a way to filter the data in the data model project based on an individual row set that the ADF view object defines. This level of authorization checking also supports defining a custom permission (corresponding to the ADF view object read operation) in the data security policy store.
Using JDeveloper, you can perform the following security-related customization tasks in the data model project:
-
Enforce row-level security for standard operations.
Standard operations that you can secure are read, update, and remove current row and are specific to the ADF entity object. OPSS authorization checking is enabled directly on the ADF entity object to be secured. Although the ADF entity object maps to all instances of the business object, the data security policy defines conditions to filter the rows displayed to the end user.
-
Enforce row-level security for custom operations.
You may wish to enforce security for custom operations that are specific to the custom business object. Custom operations are not supported by ADF Business Components on the ADF entity object. When a data security policy defines a custom operation, you must enable it using view criteria that you set on an ADF view object. The view criteria identifies the data security policy and business object.
-
Enforce security for individual attributes of business objects.
Column-level OPSS authorization checking is not supported on the attributes of ADF entity objects or ADF view objects. You must create a custom OPSS permission for the column-level read or update operation and then map that to a custom permission. Whether or not the user interface displays the column is specified by testing that custom permission in the user interface using an EL expression on the secured attribute displayed by the user interface component.
For an overview of these tasks, see About Enforcing Data Security in the Data Model Project.
Related Links
For further information about data security, see the "Implementing Oracle Fusion Data Security" chapter of the Developer's Guide.
7.3.8 What You Can Customize in the User Interface Project at Design Time
Before you define function security policies, you will use JDeveloper to create a user interface project with the custom ADF bounded task flows or top-level web pages that you intend to secure.
To simplify the task of securing the functions of the extended application, ADF Security defines a containment hierarchy that lets you define a single security policy for the ADF bounded task flow and its contained web pages. In other words, the security policy defined at the level of the bounded task flow, secures the flow's entry point and then all pages within that flow are secured by the same policy. For example, a series of web pages may guide new end users through a registration process and the bounded task flow controls page navigation for the process.
Specifically, the Oracle ADF application artifacts that you can secure in the user interface project of the extended Oracle Fusion application are:
-
An ADF bounded task flow that protects the entry point to the task flow, which in turn controls the end user's access to the pages contained by the flow
The ADF unbounded task flow is not a securable application artifact and thus does not participate in OPSS authorization checking. When you must secure the contained pages of an unbounded task flow, you define policies for the page definition files associated with the pages instead.
-
ADF page definition files associated with top-level web pages
For example, a page may display a summary of products with data coordinated by the ADF bindings of the page's associated ADF page definition file.
Oracle Fusion security separates defining policies and enforcing policies. Thus, by default, function security policies will remain ineffective until you enable OPSS authorization checking by running the ADF Security wizard in JDeveloper on the user interface project.
Note:
After you run the ADF Security wizard, OPSS authorization checking is enforced on the bounded task flows and top-level pages. These application artifacts will be inaccessible when testing the application in JDeveloper. To enable access, you must define function security policies on the protected application artifacts, as described in What You Can Customize in the Application Security Policy Store at Design Time.
Using JDeveloper, you can perform the following security-related customization tasks in the user interface project:
-
Enable OPSS authorization checking to protect Oracle ADF application artifacts.
Oracle ADF application artifacts in the user interface project, including ADF bounded task flows and the top-level web pages (with a backing ADF page definition) will be protected when you configure ADF Security by running the ADF Security wizard with the Authentication and Authorization option selected. This ensures that end users do not have unintended access to sensitive task flows of the extended application.
-
Conditionally display or hide user interface components in the web page.
ADF Security implements utility methods for use in EL expressions to access Oracle ADF application artifacts in the security context. For example, you can use the ADF Security utility methods to specify whether the end user has use the EL expression to evaluate whether the end user has the necessary permission grant to access create, edit, or delete buttons. Good security practice dictates that your application must hide user interface components and capabilities for which the end user does not have access. For example, if the end user is not allowed access to a particular task flow, you can use the EL expression to evaluate whether the end user has the necessary permission grant to determine whether or not to render the navigation components that initiate the task flow.
For an overview of these tasks, see About Defining Function Security Policies for the User Interface Project.
Related Links
The following documents provide additional information related to subjects discussed in this section:
-
For further information about creating bounded task flows and databound top-level web pages, see the "Introduction to Building Fusion Web Applications with Oracle ADF" chapter of the Developing Fusion Web Applications with Oracle Application Development Framework.
-
For further information about function security, see the "Implementing Function Security" chapter of the Developer's Guide.
7.3.9 What You Can Customize in the Application Security Policy Store at Design Time
You can use JDeveloper to add application security policies to a file-based policy store that the security administrator creates by exporting policies from the LDAP-based application security policy store. The file containing the exported policy store is the jazn-data.xml file.
As a security development guideline, use only JDeveloper tools to work on the exported file-based policy store. JDeveloper supports iterative development of security so you can locally define, test, and edit security policies that you define for Oracle ADF application artifacts. In JDeveloper, you can also create end user identities for the purpose of running and testing the application in JDeveloper's Integrated WebLogic Server. You provision a few end user test identities with roles to simulate how the actual end users will access the secured application artifacts in your local environment before deploying the application.
After testing in JDeveloper using Integrated WebLogic Server, you must consult with the security administrator to merge the LDAP-based application policy store in the staging environment with the security policies that you added to the exported XML file. Initially, the staging environment allows further testing using that server's identity store before deploying to the production environment. Thus, end user identities created in JDeveloper are not migrated to standalone Oracle WebLogic Server and are used only in Integrated WebLogic Server to test the extended application.
The basic security artifact for function security is the JAAS (Java Authentication and Authorization Service) permission, where each permission is specific to a resource type and maps the resource with an allowed action. In general, the JAAS permission specifies the allowed operations that the end user may perform on a particular application artifact. However, from the standpoint of Oracle Fusion Applications, end users typically need to interact with multiple resources to complete the duties designated by their provisioned roles. To simplify the task of creating function security policies in the Oracle Fusion Applications environment, you work with OPSS entitlements to grant permissions to a role for a variety of securable resources, including ADF task flows, web services, and service-oriented architecture (SOA) workflows.
Function security policies that comprise entitlement grants with multiple application artifacts are called entitlement-based policies. The following example shows the Oracle Fusion Applications entitlement policy Maintain Purchase Orders, which groups the OPSS permissions for ADF task flows, a web service, and a SOA workflow.
You use the security policy editor in JDeveloper to define the entitlement-based policy. JDeveloper modifies the source in the exported XML file. As the following example shows, entitlement-based policies in Oracle Fusion applications are defined in the <jazn-policies> element. The policy store section of the file contains the following definitions:
-
A
<resource-type>definition that identifies the actions supported for resources of the selected type -
A
<resource>definition to identify the resource instance that you selected from your application and mapped to a resource type -
A
<permission-set>definition to define the resources and actions to be granted as an entitlement -
A
<grant>definition with one or more entitlements (defined in the XML as a<permission-set>) and granted to the desired application roles (the grantee)
While OPSS permissions granted for a single resource are not typically defined in the Oracle Fusion Applications environment, function security policies that use OPSS permissions for a single resource are called resource-based policies. Ultimately, a function security policy may have either one or more OPSS permissions, one or more OPSS permission sets (entitlements), but not both.
Note:
Granting access to web pages in Oracle Fusion Applications is enforced at the level of ADF Controller components called bounded task flows. Task flows in Oracle Fusion Applications are ADF Controller components that assemble the application's web pages (or regions within a web page) into a workflow that supports the tasks to be performed by application end users. Defining security policies on task flows instead of individual web pages is a security best practice that blocks end users from directly accessing the pages of a task flow. Web pages that are not contained in a task flow are top-level pages and may have security policies defined individually.
Provisioning end users with role membership is defined in the application's identity store and is a configuration task to be performed by the security administrator, independent of security customization.
Using JDeveloper, you may perform the following function security customization tasks:
-
Define an entitlement-based policy for all other application roles.
An entitlement-based policy is a set of resource grants (set of OPSS permissions) that will be required by the end user to complete a task.
-
Define a resource-based policy specifically for the built-in OPSS application role
authenticated-role.A resource-based policy sets an OPSS permission on a single application resource and grants that permission to an application role. This type of function security is typically not used by securable resources in Oracle Fusion Applications. However, the resource-based policy must be used to make a custom resource accessible to any authenticated end user (ones who visit the site and log in). For example, granting a view permission to the built-in OPSS application role
authenticated-roleis the way to make an employee registration task flow accessible to all employees within the enterprise.
For an overview of these tasks, see About Defining Function Security Policies for the User Interface Project.
Related Links
The following documents provide additional information related to subjects discussed in this section:
-
For further information about implementing and testing security using JDeveloper, see the "Implementing Function Security" chapter of the Developer's Guide.
-
For further information about function security, see the "Implementing Function Security" chapter of the Developer's Guide.
