| Oracle® Application Server Enterprise Deployment Guide 10g (10.1.4.0.1) Part Number B28184-02 |
|
|
View PDF |
| Oracle® Application Server Enterprise Deployment Guide 10g (10.1.4.0.1) Part Number B28184-02 |
|
|
View PDF |
Understanding Oracle Access Manager Components
Preparing to Install Oracle Access Manager Components
Installing the First Identity Server on IDMHOST1
Installing WebPass on WEBHOST1
Configuring the First Identity Server
Installing the Second Identity Server on IDMHOST2
Configuring the Second Identity Server
Configuring Oracle Access Manager Single Sign-On for OC4J Applications
Configuring the Second Identity Server as a Failover Server
Configuring the Second Access Server as a Failover Server
Mitigating Identity Server Product Installation Failures on Linux
Creating Failover LDAP Directory Server Profiles for the Identity and Access Servers
Configuring Directory Server Failover
Configuring Access Server Directory Failover for Oracle and Policy Data
Configuring Policy Manager Failover
Creating Failover LDAP Directory Server Profiles for the Identity and Access Servers
Verifying the Status of the Identity Servers
The Oracle Access Manager authentication and authorization services are provided by the components described in this section. The components are shown in Figure 2–2.
Note:
The WebPass and AccessManager components are not available on Windows at the time of publication. Therefore, WEBHOST1, WEBHOST2 and ADMINHOST in the myJ2EEOracle Access Manager configuration must be servers with operating systems other than Windows.WebGate and WebPass on the Web tier with Oracle HTTP Server
WebGate is a web server plug-in access client that intercepts HTTP requests and forwards them to the Access Server for authentication and authorization.
WebPass is a web server plug-in that passes information between a web server and a Oracle Access Manager server. Every web server instance that communicates with a Oracle Access Manager server must be configured with WebPass. WebPass is also required on each computer hosting an Access Manager.
Oracle Access Manager, Identity Server and Access Server on the Application Tier
The Access Manager is a software component that writes policy data to Oracle Internet Directory, and updates the Access Server with policy modifications. It includes an Access System Console that enables administrators to manage policies and the system configuration.
The Oracle Access Manager Identity Server is a software component that processes all user identity, group, organization, and credentials management requests.
The Access Server is a software component that receives requests, responds to the access client, and manages the login session. The Access Server receives requests from WebGate and queries the authentication, authorization, and auditing rules in Oracle Internet Directory to:
Determine whether and how a requested resource is protected
Whether a user is already authenticated
Challenge unauthenticated users for credentials
Determine validity of credentials
Determine whether, and under what conditions, the user is authorized for the requested resource (and communicates the authentication scheme to WebGate, authorizing the user)
The Access Server also manages the login session by helping WebGate to terminate sessions, setting user session time-outs, re-authenticating when time-outs occur, and tracking session activity.
Isolated Subnet for Administration
An isolated subnet on ADMINHOST hosts the Oracle HTTP Server, WebGate, WebPass, and the Access Manager for administrator use.
Access SDK
The Access SDK provides API libraries that protect non-HTTP resources (the AJP protocol is used for communication to OC4J instances) and implement single sign-on for the OC4J applications.
This section describes the sequence for authentication and authorization for J2EE applications using Oracle Access Manager single sign-on:
The user requests an application URL.
A login page is presented.
The user provides a user name and password.
WebGate captures the name and password and communicates with Access Server.
The Access Server communicates with Oracle Internet Directory.
The Access Server authenticates the user and returns the ObSSOCookie to WebGate.
WebGate transmits the cookie and other HTTP headers to mod_oc4j, which routes the request to the appropriate OC4J instance.
OC4J validates the cookie, and/or fetches extra roles from the Access Server.
Before you install the Oracle Access Manager software:
Synchronize the clocks on WEBHOST1, WEBHOST2, IDMHOST1 and IDMHOST2 within 60 seconds. In addition, ensure that:
WEBHOST1 and WEBHOST2 (WebGate, WebPass) are not running ahead of IDMHOST1 and IDMHOST2 (Access and Oracle Access Manager Servers).
The clocks must be synchronized in this manner so that an incoming request is not stamped with a time that has not yet occurred on the receiving server. See http://www.ntp.org for information about time synchronization.
Obtain the DNS host names of all the servers on which you will install Oracle Access Manager components.
Define the Master Identity Administrator user account (this user has access to all Oracle Access Manager functionality).
Have a user account with administrator privileges on all computers.
On Windows, ensure that the user account used to install the Oracle Access Manager server and Access Server has the privilege to log on as a service. The Oracle Access Manager Administrator must have the "Log on as a service" privilege. (Select Control Panel, Administrative Tools, Local Security Policy, Local Policies, User Rights Assignments, Log on as a service.)
Ensure that the directory server you plan to use is installed and configured. If you use Oracle Internet Directory, follow the instructions in Chapter 2, "Installing and Configuring the Security Infrastructure".
Log in to IDMHOST1 as an administrator.
Issue one of the commands below to start the installation (according to platform and installation option):
Windows console installation:
Oracle_Access_Manager10_1_4_0_1_Win32_Identity_Server.exe -console
Windows GUI installation:
Oracle_Access_Manager10_1_4_0_1_Win32_Identity_Server.exe
Solaris console installation:
./Oracle_Access_Manager10_1_4_0_1_sparc-s2_Identity_Server
Solaris GUI installation:
./Oracle_Access_Manager10_1_4_0_1_sparc-s2_Identity_Server -gui
Linux console installation:
./Oracle_Access_Manager10_1_4_0_1_linux_Identity_Server
Linux GUI installation:
./Oracle_Access_Manager10_1_4_0_1_linux_Identity_Server -gui
Note:
If a password error occurs with the-gui installation option, use the console option instead. You may safely ignore any warnings about fonts or scroll bars that occur when using the (default) GUI installation on Solaris.The Welcome screen appears.
Click Next.
The license agreement appears.
Read and accept the terms and click Next.
You are prompted to specify your credentials.
Specify credentials as appropriate to the platform:
Windows:
Click Next to indicate that you are logged in with administrator privileges. If you are not, cancel the installation, log in with administrator privileges, and restart the installation.
UNIX:
Specify the user name and group that the Oracle Access Manager server will use and click Next.
You are prompted for the installation directory.
Leave the field unchanged to accept the default, or change the field to specify a directory of your choice, and click Next.
Note:
(Linux only) If the installation stops after you specify the directory, see Section 5.16.On Linux systems, you are prompted to install and provide the location of libgcc_s.so.1 and libstdc++.so.5 that is compatible with GCC 3.3.2.
On non-Linux platforms, you are prompted to select the locale (language).
Do one of the following:
On Linux, install the GCC runtime libraries and proceed with the installation.
On other platforms, select the default locale and any other locales and click Next.
The installation directory and required disk space is displayed.
Click Next.
A progress message appears, then you are prompted for the transport security mode.
Specify Simple and click Next.
You are prompted for the Identity Server configuration details.
Specify the server name. This name must:
Be unique among all server names in the Oracle Access Manager System Console
Be unique among all server names accessing the same Oracle Internet Directory
Not contain any spaces
Specify the host name on which the Identity Server will reside.
Specify the port on which the Identity server will communicate with WebPass.
You are asked if this is the first Identity server to be installed for the directory server.
Select Yes.
You are prompted for communication details.
Select the Simple option.
You are prompted to update the directory server with the Oracle Access Manager schema. (This includes Oracle Access Manager-specific workflow definitions, attribute policies, tab and panel configurations, configuration attributes, etc.
Select Yes.
Select the option that indicates where data is stored.
Select the schema update option and click Next.
Select the directory server type and click Next.
You are prompted for directory server configuration details.
Specify the Oracle Internet Directory host name, port, bind DN and password and click Next.
Note:
The distinguished name you enter for the bind DN must have full permissions for the user and Oracle Access Manager branches of the directory information tree (DIT). Oracle Access Manager will access the directory server as this account.Documentation references and contact information appears.
Click Next.
An installation summary appears.
Note any details about the installation and click Finish.
Start the Identity server by doing one of the following:
Windows:
Select Start, All Programs, Administrative Tools, Services and start the Identity server service.
Solaris:
Issue this command in Oracle Access Manager installation directory/identity/oblix/apps/common/bin:
Log in to the computer as an administrator.
Issue one of the commands below to start the installation (according to platform and installation option):
Solaris console installation:
./Oracle_Access_Manager10_1_4_0_1_sparc-s2_OHS_WebPassFoot 1
Solaris GUI installation:
./Oracle_Access_Manager10_1_4_0_1_sparc-s2_OHS_WebPass -gui
Linux console installation:
./Oracle_Access_Manager10_1_4_0_1_linux_OHS_WebPass
or
./Oracle_Access_Manager10_1_4_0_1_linux_OHS2_WebPassFoot 2
Linux GUI installation:
./Oracle_Access_Manager10_1_4_linux_OHS2_WebPass -gui
The Welcome screen appears.
Click Next.
The license agreement appears.
Read and accept the terms and click Next.
You are prompted to specify your credentials.
