4 Apply Technical Patch Bundles: P4FA
The concepts and tasks related to applying P4FA are as follows:
Anatomy of a Technical Patch Bundle (P4FA)
Patches for Fusion Applications (P4FA) are collections of one-off fixes and tech stack updates (e.g. Fusion MiddleWare, Database, Weblogic Server, etc.) compiled and certified for Fusion Applications where an installation of them improves system stability and performance substantially.
MANDATORY: Every Fusion Application release has its own set of P4FA patches and it is mandatory to apply them. P4FA patches are cumulative and administrators must always apply the most recent patch after becoming available on Oracle Support.
-
After downloading the latest patch from My Oracle Support and unzipping it, the first component in the directory is the Patch Number, this changes with every new release of the patch. A new number gets assigned to the latest version of the P4FA Patch.
-
The second component under the actual Patch Number is the README File which contains the instructions to a successful application of a Patch Bundle.
-
Further down in the directory,
/patch number/patches4fa/dist/contains the following sub-components:-
Prepatch provides some patches that need to be applied before applying the actual P4FA patch. Prepatches can be normally taken care of by FASPOT, unless they are Database patches, in which case, it remains a manual task for DBAs, per example:
-
The Exadata patches are applied for an specific type of hardware and they can be found on the
/Exadata/subdirectory. -
The Database patches can be identified within the subdirectory as
/RDBMS/database version/, and to facilitate the manual process of applying the patches, start the application with the PSU patches, and then continue applying the rest of the One-Offs.
-
-
FASPOT is a utility used to automate the application of Oracle Fusion Middleware Patches.
-
Release Directory is the number that contains the rest of the patches normally applied by FASPOT.
-
|- Patch Number
|- README.txt
|- /patches4fa/dist
|- /Prepatch
|- /RDBMS/database version
|- /PSU
|- /Exadata
|- /generic/one_off_patches
|- /FASPOT
|- /Release Directory
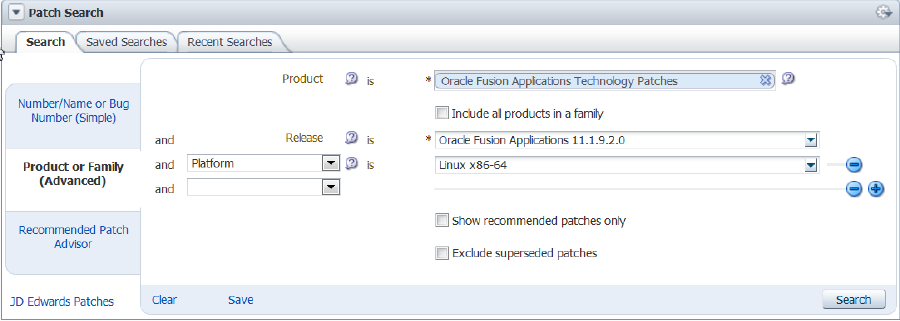
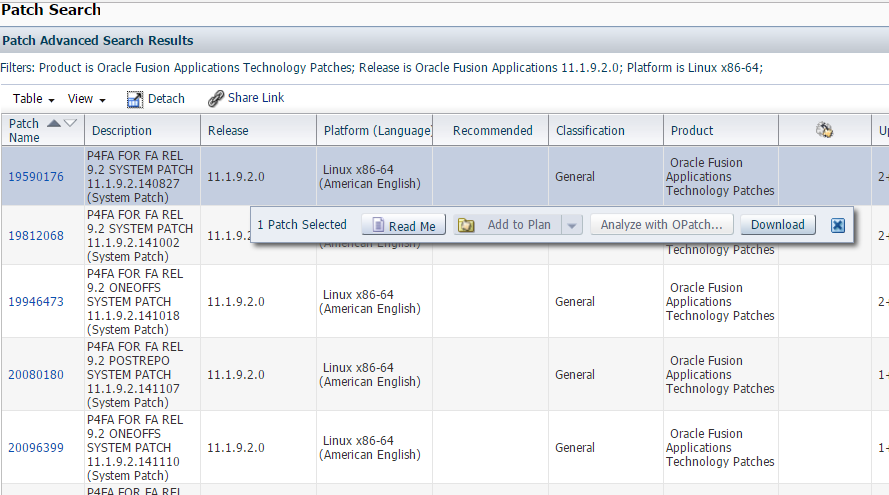
Download a Technical Patch Bundle (P4FA)
What is FASPOT?