Example 7-1 OPSS Entitlement-Based Policy Groups Permissions as a Set that May Be Granted to a Role
Resource Type: ADF Taskflow Resource: PO Summary Action: view Resource Type: ADF Taskflow Resource: PO Details Action: view Resource Type: ADF Taskflow Resource: Supplier Details Action: view Resource Type: Web Service Resource: SpendingLimitCheckWS Action: invoke Resource Type: Workflow Resource: POApproval Action: submit
Example 7-2 Entitlement-Based Security Policy Definition in jazn-data.xml File
<?xml version="1.0" ?>
<jazn-data>
<policy-store>
<applications>
<application>
<name>MyApp</name>
<app-roles>
<app-role>
<name>AppRole</name>
<display-name>AppRole display name</display-name>
<description>AppRole description</description>
<guid>F5494E409CFB11DEBFEBC11296284F58</guid>
<class>oracle.security.jps.service.policystore.ApplicationRole</class>
</app-role>
</app-roles>
<role-categories>
<role-category>
<name>MyAppRoleCategory</name>
<display-name>MyAppRoleCategory display name</display-name>
<description>MyAppRoleCategory description</description>
</role-category>
</role-categories>
<!-- resource-specific OPSS permission class definition -->
<resource-types>
<resource-type>
<name>APredefinedResourceType</name>
<display-name>APredefinedResourceType display name</display-name>
<description>APredefinedResourceType description</description>
<provider-name>APredefinedResourceType provider</provider-name>
<matcher-class>oracle.security.jps.ResourcePermission</matcher-class>
<actions-delimiter>,</actions-delimiter>
<actions>write,read</actions>
</resource-type>
</resource-types>
<resources>
<resource>
<name>MyResource</name>
<display-name>MyResource display name</display-name>
<description>MyResource description</description>
<type-name-ref>APredefinedResourceType</type-name-ref>
</resource>
</resources>
<!-- entitlement definition -->
<permission-sets>
<permission-set>
<name>MyEntitlement</name>
<display-name>MyEntitlement display name</display-name>
<description>MyEntitlement description</description>
<member-resources>
<member-resource>
<type-name-ref>APredefinedResourceType</type-name-ref>
<resource-name>MyResource</resource-name>
<actions>write</actions>
</member-resource>
</member-resources>
</permission-set>
</permission-sets>
<!-- Oracle function security policies -->
<jazn-policy>
<!-- function security policy is a grantee and permission set -->
<grant>
<!-- application role is the recipient of the permissions -->
<grantee>
<principals>
<principal>
<class>
oracle.security.jps.service.policystore.ApplicationRole
</class>
<name>AppRole</name>
<guid>F5494E409CFB11DEBFEBC11296284F58</guid>
</principal>
</principals>
</grantee>
<!-- entitlement granted to an application role -->
<permission-set-refs>
<permission-set-ref>
<name>MyEntitlement</name>
</permission-set-ref>
</permission-set-refs>
</grant>
</jazn-policy>
</application>
</applications>
</policy-store>
</jazn-data>
7.3.10 What You Cannot Do with Security Policies at Design Time
After you define the security policies, consult a security administrator to migrate the policies to the staging environment.
The security administrator is responsible for the following tasks.
-
After testing is completed in JDeveloper, the security administrator must merge the file-based policy store with the application policy store in the staging environment.
-
The security administrator must provision enterprise users by mapping enterprise roles (defined in the staging environment identity store) to the custom application roles.
-
Before running the application in the staging environment, the security administrator must reconcile the application role GUID of any data security policies that were created based on new custom application roles.
When the file-based policy store is merged, the GUIDs of application roles are not preserved.
-
Before running the application in the staging environment, the security administrator must modify the application to use the LDAP-based policy store provided by the testing environment.
-
After testing is completed in the staging environment, the security administrator can migrate the application policy store from the staging environment to the policy store in production.
Related Links
The following documents provide additional information related to subjects discussed in this section:
-
For further information about how the security administrator merges the policies using Oracle Authorization Policy Manager, see the "Upgrading Fusion Application Policies" section in the Administrator's Guide.
-
For further information about how the security administrator provisions enterprise users using Oracle Identity Manager, see the "Managing Identities After Deployment" section in the Administrator's Guide.
-
For further information about how the security administrator reconciles GUIDs in a staging environment, see the "Reconciling GUIDs" section in the Administrator's Guide.
-
For further information modifying the application to use the LDAP-based policy store, see the "Implementing Function Security" chapter of the Developer's Guide.
-
For further information about how the security administrator migrates policies to a new environment, see the "Upgrading Fusion Application Policies" section in the Administrator's Guide.
7.3.11 Before You Start Customizing Security
Before you start customizing security, you should be familiar with the Oracle Fusion application architecture that enables customization, as described in Customizing and Extending . You should also understand the typical workflows for working with customizations, as described in Understanding the Customization Development Life Cycle.
You will need to do the following before you can begin customizing security:
Related Links
The following documents provide additional information related to subjects discussed in this section:
-
For further information about creating VPD policies, see the "Using Oracle Virtual Private Database to Control Data Access" chapter of the Oracle Database Security Guide.
-
For further information about creating job roles, see the "Managing Roles" chapter of the Oracle Fusion Middleware User’s Guide for Oracle Identity Management.
-
For further information about running the ADF Security wizard, see the "Implementing Function Security" chapter of the Developer's Guide.
7.4 Defining Data Security Policies on Custom Business Objects
Before you begin defining data security policies, you should be familiar with the general process and the information gathering prerequisites that data security entails. Once you have an overview of the process, you can become familiar with the details of the various tasks that you can perform.
7.4.1 Process Overview for Defining Data Security Policies
Data security policies secure the database resources of an enterprise. The Oracle Fusion security reference implementation provides a comprehensive set of predefined data security policies for database resources that involve database tables and views that correspond to business objects; it is recommended that these database resources not be changed.
If you will be creating or editing Oracle Fusion Data Security security policies in Oracle Fusion Applications, you will need specific permissions. When you have the necessary permissions, Oracle Authorization Policy Manager allows you to access the data security customization user interface. Contact your security administrator for details.
Note:
Review but do not modify data security policies from the Oracle Fusion security reference implementation in Authorization Policy Manager except as a custom implementation to create data security policies.
The security reference implementation defines the job role IT Security Manager with a duty role hierarchy that includes the Application Data Security Administration Duty duty role. This duty role is entitled to manage data security policies (the entitlement is Manage Data Security Policy) and provides the access necessary to perform the Manage Data Security Policies task in Oracle Authorization Policy Manager. Contact your security administrator for details.
Before you begin:
Collect the following information that you will use to define the data security policy in Oracle Authorization Policy Manager:
-
The primary key of the database table or view that the custom business object represents
You specified the primary key of the database table or view when you registered the database resource.
-
The names of the conditions for which you want the security policy to control access
When you registered the database resource, you may have created named conditions to control access to instance sets composed of multiple rows (Oracle Fusion Data Security does not require that you create a named condition when you want to grant access to instance sets composed either of a single row or of all rows of the database resource).
-
The names of the actions for which you want to associate with a particular named condition (or instance set) to control access
When you registered the database resource, you named actions to identify the securable operations of the custom business object. Action names must be identical to the names of the operations the business object supports. For example, the names of actions corresponding to the supported standard operations are view, edit, and delete. However, if your data model project defines custom operations, actions may have names corresponding to operations named, for example, as
view_US_ONLY,edit_US_ONLY, ordelete_US_ONLY. -
The names of the custom duty roles for which you want to grant access to the conditions and actions of the database resource associated with the custom business object
As an Oracle Fusion Applications security guideline, predefined duty roles defined by the security reference implementation must not be modified. You must use Oracle Authorization Policy Manager to create a new duty role rather than grant data security permissions to predefined duty roles.
7.4.1.1 Defining a Data Security Policy in Oracle Authorization Policy Manager
In Oracle Authorization Policy Manager, the general process for defining a data security policy is as follows:
-
Using the Data Security user interface in Oracle Authorization Policy Manager, register the custom business object as a database resource.
-
Define the instance set of data records that you want to associate with specific securable operations of the ADF business component.
The security policy identifies named conditions from the security repository to specify the row instance set available to the end user provisioned to the role with the permission to perform the intended ADF business component operation.
In Oracle Authorization Policy Manager, a condition you create defines an instance set of multiple rows specified either by simple filters (XML-defined) or complex SQL queries whose values can be parameterized. No condition definition is needed in the case of a single row instance or all the row instances of the database resource.
-
Define the list of actions that you want to be able to grant to the role.
Action are database equivalent create, read, update, delete (CRUD) operations and correspond to the names of securable operations of the business object that the end user may invoke. The data security policy you define will associate one or more actions with an instance set.
-
If the custom business object is not supported by a data role template, define the data security policy:
-
Enter a name and start date for the data security policy.
-
Select one or more job roles or duty roles to which the policy grants access. The roles you select entitle all end users assigned to those roles with access to the data.
In Oracle Authorization Policy Manager, duty role names that you enter are identified as OPSS internal roles called application roles. Similarly, job role names are identified as OPSS external roles called enterprise roles.
-
Specify an instance set on the database resource for which the security policy will control access. This may be a single row, all rows, or multiple rows (specified by a previously defined named condition).
-
Specify one or more actions to secure on the database resource for the currently specified instance set.
-
Repeat the steps to grant actions access to additional instance sets for the current data security policy and roles.