Specify credentials as appropriate to the platform:
Windows:
Click Next to indicate that you are logged in with administrator privileges. If you are not, cancel the installation, log in with administrator privileges, and restart the installation.
UNIX:
Specify the user name and group that the WebPass web server will use and click Next.
You are prompted for the installation directory.
Leave the field unchanged to accept the default, or change the field to specify a directory of your choice (other than the Identity server directory), and click Next.
Note:
(Linux only) If the installation stops after you specify the directory, see Section 5.16.On Linux systems, you are prompted to install and provide the location of libgcc_s.so.1 and libstdc++.so.5 that is compatible with GCC 3.3.2.
On non-Linux platforms, you are prompted to select the locale (language).
Do one of the following:
On Linux, install the GCC runtime libraries and proceed with the installation.
On other platforms, select the default locale and any other locales and click Next.
The installation directory and required disk space is displayed.
Click Next.
A progress message appears, then you are prompted for the transport security mode.
Specify Simple and click Next.
You are prompted for WebPass configuration details.
Specify the WebPass name. This name must:
Be unique among all server names in the Oracle Access Manager System Console
Be unique among all server names accessing the same Oracle Internet Directory
Not contain any spaces
Specify the host name of IDMHOST1, on which the Identity server resides.
Specify the port number of the Identity server with which the WebPass will communicate, and click Next.
A progress message appears, then you are prompted to update the WebPass web server configuration.
Click Yes, then click Next.
Specify the full path of the directory containing the httpd.conf file (ORACLE_HOME/ohs/conf/httpd.conf.
Click Yes to automatically update the web server.
Stop the WebPass web server instance.
If you are using Linux RedHat Advanced Server 3.0:
Update the ORACLE_HOME/opmn/conf/opmn.xml file to set the environment variable LD_ASSUME_KERNEL for the HTTP_Server component, as shown in this example:
...
<ias-component id="HTTP_Server">
<process-type id="HTTP_Server" module-id="OHS2">
<environment>
<variable id="LD_ASSUME_KERNEL" value="2.4.19"/>
</environment>
<module-data>
...
Stop the Identity server service by issuing the following command in the Oracle Access Manager installation directory/oblix/apps/common/bin directory:
stop_ois_server
Start the Identity server service by issuing the following command in the Oracle Access Manager installation directory/oblix/apps/common/bin directory:
start_ois_server
Start the WebPass web server instance.
Click Next.
The Read Me file appears.
Review the file and click Next.
Confirm that the WebPass is installed correctly by performing the following steps:
Ensure that the Identity server and the WebPass web server are running.
Access the Oracle Access Manager system console at this URL:
http://WEBHOST1:port/identity/oblix
The Oracle Access Manager system main page appears.
After the Identity server and the WebPass instance are installed, you must specify the associations between them to make the system functional. Follow these steps to configure the first Identity server:
Access the Oracle Access Manager system console at this URL:
http://WEBHOST1:port/identity/oblix
Click the Identity System Console link.
The System Console setup page appears.
Click Setup.
The Product Setup page appears.
Select Directory Server Type and click Next.
The Schema Change page appears.
Click Next.
Specify the following server details:
In the Host field, specify the DNS host name of the user data directory server.
In the Port Number field, specify the port of the user data directory server.
In the Root DN field, specify the bind distinguished name of the user data directory server.
In the Root Password field, specify the password for the bind distinguished name.
In the Directory Server Security Mode field, specify Simple.
In the Is Oracle data stored in this directory also? field, specify Yes.
Click Next.
A page containing fields for location of user and configuration data appears.
Note:
For detailed information on completing these fields, see "Specifying Object Class Details" on page 140 of the Oracle Access Manager Access and Identity Installation Guide.Provide the Searchbase and Configuration DN and click Next.
For example, the bind distinguished name and location and location of user and configuration data would be an entry resembling the following: dc=us,dc=oracle,dc=com
Provide the Person object class and click the Auto configure objectclass text box, and click Next.
For example, the Person object class would be an entry resembling the following: inetorgPerson
The Group object class screen appears.
Provide the Group object class and click Next.
For example, the Group object class would be an entry resembling the following: groupOfUniqueNames
A message appears instructing you to restart the Oracle Access Manager system.
Stop the Web Pass web server instance.
Stop, then start the Identity server service.
Start the WebPass web server instance.
Return to the Oracle Access Manager system setup window and click Next.
A screen appears summarizing the object class changes that were made automatically.
Click Yes to accept the changes.
Review the Group object class attributes, then click Yes.
The Configure Administrators page appears.
Click Select User.
The Selector page appears.
Complete the fields with the search criteria for the user you want to select as an administrator and click Go.
Search results matching the specified criteria appear.
Click Add next to the person you want to select as an administrator.
The name of the person appears under the Selected column on the right.
Add other names as needed.
Click Done.
The Configure Administrators page appears with the selected users listed as administrators.
Click Next.
The Securing Data Directories page appears.
Verify the configuration by performing these steps:
Access the Oracle Access Manager system console at this URL:
http://WEBHOST1:port/identity/oblix
Click User Manager, Group Manager, or Org. Manager and log in with the newly created administrator user's credentials.
Log in to IDMHOST2 as an administrator.
Issue one of the commands below to start the installation (according to platform and installation option):
Windows console installation:
Oracle_Access_Manager10_1_4_0_1_Win32_Identity_Server.exe -console
Windows GUI installation:
Oracle_Access_Manager10_1_4_0_1_Win32_Identity_Server.exe
Solaris console installation:
./Oracle_Access_Manager10_1_4_0_1_sparc-s2_Identity_Server
Solaris GUI installation:
./Oracle_Access_Manager10_1_4_0_1_sparc-s2_Identity_Server -gui
Linux console installation:
./Oracle_Access_Manager10_1_4_0_1_linux_Identity_Server
Linux GUI installation:
./Oracle_Access_Manager10_1_4_0_1_linux_Identity_Server -gui
Note:
If a password error occurs with the-gui installation option, use the console option instead. You may safely ignore any warnings about fonts or scroll bars that occur when using the (default) GUI installation on Solaris.The Welcome screen appears.
Click Next.
The license agreement appears.
Read and accept the terms and click Next.
You are prompted to specify your credentials.
Specify credentials as appropriate to the platform:
Windows:
Click Next to indicate that you are logged in with administrator privileges. If you are not, cancel the installation, log in with administrator privileges, and restart the installation.
UNIX:
Specify the user name and group that the Identity Server will use and click Next.
You are prompted for the installation directory.
Leave the field unchanged to accept the default, or change the field to specify a directory of your choice, and click Next.
Note:
(Linux only) If the installation stops after you specify the directory, see Section 5.16.On Linux systems, you are prompted to install and provide the location of libgcc_s.so.1 and libstdc++.so.5 that is compatible with GCC 3.3.2.
On non-Linux platforms, you are prompted to select the locale (language).
Do one of the following:
On Linux, install the GCC runtime libraries and proceed with the installation.
On other platforms, select the default locale and any other locales and click Next.
The installation directory and required disk space is displayed.
Click Next.
A progress message appears, then you are prompted for the transport security mode.
Specify Simple and click Next.
You are prompted for Identity Server configuration details.
Specify the Identity Server name. This name must:
Be unique among all server names in the System Console
Be unique among all server names accessing the same Oracle Internet Directory
Not contain any spaces
Specify the host name on which the Identity Server will reside.
Specify the port on which the Identity Server will communicate with WebPass.
You are asked if this is the first Identity Server to be installed for the directory server.
Select No.
You are prompted for communication details.
Select the Simple option.
You are prompted to update the directory server with the Identity Server schema. (This includes Identity Server-specific workflow definitions, attribute policies, tab and panel configurations, configuration attributes, etc.
Select Yes.
Select the option that indicates where data is stored.
Select the schema update option and click Next.
Select the directory server type and click Next.
You are prompted for directory server configuration details.
Specify the second instance's Oracle Internet Directory host name, port, bind DN and password and click Next.
Note:
The distinguished name you enter for the bind DN must have full permissions for the user and Identity Server branches of the directory information tree (DIT). Oracle Access Manager will access the directory server as this account.Documentation references and contact information appears.
Click Next.
An installation summary appears.
Note any details about the installation and click Finish.
Start the Identity Server by doing one of the following:
Windows:
Select Start, All Programs, Administrative Tools, Services and start the Identity Server service.
Solaris:
Issue this command in Identity Server installation directory/identity/oblix/apps/common/bin:
start_ois_server
Follow the steps in Section 5.5, "Installing WebPass on WEBHOST1" to install WebPass on WEBHOST2. After the installation is complete, confirm that the WebPass is installed correctly by performing the following steps:
Ensure that the Identity Server and the WebPass web server are running.
Access the Identity Server system console at this URL:
http://WEBHOST2:port/identity/oblix
The Identity Server system main page appears.
Access the Identity Server system console at this URL:
http://WEBHOST2:port/identity/oblix
The Identity Server System screen appears.
Click Identity Server System Console.
A dialog appears with the message "Application is not set up."
Click Setup.
The Directory Server Type containing User Data screen appears.
Select Oracle Internet Directory from the drop-down list and click Next.
