| Oracle® Access Manager Introduction 10g (10.1.4.0.1) Part Number B25342-01 |
|
|
View PDF |
| Oracle® Access Manager Introduction 10g (10.1.4.0.1) Part Number B25342-01 |
|
|
View PDF |
The Oracle Access Manager Access System is an optional companion to the Oracle Access Manager Identity System. The Access System provides centralized authentication, authorization, and auditing to enable single sign-on and secure access control across enterprise resources. Resources include Web content, applications, services, objects in applications on the Web, and similar types of data in non-Web (non-HTTP) resources.
This chapter provides a more in depth look at:
Table 3–1 outlines key access-control features. Details follow the table.
Table 3-1 Access System Features
| Features |
|---|
|
Primary Access System features include authentication, authorization, and auditing (sometimes known as AAA). These features help enforce your company's access security policies for Web applications and content as described in more detail below:
Authentication Services—Provide a generalized means to authenticate users and systems attempting to access resources protected by Oracle Access Manager. Authentication services support both the basic username and password authentication method as well as stronger methods such as digital certificates or SecurID cards.
You can either use standard authentication plug-ins or create your own custom plug-ins using the Authentication Plug-In API. Each custom plug-in implements the authentication interface to pass relevant information between the Access Server and the plug-in. Methods within the interface parse the data. See also "Access System Customization" and "External Authentication".
Once a user is authenticated, Oracle Access Manager creates a single-sign-on (SSO) session for the client that frees the user from having to sign on again to access other resources or applications.
Authorization Services—Deliver consistent, centralized management of policies across applications, while providing users granular access to Web-based content and resources. You can secure sensitive information while helping ensure that users and systems have the easy access they need.
Authorization is governed by a policy domain that includes an authorization expression among a set of default rules that specify how resources for this domain are protected. You can use the authorization scheme provided by the Access System or configure one or more custom schemes that include custom plug-ins created using the Authorization Plug-In API. For details about APIs, see the Oracle Access Manager Developer Guide.
Once authorization is confirmed, the user is granted access to the resource.
Auditing Services—Provide flexible and detailed reporting, auditing, and logging of events in Oracle Access Manager with out-of-the-box reports for Crystal Reports. The auditing and log files enable you to perform threat and intrusion detection, security monitoring, and business-level reporting by integrating with third-party products. Auditing services are global and can be used for Identity System functions as well. For more information about auditing, see the Oracle Access Manager Identity and Common Administration Guide.
Personalization Services—Enable personalization for other applications through HTTP header variables and redirection URLs. When Oracle Access Manager authenticates or authorizes user requests, the URL it returns can contain HTTP header variables which in turn can contain any user data stored under the authenticated user's ID in the directory.
The downstream application can decode this information and use it to personalize the user experience. You can include a redirection URL with the URL returned by Oracle Access Manager, which may take the user to another Web page tailored to the identity of the user.
Single Sign-On—Enables users and groups of users to access multiple applications after a single login and authentication. This improves the user experience by eliminating multiple logins. During a session, a cookie is generated and stored on the user's computer. This cookie eliminates the need for additional logins when users need access to single-domain servers for subsequent requests to the Web site. Users needing access to multi-domain servers have a cookie generated by a central Web login server; this occurs transparently for each accessed server within the associated Web system.
Delegated Access Administration—Enables distribution of administrative tasks. When the responsibility for managing the Access System falls on a few people, you may want these people to appoint others to share the work. For example, you can delegate the ability to modify the revoked user list and to add, modify, or delete configuration details and schemes.
The next discussion provides a sample Access System installation.
The Oracle Access Manager Access System enables you to centralize access policy creation while decentralizing policy management and enforcement. The following types of resources can be protected using the Access System:
HTTP resources including directories, pages, Web-based applications, query strings, and so forth
J2EE application server resources, including Java server pages (JSPs), servlets, and enterprise Java beans (EJBs)
Other resources, including standalone programs (Java, C, C++), ERP applications, CRM applications, and the like
Figure 3-1 shows the basic components of the Access System. The WebGate communicates with the Access Server; the Access Server communicates with the directory server; the Policy Manager communicates with the directory server through a WebPass.