The following figure illustrates the Actions tab in the Edit Data Security page after several actions have been selected. Available actions will be limited to the actions that had been defined for the database resource.
Figure 7-1 Creating a Data Security Policy - Selecting Actions
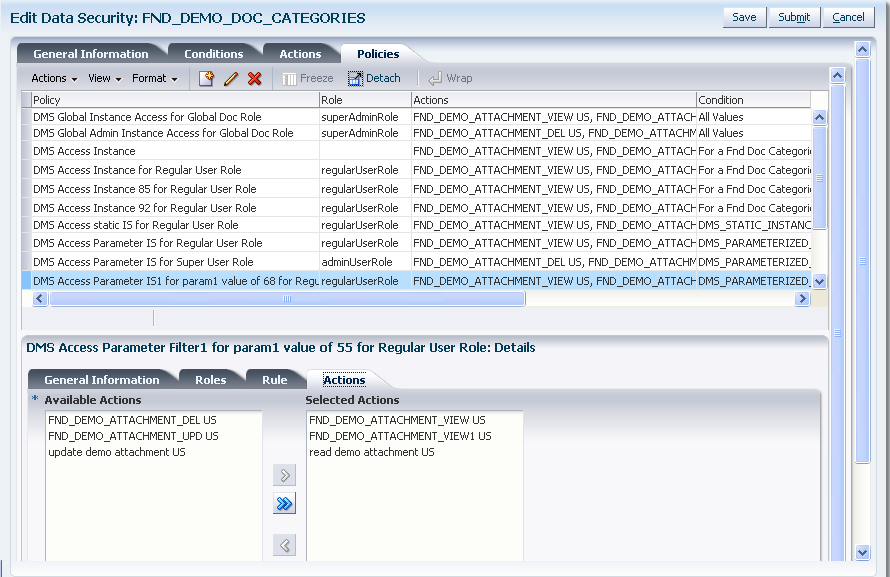
-
7.4.2 Overview of Specific Data Security Tasks You Can Perform
Data security consists of permissions conditionally granted to a role, and these grants are used to control access to instance sets of a business object. A permission is a single action corresponding to an operation on a single business object. Instance sets are rows of a database resource returned by a user-defined SQL WHERE clause; instance sets may be a single row of data, multiple rows of a single table, or all rows of a single table. A data security policy is, therefore, a set of permissions to a principal on a business object for a given instance set.
The security administrator uses Oracle Authorization Policy Manager to create and administer data security policies. A data security policy involves the following security artifacts:
-
A database resource that references a primary key corresponding to the database table or view of the business object to be secured
-
A role that has been provisioned with the users who can perform the granted actions
-
A rule (also known as a condition) to define the available row instances in the form of an SQL predicate or simple filter (stored as XML) defined on the rows of the database resource
-
One or more actions (such as view, edit, or delete) performed on database records that correspond to the operations supported by the business object, and which may include custom operations
7.4.2.1 Registering the Business Object as a Database Resource
The following sections describe how to create a database resource and how to manage the available columns of a database resource for which security policies may be defined:
The following figure shows the General Information tab in the Edit Data Security page after the FND_DOC_CATEGORIES table has been registered as a database resource with the primary key CATEGORY_ID and no columns filtered.
Figure 7-2 Creating a Database Resource - Specifying the Primary Key Columns
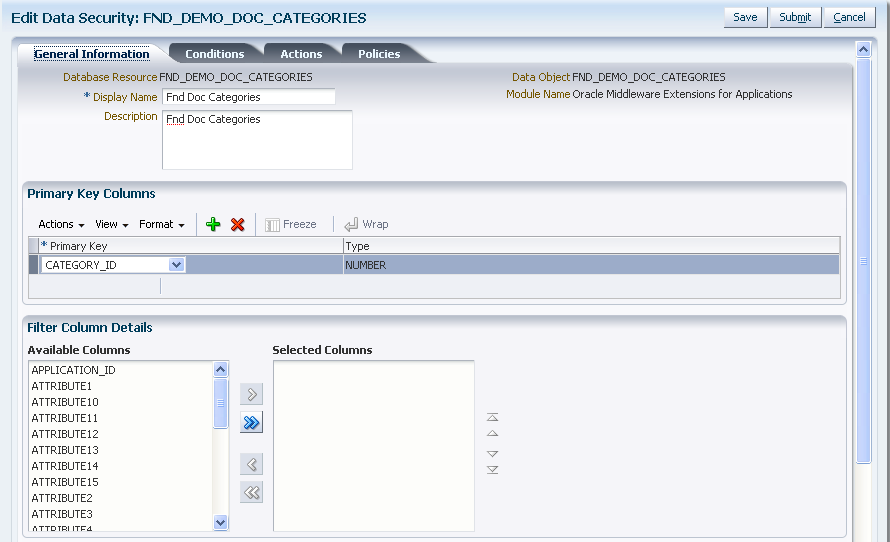
7.4.2.1.1 Specifying the Primary Key Columns of the Policy's Database Resource
The database resource is a database table or view. You use the table or view's primary key column(s) to register it as a database resource.
To specify the primary key of the database resource, proceed as follows:
-
Identify the database resource by matching the name of the database resource that the policy will secure.
-
In the General Information tab, click Add and choose the database resource's primary key from the dropdown list. You can add additional key columns when more than one key column is defined by the resource.
-
Click Save to complete the specification of the primary key.
7.4.2.1.2 Filtering Columns of the Policy's Database Resource
You can filter columns at the level of the database resource when you want to exclude columns from the row instance sets defined by data security policies. Additionally, the data from filtered columns will not be accessible by the user.
To filter the list of columns that the database resource defines, proceed as follows:
-
Identify the database resource by matching the name of the database resource that the policy will secure.
-
In the General Information tab, move available columns to the Selected Column list when you want to exclude that column from the database resource.
Excluded columns will not be available when defining database resource conditions and the data of these columns will not be accessible to any user.
-
Click Save to complete the filtering the list of columns.
7.4.2.2 About Managing Database Resource Conditions
You define conditions on the database resource to specify what portions of the database resource may be secured by data security policies. A condition is a group of row instances that are determined by a simple XML filter or an SQL predicate (WHERE clause) that queries the attributes of the resource itself. Conditions are always defined on a single table or view.
You can define a condition to specify multiple row instance sets using a parameterized SQL WHERE clause. For example, the condition may be defined by the predicate REGION=&PARAM where the parameter PARAM is associated with different regions. When an action is granted for a condition, it may be done for a particular value of the parameter, such as a "sales manager" in the West region may have an action granted for a Region condition with the parameter value West.
You do not need to define a condition for single row instance condition (single value) or for all row instances conditions (all values). Both the single-value case and the all-values case may be easily defined when you create the data security policy. Internally, Oracle Authorization Policy Manager will save these as conditions with the appropriate SQL query clause.
The following figure shows the Conditions tab in the Edit Data Security page after several row instance sets have been defined as conditions of the database resource. You can perform these operations using the Conditions tab:
-
Click New to define a new condition.
-
Select an existing condition and click Edit to edit the condition details.
-
Select an existing condition and click Delete to delete the condition.
Figure 7-3 Creating a Database Resource - Adding to the Available Conditions List
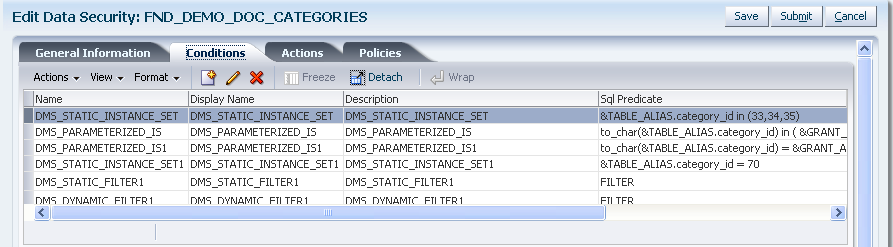
7.4.2.2.1 Defining a New Database Resource Condition
To define a new database resource condition, proceed as follows:
-
Identify the database resource to secure by matching the name of the database resource that the policy secures.
-
In the Conditions tab, click New and define what portions of the database resource may be secured by data security policies. For details, see About Managing Database Resource Conditions.
-
In the Create Database Resource Condition dialog, enter the following information:
-
A name (required)
-
A display name (required)
-
A description (optional)
-
A condition type (required)
-
When you what to use the attribute tree picker user interface to define a simple condition, choose Filter.
-
When you know the attributes names of your condition and you want to define an SQL WHERE clause, for example to specify a dynamic condition, using a parameterized SQL predicate, choose SQL Predicate.
-
-
-
If you chose a Filter condition type, then define the condition as follows:
-
Click Add and choose the column name from the dropdown list that you want to define the filter on.
-
Choose the tree operator for the selected column.
-
Enter a value as the test for the operator.
-
Add additional columns as needed.
-
Select Match All or Match Any depending on whether you want the filter conditions to be ANDed (match all) or ORed (match any).
The following figure shows the Create Database Resources Condition dialog in the Edit Data Security page when creating an XML filter condition.
