| Oracle® Access Manager Introduction 10g (10.1.4.0.1) Part Number B25342-01 |
|
|
View PDF |
| Oracle® Access Manager Introduction 10g (10.1.4.0.1) Part Number B25342-01 |
|
|
View PDF |
Identity administration governs how digital identities, groups and organizations are created, maintained, and leveraged throughout an organization. The Oracle Access Manager Identity System provides a full range of identity administration applications and functions that provide a simple, controlled means to change user, role, group, and organization information that dynamically affects access privileges. It is the roles and relationships used by the policies that determine what on-line systems and applications a person can access.
This chapter provides a more in depth look at:
Table 2–1 outlines Identity System administration features. Descriptions follow the table.
Table 2-1 Features and Benefits of the Identity System
| Features |
|---|
|
The items in the table above are described in greater detail below:
Centralized User, Group, and Organization (object) Management—Enables you to provide different access policies for different people and groups and to manage organizational entities, such as assets and maps. Information in the Oracle Access Manager Identity System can then be leveraged by the Oracle Access Manager Access System to manage access privileges based on user attributes, group membership, or association with an organizational entity.
Dynamic Role-Based Identity Administration—Provides security that is guided by user identity-based access privileges. For example, a role may include all users or all managers or direct-reports only, and so on.
A Customizable Multi-Step Identity Workflow Engine—Enables you to map and automate business processes, policies, and approvals relating to identity data. For example, you can model your business processes in the Identity System using workflows to:
Create, delete, and modify users, groups, and organizations
Implement self-registration of users and organizations
Subscribe and unsubscribe to groups
Multi-Level Delegation of Identity Administration—Enables you to scale up to millions of users by delegating identity administration activities. Administrators can delegate all or some of the rights they have been granted, and they can choose whether or not to allow their delegates to pass these rights on to others. The tasks that are delegated are specific to the right, the target, and the tree path.
Self-Service—Enables you to implement a secure self-service model for organizational functions such as password change. Users with self-service permissions can manage their own information without the use of a workflow.
Self-Registration—Provides limited access to your system through the initiation and processing of a self-registration workflow.
For example, you can set up a self-registration workflow such that when a user self-registers, the registration request is forwarded to appropriate people for approval. Upon approval, the user is immediately and automatically granted access to all appropriate resources based on his or her identity attributes.
Data Management Layer—Supports multiple LDAP environments, RDBMS databases, and split-directory profiles. This feature is also known as Data Anywhere and is available with Oracle Virtual Directory. Data Anywhere aggregates and consolidates data from RDBMS and LDAP directories into a virtual LDAP tree. The tree can be managed by the Oracle Access Manager Identity System and used to support authentication and authorization with the Oracle Access Manager Access System. For complete details, see the Oracle Access Manager Identity and Common Administration Guide.
Password Management Services—Enables you to specify multiple password policies, constraints on password composition, a configurable password validity period and notification, forced password change, lost password management setup, and password creation/change rules.
User Interface Customization—Provides several methods you can use to change the appearance of Oracle Access Manager applications and control operations, and connect CGI files or JavaScripts to Oracle Access Manager screens. For details, see the Oracle Access Manager Customization Guide.
Extensive APIs for Identity Integration—Enables you to gain access and interact with Oracle Access Manager without using a browser, and implement functions and executables triggered by events within Oracle Access Manager. For details, see the Oracle Access Manager Customization Guide.
Unless otherwise indicated, you can find more information about these features and how to configure them in the Oracle Access Manager Identity and Common Administration Guide. For a simple installation diagram, see the next discussion: "Identity System Components, Applications, and Functions".
The Oracle Access Manager Identity System provides the infrastructure needed for other applications and systems to leverage user identity and policy information across the enterprise. This eliminates the need to create and manage separate user identity repositories for each application.
Figure 2-1 illustrates the basic Identity System components in a simple environment, as well as transport security between components over the Oracle Identity Protocol (formerly known as the NetPoint or COREid Identity Protocol). The end users and Administrators are separated from components by a firewall. The Web server with WebPass installed resides in the DMZ. The Identity Server and directory server reside behind the second firewall.