The Location of Directory Server with User Data screen appears.
Complete the fields and selections as follows:
Host - Type the OIDHOST2 host name.
Port Number - 389
Root DN - cn=orcladmin
Root Password - Type the root password.
Directory Server Security Mode - Open
Is the Configuration Data stored in this directory also? - Yes
Click Next.
The Location of Configuration Data and the Identity Server Searchbase screen appears.
Complete the fields as follows:
Configuration DN - dc=us,dc=oracle,dc=com
Searchbase - dc=us,dc=oracle,dc=com
Click Next.
The Securing Data Directories screen appears.
Click Done.
Restart the identity server and the web server.
Access this URL:
http://WEBHOST2:port/identity/oblix
Click any of the links (User Manager, Group Manager, Org. Manager or Identity Server System Console) and log as the administrator user specified in Section 5.6.
Access this URL:
http://WEBHOST2:port/identity/oblix
Click Identity Server System Console.
A login dialog appears.
Provide the orcladmin user name and password and click Login.
The System Configuration screen appears.
Scroll down, and then click Identity System Console. Click System Configuration, then click WebPass.
The two WebPass instances are listed.
Click the WebPass instance for WEBHOST1.
The Details for WebPass screen appears.
Select the WebPass that is installed on WEBHOST1 and click List Identity Servers.
The Identity Servers associated with the WebPass are listed.
Click Add.
The Add a new Identity Server to the WebPass: screen appears.
Select the identity server installed on APPHOST2, select Primary Server and specify 2 connections, then click Add.
Repeat Steps 18 through 21 for the WEBHOST2 WebPass instance.
The Access System consists of three components: The Policy Manager, the Access Server, and the WebGate. The Access System must also have a web server instance installed.
Policy Manager
The Policy Manager is the login interface for the Access System. Administrators use the Access Manager to define the resources to be protected, and to group resources into policy domains.
Access Server
The Access Server is a software component that provides dynamic policy evaluation services for resources and applications. The Access Server receives a request from the web server, queries the LDAP directory to authenticate users, and manages user sessions.
WebGate
The WebGate is a web server plug-in access client that intercepts HTTP requests for Web resources and forwards them to the Access Server for authentication and authorization.
The primary function of the Access System is to provide an access system console for administrators. It is installed on an isolated subnet to provide secure system administrator access to the Identity Server system.
In myJ2EECompany with Oracle Access Manager, these components are installed on the following servers:
Policy Manager on ADMINHOST
Access Server on IDMHOST1 and IDMHOST2
WebGate on ADMINHOST and WEBHOST1 and WEBHOST2
WebPass on ADMINHOST and WEBHOST1 and WEBHOST2
A web server instance is needed to host the Policy Manager components. Follow the steps in Section 3.2.2, "Installing the Oracle HTTP Servers on WEBHOST1 and WEBHOST2" to install a Web Server on ADMINHOST for use with the Policy Manager.
A WebPass instance must be installed on ADMINHOST, at the same directory level on which the Policy Manager will be installed. Follow the steps in Section 5.5, "Installing WebPass on WEBHOST1" to install WebPass for the Policy Manager.
During the installation:
You will be prompted to configure the WebPass against the Identity Server on IDMHOST1:6022; follow the prompts to configure the WebPass.
Note the installation path for the WebPass, since this is the path you will specify in the Policy Manager installation.
After the installation, access the system console at http://ADMINHOST:port/identity/oblix and add a second Identity Server instance, IDMHOST2 on port 6022, for the WebPass.
The Policy Manager must be installed in the same directory as the WebPass on ADMINHOST. Follow these steps to install the Policy Manager:
Log in to ADMINHOST as an administrator.
Issue one of the commands below to start the installation (according to platform and installation option):
Oracle_Access_Manager10_1_4_0_1_Win32_NSAPI_Policy_Manager.exe
Solaris console installation:
./Oracle_Access_Manager10_1_4_0_1_sparc-s2_OHS_Policy_ManagerFoot 3
Solaris GUI installation:
./Oracle_Access_Manager10_1_4_0_1_sparc-s2_OHS_Policy_Manager -guiFoot 4
or
Linux console installation:
./Oracle_Access_Manager10_1_4_0_1_linux_OHS2_Policy_Manager
Linux GUI installation:
./Oracle_Access_Manager10_1_4_0_1_linux_OHS2_Policy_Manager -gui
The Welcome screen appears.
Click Next.
The license agreement appears.
Read and accept the terms and click Next.
You are prompted to specify your credentials.
Specify credentials as appropriate to the platform:
Windows: Click Next to indicate that you are logged in with administrator privileges. If you are not, cancel the installation, log in with administrator privileges, and restart the installation.
UNIX: Specify the user name and group that the web server will use and click Next.
You are prompted for the installation directory.
Leave the field unchanged to accept the default, or change the field to specify a directory of your choice, and click Next.
Note:
(Linux only) If the installation stops after you specify the directory, see Section 5.16.On Linux systems, you are prompted to install and provide the location of libgcc_s.so.1 and libstdc++.so.5 that is compatible with GCC 3.3.2.
On non-Linux platforms, you are prompted to select the locale (language).
Do one of the following:
On Linux, install the GCC runtime libraries and proceed with the installation.
On other platforms, select the default locale and any other locales and click Next.
The installation directory and required disk space is displayed.
Click Next.
A progress message appears, then you are prompted for the location of policy data.
Select No.
You are prompted for the communication method for Oracle Internet Directory.
Select the Open option.
A progress message appears, then you are prompted to update the WebPass web server configuration.
Click Yes, then click Next.
Specify the full path of the directory containing the httpd.conf file (ORACLE_HOME/Apache/Apache/conf).
Click Next.
A message informs you that the web server configuration has been updated.
Stop the Policy Manager web server instance.
Stop and then start the Identity Server instance.
Start the Policy Manager web server instance.
Click Next.
Read Me information appears.
Review the information and click Next.
A message appears informing you that the installation was successful.
Click Finish.
The Policy Manager must be configured to communicate with Oracle Internet Directory. Follow these steps to configure the communication:
Ensure that the web server is running.
Access the Access System Console at the URL for the WebPass instance that connects to the Policy Manager:
http://ADMINHOST:port/access/oblix
The Access System main page appears.
Click the Access System Console link.
A message informs you that the application is not yet set up.
Click Setup.
You are prompted for the directory server type.
Select the user data directory server type.
Specify the following server details:
In the Machine field, specify the DNS host name of the user data directory server.
In the Port Number field, specify the port of the user data directory server.
In the Root DN field, specify the bind distinguished name of the user data directory server.
In the Root Password field, specify the password for the bind distinguished name.
You are prompted for the type of directory server containing Oracle configuration data.
Select the configuration data directory server type and click Next.
A message informs you that you can store user data and Oracle data in the same or different directories.
Select Store Oracle data in the User Directory Server.
You are prompted for the location of policy data.
Select Store Policy and Oracle data in the same directory server.
Specify the following:
Searchbase dc=us,dc=oracle,dc=com (the same searchbase specified during Identity Server installation)
Configuration DN dc=us,dc=oracle,dc=com (the same configuration distinguished name specified during Identity Server installation)
Policy Base dc=us,dc=oracle,dc=com
You are prompted to specify the Person object class.
Specify the Person object class that was specified during Identity Server system configuration, and click Next.
You are prompted to restart the web server.
Stop and then start the WebPass and Access Manager web server instance and the related Identity Server instance.
Click Next.
You are prompted for the root directory for policy domains.
Accept the default root directory for policy domains, or specify a root directory, then click Next.
You are prompted for information about configuring authentication schemes.
Select Yes to start the automatic configuration.
Select Basic Over LDAP and Client Certificate and click Next.
The Define a new authentication scheme screen appears with the Basic over LDAP parameters.
Change the parameters, if needed, and click Next.
The Define a new authentication scheme screen appears with the Client Certificate parameters.
Change the parameters, if needed, and click Next.
You are prompted to configure policies to protect NetPoint URLs.
Select Yes and click Next.
Instructions for completing the Policy Manager setup appear.
Read the information.
Stop the WebPass/Access Manager web server instance.
In the ACCESS_MANAGER_HOME/Apache/Apache/conf/httpd.conf file, comment out this directive:
LoadModule php4_module modules/mod_php4.so
Stop and then start the Identity Server service for the WebPass.
Restart the WebPass/Policy Manager web server instance.
After the Web server reastarts, click Done.
The Policy Manager home page appears.
Confirm that the Policy Manager is installed correctly by performing the following steps:
Access the Access System Console at this URL:
http://ADMINHOST:port/access/oblix
Click the Access System Console link.
Log in as an administrator.
Click the Access System Configuration tab.
Click Authentication Management.
A list of the authentication schemes configured appears.
Before you begin installing the Access Server:
On Windows, ensure that the user account used to install the Access Server has the privilege to log on as a service. The Access Server Administrator must have the "Log on as a service" privilege. (Select Control Panel, Administrative Tools, Local Security Policy, Local Policies, User Rights Assignments, Log on as a service.)
Note that the Access Server cannot be installed in the same directory as the Access Manager.