Figure 7-4 Creating a Database Resource Condition - Defining an XML Filter Condition
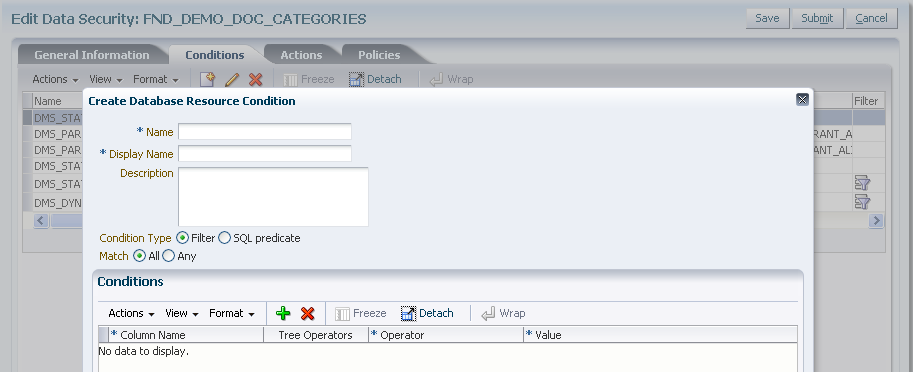
-
-
If you chose a SQL Predicate condition type, then enter the SQL predicate consisting of a query on the table or view named by the database resource.
The following figure shows the Create Database Resources Condition dialog in the Edit Data Security page where you enter an SQL predicate condition.
Figure 7-5 Creating a Database Resource Condition
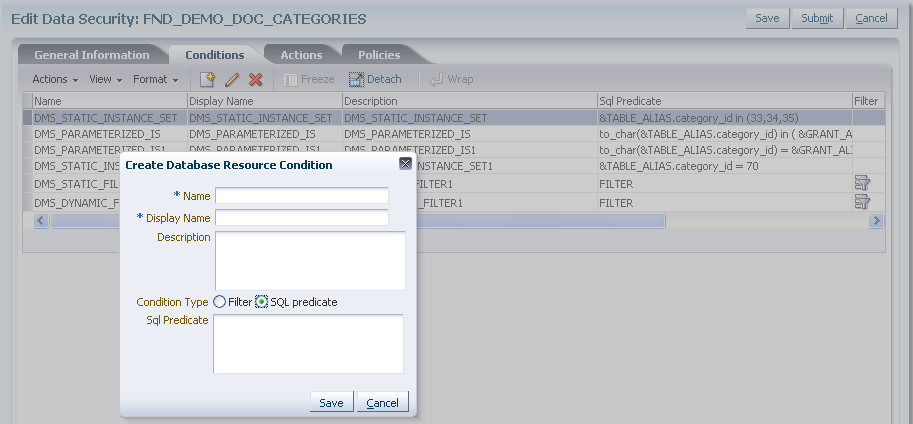
-
Click Save to complete the creation of a database source condition.
7.4.2.3 Managing Database Resource Actions
You define actions on the database resource to specify what kind of access data security policies will secure on a business object. For example, you can specify whether a user might have read, update, or delete access by naming actions for each of these and granting them in a data security policy to a particular role.
An action corresponds one to one with an operation that the business object implements. Action names must match the corresponding business object operation names established by the business object developer. Actions may correspond to either standard operations or custom operations. For example, a business object might define custom read operations based on the regions West and East, which allows you to create the corresponding actions read_WEST and read_EAST. Alternatively, actions that you define, such as read and update, may correspond to the standard read and update operations of the same business object, when no region is specified.
Actions act on the row instance sets of the database resource conditions that you define in a data security policy. When the user invokes an operation on the business object, the system will act on the row set instances defined by the condition and the corresponding action of the security policy in effect for that business object. The system will perform the operation only if the policy grants the user a permission for the corresponding action.
The following figures shows the Actions tab in the Edit Data Security page after several actions have been defined on the database resource. You can perform these operations using the Actions tab:
-
Click Add to define a new action.
-
Click in any field of an existing action and edit the details; do not change the name of an action unless the name of the corresponding business object operation should be changed too.
-
Select an existing action and click Delete to delete the action.
Figure 7-6 Creating a Database Resource - Adding to the Available Actions List
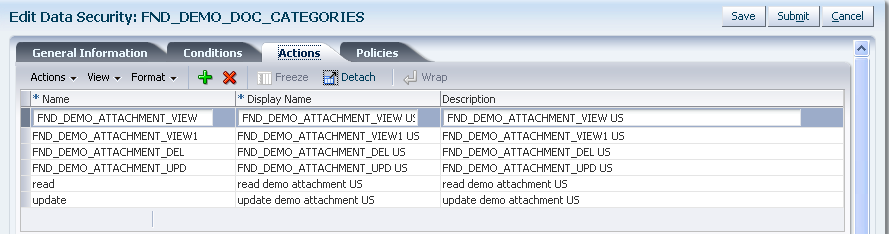
To define a new database resource action, proceed as follows:
-
Identify the database resource to secure by matching the name of the database resource that the policy secures.
-
In the Actions tab, click New and enter the following information in the list of actions table:
-
An action name (required) - the name must match the corresponding operation of the business object. When defining actions for custom operations, consult the developer for the names of the operations.
-
A display name (required)
-
A description (optional)
-
-
Click Save.
7.4.2.4 About Creating a Data Security Policy
You define data security policies to make data of a custom business object available to the users of the application.
The following figures shows the Policies Details tab in the Manage Database Resources and Polices page after several data security policies have been created for the database resource. You can perform these operations using the Policies tab:
-
Click New to define a new policy.
-
Select an existing policy and click Edit to edit the details in the Details tab.
-
Select an existing policy and click Delete to delete the policy.
Important: Duty roles in security policies in the Oracle Fusion reference implementation should not be edited or deleted; only their role hierarchies should be modified.
Figure 7-7 Creating a Data Security Policy - Adding to the Policy List
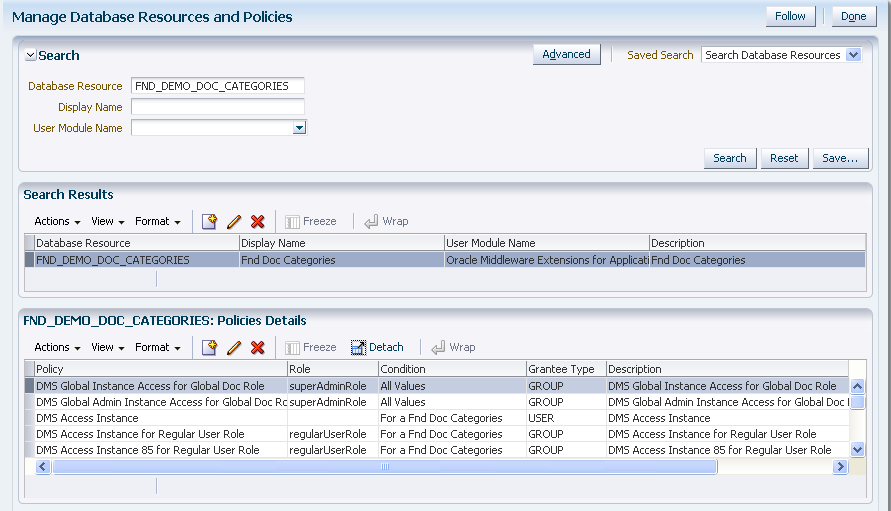
7.4.2.4.1 Performing Prerequisite Tasks
Before you create a data security policy, perform the following tasks:
-
Register the business object as a database resource, as described in Registering the Business Object as a Database Resource.
-
Define the conditions that you want to apply for specific actions of the policy, as described in About Managing Database Resource Conditions. Conditions determine the row instance set available to a user for a given operation.
-
Define the actions to grant to the role, as described in Managing Database Resource Actions. Actions correspond to the operations of the business object that the user may invoke.
-
Obtain the name of the application role or enterprise role for which you want to create the policy.
7.4.2.4.2 Creating a New Data Security Policy
To create a new data security policy, proceed as follows:
-
Identify the database resource to secure by matching the name of the database resource that the policy secures.
-
In the Policies tab, click New.
-
In the General Information tab of the Details section, enter the following information for the data security policy being created:
-
A name (required)
-
A module (required)
-
A start date for the policy to become effective (required)
-
An end date for the policy to cease to be effective (optional)
-
A description (optional)
-
-
In the Roles tab of the Details section, select the role to which the policy grants access. The roles you add entitle all users assigned to those roles with access to the data.
The following figure shows the Select and Add: Roles dialog in the Edit Data Security page.