A P4FA contains several individual patches, which can result in complex and time consuming installations. FASPOT automates the P4FA patch installation, and its scripts are bundled with the P4FA patches. FASPOT is used to simplify the Fusion Applications tech stack patching process. Since P4FA patches are cumulative, subsequent patches will also include updates from previous patches although they only need to be applied once.
FASPOT orchestrates the installation of the P4FA using ant and provides several targets. FASPOT requires preparation tasks, as described in the Prepare to Apply a P4FA With FASPOT section. After the preparation steps are complete, the patching installation process is performed by an ant script.
MANDATORY: FASPOT must run once on every server that hosts a component of the Fusion Applications tech stack.
FASPOT applies the patches to the following categories:
-
Fusion Middleware Components (including atgpf, ODI, oracle_common, SOA, webtier, BI, ECM, SES, WebCenter, wls)
-
Identity and Access Management (including OID & OHS)
The installation of RDBMS patches are not within the scope of FASPOT and remains a manual task for DBAs. These are out of scope for FASPOT. Number of combinations and variants of existing DB topologies would make it too complex to be automated by scripts. Usually DBA’s use their own mechanisms and best practices to perform DB life cycle management.
Overview of Installing a P4FA With FASPOT
-
Download and extract the P4FA patch, preferably on a shared file system accessible by all hosts for FA, IDM and OHS.
-
Complete the preparation steps as described in the Prepare to Apply a P4FA With FASPOT section.
-
Prepare the staging.
-
Complete RDBMS P4FA patching manually for IDM and FA databases.
-
Start both IDM and FA databases and their services.
-
Run the IDM and FMW patch-apply targets.
-
Start up IDM and FA completely.
-
Run the IDM and FMW post-install targets to deploy various artifacts.
-
Validate the results by performing functional tests.
Prepare to Apply a P4FA With FASPOT
-
Verify disk space availability to support a full installation of P4FA.
-
Unzip the PATCH_DOWNLOAD_DIR/ FASPOT directory. This will now be referred to as FASPOT_HOME_DIR.
-
Verify the Contents of FASPOT_HOME_DIR. The following files and directories should exist in FASPOT_HOME_DIR:
|- README.txt |- build.xml |- config |- … |- env |- faspot.properties |- … |- faspot.sh |- patch_log_dir |- … |- setEnv.sh |- tools |- …
The meaning of files and directories mentioned in this guide is as follows:-
build.xml: The script that contains all targets and actions to perform while patching in a Fusion Applications environment.
-
README.txt: The documentation for each patch.
-
faspot.sh: The script that handles the ant calls for different targets, and is called to execute the ant targets.
-
setEnv.sh: The script to set the environment for the FASPOT utility execution.
-
env: The directory that contains property files that must be updated before script execution.
-
env/faspot.properties: Contains details about installed components and the patch download location.
-
env/faspot.properties.template: The sample template file used to populate the values and generate faspot.properties .
-
config: Contains product specific configuration files and templates that are generated during runtime.
-
tools: Contains ant libraries that are used for setting the ANT_HOME in setEnv.sh.
-
relnumoneoffs: Includes a subdirectory for each type of tech stack. For example, pfcore, weblogic, odi, and idm.
-
prepatch: Includes a subdirectory for each type of tech stack. For example, atgpf, ecm, odi, and soa.
-
-
Create the two directories used by FASPOT as follows:
-
PATCH_WORK_DIR: This directory should be an external directory to be used during runtime by all pods and hosts. It will contain all of the extracted P4FA patches organized in the format required by the FASPOT script.