Follow these instructions to install the Access Server:
Create an instance for the Access Server in the Access System Console:
Access the Access System Console at this URL:
http://ADMINHOST:port/access/oblix
Click the Access System Console link.
Log in as an administrator.
Click the Access System Configuration tab.
Click Access Server Configuration.
Click Add.
The Add Access Server page appears.
In the Name field, provide a name for the Access Server that is different from all others already specified for this directory server.
In the Hostname field, specify IDMHOST1.
In the Port field, specify the port on which the Access Server will listen.
In the Transport Security field, specify Simple (the transport security mode must be the same between all Access Servers and WebGates).
Click Save.
The List All Access Servers page appears with a link to the newly created instance.
Click the link for the instance, print the Details page for reference, and then click Back.
Click Logout and close the browser window.
Issue one of the commands below to start the installation (according to platform and installation option):
Windows console installation:
Oracle_Access_Manager10_1_4_0_1_Win32_Access_Server.exe -console
Windows GUI installation:
Oracle_Access_Manager10_1_4_0_1_Win32_Access_Server.exe
Solaris console installation:
./Oracle_Access_Manager10_1_4_0_1_sparc-s2_Access_Server
Solaris GUI installation:
./Oracle_Access_Manager10_1_4_0_1_sparc-s2_Access_Server -gui
Linux GUI installation:
./Oracle_Access_Manager10_1_4_0_1_linux_Access_Server
The Welcome screen appears.
Click Next.
The license agreement appears.
Read and accept the terms and click Next.
You are prompted to specify your credentials.
Specify credentials as appropriate to the platform:
Windows:
Click Next to indicate that you are logged in with administrator privileges. If you are not, cancel the installation, log in with administrator privileges, and restart the installation.
UNIX:
Specify the user name and group that the web server will use and click Next.
You are prompted for the installation directory.
Leave the field unchanged to accept the default, or change the field to specify a directory of your choice, and click Next.
Note:
(Linux only) If the installation stops after you specify the directory, see Section 5.16.On Linux systems, you are prompted to install and provide the location of libgcc_s.so.1 and libstdc++.so.5 that is compatible with GCC 3.3.2.
On non-Linux platforms, you are prompted to select the locale (language).
Do one of the following:
On Linux, install the GCC runtime libraries and proceed with the installation.
On other platforms, select the default locale and any other locales and click Next.
The installation directory and required disk space is displayed.
Click Next.
A progress message appears, then you are prompted for the transport security mode.
Specify Simple for the transport security mode.
You are prompted for mode in which the Directory Server containing Oracle configuration data is running.
Specify Open.
You are prompted for directory server details.
Specify the following server details:
In the Host field, specify the DNS host name of the Oracle configuration data directory server.
In the Port Number field, specify the port of the Oracle configuration data directory server.
In the Root DN field, specify the bind distinguished name of the Oracle configuration data directory server.
In the Root Password field, specify the password for the bind distinguished name.
In the Oblix Directory field, specify the type of directory server for the Oracle configuration data.
Choose Oracle Directory to specify the location of the policy data.
You are prompted for the Access Server instance ID specified in the Access System Console, and the configuration DN and policy base.
Specify the following:
Access Server ID the name specified when installing the Access Server (step 1.g. in Section 5.10.5, "Installing the Access Server on IDMHOST1 and IDMHOST2").
Configuration DN dc=us,dc=oracle,dc=com (the same configuration distinguished name specified during Identity Server installation)
Policy Base dc=us,dc=oracle,dc=com
Click Next.
Read Me information appears.
Review the information and click Next.
A message appears informing you that the installation was successful.
Click Finish.
Start the Access Server by doing one of the following:
Windows: Locate and start the Windows service for this Access Server. The service name will be the Access Server ID you specified in the Access System Console prepended with NetPoint AAA Server.
Solaris: In the Access Server installation directory/access/oblix/apps/common/bin directory, issue this command:
start_access_server
Repeat the preceding steps on IDMHOST2, substituting the hostname where appropriate.
Before you begin installing the WebGate:
Ensure that the user account used to install the WebGate has administration privileges.
Note that the WebGate may be installed in the same directory as the Access Manager and WebPass. Separate _jvmWebGate and _uninstWebGate subdirectories are included and WebGate information is added to the /oracle directory. If you install WebGate into the same directory as the Access Manager and WebPass, a prompt will appear asking you if you want to replace files. Select No to All.
The WebGate may be installed at the root level or the site level. However, if you have multiple virtual sites, you still only have one instance of WebGate.
You must install WebGate on a computer that hosts a web server. You can configure the WebGate at the machine level or the virtual web server level. However, do not install at both the machine level and the virtual server level.
Follow these instructions to install the WebGate:
Create an instance for the WebGate in the Access System Console:
Access the Access System Console at one of these URLs (depending on where you are installing):
http://ADMINHOST:port/access/oblix
Click the Access System Console link.
Log in as an administrator.
Click the Access System Configuration tab.
Click Add New Access Gate.
In the AccessGate Name field, provide a name for the WebGate that is different from all others already specified for this directory server.
In the Description field (optional), supply additional descriptive information about the WebGate.
In the Hostname field, specify IDMHOST1 or IDMHOST2 or ADMINHOST.
(Optional) In the Port field, specify the port on which the web server will listen.
In the AccessGate Password and Re-type AccessGate Password fields, provide and confirm a unique password for the instance.
In the Transport Security field, specify Simple (the transport security mode must be the same between all Access Servers and WebGates).
In the Preferred HTTP Host field, you may enter the WebGate host name, or you may leave the field blank.
The Primary HTTP Cookie Domain is used to designate a single-sign on domain between WebGates on different hosts. You may leave this field blank.
Click Save.
Details for the WebGate instance appear, and you are prompted to associate an Access Server or Access Server cluster with the WebGate.
Print the page for reference, and then click Back.
Assign an Access Server to the WebGate by performing the following steps:
Navigate to the Details for NetPoint AccessGate page, if necessary. (From the Access System Console, select Access System Configuration, then AccessGate Configuration, then the link for the WebGate.)
The Details for NetPoint AccessGate page appears.
Click List Access Servers.
A page appears with a message that there are no primary or secondary Access Servers currently configured for this WebGate.
Click Add.
The Add a new Access Server page appears.
Select an Access Server from the Select Server list, specify primary server, and define 2 Access Servers (connections) for the WebGate.
Click Add.
A page appears, showing the association of the Access Server with the WebGate.
Repeat Steps c through e to add the second Access Server.
Issue one of the commands below to start the installation (according to platform and installation option):
Windows console installation:
Oracle_Access_Manager10_1_4_0_1_Win32_Domino_WebGate.exe -console
Windows GUI installation:
Oracle_Access_Manager10_1_4_0_1_Win32_Domino_WebGate.exe
Solaris console installation:
./Oracle_Access_Manager10_1_4_0_1_sparc-s2_OHS_WebGateFoot 5
Solaris GUI installation:
./Oracle_Access_Manager10_1_4_0_1_sparc-s2_OHS_WebGate -guiFoot 6
Linux GUI installation:
./Oracle_Access_Manager10_1_4_0_1_linux_OHS_WebGate
or
./Oracle_Access_Manager10_1_4_0_1_linux_OHS2_WebGate
The Welcome screen appears.
Click Next.
The license agreement appears.
Read and accept the terms and click Next.
You are prompted to specify your credentials.
Specify credentials as appropriate to the platform:
Windows: Click Next to indicate that you are logged in with administrator privileges. If you are not, cancel the installation, log in with administrator privileges, and restart the installation.
UNIX: Specify the user name and group that the web server will use and click Next.
You are prompted for the installation directory.
Leave the field unchanged to accept the default, or change the field to specify a directory of your choice, and click Next.
Note:
(Linux only) If the installation stops after you specify the directory, see Section 5.16.On Linux systems, this prompt appears:
To proceed with installation of Oracle Access Manager 7.0.4 WebGate and for successfully running the product, you must install additional GCC runtime libraries, namely libgcc_s.so.1 and libstdc++.so.5. Note that these libraries should be compatible with GCC 3.3.2. The libraries are available for download from either of the following locations - http://metalink.oracle.com (requires login), or http://www.oracle.com/technology/products/ias/index.html. Once these libraries are locally available, please specify the directory containing the files and proceed with the installation. Location of GCC runtime libraries []:
On non-Linux platforms, you are prompted to select the locale (language).
Do one of the following:
On Linux, install the GCC runtime libraries and proceed with the installation.
On other platforms, select the default locale and any other locales and click Next.
The installation directory and required disk space is displayed.
Click Next.
A progress message appears, then you are prompted for the transport security mode.
Specify Cert for the transport security mode for the WebGate.
You are prompted for directory server details.
Specify the following WebGate details:
In the WebGate ID field, specify the unique ID that identifies the WebGate in the Access System Console.
In the WebGate password field, specify the password defined in the Access System Console. If no password was specified, leave this field blank.
In the Access Server ID field, specify the Access Server associated with the WebGate.
In the DNS Hostname field, specify the DNS host name of the Access Server.