Figure 7-8 Creating a Data Security Policy, Selecting a Role
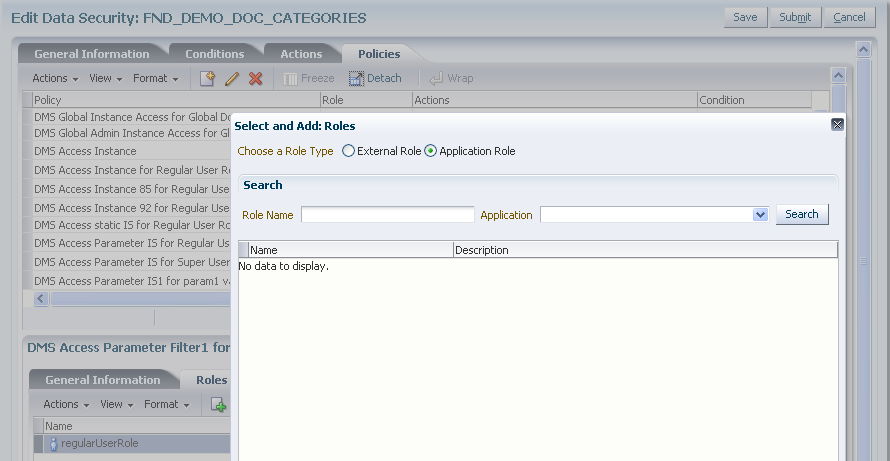
-
In the Rule tab of the Details section, specify the rows of the database resource on which the policy applies in the following ways:
-
When you want to secure a specific row, select Single Value.
-
When you want to secure all rows, select All Values.
-
When you want to change the condition in order to change the secured rows of the database resource, select Multiple Values and click the Search icon and choose the desired condition. To create a new condition, see About Managing Database Resource Conditions.
The following figure shows the Pick a Set of Database Row dialog in the Edit Data Security page after several conditions have been selected from the list of available conditions.
Figure 7-9 Creating a Data Security Policy, Selecting Database Row
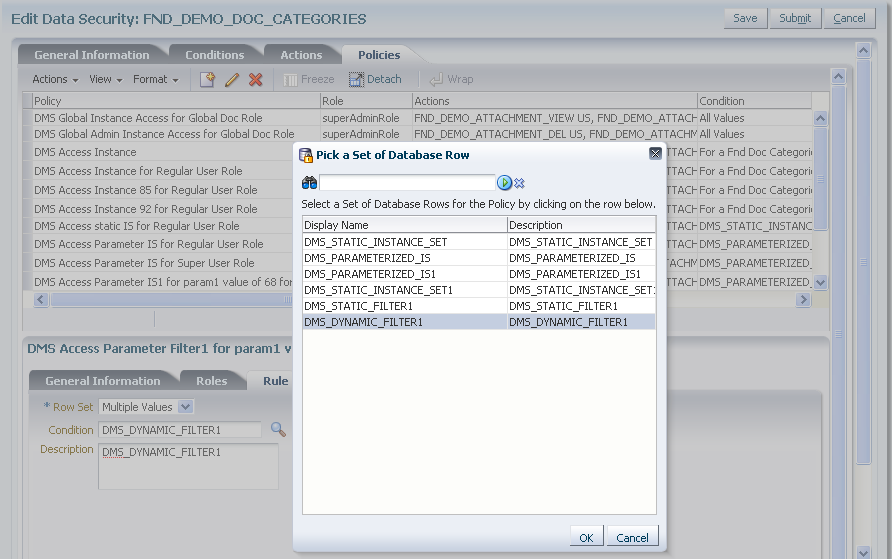
-
-
In the Action tab of the Details section, click New and specify what kind of access data security policies will secure on the database resource. For details, see Managing Database Resource Actions.
The following figures shows the Actions tab in the Edit Data Security page after several actions have been selected.
Figure 7-10 Creating a Data Security Policy, Selecting Actions
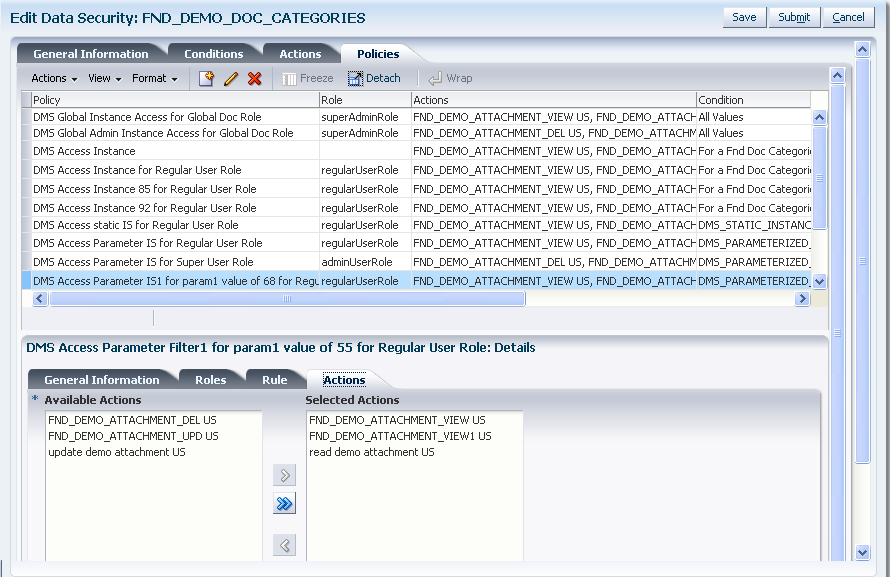
-
Click Save to compete the creation of the data security policy.
7.4.2.5 Modifying a Custom Data Security Policy
Data security policies (and data role templates) provided in the Oracle Fusion security reference implementation can be viewed but it is recommended that they not be modified; other data security policies, that is, those created with Oracle Authorization Policy Manager, can be modified.
To modify a data security policy, proceed as follows:
-
Identify the data security policy to modify or view in either of the following ways:
-
By matching the name of the policy.
-
By matching the name of the database resource that the policy secures.
-
-
In the Policies tab, select the policy to modify from the Policy list and modify the following details for the data security policy:
-
In the General Information tab, you can modify the policy start and end dates, as well as change the name of the policy and its description.
-
In the Roles tab, you can change the roles to which the policy grants access. You can add a new role to the policy when you want to entitle all users who belong to that role with access to the data. You can also remove an existing role from the policy.
-
In the Rule tab, you can change the rows of the database resource on which the policy applies in the following ways:
-
When you want to secure a specific row, select Single Value.
-
When you want to secure all rows, select All Values.
-
When you want to change the condition in order to change the secured rows of the database resource, select Multiple Values and click the Search icon and choose the desired condition. To create a new condition, see About Managing Database Resource Conditions.
-
-
In the Actions tab, you can change the actions on the database resource's records secured by the policy. To create a new action, see Managing Database Resource Actions.
-
-
Click Save to complete the modification of the data security policy.
7.5 Defining Data Security Policies Using Data Role Templates
Before you begin defining data security policies using data role templates, you should be familiar with the general process and the information gathering prerequisites that templates entail. Once you have an overview of the process, you can become familiar with the details of the various tasks that you can perform.
7.5.1 Process Overview for Defining Data Security Policies
A template or data role template specifies key characteristics of external roles and data security policies. These characteristics include:
When run, the data role template generates all the external roles and the data security policies that satisfy the values in the template. The external roles generated (by a template run) are stored in the domain identity store; the data security policies generated are stored in the data security store; templates are stored in the metadata storage (MDS).
The basic principle behind the generation of external roles and data policies is that one can take the cross product of the first two sets of characteristics (external roles times dimension values) to obtain a set of external roles named according to the third set (naming rules), and associate them with a set of permissions, for a given data stripe, in data security policies.
The external roles and the data security policies that a template run generates are specified as a set of external roles and a set of dimensions (rows or attributes returned by an SQL query). Each dimension attribute is associated with an alias, which is used (by the naming conventions) to generate names for the roles and data security policies generated.
A dimension attribute can be the attribute return by an SQL query, such as, the following:
where territory=US, business unit=Finance, and legal entity=North America
The number of external roles generated equals the number of specified external roles times the number of rows returned by the query (or number of dimensions). Each external role generated inherits from the corresponding specified external role.
For example, a template specifying the external roles Employee-Role and Manager-Role, the dimensions US and UK, and the naming rule [external role]:[dimension code name] would generate the following four external roles:
Employee-Role:US, Employee-Role:UK, Manager-Role:US, Manager-Role:UK
Each of the four generated role inherits from one of the specified external roles, Employee-Role or Manager-Role.
The list of external roles and data security policies that a template run generates can be previewed, that is, displayed before the actual creation of roles and associated data security policies takes place.
If you will be creating or editing Oracle Fusion Data Security security policies in Oracle Fusion Applications, you will need specific permissions. When you have the necessary permissions, Oracle Authorization Policy Manager allows you to access the data security customization user interface. Contact your security administrator for details.
The security reference implementation defines the job role IT Security Manager with a duty role hierarchy that includes the Application Data Security Administration Duty duty role. This duty role is entitled to manage data security policies (the entitlement is Manage Data Security Policy) and provides the access necessary to perform the Manage Data Security Policies task in Oracle Authorization Policy Manager. Contact your security administrator for details.
Two particular data sources must be set using WebLogic Server before using data role, described in the following table. Each data source can be configured with the WebLogic Console by navigating to JDBC > Data Sources. The data source ApmRgxDimDBDS must be created with a credential that includes the database writing permission.
Table 7-2 Data Sources Required by Templates
| Data Source Name | JNDI Name | Description |
|---|---|---|
|
|
|
Used by role templates to execute dimension SQLs. |
|
|
|
Stores role template records to create security artifacts. |
Additionally, collect the following information that you will use to define the data security policy in Oracle Authorization Policy Manager:
-
The primary key of the database table or view that the custom business object represents
You specified the primary key of the database table or view when you registered the database resource.