Figure 3-1 Basic Access System Installation
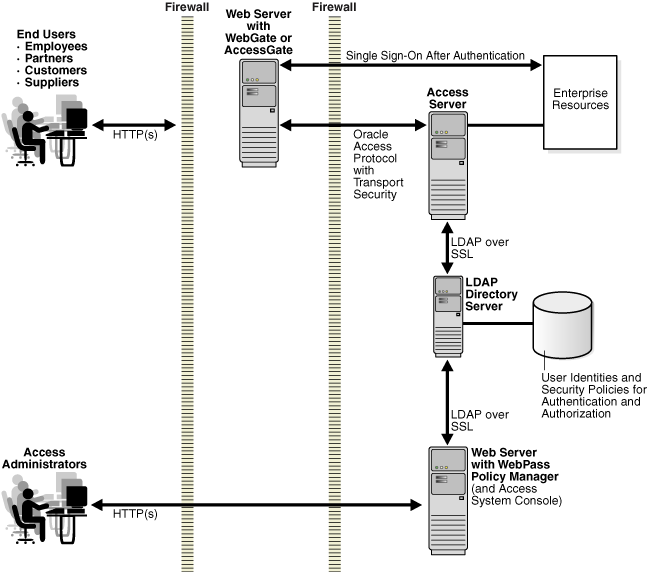
The Oracle Access Protocol (formerly known as the NetPoint or COREid Access Protocol) enables communication between Access System components during user authentication and authorization. Transport security between Oracle Access Manager Web clients (Policy Manager and WebPass; Access Server and WebGate) can be Open, Simple (Oracle-provided), or Cert (third-party CA). In both Simple and Cert mode, Oracle Access Manager components use X.509 digital certificates only.
Transport security between Access Servers and the directory server (and Policy Managers and directory server) may be either open or SSL-enabled. The same mode must be used between all Policy Managers and the directory server.
During Policy Manager installation and setup, the LDAP directory server is updated to include policy data (access policy data). All access policy definitions defined in the Policy Manager are stored in the directory server.
Access System components and operations are discussed in greater detail in the discussions:
This discussion introduces the Policy Manager, Access System Console, and functions available with each.
Policy Manager—Provides a Web-based interface where administrators can create and manage access policies. The Policy Manager also communicates with the directory server to write policy data, and communicates with the Access Server over the OAP to update the Access Server when certain policy modifications are made.
Master Access Administrators and Delegated Access Administrators use the Policy Manager to:
Create and manage policy domains that consist of:
Resource types to protect
Authentication, authorization, and audit rules
Policies (exceptions)
Administrative rights
Add resources to policy domains
Test access policy enforcement
The Policy Manager must be installed on a machine hosting a Web server instance with a WebPass (installed at the same directory level as the Policy Manager). Oracle recommends that you install multiple Policy Managers for fault tolerance. For details about installing and setting up the Policy Manager, see the Oracle Access Manager Installation Guide.
Access System Console—Included with the Policy Manager installation. The Web-based Access System Console provides a login interface to the tabs and functions that allow any Master Administrator, Master Access Administrator, and Delegated Access Administrator to perform specific operations, including:
System Configuration Tab—Enables a Master Administrator to assign one or more users to be a Master Access Administrator, as well as add or remove Delegated Access Administrators and their rights. Responsibilities of a Master Access Administrator include defining resource types, policy domains, and authentication and authorization schemes.
From the System Configuration tab, administrators can also view and change server settings. For example, specify email addresses for bug reports, user feedback, and the company Web master.; change the default logout URL for single sign-on; configure directory server settings; view cache settings.
System Management Tab—Enables a Master Administrator to manage:
Diagnostics—Show Access Server details, including connection information.
Manage Reports—Create, view, or modify user access privilege reports.
Manage Sync Records—Archive or purge synchronization records generated by the Policy Manager before a given date. To help manage the space these records consume on the directory server, it is a good idea to periodically archive or purge all the records before a specified date.
Access System Configuration Tab—Enables a Master Access Administrator or Delegated Access Administrator to complete the following tasks:
View, add, modify, and delete AccessGates, Access Servers, Access Server clusters, Host Identifiers
View and modify authentication and authorization parameters; Web resource user rights; and common information
Configure common information, including:
Shared Secret: Generate a cryptographic key that encrypts cookies to a browser.