In the Port Number field, specify the port on which the Access Server listens for the WebGate.
Specify the password phrase.
Click Next.
Click Yes to automatically update the web server, then click Next.
Specify the full path of the directory containing the httpd.conf file (ORACLE_HOME/Apache/Apache/conf).
A message informs you that the web server configuration has been updated.
Stop, and then start, the web server.
Click Next.
Read Me information appears.
Review the information and click Next.
A message appears informing you that the installation was successful.
Click Finish.
Restart the computer.
Verify the installation by performing the following steps:
Ensure that the Identity Server, WebPass, and Access Server are running.
Access this URL:
https://WEBHOST1:7777/access/oblix/apps/webgate/bin/webgate.cgi?progid=1
The WebGate page appears as shown in Figure 5-1.
If the Load Balancing Router is configured for SSL acceleration, and Oracle HTTP Server is listening on a non-SSL port, you must perform the following steps to make the Access Server function properly:
Access the Access System Console at this URL:
http://ADMINHOST:port/access/oblix
Click the Access System Console link.
Log in as an administrator.
Click the Access System Configuration tab.
Navigate to the WebGate entries section.
Add the user-defined parameter ProxySSLHeaderVar, providing a header variable name, for example:
Name: ProxySSLHeaderVarVal: IS_SSL
Modify the Load Balancing Router (reverse proxy web server) settings to insert an HTTP header string that sets the IS_SSL value to ssl. For example, in the F5 load balancer, in Advanced Proxy Settings, you add the HTTP header string IS_SSL:ssl.
The Access Server SDK contains Access Server API libraries that are needed to perform authentication and authorization services on the Access Server for OC4J applications, specifically to:
Protect non-HTTP resources (the AJP protocol is used for communication to OC4J instances)
Implement single sign-on for the OC4J applications
The Access Server SDK is not included with the Access Server installation package. The SDK is provided in a separate setup package, Oracle_Access_Manager10_1_4_platform_AccessServerSDK[.ext]. You can obtain the Access SDK at:
(URL for Access SDK)
For a comprehensive discussion of the Access SDK, see Chapter 5 of the Oracle Identity Management Application Developer's Guide.
Follow these steps to install the Access SDK on the computers on which you plan to install J2EE applications:
Log on to the computer as an administrator.
Navigate to the Access Server SDK installation package directory.
Launch the installer by double-clicking Oracle_Access_Manager_Win32_AccessServerSDK.exe
The Welcome screen appears.
Click Next.
Click Next.
The license agreement appears.
Read and accept the terms and click Next.
You are prompted to specify your credentials.
Specify credentials as appropriate to the platform:
Click Next to indicate that you are logged in with administrator privileges. If you are not, cancel the installation, log in with administrator privileges, and restart the installation.
You are prompted for the installation directory.
Leave the field unchanged to accept the default, or change the field to specify a directory of your choice, and click Next.
You are prompted to select the locale (language).
Select the default locale and any other locales and click Next.
The installation directory and required disk space is displayed.
Make a note of the directory (you will be prompted to provide it later).
Click Next.
Respond to the successive prompts.
A screen appears with a message that the installation was successful.
Log on to the computer as the owner of the application that the AccessGate will protect.
Navigate to the Access Server SDK installation package directory.
Launch the installer by issuing one of these commands (substituting the platform for the installation):
Solaris GUI:
./Oracle_Access_Manager10_1_4_0_1_sparc-s2_AccessServerSDK
Solaris command line:
./Oracle_Access_Manager10_1_4_0_1_sparc-s2_AccessServerSDK
Linux:
./Oracle_Access_Manager10_1_4_0_1_linux_AccessServerSDK
The Welcome screen appears.
Click Next.
The license agreement appears.
Read and accept the terms and click Next.
You are prompted to specify your credentials.
Specify the user name and group of the owner of the application that the AccessGate will protect and click Next.
You are prompted for the installation directory.
Leave the field unchanged to accept the default, or change the field to specify a directory of your choice, and click Next.
Note:
(Linux only) If the installation stops after you specify the directory, see Section 5.16.You are prompted to select the locale (language).
Select the default locale and any other locales and click Next.
The installation directory and required disk space is displayed.
Make a note of the directory (you will be prompted to provide it later).
Click Next.
On Linux systems, this prompt appears:
To proceed with installation of Oracle Access Manager 7.0.4 Access Server SDK and for successfully running the product, you must install additional GCC runtime libraries, namely libgcc_s.so.1 and libstdc++.so.5. Note that these libraries should be compatible with GCC 3.3.2. The libraries are available for download from either of the following locations - http://metalink.oracle.com (requires login), or http://www.oracle.com/technology/products/ias/index.html. Once these libraries are locally available, please specify the directory containing the files and proceed with the installation. Location of GCC runtime libraries []:
Respond to the prompts.
A screen appears with a message that the installation was successful.
Create an instance for the AccessGate in the Access System Console:
Access the Access System Console at this URL:
http://ADMINHOST:port/access/oblix
Click the Access System Console link.
Log in as an administrator.
Click the Access System Configuration tab.
Click Add New AccessGate.
In the AccessGate Name field, provide a name for the AccessGate that is different from all others already specified for this directory server.
In the Description field (optional), supply additional descriptive information about the AccessGate.
In the Hostname field, specify IDMHOST1 or IDMHOST2 or ADMINHOST.
(Optional) In the Port field, specify the port on which the web server will listen.
In the AccessGate Password and Re-type AccessGate Password fields, provide and confirm a unique password for the instance.
In the Transport Security field, specify Simple (the transport security mode must be the same between all Access Servers and WebGates).
Click Save.
Details for the AccessGate instance appear, and you are prompted to associate an Access Server or Access Server cluster with the AccessGate.
Print the page for reference, and then click Back.
Navigate to:
AccessServerSDK path/oblix/tools/configureAccessGate
Issue this command:
./configureAccessGate -i AccessServerSDK path -t AccessGate
The following prompt appears:
Please enter the Mode in which you want the AccessGate to run: 1(Open) 2(Simple) 3(Cert):
Enter 2.
The following prompt appears:
Please enter the AccessGate ID:
Enter access_gate_APPHOST1_sdk1
The following prompt appears:
Please enter the Password for this AccessGate:
Enter a password.
The following prompt appears:
Please enter the Access Server ID:
Enter access_server_IDMHOST1.
The following prompt appears:
Please enter the Access Server Host Machine Name:
Enter IDMHOST1.mycompany.com.
The following prompt appears:
Please enter the Access Server Port:
Enter 6021.
The following prompts appear:
Preparing to connect to Access Server. Please wait.AccessGate installed Successfully.Press enter key to continue...
Press Enter.
Repeat the steps above on APPHOST2, substituting the host name where appropriate.
Update the opmn.xml file in all OC4J instances to include the AccessSDK shared library path:
<process-type id="app1" module-id="OC4J" status="enabled">
<module-data>
<category id="start-parameters">
<data id="java-options" value="-server
-Djava.library.path=AccessServerSDK path/oblix/lib
-Djava.security.policy=$ORACLE_HOME/j2ee/app1/config/java2.policy
-Djava.awt.headless=true -Dhttp.webdir.enable=false"/>
Restart OPMN by issuing this command in APPHOST2_ORACLE_HOME/OPMN/BIN:
opmnctl reload
Restart the OC4J instances in which the applications using Oracle Access Manager are deployed.
See the Oracle Containers for J2EE Security Guide, Chapter 10, "Oracle Access Manager as Security Provider" for instructions on how to implement single sign-on for OC4J applications on APPHOST1 and APPHOST2.
The Identity Server on IDMHOST2 must be configured to service requests routed to the Identity Server on IDMHOST1 if IDMHOST1 becomes unavailable. Before you can configure the Identity Server on IDMHOST2 as a failover server, it must:
Communicate with the existing Oracle Internet Directory
Be associated with the existing WebPass as a secondary server
There are two failover paths to configure:
Access the Identity Server system console at this URL:
http://ADMINHOST:port/identity/oblix
The Identity Server system main page appears.
Select System Admin, System Configuration, Configure WebPass, WebPass name, Modify.
Complete the fields as follows:
Failover Threshold — The number of live connections from the web component to its primary NetPoint server.
Identity Server Timeout Threshold — The number of seconds the web component waits for a non-responsive NetPoint server before it considers it unreachable and attempts to contact another.
Sleep For (seconds) — The number of seconds after which the WebGate verifies that the number of valid connections equals the maximum number of connections configured.
Save the changes.
Click List Identity Servers.
Click Add.
Select the Identity Server from the drop-down list.
Set the Priority to Primary Server.
Set Number of Connections to 2 or more.
Click Add.
Both Identity servers are listed. Ensure that the number of connections for each is 2 or more.
Select System Admin, System Configuration, Configure Directory Options.
The Configure Profiles page appears with the directory server information.
Select the name of the Identity Server profile from under the Configure LDAP Directory Server Profiles heading.
The Modify Directory Server Profile page appears.
Locate the Used by field and select All Identity Servers.