-
The names of the conditions for which you want the security policy to control access
When you registered the database resource, you may have created named conditions to control access to instance sets composed of multiple rows (Oracle Fusion Data Security does not require that you create a named condition when you want to grant access to instance sets composed either of a single row or of all rows of the database resource).
-
The names of the actions for which you want to associate with a particular named condition (or instance set) to control access
When you registered the database resource, you named actions to identify the securable operations of the custom business object. Action names must be identical to the names of the operations the business object supports. For example, the names of actions corresponding to the supported standard operations are view, edit, and delete. However, if your data model project defines custom operations, actions may have names corresponding to operations named, for example, as
view_US_ONLY,edit_US_ONLY, ordelete_US_ONLY. -
The names of the custom duty roles for which you want to grant access to the conditions and actions of the database resource associated with the custom business object
As an Oracle Fusion Applications security guideline, predefined duty roles defined by the security reference implementation must not be modified. You must use Oracle Authorization Policy Manager to create a new duty role rather than grant data security permissions to predefined duty roles.
7.5.1.1 Creating or Revising a Data Role Template
To create or revise a data role template, do the following:
-
In the global area of Oracle Fusion Applications, click your name and select Setup and Maintenance, and Manage Data Role Templates.
-
In the data role template workflow, use the tabbed pages (External Role, Dimension, Naming, and Policies tabs sequentially) to create a data role template or revise an existing one.
-
When the job role grantees of the data security policies generated by the template are not already defined by the existing data role template, add a new external role.
The data role template specifies which base roles to combine with which dimension values for a set of data security policies.
-
When the custom business object expresses a new data stripe to apply to the generated data security policies, modify the SQL code that identifies the dimension values of the template.
Note that the SQL code cannot be modified after running the template.
-
When the data role grantee of the data security policies generated by the template are not already defined by the existing data role template, configure a new data role name.
The data role template constrains the data roles with access permissions for specific data records with particular actions. The data role provides provisioned end users with permissions to access a dimensional subset of the data granted by a data security policy.
-
Select the database resource that you registered for the custom business object.
-
Optionally, select one or more data sets that you specified as named conditions when you created the database resource.
Alternatively, the template can generate policies based on the primary key of the database resource.
-
Specify one or more actions to secure on the database resource for the currently specified instance set.
-
7.5.2 Specific Data Role Template Tasks You Can Perform
A business object can be mapped to a set of dimension values and data role naming rules defined by data role templates. A data role for a defined set of data describes the job an end user does within that defined set of data. A data role inherits job or abstract roles and grants entitlement to access data within a specific dimension of data based on data security policies. The dimension expresses data stripes, such as territorial or geographic information you use to partition enterprise data. You use data role templates to generate data roles and the template applies the values of the dimension and participant data security policies to the group of base roles.
7.5.2.1 Creating a Template
To create a new template, proceed as follows:
-
Select Global > Role Templates, in the left panel, and then click New to display an Untitled page in the right panel containing six tabs: General, External Roles, Dimension, Naming, Policies, and Summary.
-
In the General tab, enter the following data for the template being created:
-
A display name (required)
-
A name (required)
-
A description (optional)
-
A template group (optional) - This attribute allows searching templates by group and running simultaneously the set of templates in a group.
-
-
In the External Roles tab, specify the external roles for the template in one of the following ways:
-
Click Add, at the top of the Roles area, to display bring up the Add External Role dialog where you can search for external roles matching a given pattern; then select roles from the results of the query and click Add. The role(s) selected are displayed in the Roles table.
-
Perform a regular search for external roles and drag-and-drop the desired roles from the Search Results list into the Roles table.
The following figure shows the Roles table in the External Roles tab after two external roles have been added to the table. When the mouse hovers the blue icon, at the right of a role row, the following information about the role is displayed: the role code, the role name, and the role description; these three attributes can always be used in the Naming tab to specify the names of generated roles.
Figure 7-11 Creating a Template, External Roles
-
-
In the Dimension tab, specify the SQL that identifies the dimensions of the template.
The user must have access permission to the data queried. The data returned by that SQL is displayed in the Preview Data table. Optionally, enter aliases for the column names of the returned data in the Column Display Names table, at the bottom of the page.
The following figure shows the Dimension tab with an SQL query, the data returned by it, and display name aliases; the attributes
SET_ID,SET_CODE, andSET_NAMEcan be used in the Naming tab to specify the names of generated roles.Figure 7-12 Creating a Template, Dimensions
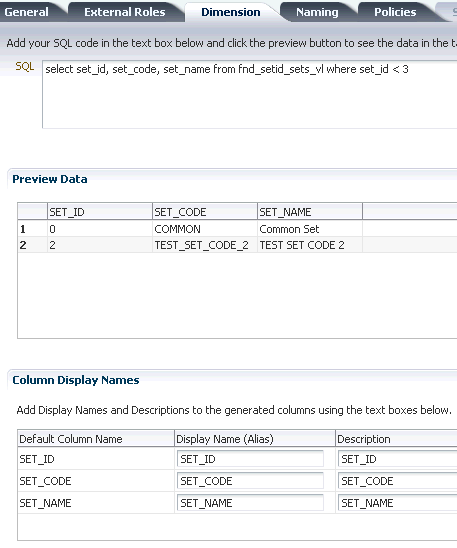
-
In the Naming tab, specify the rule to follow to generate names of the data roles created by the template. These names are put together by concatenating several strings that you specify in the area Configure Role Name. Typically, one chooses an attribute of the base role and an attribute of the dimension (such as
SET_ID,SET_CODE, orSET_NAMEin the above figure); the role attributesRole_Code,Role_Name, andRole_Descripare available by default. The resulting names must be unique.Similarly, specify the rule to follow to generated display names for the data roles created by the template. These names are put together by concatenating several strings that you specify in the area Configure Display Name. The resulting names need not be unique, but it is recommended that you specify enough attributes to make them unique too.
Optionally, enter a description for the roles generated in the area Description.
The following figure shows a portion of a Naming tab with naming values for the names and the display names for the external roles generated by the template. Note the following points: (a) the pattern of the concatenation is shown at the bottom of each area after the heading Generates; (b) the use of square brackets in the description to refer to data values.
Figure 7-13 Creating a Template, Role Naming
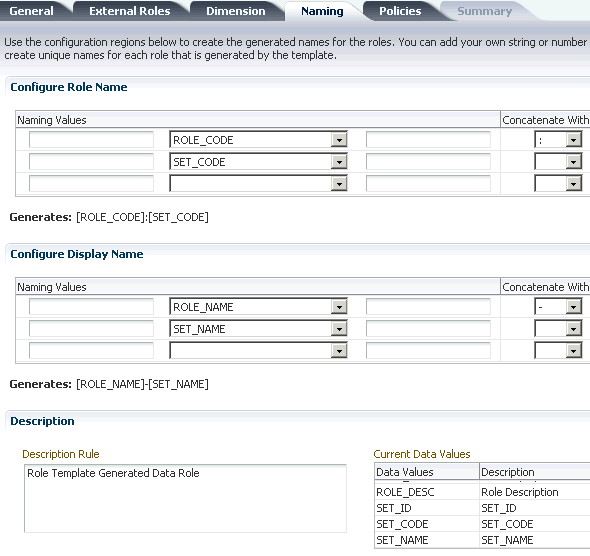
-
In the Policies tab, specify the rules to create data set grants, as follows:
-
In the Database Resource area, use the button Add to add a database resource, that is, the object to be secured by the generated data security grants.
-
In the Data Sets tab, specify wether the grant is using a Primary Key or an Instance Set (the instance set is selected from the available instance sets associated with the resource, which are defined at resource creation), and how the data set is mapped to a dimension attribute.
-
In the Actions tab, specify the actions allowed on the database resource.
Figure 7-14 illustrates the specification of a data set by a primary key and the corresponding mapping to a dimension attribute; Figure 7-15 illustrates the specification of a data set by an instance set and the corresponding mapping to dimension attributes; and Figure 7-16 illustrates the selection of actions allowed on the database resource.