Master Audit Rule: Create the default Master Audit Rule for this installation.
Resource Type Definitions: Define and manage resource types.Flush Password Policy Cache: Select a password policy and flush all associated caches or select a Lost Password Management policy and flush all associated caches.Duplicate Actions: Select a policy for handling Duplicate Action Headers
Administrators access the Policy Manager and Access System Console by entering the following URL in a browser, where hostname refers to the machine that hosts the WebPass and Web server; port refers to the HTTP port number of the WebPass Web server instance; and /access/oblix connects to the targeted Access System.
http://hostname:port/access/oblix
The Oracle Access Manager Access Server plays a key role in authentication and authorization:
Authentication involves determining what authentication method is required for a resource and gathering credentials from the directory server, then returning an HTTP response based on the results of credential validation to the access client (WebGate or AccessGate).
Authorization involves gathering access information and granting access based on a policy domain stored in the directory and the identity established during authentication.
To perform these operations, you may have one or more standalone Access Server instances that communicate with both the directory server and WebGate. Before you can install an Access Server instance, you must define it in the Access System Console.
|
Note: Oracle recommends that you install multiple Access Servers for failover and load balancing. |
Process overview: The Access Server
Receives requests from an Oracle Access Manager access client (WebGate or AccessGate)
Queries authentication, authorization, and auditing rules in the directory server to determine whether:
The resource is protected (and if so, how)
The user is already authenticated (if the user is not yet authenticated, a challenge is provided)
The user credentials are valid
The user is authorized for the requested resource, and under what conditions
Responds to the access client as follows:
Manages the session, by:
Helping the WebGate terminate user sessions
Re-authenticating when there is a time out
Tracking user activity during a session
Setting session timeouts for users
Throughout Oracle Access Manager manuals, the terms AccessGate and WebGate may be used interchangeably. However, there are differences worth noting:
A WebGate is a Web server plug-in access client that intercepts HTTP requests for Web resources and forwards them to the Access Server for authentication and authorization. A WebGate is shipped out-of-the-box with Oracle Access Manager.
An AccessGate is a custom access client that is specifically developed using the Software Developer Kit (SDK) and Oracle Access Manager APIs, either by you or by Oracle. An AccessGate is a form of access client that processes requests for Web and non-Web resources (non-HTTP) from users or applications. For more information, see "Custom Access Clients".
A WebGate intercepts requests for resources from users or applications and forwards requests to the Access Server for authentication and authorization. See "Access System Operation" for more information.
Before you can install a WebGate, you must define it in the Access System Console and associate it with an Access Server or cluster of Access Servers. For details, see Oracle Access Manager Installation Guide.
Figure 3-2 illustrates how Access System components work in concert during authentication and authorization. A description follows the figure.
Figure 3-2 Basic Access System Operations
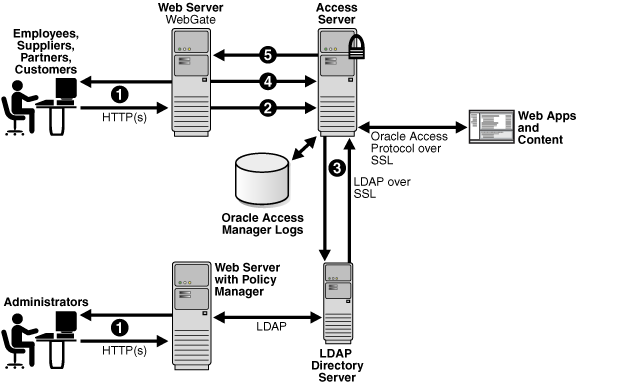
Process overview: When a user requests access
The WebGate intercepts the request.
Servers that can be protected include Web servers, application servers, and FTP servers (using the Oracle Access Manager SDK), among others.
The WebGate forwards the request to the Access Server to determine whether the resource is protected, how, and if the user is authenticated (if not, there is a challenge).
The Access Server checks the directory server for credentials such as a user ID and password, sends the information back to WebGate, and generates an encrypted cookie to authenticate the user.