-
PATCH_LOG_DIR: This directory will be used to store logs generated during execution of the FASPOT script.
-
-
Edit the
faspot.propertiesfile as follows:The
faspot.propertiesfile contains information about the Fusion Applications installation such as host names, directory names, user names, and passwords. This file should be edited for each specific P4FA patch application.-
Copy the properties template file
FASPOT_HOME_DIR/env/faspot.properties.templatetoFASPOT_HOME_DIR/nv/faspot.propertiesso the new file can be edited. Before editing it, make a copy ofFASPOT_HOME_DIR/env/faspot.properties -
Edit both variables for the P4FA download directory and the patch staging directory, as shown in the following example:
PATCH_DOWNLOAD_DIR=P4FA_PATCH_EXTRACTION_DIR/patches4fa PATCH_WORK_DIR=any_directory_to_run_patches_from
-
Update the remaining properties in
env/faspot.properties. As a general rule, replace all placeholder%<value>%with values that are specific to the environment. The following example of thefaspot.propertiesfile shows sample values for each property:#############GENERAL######################################### #PATCH_DOWNLOAD_DIR should contain the following folders ### 1)reloneoffs ############################################################# PATCH_DOWNLOAD_DIR=/u01/fastage/p4fa/19290105/patches4fa/dist PATCH_WORK_DIR=/u01/fastage/p4fa/19290105/patches4fa/workdir ############################################################# ############FA(FMW COPONENTS)################################ #atgpf - ATGPF ############################################################# ATGPF_HOST_NAME=fusionhost.mycompany.com ATGPF_ORACLE_HOME=/u01/app/fa/fusionapps/atgpf ATGPF_JDK_LOC=/u01/app/fa/fusionapps/jdk6 ATGPF_DEFAULTS_FILE=/u01/app/fa/config/atgpf/admin/defaults.txt ATGPF_ADPATCH_WORKERS=4 ATGPF_FA_DB_SID=slc01hye ATGPF_FA_DB_USER=fusion ATGPF_FA_DB_PASSWD=Welcome1 ATGPF_FUSION_ORA_ESS_USER=fusion_ora_ess ATGPF_FUSION_ORA_ESS_PASSWORD=Welcome1 ATGPF_FUSION_RUNTIME_USER=fusion_runtime ATGPF_FUSION_RUNTIME_PASSWORD=Welcome1 ATGPF_SYSTEM_PASSWORD=Welcome1 ATGPF_SYS_PASSWORD=Welcome1 ATGPF_MIDDLEWARE_HOME=/u01/app/fa/fusionapps ATGPF_WEBLOGIC_HOME=/u01/app/fa/fusionapps/wlserver_10.3 ############################################################# #bi - BI ############################################################# #P4FA patching is done from Primoridal host. #Enter PRIMORDIAL_HOST_NAME for BI_HOST_NAME BI_HOST_NAME=fusionhost.mycompany.com BI_ORACLE_HOME=/u01/app/fa/fusionapps/bi BI_JDK_LOC=/u01/app/fa/fusionapps/jdk6prepare-patch-stage BI_WL_ADMIN_USER=FAAdmin BI_WL_ADMIN_PASSWD=Welcome1 BI_WL_ADMIN_URL=t3://fusionhost.mycompany.com:10201
MANDATORY: The previous example does not include all of the sections in thefaspot.propertiesfile which must be edited. The remaining sections that must be edited are as follows:-
ECM
-
ODI
-
OSN
-
ORACLE COMMON – FA(FMW)
-
SES
-
SOA
-
PFCORE
-
WEBCENTER
-
WEBTIER-ADMIN
-
WEBTIER-APPSOHS
-
WEBLOGIC
-
DATABASE
-
OHS – IDM
-
-
Prepare the Patch Staging Area
-
Create the staging area by running the
prepare-patch-stagetarget, which extracts the P4FA patches fromPATCH_DOWNLOAD_DIRinto the directory that is specified by thePATCH_WORK_DIRproperty in thefaspot.propertiesfile. To run theprepare-patch-stage, as follows:cd FASPOT_HOME_DIR sh ./faspot.sh -Dlogfile=prepare-patch-stage prepare-patch-stage > prepare-patch-stage-stdout.log 2>&1 -
Prepare the local environment by creating the required configuration files under the