Figure 7-14 Creating a Template, Specify Data Set with Primary Key
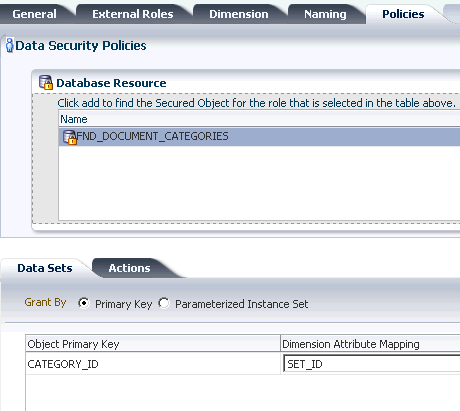
Figure 7-15 Creating a Template, Specify Data Set with Instance Set
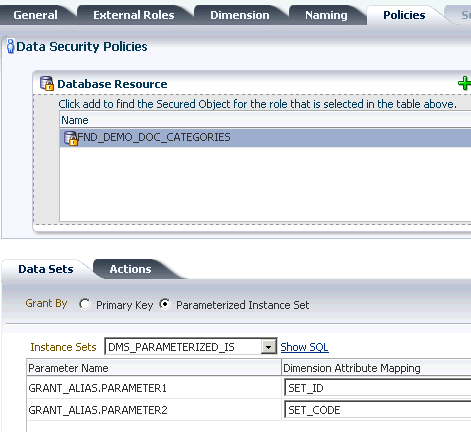
Figure 7-16 Creating a Template, Specifying Actions
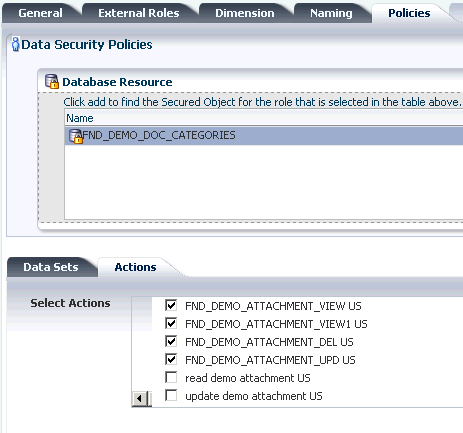
-
-
Click Save. Oracle Authorization Policy Manager validates the information supplied and, if all data passes validation, the template is saved and the tab Summary becomes available.
7.5.2.2 Running a Template
The roles that a template run generates can be previewed before the creation of security artifacts takes place. The procedures in this section assume that the template (mentioned in the procedures) has been created and saved.
A template or a set of templates can also be run programmatically via web-services. For details, see About Running Templates Programmatically.
To preview the external roles that a template run would generate, proceed as follows:
-
Open the template and bring the Summary tab to the foreground (this tab is available since the template has been saved).
-
Click the button Preview Roles, near the top of the page, to display the Preview Roles dialog, where the external roles that would be generated by an actual template run are grouped in the following five disjoint categories:
-
Valid Roles - Set of roles with no issues.
-
Invalid Roles - Set of roles with no base role in the identity store.
-
Inconsistently Created Roles - Set of roles with identical names to existing roles in the identity store. These roles, typically, get to be included in this category because of a change or deletion in records from where the dimensions are computed.
-
Inconsistently Deleted Roles - Set of roles that have been deleted from the identity store.
-
Missing Link Roles - Set of roles that are missing the link to the parent base role.
The following figure shows a portion of the Preview Roles dialog with the category Valid Roles expanded.
Figure 7-17 Previewing Roles, Five Categories
-
To run a template, proceed as follows:
-
Open the template and bring the Summary tab to the foreground (this tab is available since the template has been saved).
-
Click the button Generate Roles. The roles generated are displayed in the five disjoint categories mentioned in the preceding procedure. Each external role generated by the run inherits from the corresponding parent external role.
-
Reconcile roles in the following four categories, as appropriate:
-
Invalid Roles - A role in this category is a role for which the base role is not found in the identity store. Delete or allow roles in this set; deleting an invalid role:
-
Removes the role, if it is not being used by any policy.
-
Removes the data security generated for the role.
-
-
Inconsistently Created Roles - A role in this category is a role with a name identical the name of some other role already in the identity store. Typically, these roles show up because of a change or deletion in records from where the dimensions are computed. Delete or reuse roles in this set; reusing an inconsistently created role:
-
Overwrites the existing role with the generated one.
-
Adds a link between the base role and the role.
-
Refreshes the role's display name and description.
-
Adds the data security for the role.
-
Does not affect data securities defined by other templates.
-
-
Inconsistently Deleted Roles - Delete or recreate roles in this set; recreating an inconsistently deleted role:
-
Creates the role in the identity store using the template's naming definition.
-
Adds the data security for the role.
-
Adds a link between the base role and the role, if it was not already in place.
-
-
Missing Link Roles - A role in this category is missing the required link to a base role. Relink roles in this set; relinking a missing link:
-
Adds a link between the base role and the role.
-
Updates the grant associated with the role.
-
-
Once external roles and data policy grants have been generated, you can verify that they have been properly created by searching and opening a particular role or policy. The following figure shows how the generated external role Benefits Administrator:Financial Mgnt inherits, as expected, from the base external role Benefits Administrator (the names displayed in the External Role Hierarchy table are the role display names, not role names):
Figure 7-18 Generated Role Inheriting from a Based Role
7.5.2.2.1 About Running Templates Programmatically
The following two functions support running a single template or the collection of templates with a given group id via web-services:
public String executeTemplate(String TemplateName) public String executeTemplateByGroupId(String GroupId)
The string returned by either of them describes the status of the run. If successful, it identifies the template(s) that were run; otherwise, it identifies the error that was encountered.
7.5.2.3 Updating a Template
There are rigorous restrictions on how a template can be changed once it has been run.
-
The name of a template cannot be updated.
-
The SQL that defines the template dimensions cannot be changed. The data that this SQL accesses, however, can change and, therefore, a new template run may return a different set of dimensions than those returned by the last run.
-
When a dimension is added (to the set of dimensions of the last run), the template run creates external roles for the added dimension only.
-
When a dimension is deleted (from the set of dimensions of the last run), the administrator can either deactivate the external roles involving the deleted dimension or left them unchanged.
-
After execution, the template's naming cannot be updated.
On the other hand, external roles can be added or deleted from a template at any time.
-
When an external role is added to a template, a template run creates external roles for the added role and each of the dimensions.
-
When an external role is deleted from a template, then the administrator can either deactivate the external roles involving the deleted role or left them unchanged.
Use the following procedure to update a template.
-
Locate the template to update by performing a regular search or an advanced search.
Data Role Templates can be searched by specifying a template name, display name, and group id.
-
Select Global > Role Templates in the navigation panel and click Open (the folder icon on top of the panel) to display the Search - Role Templates page.
-
Enter an operator and a string to match for the template name, an operator and a string to match for the template display name, and an operator and a string to match for the template group id.
-
Click Search to trigger the search and to display the templates that match the entered specification in the Search Results table.
-
Double-click an item in the Search Results table to open it.
Alternately, select the template in the Search Results table and click Open.
-
-
Click Edit to open the template for editing in the Home area.
-
Modify fields as appropriate and as allowed in the page tabs.
-
Click Apply to save changes.
7.5.2.4 Importing and Exporting a Template
A data role template can be imported to or exported from the Oracle Authorization Policy Manager environment with the use of the following two utilities: importMetadata and exportMetadata. Both utilities require establishing a connection to the Oracle WebLogic server before they can be used. The following code illustrates how to establish a connection to a WebLogic server:
> connect ('aUser','aPassword','t5://localhost:7133')
In the code, the first argument is the user name, the second is the password for that user, and the third is the connection URL to the server. The connection so established is terminated with the command exit().
Use the following procedure to import one or more data role templates.
-
Connect to the server.
-
Execute the utility
importMetadata, as illustrated in the following sample (the arguments are listed in different lines only for clarity of exposition):> importMetadata(application='oracle.security.apm', server='AdminServer', fromLocation='/myLocation/myRoleTemplates', docs='/oracle/apps/apm/**', restrictCustTo='site')The meaning of the arguments is as follows:
-
applicationspecifies the owner of the data role template to be imported. -
serverspecifies the name of the WebLogic server to which one is connected. -
fromLocationspecifies the directory where the data role template to be imported is located. -
docsspecifies the template in the directoryfromLocationto be imported. To import all templates (including template subdirectories) in the specified directory, use **, as illustrated in the example above. -
restrictCustTois an argument that should always be set tosite.
-
To export a data role template, proceed as follows:
-
Connect to the server.
-
Execute the utility
exportMetadata, as illustrated in the following sample (the arguments are listed in different lines only for clarity of exposition):> exportMetadata(application='oracle.security.apm', server='AdminServer', toLocation='/myLocation/myRoleTemplates', docs='/oracle/apps/apm/**', restrictCustTo='site')The meaning of the arguments is identical to those used for importing, except for
toLocation, which specifies the location where the data role template(s) should be downloaded.
7.6 About Enforcing Data Security in the Data Model Project
Data security policies secure data from business objects based on the grants made to roles. The business object participating in data security defines a database resource (a database table or view) that has been registered in the Oracle Fusion Applications FND_OBJECTS table. When you need to expose data records in the extended application, you can use JDeveloper and Oracle ADF to create a data model project with ADF entity objects based on secured database resources. However, it is not sufficient to register the business object in FND_OBJECTS and define data security policies. Additionally, you must opt into those data security policies by enabling row-level OPSS authorization checking for specific operations on ADF entity objects in the data model project.
Enabling OPSS authorization checking for the operations (such as view, edit, delete) by setting metadata on the ADF entity object of the data model project, ensures that only end users with sufficient permission are authorized to perform the actions on the database resources corresponding to the ADF entity object.
JDeveloper saves the security metadata that you define on the data model project into an Oracle Metadata Services (MDS) repository.
If the ADF entity object does not appear in the data model project, then you cannot opt into data security policies that may exist for the business object. You must use JDeveloper to create the ADF entity object based on a database table or database view that you intend to register in the Oracle Fusion Data Security schema. For more information, see Customizing and Extending Application Artifacts.