The Access Server on IDMHOST2 must be configured to service requests routed to the Access Server on IDMHOST1 if IDMHOST1 becomes unavailable. Before you can configure the Access server on IDMHOST2 as a failover server, it must:
Communicate with the existing Oracle Internet Directory
Be associated with the existing WebPass as a secondary server
Access the Access System Console at the URL for the WebPass instance that connects to the Access Manager:
http://ADMINHOST:port/access/oblix
The Access system console page appears.
Select Access System Configuration, AccessGate Configuration, All, Go, Name.
The AccessGate page appears.
Complete the fields as follows:
Failover Threshold — The number of live connections from the web component to its primary NetPoint server.
Access Server Timeout Threshold — The number of seconds the web component waits for a non-responsive NetPoint server before it considers it unreachable and attempts to contact another.
Sleep For (seconds) — The number of seconds after which the WebGate verifies that the number of valid connections equals the maximum number of connections configured.
Save the changes.
Select System Configuration, View Server Settings.
The View Server Settings page appears with the directory server information.
Select the name of the Access Server profile from under the Configure LDAP Directory Server Profiles heading.
The Modify Directory Server Profile page appears.
Locate the Used by field and select All Access Servers.
Save the changes.
At the time of publication, an unresolved defect in a third-party product, InstallShield, caused some Identity Server product installations to stop after the installation directory was specified. This occurred intermittently, and only in the Linux version.
If an installation stopped after the installation directory was specified, repeat the installation as follows:
Open a shell window and paste these lines into it:
cd /tmp mkdir bin.$$ cd bin.$$ cat > mount <<EOF #! /bin/sh exec /bin/true EOF chmod 755 mount export PATH=`pwd`:$PATH
Perform the installation steps for the product you want to install.
Issue this command to empty the temporary directory:
rm -r /tmp/bin.$$
The instructions for configuring failover from Identity Server components to directory servers vary, depending on the component (Identity Server, Access Server, or Access Manager), and whether you are configuring failover for user data or Oracle data. Table 5-1 lists the components, data stores, and configuration methods.
Table 5-1 Supported Failover Configurations for Directory Servers
| Component | Data Store | Operation | Configuration Method |
|---|---|---|---|
|
Identity Server |
User |
Read/Write |
Directory Profile See Section 5.17.1, "Configuring Directory Failover for User Data" |
|
Identity Server |
Oracle |
Read/Write |
Directory Profile and XML Configuration Files See Section 5.17.2, "Configuring Directory Failover for Oracle and Policy Data" |
|
Access Server |
User |
Read/WriteFoot 1 |
Directory Profile See Section 5.17.1, "Configuring Directory Failover for User Data" |
|
Access Server |
Oracle |
Read/WriteFoot 2 |
Section 5.17.2, "Configuring Directory Failover for Oracle and Policy Data" |
|
Access Server |
Policy |
Read/WriteFoot 3 |
Section 5.17.2, "Configuring Directory Failover for Oracle and Policy Data" |
|
Access Manager |
User |
Read |
Directory Profile XML Configuration Files |
|
Access Manager |
Oracle |
Read/WriteFoot 4 |
Section 5.17.2, "Configuring Directory Failover for Oracle and Policy Data" |
|
Access Manager |
Policy |
Read/WriteFoot 5 |
XML configuration files Section 5.17.2, "Configuring Directory Failover for Oracle and Policy Data" |
Footnote 1 Only applicable when password policy is enabled
Footnote 2 Only applicable when the Access Management Service is On. Unless there is only one back-end RAC database, load balancing is not recommended due to cache synchronization problems.
Footnote 3 Only applicable when the Access Management Service is On. Unless there is only one back-end RAC database, load balancing is not recommended due to cache synchronization problems.
Footnote 4 Load balancing for the Access Manager Write profile is not supported unless there only one back-end RAC database, due to cache synchronization problems.
Footnote 5 Load balancing for the Access Manager Write profile is not supported unless there only one back-end RAC database, due to cache synchronization problems.
Note:
Load balancing will work with Oracle Internet Directory, since the directory server instances refer to the same data. However, using load balancing with the directory server in replication mode (for example, IPlanet load balancing) is not recommended, because replication delays can occur, with resulting cache synchronization problems across access servers.This section explains how to configure failover of Identity Server requests to directory servers that contain user data. The failover sequence consists of the LDAP SDK detecting a failure, returning a connection or "server down" error, and directing the request to a secondary directory server.
Each installed component has a directory profile. Follow these steps to configure user data directory failover using the Identity Server System or Access System Directory Profile page:
Access the Directory Profile page for the server on which you are configuring failover:
From the Identity Server System Console, log in as the administrator, then navigate to System Configuration, Directory Profiles.
From the Access System Console, select System Configuration, Server Settings.
Under Configure LDAP Directory Server Profiles, select the directory profile that contains connection information for the component and data for which you want failover capability.
Complete the Failover Threshold field.
Failover Threshold — The number of live primary directory servers required. If the number of primary directory servers drops below the failover threshold, Identity Server attempts to establish a connection to a primary server, if available, and if not, the first secondary server listed, and then the next secondary server listed, and so on.
Complete the Sleep For field with the number of seconds before the watcher thread wakes up and attempts to re-establish or create new connections when connections fail.
Navigate to Database Instances, select Add, and indicate the instances' status as secondary servers.
Note:
To load balance requests between the two Directory Servers, specify both as primary servers here (which represents an active-active failover solution). To configure one server as active and the other as standby (representing an active-passive solution), designate the directory server you added as the secondary server. The secondary server will not operate unless the primary server is not available. In either case, failover is achieved; however, in this guide the active-active solution is emphasized. You may have special considerations that indicate use of an active-passive solution.This section explains how to configure failover in the Identity Server for Oracle and Policy data.
Most of the configuration data is managed in XML configuration files. Multi-language and referential integrity data is managed on the Directory Profile page.
If there is a failure of the primary configuration data directory server, then the Identity Server cannot read any configuration entries. The failover.xml file provides bootstrap secondary directory server information. See Example 5-1 for an example of the failover.xml file.
The procedure for configuring Identity Server failover for Oracle data is:
Follow these steps to create the file for each Identity Server that needs failover capability:
Copy and paste the existing sample_failover.xml file template into the Oracle_Access_Manager_INSTALLATION_DIRECTORY/identity/oblix/config/ldap directory.
Use a text editor to add failover information for secondary servers, using Example 5-1 as a guide (server information and encrypted password shown in bold).
Note:
Instructions for obtaining the encrypted password are provided in Section 5.17.2.1.3, "Creating the Encrypted Password for the Bind DN".Save the sample_failover.xml file as failover.xml.
Example 5-1 failover.xml File
<?xml version="1.0" encoding="ISO-8859-1"?> <CompoundList xmlns="http://www.oblix.com" ListName="failover.xml"> <!-- # Max number of connections allowed to all the active ldap servers -- note this is the same as Max Active Servers> <SimpleList> <NameValPair ParamName="maxConnections" Value="1"> </NameValPair> </SimpleList> <!-- # Number of seconds after which we switch to a secondary or reconnect to a restarted primary ldap server --> <SimpleList> <NameValPair ParamName="sleepFor" Value="60"> </NameValPair> </SimpleList> <!-- # Max amount of time after which a connection to the ldap server will expire --> <SimpleList> <NameValPair ParamName="maxSessionTime" Value="0"></ NameValPair> </SimpleList> <!-- # Minimun number of active primary ldap servers after which failover to a secondary server will occur --> <SimpleList> NameValPair ParamName="failoverThreshold" Value="1"> </NameValPair></SimpleList><!-- # Specify the list of all secondary ldap servers here --><ValList xmlns="http://www.oblix.com"ListName="secondary_server_list"><ValListMember Value="sec_ldap_server"> </ValListMember></ValList><!-- # Specify the details of each secondary ldap server here --><ValNameList xmlns="http://www.oracle.com"ListName="sec_ldap_server"><NameValPair ParamName="ldapSecurityMode" Value="Open"> </NameValPair><NameValPair ParamName="ldapServerName" Value="oidhost.mycompany.com"> </NameValPair><NameValPair ParamName="ldapServerPort" Value="389"> </NameValPair> <NameValPair ParamName="ldapRootDN" Value="cn=orcladmin"> </NameValPair><NameValPair ParamName="ldapRootPasswd"Value="000A0259585F5C564C"> </NameValPair><NameValPair ParamName="ldapSizeLimit" Value="0"></NameValPair><NameValPair ParamName="ldapTimeLimit" Value="0"></NameValPair> </ValNameList> </CompoundList>
To configure directory failover, access the Directory Profile page for the directory profile that contains the Oracle branch of the tree, as described in Section 5.17.1, "Configuring Directory Failover for User Data".
Follow these steps to create the encrypted password:
This section explains how to configure directory failover in the Access Server for Oracle and Policy data.
Navigate to the directory containing the configureAAAServer tool:
AccessServer installation directory/access/oblix/tools/configureAAAServer
Issue this command:
configureAAAServer reconfig AccessServer installation directory
In the preceding command, AccessServer installation directory is the directory in which the Access Server is located.
Type 2 to specify the Simple security mode for the Access Servers that will connect to the directory servers.