Figure 2-1 Components in a Simple Environment
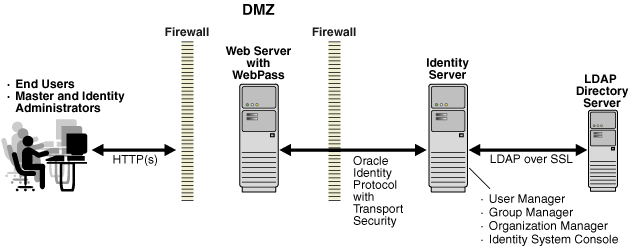
The Oracle Identity Protocol facilitates communication between Identity Servers and associated WebPass instances. Transport security between Oracle Access Manager Web clients (WebPass and Identity Server) may be specified as Open, Simple (Oracle-provided), or Cert (third-party CA). In both Simple and Cert mode, Oracle Access Manager components use X.509 digital certificates only. Transport security between Identity Servers and the directory server may be either open or SSL-enabled.
During Identity System installation and setup, the LDAP directory server is updated to include the Oracle Access Manager schema with object classes and attributes for the entire system. Oracle Access Manager enables you to store various types of data on the same directory server type, or separate directory server types. Data types include:
User Data—User directory entries managed by Oracle Access Manager.
Configuration Data—Oracle Access Manager configuration details stored in the directory and managed by the Identity System.
Policy Data—Access policy definitions defined in the Policy Manager are stored in the directory server.
For more information, see the Oracle Access Manager Installation Guide.
Also during Identity System installation and setup, the Master Oracle Access Manager Administrator (Master Administrator) is assigned. The Master Administrator is a super user who is empowered to configure the deployment and assign administrative tasks. Using the System Console, the Master Administrator can create additional Master Administrators, as well as Master Identity Administrators and Master Access Administrators. For example, a Master Identity Administrator can delegate authority to other administrators, which enables management of millions of users.
In addition to managing identity information, you can use the Identity System to manage access privileges for a user based on a specific user attribute, membership in a group, or association with an organization. Administrators can link privileges together into a workflow so that, for example, when a user self-registers, the registration request is forwarded to appropriate people for signoff.
The Identity System is required in all Oracle Access Manager installations and consists of:
Your Oracle Access Manager installation must include at least one Identity Server. You use the Identity Server to manage identity information about users, groups, organizations, and other objects. Your installation may include one or more Identity Server instances. The Identity Server performs three main functions:
Reads and writes to your LDAP directory server across a network connection
Stores user information on a directory server and keeps the directory current
Processes all requests related to user, group, and organization identification
Each instance of the Identity Server communicates with a Web server through a WebPass plug-in, as discussed in "WebPass".
The Identity Server provides the following Identity applications, which are accessed through a Web-based interface. All have a reporting capability:
User Manager—Enables complete management of all identity information related to individual network users.
The User Manager enables administrators to add, modify, deactivate, and delete user identities. In addition, the User Manager enables administrators to provide users with access privileges based on their directory profiles (and substitute rights), as well as view and monitor requests.
Typically, end users can view other users and modify their own identity information. The users that a person can view and the identity information that someone can modify depends on the privileges granted by the Master Administrator.
Group Manager—Enables authorized personnel to create, manage and delete static, dynamic, or nested groups or to delegate group administration.
Administrators can create or delete groups, and enable users to subscribe or unsubscribe from groups.
End users can view groups and subscribe to membership in a group. The groups that a person can view, and subscription rights, are granted by a Master Administrator.
Organization Manager—Helps you manage system rules, access privileges, and workflows to manage ongoing changes for entire organizations.
Administrators can create and delete organizations and other objects (such as floor plans and assets) that do not belong in the User Manager or Group Manager.
End users can view organizational entities. The organizational entities that a person can view depend upon the rights granted by a Master Administrator.
Identity System Console—Provides Web-based administration and configuration that is used to create administrators and assign the right to delegate administrative tasks. Look for the following tabs in the Identity System Console to gain access to specific identity administration functions:
System Configuration Tab—Permits you to configure and manage the following functions:
Password Policy: For the Oracle Access Manager Identity System
Lost Password Policy: For Oracle Access Manager
Directory Profiles: Configure separate directory server profiles that each contain information for different parts of the DIT (for directory server partitioning).
Identity Servers: Display, add, remove, and modify Identity Server configurations, including audit and logging details
WebPass: Display, add, remove, and modify WebPass configurations
Server Settings: View and change various Identity Server configuration parameters, including: session timeout, email destinations, mail server settings, and URL prefix cache, and multi-language settings
Diagnostics: Select an Identity Server on which to run diagnostics to verify the state of the Identity Servers and their connectivity to the Directory Server.