For OPSS to enforce security, the database table or view backing the ADF entity object must be registered as a business object with the FND_OBJECTS table provisioned by Oracle Fusion Data Security (the registered business object is also called a database resource of the Oracle Fusion Data Security schema). You must use Oracle Authorization Policy Manager to register the custom business object corresponding to the ADF entity object data source. For further information about managing data security policies, see Defining Data Security Policies on Custom Business Objects.
Enabling security for custom operations in the data model project requires a custom permission in the data security policy defined on the business object. You must create the custom permission in the data security repository. For more information, see Defining Data Security Policies on Custom Business Objects.
7.6.1 Enforcing Row Security for the Standard Operations of a Business Object
The ADF entity object in a data model project defines metadata that enables OPSS authorization checking against data security policies for view, update, or delete operations (also called standard operations) of the registered business object. You enable row-level security for standard operations by selecting the operation on the ADF entity object that maps to the business object upon which data security policies exist. Although the ADF entity object maps to all instances of the business object, the data security policy defines business object conditions to filter the records available to the end user. Filtering of the business object for standard operations supports only row-level security.
To enforce authorization checking for standard operations:
-
In JDeveloper, display the ADF entity object in the overview editor.
-
In the editor, click the General navigation tab and expand the Security section, and then select the list of standard operations for which you want to enforce authorization checking against data security policies.
Related Links
For further information about enforcing row security for standard operations, see the "Implementing Oracle Fusion Data Security" chapter of the Developer's Guide.
7.6.2 Enforcing Row Security for a Custom Operation of a Business Object
The ADF entity object in a data model project does not support OPSS authorization checking against data security policies for custom operations of the registered business object. You enable row-level security for custom operations by mapping view criteria that you create in the data model project to custom permissions in the data security policies defined on the business objects. The view criteria creates a row set filter by naming the custom permission and business object. Filtering of the business object by view criteria works only with custom operations.
To enforce authorization checking for a custom operation:
-
In JDeveloper, display the ADF view object that you will use to filter the rows and, in the overview editor for the view object, click the Query navigation tab.
-
Expand the View Criteria section and then you click the Add button to create a view criteria to enforce authorization checking for a custom operation. The view criteria must be defined as follows:
-
In the Create View Criteria dialog, create a named view criteria with no view criteria items and name the view criteria using the following format:
FNDDS__permissionName__objectName__objectAlias
where:
permissionNameis the permission name that is used to filter the data.objectNameis the name of the secured database resource in theFND_OBJECTStable.objectAliasis optional and is the alias for the resource.Note:
The delimiter is "__" (double underscore characters). This is because no other special character is allowed in a view criteria name.
-
Select Both for the Query Execution Mode.
The query execution mode for the data security view criteria must be set to Both. If you leave the default setting Database selected, then the ADF Business Components association consistency feature will not work properly.
-
-
Double click the application module that defines the view instance to be filtered and, in the application module overview editor, select the Data Model navigation tab and select the view instance to filter, then click Edit to apply the previously defined view criteria.
Related Links
For further information about enforcing row security for a custom operation, see the "Implementing Oracle Fusion Data Security" chapter of the Developer's Guide.
7.6.3 Enforcing Security for Attributes of a Business Object (as an Alternative to Column-level Security)
The ADF entity object in a data model project does not support authorization checks against data security policies for columns of the registered business object. You enable security for attributes by creating a custom OPSS permission to control access to the column read or update operation, and then, in the Oracle Fusion Data Security repository, you map the operation to a custom permission and grant the permission to specify the roles that are authorized to view or update the data records. Last, in the user interface, you enter an EL expression to test that custom permission on the user interface component displaying the attribute.
Related Links
For further information about enforcing security for attributes of a business object, see the "Implementing Oracle Fusion Data Security" chapter of the Developer's Guide.
7.7 About Defining Function Security Policies for the User Interface Project
Before you begin defining function security policies, you should be familiar with the general process and the information gathering prerequisites that function security entails. Once you have an overview of the process, you can become familiar with the details of the various tasks you can perform.
7.7.1 Process Overview for Function Security
As a security development guideline, you must use only JDeveloper tools to define function security policies. This requires a security administrator to export the policies that exist in the LDAP-based application security policy store (residing in a production environment) into an XML file that can be loaded in JDeveloper and edited using the provided security policy editor.
After editing the XML file, you must consult the security administrator to merge the security policies into the production environment.
In addition, consult the security administrator to obtain the file-based application policy store in the form of a jazn-data.xml file. The security administrator can run an Oracle WebLogic Scripting Tool (WLST) script to export the LDAP-based application policy store to the XML file. For further information about how the security administrator exports the application policy store, see the "Extracting Data from an OID Store to a File" section in the Administrator's Guide.
If the custom bounded task flows or top-level web pages do not appear in the user interface project of the extended application, then you cannot define application security policies. You must use JDeveloper to create the securable Oracle ADF application artifacts. For more information, see Customizing and Extending Application Artifacts.
As an Oracle Fusion Applications security guideline, predefined duty roles defined by the security reference implementation must not be modified. You must use Oracle Authorization Policy Manager to create a new duty role rather than grant function security permissions to predefined duty roles. For further information about creating duty roles, see "Managing Policy Objects in an Application" in the online help for Oracle Authorization Policy Manager, where they are known as application roles.
7.7.1.1 Defining Function Security Policies
In JDeveloper, the general process for defining function security policies is as follows:
-
Consult a security administrator to export all predefined function security policies of the application that you are customizing into a
jazn-data.xmlfile. -
Copy the exported
jazn-data.xmlfile into your application workspace.This is the file that JDeveloper will update when you define function security policies. For JDeveloper to use the file, copy the file to your application workspace in the
<JDevAppHome>/src/META-INFfolder. -
Create an entitlement to group one or more custom resources and their corresponding actions that together entitle end users to access the resource when needed to complete a specific duty.
In the Oracle Fusion Applications environment, the basic security artifact for entitlement-based security polices is the entitlement (an entitlement is defined as a OPSS permission set).
-
Grant the entitlement to a custom duty role that was added to the Oracle Fusion application policy store.
The entitlement grant to the role specifies that the end user must be a member of the role to access the resources specified by the entitlement. You must use custom duty roles and you must not grant entitlements to predefined duty roles.
In JDeveloper, duty role names that you select are identified as OPSS internal roles called application roles.
-
Enable ADF Security for the application by running the Configure ADF Security wizard.
The wizard configures files that integrate ADF Security with OPSS on Integrated WebLogic Server.
After you run the ADF Security wizard, any web page associated with an ADF bounded task flow will be protected. Therefore before you can run the application and test security, you must define the security policies that grant end users access.
7.7.2 About Specific Function Security Tasks You Can Perform
Tasks that you perform to secure functions of the application depend on the type of function and whether the function should be publicly accessible.
7.7.2.1 Creating Entitlement Grants for a Specific Application Role
An entitlement grant is a set of resource grants (set of OPSS permissions) that will be required by the end user to complete a task. Each permission in the entitlement grant names an OPSS permission class, a resource, and an action. Entitlements must be granted to custom application roles.
To grant end users access to enable them to perform tasks:
-
In JDeveloper, select Application then Security and then Entitlement Grants.
-
In the overview editor for security, name the entitlement, add member resources, and add the actions that you want to secure.
-
Grant the entitlement to a custom application role.
Related Links
For further information about creating entitlement grants for a specific application role, see the "Implementing Function Security" chapter of the Developer's Guide.
7.7.2.2 Creating Resource Grants for the Authorized User Role
A resource grant sets an OPSS permission on a single application resource and grants that permission to an application role.
To make a resource publicly accessible by end users:
-
In JDeveloper, to make the resource publicly accessible, select Application then Security and then Resource Grants.
-
In the overview editor for security, select the Oracle ADF artifact, the built-in OPSS role authenticated-role (or anonymous-role) as the grantee, and the action that you want to make public.
Related Links
For further information about creating resource grants for the authenticated user role, see the "Implementing Function Security" chapter of the Developer's Guide.
7.7.2.3 Displaying or Hiding User Interface Components in a Web Page
The rendered attribute of a user interface component controls whether or not the component is visible in the web page. You can create an EL expression using ADF Security utility methods to conditionally render the UI component based on whether the end user has the necessary permission grant.
To hide components in a web page from unauthorized end users:
-
In JDeveloper, open the web page and, in the Property Inspector, select Expression Builder for the Rendered property of the UI component that you want to conditionally render.
-
In the Expression Builder, expand ADF Bindings - securityContext and then select the appropriate EL method followed by the qualified name of the ADF resource that the user will attempt to access.
Related Links
For further information about displaying or hiding user interface components in a web page, see the "Enabling ADF Security in a Fusion Web Application" chapter of the Developing Fusion Web Applications with Oracle Application Development Framework.
7.7.2.4 About Creating a Custom Oracle Platform Security Services Permission and Using it in a Grant
A resource may have a custom OPSS permission that you create to identify an operation that is unique to the resource. You can set the custom permission on a single resource or you can set it in an OPSS permission set, and then grant to an application role. In JDeveloper, you display the Create JAAS Permission dialog that you select in the New Gallery to create the custom permission. You then display the jazn-data.xml file in the overview editor, and in the editor, click the Resource Grants tab or Entitlement Grants navigation tab to use the custom permission in a grant.