You are asked if you want to specify failover information for Oracle or policy data.
Select Y (Yes).
You are prompted to specify the location of the data.
Type the number that corresponds to the location of the data (1 for Oracle tree, 2 for Policy tree).
You are prompted for the action to take.
Type 1 (Add a failover server).
Complete the following fields:
Directory server name
Directory server port
Note:
For LDAP in an Active Directory forest environment, use port 3269 for SSL mode. These are the global catalog ports.Directory server login DN
Directory server password
Select 2 (Open) for Security Mode and 2 (Secondary) for Priority.
Type 5 and press Enter to quit.
You are prompted to commit the changes.
Select 1 (Y) and press Enter to commit the changes.
The ConfigureAAAServer tool automatically creates the following .xml files in the Access Server installation directory/access/oblix/config/ldap directory:
Copy the WebResrcDBfailover.xml file from the Access Server configuration directory to the Policy Manager install directory.
Copy the AppDBfailover.xml file from the Access Server configuration directory to the Policy Manager install directory.
Copy the ConfigDBfailover.xml file from the Access Server configuration directory to the Policy Manager install directory.
Each Identity and Access Server must have a failover directory server profile for user data. A directory server profile is created for each Identity and Access Server at installation time. Each Identity and Access Server must also have a second profile that gives connection information to another directory server, so that if the default directory server is unavailable, the Identity or Access server can connect to another directory server.
Access the Identity Server system console at this URL:
http://ADMINHOST:port/identity/oblix
The Identity Administration page appears.
Select Identity System Console.
A login dialog appears.
Provide the user ID and password and click Login.
The System Configuration page appears.
Click System Configuration, then Directory Profiles.
The Configure Profiles screen appears as shown in Figure 5-2.
Figure 5-2 Oracle Access Administration Configure Profiles Screen
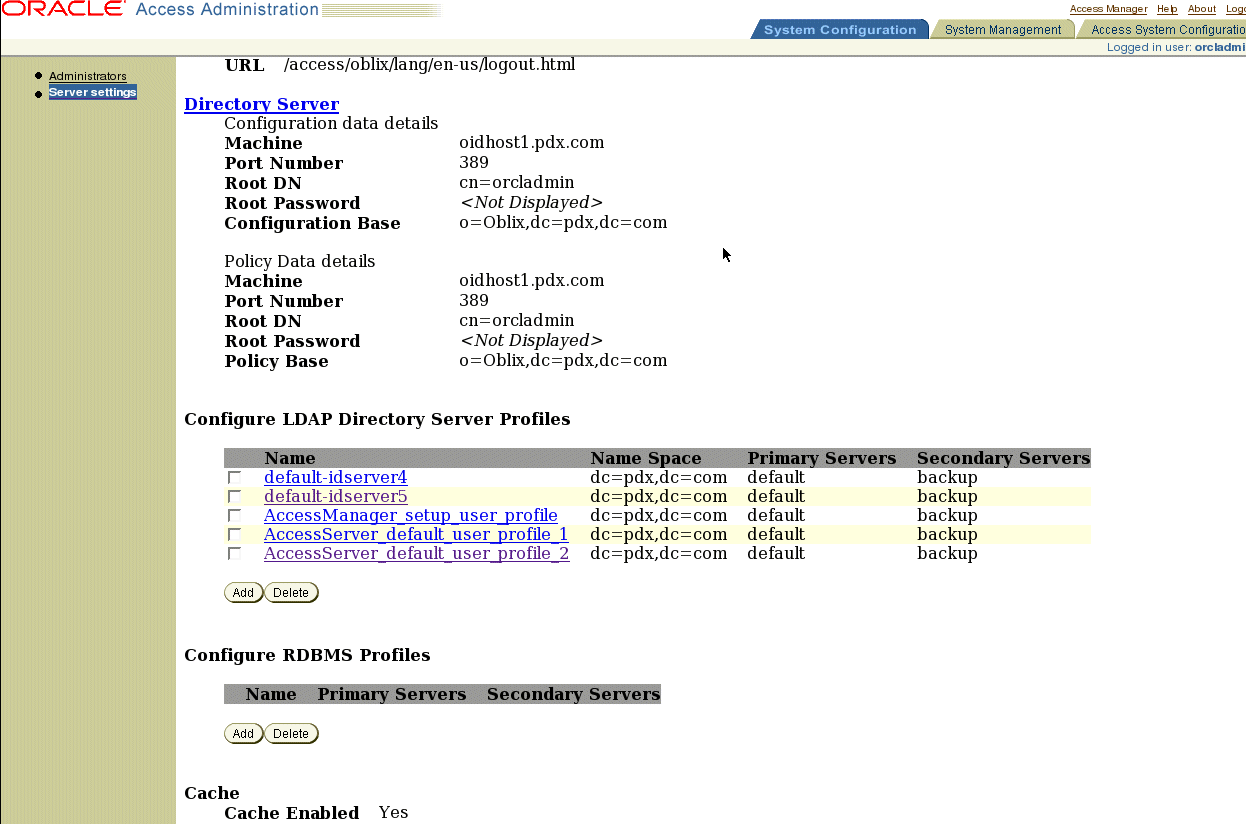
Click the link for the first Identity Server directory server profile in the Configure LDAP Directory Server Profiles section.
The Modify Directory Server Profile screen appears.
In the Database Instances section, click Add.
The Create Database Instance screen appears.
Specify oidhost2.mycompany.com, and select Secondary from the Server Type drop-down list.
Click Save.
The Modify Directory Server Profile screen appears.
Click the link for the second Identity Server directory profile in the Configure LDAP Directory Server Profiles section.
In the Database Instances section, click Add.
The Create Database Instance screen appears.
Specify oidhost1.mycompany.com, and select Secondary from the Server Type drop-down list.
Click Save.
The Modify Directory Server Profile screen appears.
Restart both Identity Servers.
Figure 5-3 Oracle Access Administration Create Directory Server Profile Screen
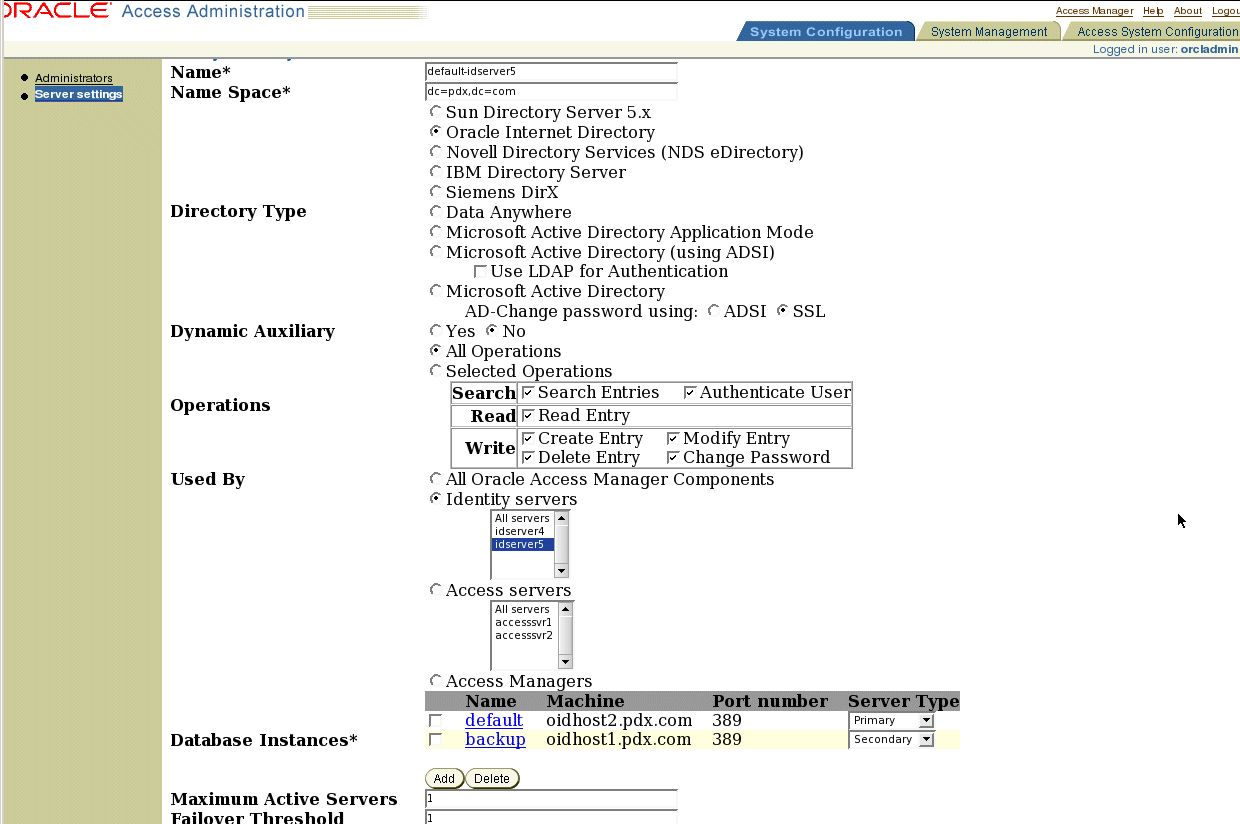
Access the Identity System console at this URL:
http://ADMINHOST:port/access/oblix
The Identity Administration page appears.