Administrators: View and modify Master Administrators and Master Identity Administrators
Styles: Create and deploy a customized style for the user interface
Photos: Import custom photograph images for your User Manager User Profiles after assigning the Photo semantic type to any attribute in the gensiteorgperson object class.
User Manager Configuration Tab—Enables you to manage and customize Oracle Access Manager User Manager appearance and behavior, including tabs, reports, and auditing policies.
Group Manager Configuration Tab—Permits you to manage and customize Oracle Access Manager Group Manager appearance and behavior, and provides the following functions:
Tabs
Reports
Group types
Group Manager Options
Auditing policies
Group cache
Organization Manager Configuration Tab—Enables you to manage and customize Organization Manager appearance and behavior, including tabs, reports, and auditing policies.
Common Configuration Tab—Enables you to configure functionality common to Identity applications, including object classes, workflow panels, master audit policy, and global auditing policies.
System Management Tab—Eliminated in 10g (10.1.4.0.1). In earlier releases this tab provided the Diagnostics function, which now appears on the System Configuration tab.
Administrators access the Identity System Console by entering the following URL in a browser, where hostname refers to the machine that hosts the WebPass Web server; port refers to the HTTP port number of the WebPass Web server instance; /identity/oblix connects to the Identity System landing page:
http://hostname:port/identity/oblix
A WebPass is an Oracle Access Manager Web server plug-in that passes information back and forth between a Web server and the Identity Server. Depending upon its configuration, the Identity Server processes the request either as an XML or HTML file.
A WebPass can communicate with multiple Identity Servers. Each Web server instance that communicates with the Identity Server must be configured with a WebPass. In a Oracle Access Manager installation:
At least one WebPass must be installed on a Web server and configured to communicate with at least one Identity Server.
A WebPass is required on each machine hosting an Oracle Access Manager Policy Manager.
After installing an Identity Server and a WebPass, you must complete an initial Identity System setup process so the Identity Server and WebPass can communicate.
Process overview: WebPass functions
The WebPass receives the user request and maps the URL to a message format.
The WebPass forwards the request to an Identity Server.
The WebPass receives information from the Identity Server and returns it to the user's browser.
Various components and methods are provided to help you customize the Identity System. See also:
The Identity Event Plug-in API is a standard component installed with the Identity Server. It is a subset of the Oracle Access Manager Software Developer Kit (also known as the Access Manager SDK). The Identity Event Plug-in API enables you to extend base Identity System functionality by developing your own small applications (called actions) to perform custom business logic and integrate with external systems. The Identity System makes certain data available to the actions, which are then allowed to modify the data and influence the outcome of the event.
For example, when defining a workflow for user creation, you may want to call out to a Human Resources Management System, which in turn creates an account for a user. The new user ID can then be returned to the Identity System.
More information is provided in the Oracle Access Manager Developer Guide.
IdentityXML enables you to access Identity System functionality without a browser. Through IdentityXML, external applications can initiate remote procedure calls that pass arguments to the Identity System.
For example, an external application can initiate batch processing of new users in the Identity System without going through the Identity System browser interface. IdentityXML allows for cross-firewall integration without exposing the directory.
More information on IdentityXML is provided in the Oracle Access Manager Developer Guide.
Portal inserts are embeddable pieces of Oracle Access Manager Identity System functionality that are available as URLs. You can place a portal insert anywhere on your site or portal to insert content generated by the Identity System into other applications, without programming.
You can, for instance, use the Identity System's searching capabilities to add a company directory search feature to your site or embed a page from the Group Manager into your extranet portal. Users can access this functionality directly from the portal without viewing the standard Identity System interface.
More information about portal inserts is available in the Oracle Access Manager Customization Guide.
PresentationXML enables you to tailor the Identity System user interface. For example, you can:
Apply your organization's look and feel to the user pages, including color schemes, fonts, button images, and logos.
Add, modify, or remove functions on a page.
Create hidden information on a page for the Identity Event API to use.
Create new pages and functionality.
More information on PresentationXML is provided in the Oracle Access Manager Customization Guide.
Other chapters in this guide provide a more in depth look at other Oracle Access Manager components, applications, functions, features, behaviors, and terminology. For example:
Chapter 3, "About the Access System" includes the diagram of a simple Access System installation