FASPOT_HOME_DIR/configdirectory. All required instance information needed by other patch application targets is derived from these configuration files. Run the following command from theFASPOT_HOME_DIRdirectory:cd FASPOT_HOME_DIR sh ./faspot.sh -Dlogfile=prepare-local-env prepare-local-env > prepare-local-env-stdout.log 2>&1If a failure occurs while running
prepare-local-envthat requires an update tofaspot.properties, runprepare-local-envagain. The instance specific configuration files underFASPOT_HOME_DIR/configare generated by theprepare-local-envtarget, so any subsequent changes infaspot.propertieshave no impact on the execution of FASPOT targets untilprepare-local-envruns successfully after the updates tofaspot.properties. -
Confirm the primordial host and APPOSH hosts are ready for the P4FA application by running the environment checking target. This target checks the existence of prerequisite patches, the directory paths that are specified in the properties file, connectivity to the databases, and any locks that may prevent patching. Run the following command from the FASPOT_HOME_DIR directory:
cd FASPOT_HOME_DIR sh ./faspot.sh -Dlogfile=fmw-prereq-check fmw-prereq-check > fmw-prereq-check-stdout.log 2>&1 -
Verify the log file after target execution for any failures. In the case of any wrong values provided in
faspot.properties, change the values and rerunprepare-local-envas explained in Step 1. Repeat thefmw-prereq-checktarget execution until all failures are resolved. -
Confirm the AUTHOHS, OAM, and OID hosts are ready for the P4FA application by running the environment checking target. Run the following command from the FASPOT_HOME_DIR directory:
cd FASPOT_HOME_DIR sh ./faspot.sh -Dlogfile=idm-prereq-check idm-prereq-check > idm-prereq-check-stdout.log 2>&1 -
Verify the log file after target execution for any failures. In the case of any wrong values provided in
faspot.properties, change the values and rerunprepare-local-envas explained in Step 1. Repeat theidm-prereq-checktarget execution until all failures are resolved.
Apply Patches with FASPOT
cd FASPOT_HOME_DIR
sh ./faspot.sh -Dlogfile=<target-name> <target-name> > <target-name>-stdout.log 2>&1
- On the IDM host, run
idm-patch-apply. - On the FA host, run
fmw-patch-apply. - On the FA host, run
fmw-patch-postinstall. - On the IDM host, run
idm-patch-postinstall.
Run the IDM and FMW patch-apply Targets
-
Run
idm-patch-applyon the IDM host by performing the following:cd FASPOT_HOME_DIR sh ./faspot.sh -Dlogfile=idm-patch-apply idm-patch-apply > idm-patch-apply-stdout.log 2>&1 -
Run
fmw-patch-applyon the FA host by performing the following:cd FASPOT_HOME_DIR sh ./faspot.sh -Dlogfile=idm-patch-postinstall patch-postinstall > patch-postinstall-stdout.log 2>&1 -
Start the IDM and Fusion Applications Databases
Perform the IDM and FMW Post-Install Tasks
-
Run
fmw-patch-postinstallon the FA host by performing the following:cd FASPOT_HOME_DIR sh ./faspot.sh -Dlogfile=idm-patch-postinstall patch-postinstall > patch-postinstall-stdout.log 2>&1 -
Run
idm-patch-postinstallon the IDM host by performing the following:cd FASPOT_HOME_DIR sh ./faspot.sh -Dlogfile=idm-patch-postinstall patch-postinstall > patch-postinstall-stdout.log 2>&1
Validate Results with Functional Tests
Verify Whether FASPOT Was Successful
-
If FASPOT was successful, then the process ended.
-
If FASPOT was not successful, then see the Troubleshoot Patching Sessions for FASPOT section.