Select Identity System Console.
A login dialog appears.
Provide the user ID and password and click Login.
The System Configuration page appears.
Click System Configuration, then Directory Profiles.
The Configure Profiles screen appears as shown in Figure 5-2.
Click the link for the first Access Server directory server profile in the Configure LDAP Directory Server Profiles section.
The Modify Directory Server Profile screen appears.
Record all entries and selections for the first Access Server's directory server profile (print the screen or write the entries and selections).
In the Used By section, select the Access Servers radio button and select Access Server 1 from the drop-down list.
In the Database Instances section, click Add.
The Create Database Instance screen appears.
Specify oidhost2.mycompany.com, and select Secondary from the Server Type drop-down list.
Click Save.
The Modify Directory Server Profile screen appears.
Click Add in the Configure LDAP Directory Server Profiles section.
The Create Directory Server Profile screen appears.
Figure 5-4 Oracle Access Administration Create Directory Server Profile Screen
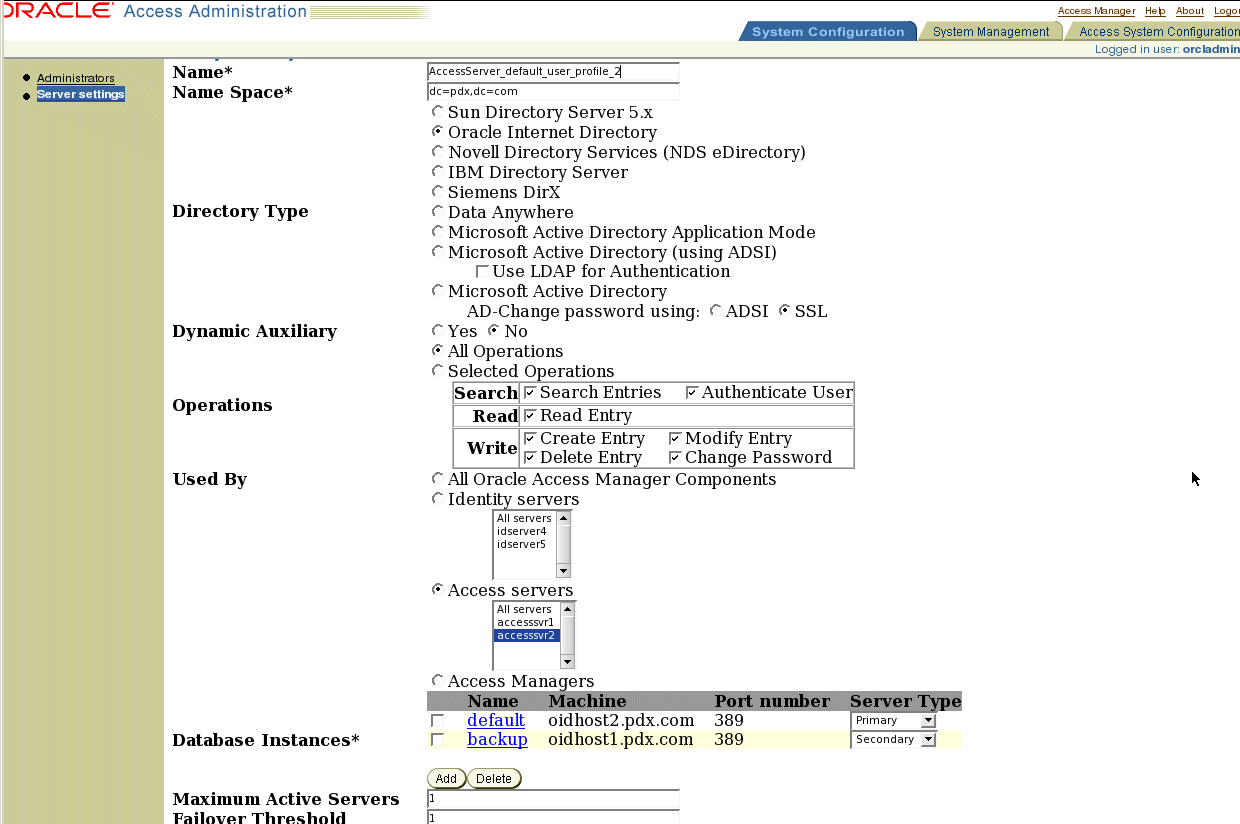
Complete the Name field with a descriptive name for the directory server profile for the second Access Server on IDMHOST2.
Specify these entries and selections:
Directory Type: Oracle Internet Directory
Dynamic Auxiliary: No
Operations: All Operations
Used By: Access Servers (select Access Server 2 from the drop-down list)
Database Instances: oidhost1.mycompany.com (select Secondary from the drop-down list), oidhost2.mycompany.com (select Primary from the drop-down list)
Click Save.
A confirmation dialog appears.
Click OK.
IDMHOST2 now has a default and a failover profile.
You can stop and start servers, perform operations, and then view the status to verify that failover is working.
Access the Identity System console at this URL:
http://IDMHOST1:port/identity/oblix
The Identity Administration page appears.
Select Identity System Console.
A login dialog appears.
Provide the user ID and password and click Login.
The System Configuration page appears.
Click System Configuration, then Diagnostics.
The Server Diagnostics screen appears as shown in Figure 5-2.
Figure 5-5 Oracle Identity Administration Server Diagnostics Screen
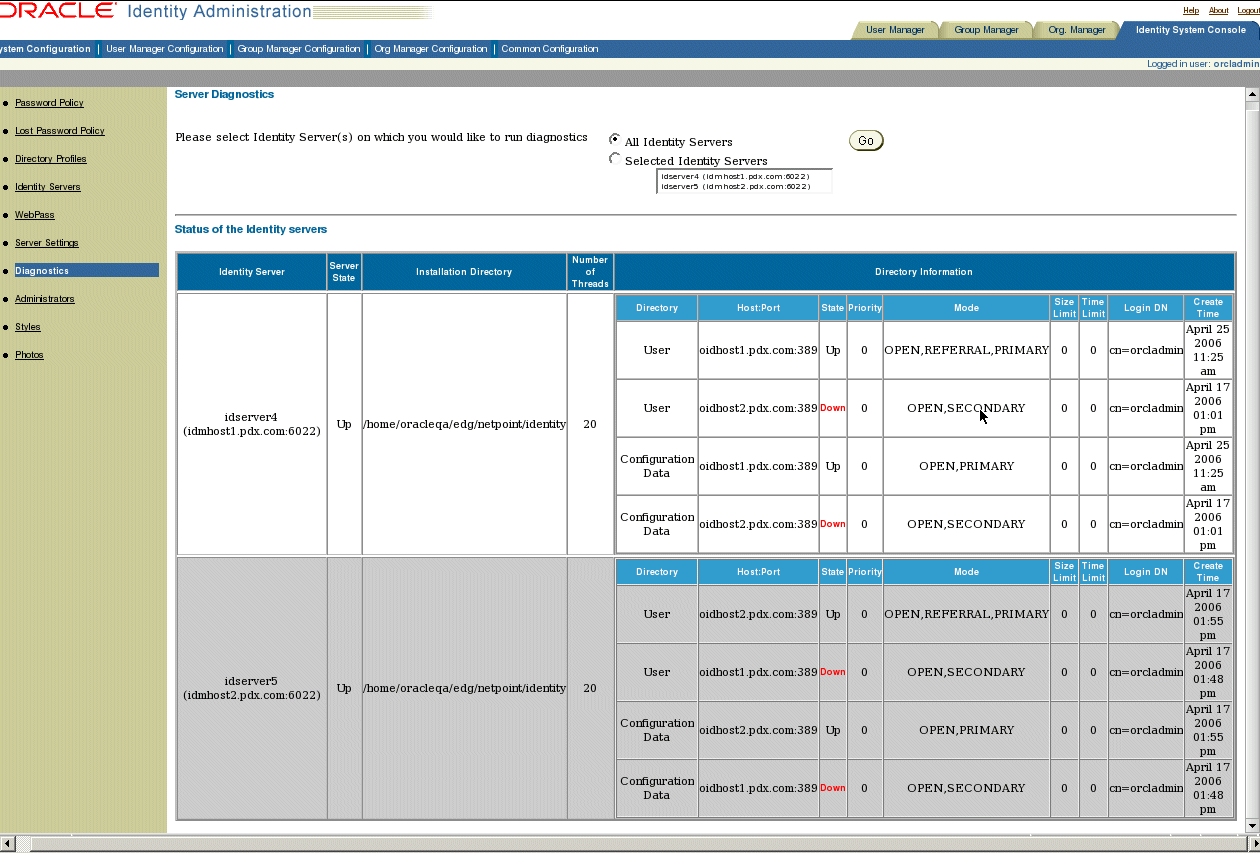
Footnote Legend
Footnote 1: OHS is the Oracle HTTP Server based on the Apache HTTP Server version 1.3