Release 9.2
Part Number A96574-01
Home |
Book List |
Contents |
Index |
 Master Index |
 Feedback |
| Oracle Internet Directory Administrator's Guide Release 9.2 Part Number A96574-01 |
|
This chapter explains how Oracle Internet Directory centrally stores security credentials for easy administration by end users and administrators.
This chapter contains these topics:
Oracle Internet Directory centrally stores security credentials as directory data to make their administration easy for both end users and administrators. When a user leaves a company or changes jobs, that user's privileges should change the same day to guard against misuse of old or unused accounts and privileges. In large enterprises, with user accounts and passwords distributed over multiple databases, an administrator may not be able make all the changes as quickly as good security requires without centralized password administration.
Oracle Internet Directory stores:
Users can store non-Oracle authentication credentials if the non-Oracle applications are directory enabled. These applications must create their own container under the Products entry.
Oracle Internet Directory stores a user's directory password in the userPassword attribute. You can protect this password by storing it as a base 64 encoded string of a one-way hashed value using one of Oracle Internet Directory's supported hashing algorithms. Storing passwords as one-way hashed values--rather than as encrypted values--more fully secures them because a malicious user can neither read nor decrypt them.
During authentication to a directory server, clients supply a password to the directory server in clear text. The directory server hashes this password by using the hashing algorithm specified in the root directory-specific entry (DSE) attribute orclCryptoScheme. It then verifies it against the hashed password stored in the binding entry's userPassword attribute. If the hashed password values match, then the server authenticates the user. If they do not match, then the server sends the user an "Invalid Credentials" error message.
During installation, Oracle Universal Installer prompts you to set the one-way hashing scheme for protecting users' passwords to the directory. It presents you with these options:
The hashing algorithm value you specify at installation is stored in the orclCryptoScheme attribute in the root DSE. You can change that value by using either Oracle Directory Manager or ldapmodify.
You must be a super user to do the following.
To change the type of password protection by using Oracle Directory Manager:
The following example changes the password hashing algorithm to SHA by using an LDIF file named my_ldif_file:
ldapmodify -D cn=orcladmin -w welcome -h myhost -p 389 -v -f my_ldif_file
The LDIF file, my_ldif_file, contains:
dn: changetype: modify replace: orclcryptoscheme orclcryptoscheme: SHA
Oracle components store both passwords and password verifiers in Oracle Internet Directory. This section contains these topics:
Oracle components can store their password values in Oracle Internet Directory as password verifiers. A password verifier is a hashed version of a clear text password. This hashed version is then encoded as a BASE64 encoded string.
You can choose one of these hashing algorithms to derive a password verifier:
During Oracle application installation, the Oracle Universal Installer creates for that application a password verifier profile entry containing all the necessary password verification information. It places this entry as shown in Figure 16-1: immediately below the application entry, which resides under the products entry, which, in turn, resides under the subscriber-specific or default Oracle context.
This verifier profile entry is applicable only to users under the given subscriber. It does not apply to users under a different subscriber. The orclcommonusersearchbase attribute in the common entry of the subscriber Oracle context must be set to the appropriate value for the verifier generation to be successful. This attribute must be set before verifier generation can take effect.
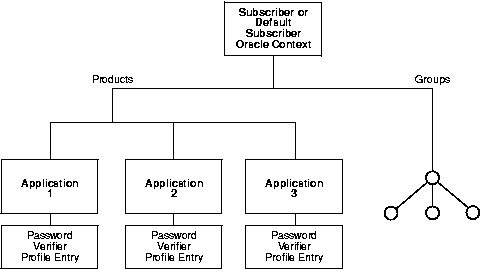
Unlike the directory, which stores user passwords in the userPassword attribute, Oracle components store user password verifiers in one of two password attribute types--authPassword and orclPasswordVerifier--within the user entry. Each attribute type has appID as an attribute subtype. The appID attribute is a unique identifier representing an Oracle application server or authenticating identity. It is generated during application installation. For example, the appID can be the ORCLGUID of the application entry. This uniquely identifies a particular application.
In Figure 16-2, various Oracle components store their password verifiers in Oracle Internet Directory. Oracle9iAS Single Sign-On uses the same password as that for the directory, and hence stores it in the userPassword attribute.The other applications use different passwords and hence store their verifiers in orclPasswordVerifier attribute.
The following is an example of an Application-Verifier Profile:
dn: cn=IFSVerifierProfileEntry,cn=IFS,cn=Products,cn=OracleContext,o=Oracle,dc=com objectclass:top objectclass:orclpwdverifierprofile cn:IFSVerifierProfileEntry orclappid:8FF2DFD8203519C0E034080020C34C50 orclpwdverifierparams;authpassword: crypto:SASL/MDS $ realm:dc=com orclpwdverifierparams;orclpasswordverifier: crypto:ORCLLM
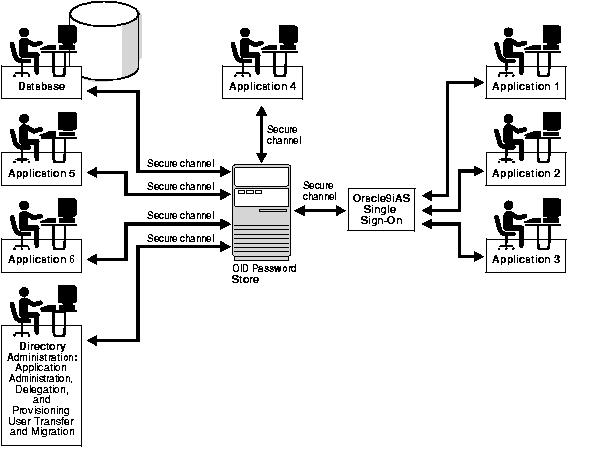
Figure 16-3 shows an example of password verification. In this example, the Oracle component stores its password verifiers in the directory.
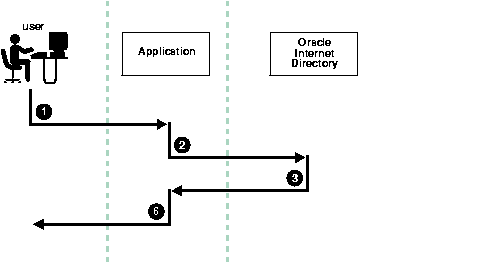
ldapcompare -p389 -D "<dn of the app entity>" -w "<password>" -b "<dn of the user>" -a orclpasswordverifier; <appID> -v <password of the user>
If an application does not use the compare operation, then it simply retrieves from the directory the hashed value of clear text password as entered by the user. The application then compares that value with the hash value it computes. If the two values match, then the application authenticates the user.
You can use Oracle Directory Manager to view and modify password verifier profile entries.
To view an application's password verifiers:
To view an application's password verifier, perform a search specifying the DN of the password verifier profile.
The following example changes the hashing algorithm in an application password verifier profile entry. This password verifier synchronizes with the user's directory password.
ldapmodify -p 389 -h my_host -v <<EOF dn: cn=MyAppVerifierProfileEntry,cn=MyApp,cn=Products,cn=OracleContext,
o=my_company,dc=com changetype: modify replace: orclPwdVerifierParams orclPwdVerifierParams;authPassword: crypto:SASL/MD5 $ realm:dc=com EOF
|
 Copyright © 1999, 2002 Oracle Corporation. All Rights Reserved. |
|