The Access Server authenticates the user with a customer-specified authentication method to determine the identity, leveraging information stored in the directory server. Oracle Access Manager authentication supports any third-party authentication method as well as different authentication levels. Resources with varying degrees of sensitivity can be protected by requiring higher levels of authentication that correspond to more stringent authentication methods.
Following authentication, the WebGate prompts the Access Server to look up the appropriate security policies, compare them to the user's identity, and determine the user's level of authorization.
If the access policy is valid, the user is allowed to access the desired content or applications.
If the policy is false, the user is denied access and redirected to another URL determined by the organization's administrator.
As mentioned earlier, the Policy Manager communicates with the directory server to write policy data, and communicates with the Access Server over the OAP to update the Access Server when you make certain policy modifications. The WebPass intercepts and forwards administrator requests for the Policy Manager.
Various components and methods are provided to help you customize the Oracle Access Manager Access System, including:
AccessGates are custom-built Access Server clients (or agents) that process user requests for access to resources within the LDAP domain protected by Oracle Access Manager. The code for processing user requests can be embedded in a plug-in or written as a standalone application.
An AccessGate uses an Access Server to control attempts to access a Web site. AccessGates allow you to extend authorization and authentication rules to other resources in addition to URLs and to control user interaction with applications outside of Oracle Access Manager. This provides you with centralized policy information that applies to Web and non-Web resources.
For more information about AccessGates, see the Oracle Access Manager Developer Guide. See also "Access Manager API".
You can either use the standard authentication and authorization plug-ins that are installed with the product, or create your own custom plug-ins using the Oracle Access Manager Authentication Plug-In API and Authorization Plug-In API. Each custom plug-in implements the appropriate interface (authentication or authorization). Depending on the plug-in, the interface is activated to pass relevant information between the Access Server and the plug-in. Methods within the interface parse the data.
Custom plug-ins can be developed using the C language and C# (.NET managed code) Authentication Plug-In API and Authorization Plug-In API.
The Access Manager API is a subset of the Software Developer Kit. You can use the Access Manager API to write custom access client code in any of the four supported development languages to integrate with Java, C and C++, and C# (.NET) applications. The four implementations are functionally equivalent even though each takes advantage of platform-specific features to implement the API.
For more information, see "Custom Access Clients".
You can use the Policy Manager API (a subset of the Access Manager SDK) to create and manage policy domains and their contents and to allow custom applications to access the authentication, authorization, and auditing services of the Access Server. For example, you can write applications that use the programmatic interface instead of the GUI to create, modify, delete, and retrieve policy domains and their contents.
To better understand the functions provided by the Policy Manager (and Policy Manager API), explore the Policy Manager GUI and see information in the Oracle Access Manager Access Administration Guide.
The Policy Manager API provides Java, C, and managed code bindings for classes which you can use to instantiate specific objects. For more information, see Oracle Access Manager Developer Guide.
The Oracle Access Manager Software Developer Kit is an optional component that must be installed independently. It provides libraries, build instructions, examples and resources for Access System APIs for each of the supported development platforms. Using the APIs, you can construct interfaces that can be built into commercially available application servers such as IBM WebSphere, Sun, or another application that can access the Access Server for authentication and authorization.
Individual Access System APIs are introduced in this chapter. For details about the Software Developer Kit and all APIs, see the Oracle Access Manager Developer Guide.
Oracle Access Manager external authentication enables you to integrate multiple security systems across corporate boundaries through trust and technology relationships.
After installation, Oracle Access Manager must be configured to trust an external SSO solution for authentication. During authentication runtime, identity information provided by the third-party authentication mechanism is accepted and mapped to the appropriate user being authorized by Oracle Access Manager.
For details about external authentication mechanisms, see the Oracle Access Manager Access Administration Guide and the Oracle Access Manager Integration Guide.
The term federation is derived from the Latin word for trust. When used in the context of security management, federation essentially means integrating multiple security systems together through trust and technology relationships. Federated authentication enables you to integrate multiple security systems across corporate boundaries.
For details about external authentication mechanisms supported by Oracle Identity Federation, see the Oracle Identity Federation Administrator's Guide.
Other chapters in this guide provide a more in depth look at concepts, behaviors, manuals, and terminology: