2 Deploying the Connector
The procedure to deploy the connector can be divided into the following stages:
Note:
Some of the procedures described in this chapter are meant to be performed on the target system. The minimum permissions required to perform these procedures depends on the target system that you are using:-
If the target system is Microsoft Active Directory, then the permissions required are those assigned to members of the Domain Admins group.
-
If the target system is Microsoft ADAM, then the permissions required are those assigned to members of the Administrators group.
2.1 Preinstallation
Preinstallation information is divided across the following sections:
2.1.1 Preinstallation on Oracle Identity Manager
This section contains the following topics:
2.1.1.1 Files and Directories On the Installation Media
The contents of the connector installation media directory are described in Table 2-1.
Table 2-1 Files and Directories On the Installation Media
| File in the Installation Media Directory | Description |
|---|---|
|
configuration/ActiveDirectory-CI.xml |
This XML file contains configuration information that is used during the connector installation process. |
|
Files in the DataSets directory |
These XML files specify the information to be submitted by the requester during a request-based provisioning operation. Note: These files are specific to Oracle Identity Manager release prior to 11.1.2. |
|
lib/xliActiveDirectory.jar |
This JAR file contains the class files required for provisioning. During connector installation, this file is copied to the following location:
|
|
lib/xliADRecon.jar |
This JAR file contains the class files required for reconciliation. During connector installation, this file is copied to the following location:
|
|
Files in the resources directory |
Each of these resource bundles contains language-specific information that is used by the connector. During connector installation, these resource bundles are copied to the following location:
Note: A resource bundle is a file containing localized versions of the text strings that include GUI element labels and messages. |
|
scripts/ProvTerminalServiceAttr.vbs |
This VBScript file is used to set values for Terminal Services Profile fields of the target system during provisioning operations. This script is called by the Remote Manager. While performing the procedure described in "Installing the Remote Manager", you copy this file into a directory on the target system host computer. |
|
scripts/ReconTerminalServiceAttr.vbs |
This VBScript file is used to fetch values from Terminal Services Profile fields of the target system during reconciliation runs. This script is called by the Remote Manager. While performing the procedure described in "Installing the Remote Manager", you copy this file into a directory on the target system host computer. |
|
test/config/config.properties |
This file is used to set input test data for the connector testing utility. |
|
test/config/log.properties |
This file is used to set log messages that must be displayed on the console when you run the connector testing utility. |
|
test/lib/xlapiclient.ear |
This EAR file contains the JAR files required to run the testing utility for Oracle Identity Manager running on IBM WebSphere Application Server. |
|
test/scripts/runADTest.bat test/scripts/runADtest.sh |
These scripts are used to run the testing utility. |
|
test/scripts/wsapiclient.cmd |
This file is used by the testing utility if Oracle Identity Manager is running on IBM WebSphere Application Server. |
|
xml/ActiveDirectory-ConnectorConfig.xml |
This XML file contains definitions for the connector components. These components include the following:
|
Note:
The files in the test directory are used only to run tests on the connector by using the testing utility. The Diagnostic Dashboard is an alternative to the testing utility. Chapter 5, "Testing the Connector" describes both testing options.2.1.1.2 Determining the Release Number of the Connector
Note:
If you are using Oracle Identity Manager release 9.1.0.x, then the procedure described in this section is optional.If you are using Oracle Identity Manager release 11.1.1.x or 11.1.2.x, then skip this section.
You might have a deployment of an earlier release of the connector. While deploying the latest release, you might want to know the release number of the earlier release. To determine the release number of the connector that has already been deployed:
-
In a temporary directory, extract the contents of the following JAR file:
OIM_HOME/xellerate/JavaTasks/xliActiveDirectory.jar
-
Open the Manifest.mf file in a text editor. The Manifest.mf file is one of the files bundled inside the xliActiveDirectory.jar file.
In the Manifest.mf file, the release number of the connector is displayed as the value of the Version property.
2.1.2 Preinstallation on the Target System
Preinstallation on the target system involves performing the procedure described in the following section.
2.1.2.1 Creating a Target System User Account for Connector Operations
Oracle Identity Manager requires a target system user account to access the target system during reconciliation and provisioning operations. You provide the credentials of this user account while performing the procedure described in "Configuring the IT Resource for the Target System".
You can use a Microsoft Windows 2003 Server (Domain Controller) administrator account. Alternatively, you can create a user account and assign the minimum required rights to the user account.
Note:
If you want to enable the reconciliation of deleted target system records, then you must use an administrator account.To create the Microsoft Active Directory user account for connector operations:
See Also:
Microsoft Active Directory documentation for detailed information about performing this procedure-
Create a group (for example, OIMGroup) on the target system. While creating the group, select Security Group as the group type and as Global or Universal as the group scope.
-
Make this group a member of the Account Operators group.
-
Assign all read permissions to this group.
Note:
You assign read permissions on the Security tab of the Properties dialog box for the user account. This tab is displayed only in Advanced Features view. To switch to this view, select Advanced Features from the View menu on the Microsoft Active Directory console. -
Create a user (for example, OIMUser) on the target system.
-
Make the user a member of the group (for example, OIMGroup) created in Step 1.
To create the Microsoft ADAM user account for connector operations:
See Also:
Microsoft ADAM documentation for detailed information about these steps-
Create a user account in Microsoft ADAM.
-
Set a password for the user account.
-
Enable the user account by setting the msDS-UserAccountDisabled field to
false. -
Enter a value in the userPrincipalName field.
The value that you provide must be in the
user_name@domain_nameformat, for example,OIMuser@mydomain.com. -
Add the distinguished name of the user to the Administrators group.
2.2 Installation
Installation steps are divided across the following sections:
2.2.1 Installation on Oracle Identity Manager
Installation on Oracle Identity Manager consists of the following procedures:
2.2.1.1 Running the Connector Installer
Note:
In this guide, the term Connector Installer has been used to refer to the Connector Installer feature of the Administrative and User Console.To run the Connector Installer:
-
Copy the contents of the connector installation media directory into the following directory:
Note:
In an Oracle Identity Manager cluster, perform this step on each node of the cluster.-
For Oracle Identity Manager release 9.1.0.x: OIM_HOME/xellerate/ConnectorDefaultDirectory
-
For Oracle Identity Manager release 11.1.1 or 11.1.2.x: OIM_HOME/server/ConnectorDefaultDirectory
-
-
Depending on the Oracle Identity Manager release you are using, perform one of the following steps:
-
For Oracle Identity Manager release 9.1.0.x:
-
Log in to the Administrative and User Console by using the user account described in the "Creating the User Account for Installing Connectors" section of Oracle Fusion Middleware Administrator's Guide for Oracle Identity Manager.
-
Click Deployment Management, and then click Install Connector.
-
-
For Oracle Identity Manager release 11.1.1:
-
Log in to the Administrative and User Console by using the user account described in the "Creating the User Account for Installing Connectors" section of Oracle Fusion Middleware Administrator's Guide for Oracle Identity Manager.
-
On the Welcome to Identity Manager Advanced Administration page, in the System Management region, click Manage Connector.
-
In the Manage Connector page, click Install.
-
-
For Oracle Identity Manager release 11.1.2.x:
-
Log in to Oracle Identity System Administration by using the user account described in the "Creating the User Account for Installing Connectors" section of Oracle Fusion Middleware Administrator's Guide for Oracle Identity Manager.
-
In the left pane, under System Management, click Manage Connector.
-
In the Manage Connector page, click Install.
-
-
-
From the Connector List list, select ActiveDirectory RELEASE_NUMBER. This list displays the names and release numbers of connectors whose installation files you copy into the default connector installation directory in Step 1.
If you have copied the installation files into a different directory, then:
-
In the Alternative Directory field, enter the full path and name of that directory.
-
To repopulate the list of connectors in the Connector List list, click Refresh.
-
From the Connector List, select ActiveDirectory RELEASE_NUMBER.
-
-
Click Load.
-
To start the installation process, click Continue.
The following tasks are performed, in sequence:
-
Configuration of connector libraries
-
Import of the connector XML files (by using the Deployment Manager)
-
Compilation of adapters
On successful completion of a task, a check mark is displayed for the task. If a task fails, then an X mark and a message stating the reason for failure is displayed. Depending on the reason for the failure, make the required correction and then perform one of the following steps:
-
Retry the installation by clicking Retry.
-
Cancel the installation and begin again from Step 1.
-
-
If all three tasks of the connector installation process are successful, then a message indicating successful installation is displayed. In addition, a list of steps that you must perform after the installation is displayed. These steps are as follows:
-
Ensuring that the prerequisites for using the connector are addressed
Note:
At this stage, run the Oracle Identity Manager PurgeCache utility to load the server cache with content from the connector resource bundle in order to view the list of prerequisites. See "Clearing Content Related to Connector Resource Bundles from the Server Cache" for information about running the PurgeCache utility.There are no prerequisites for some predefined connectors.
-
Configuring the IT resource for the connector
Record the name of the IT resource displayed on this page. The procedure to configure the IT resource is described later in this guide.
-
Configuring the scheduled tasks
Record the names of the scheduled tasks displayed on this page. The procedure to configure these scheduled tasks is described later in this guide.
-
When you run the Connector Installer, it copies the connector files and external code files to destination directories on the Oracle Identity Manager host computer. These files are listed in Table 2-1.
Installing the Connector in an Oracle Identity Manager Cluster
Note:
If you are using Oracle Identity Manager release 11.1.1 or 11.1.2.x then skip this section as it is not applicable.While installing the connector in a Oracle Identity Manager cluster, you must copy all the JAR files and the contents of the resources directory into the destination directories on each node of the cluster. See the "Determining the Release Number of the Connector" section for information about the files that you must copy and their destination locations on the Oracle Identity Manager host computer.
2.2.1.2 Copying the ldapbp.jar File
The ldapbp.jar file is used by the connector to enable LDAP-based search of user records on the target system. You must download this file from the Sun Web site and copy it into the ThirdParty directory as follows:
-
Log on the Sun Web site at
-
Click Download JNDI 1.2.1 & More.
-
From the table on the page that is displayed, select and download the ldap-1_2_4.zip file.
-
Extract the contents of the ZIP file to a temporary location.
-
If you are using Oracle Identity Manager release 9.1.0.x, then copy the ldapbp.jar file from the temporary location to the OIM_HOME/xellerate/ThirdParty directory.
Note:
In an Oracle Identity Manager cluster, copy this JAR file into the ThirdParty directory on each node of the cluster. -
If you are using Oracle Identity Manager release 11.1.1 or 11.1.2.x, then:
Run the Upload JARs utility to post the ldapbp.jar file from the temporary location to the Oracle Identity Manager database. This utility is copied into the following location when you install Oracle Identity Manager:
Note:
Before you run this utility, verify that the WL_HOME environment variable is set to the directory in which Oracle WebLogic Server is installed.For Microsoft Windows:
OIM_HOME/server/bin/UploadJars.bat
For UNIX:
OIM_HOME/server/bin/UploadJars.sh
When you run the utility, you are prompted to enter the login credentials of the Oracle Identity Manager administrator, URL of the Oracle Identity Manager host computer, context factory value, type of JAR file being uploaded, and the location from which the JAR file is to be uploaded. To upload the ldapbp.jar file, specify
3as the value of the JAR type.See Also:
Oracle Fusion Middleware Developer's Guide for Oracle Identity Manager for detailed information about the Upload JARs utility
2.2.1.3 Configuring the IT Resource for the Target System
The IT resource for the target system is created during connector installation. This IT resource contains connection information about the target system. Oracle Identity Manager uses this information during reconciliation and provisioning.
You must specify values for the parameters of the ADITResource IT resource as follows:
-
Depending on the Oracle Identity Manager release you are using, perform one of the following steps:
-
For Oracle Identity Manager release 9.1.0.x:
-
Log in to the Administrative and User Console.
-
Expand Resource Management, and then click Manage IT Resource.
-
-
For Oracle Identity Manager release 11.1.1:
-
Log in to the Administrative and User Console.
-
On the Welcome to Oracle Identity Manager Self Service page, click Advanced in the upper-right corner of the page.
-
On the Welcome to Oracle Identity Manager Advanced Administration page, in the Configuration region, click Manage IT Resource.
-
-
For Oracle Identity Manager release 11.1.2.x:
-
Log in to Oracle Identity System Administration.
-
In the left pane, under Configuration, click IT Resource.
-
-
-
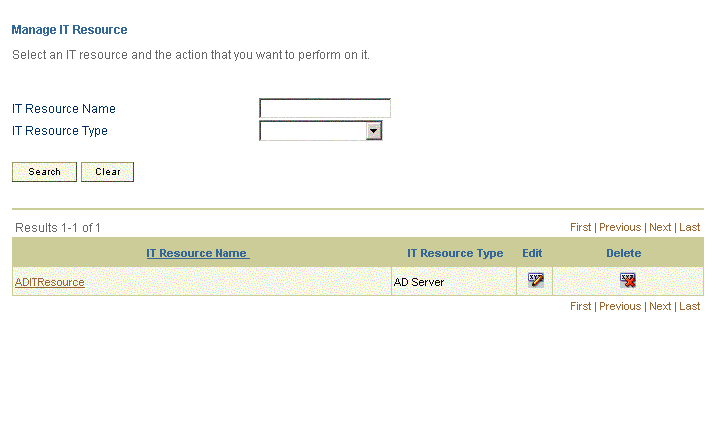
In the IT Resource Name field on the Manage IT Resource page, enter ADITResource and then click Search. Figure 2-1 shows the Manage IT Resource page.
-
Click the edit icon for the IT resource.
-
From the list at the top of the page, select Details and Parameters.
-
If you are using a Remote Manager to provision to or reconcile from the Terminal Services Profile fields, then select the name of the Remote Manager.
-
Specify values for the parameters of the IT resource. Figure 2-2 shows the Edit IT Resource Details and Parameters page.
Figure 2-2 Edit IT Resource Details and Parameters Page
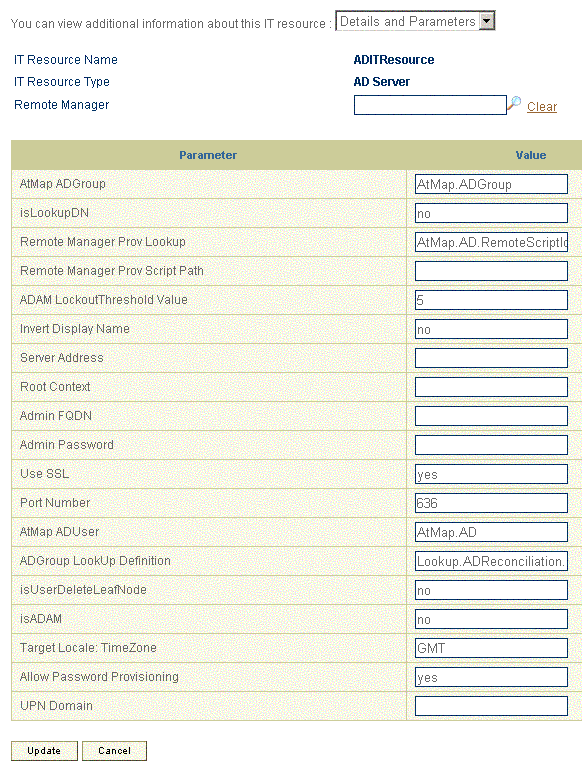
Description of ''Figure 2-2 Edit IT Resource Details and Parameters Page''
Table 2-2 describes each parameter of the IT resource.
Table 2-2 Parameters of the IT Resource for the Target System
Parameter Description ADAM Lockout Threshold Value
If the target system is Microsoft ADAM, then enter the number of unsuccessful login attempts after which a user's account must be locked.
If the target system is Microsoft Active Directory, then you need not enter a value. The value set in Microsoft Active Directory is automatically determined and used.
Default value:
5This parameter holds the name of the lookup definition in which the names of group fields are stored after group lookup synchronization.
Value:
Lookup.ADReconciliation.GroupLookupThis value is the same as that of the Lookup Code Name attribute of the AD Group Lookup Recon scheduled task, which is discussed in "Scheduled Tasks for Lookup Field Synchronization".
Note: You must not change the value of this parameter.
Admin FQDN
Enter the fully qualified domain name of the user account that you create by performing the procedure described in "Creating a Target System User Account for Connector Operations".
You can use any one of the following formats to enter the domain name:
-
user_login@domain.com -
cn=user_login,cn=Users,dc=domain,dc=com
Sample values:
john_doe@example.comcn=OIMadmin,cn=Users,dc=domain,dc=comAdmin Password
Enter the password of the user account that you create by performing the procedure described in "Creating a Target System User Account for Connector Operations".
AtMap ADUser
This parameter holds the name of the lookup definition for user field mappings between Oracle Identity Manager and the target system. This lookup definition is used during user provisioning operations.
The default value of this parameter is
AtMap.AD. Retain this value if the target system is Microsoft Active Directory.If you are using Microsoft ADAM, then change the value to
AtMap.ADAM.Enter the number of the port at which SSL is running on the target system host computer.
Sample values:
For Microsoft Active Directory:
-
636, if the Use SSL parameter is set to
yes -
389, if the Use SSL parameter is set to
no
For Microsoft ADAM:
-
50000, if the Use SSL parameter is set to
yes -
50001, if the Use SSL parameter is set to
no
The Use SSL parameter is described later in this table. This parameter is also mentioned in "Configuring SSL for Microsoft Active Directory".
This parameter holds the name of the lookup definition that stores Terminal Services Profile field mappings between Oracle Identity Manager and the target system.
Value:
AtMap.AD.RemoteScriptlookUpNote: You must not change the value of this parameter.
If you want to use Environment, Remote Control, or Sessions fields for provisioning operations, then see "Adding New Fields for Provisioning".
Enter the full path and name of the ProvTerminalServiceAttr.vbs script file on the target system host computer.
Sample value:
RM_HOME\scripts\ProvTerminalServiceAttr.vbsSee "Installing the Remote Manager" for more information.
Note:
-
Do not enter a value for this parameter if you do not want to use the Remote Manager.
-
This parameter is not used for Microsoft ADAM.
Root Context
Enter the base DN on which reconciliation of deleted user data and provisioning are to be carried out.
Sample values:
dc=example,dc=comNote: You must enter a value for this parameter.
Server Address
Enter the host name or IP address of the Microsoft Windows computer (target system host computer) on which Microsoft Active Directory is installed.
Sample values:
w2khost172.20.55.120Invert Display Name
Enter
yesif you want the Display Name field to be in the LAST_NAME FIRST_NAME format. Enter (or retain)noif you want the Display Name field to be in the FIRST_NAME LAST_NAME format.For example, if you enter
yes, then the Display Name field for user John Doe would showDoe John.Default value:
noNote:
-
This parameter is used only during provisioning operations.
-
If you want to set this parameter to
yes, then note that it works only with the ADITResource IT resource. It will not work if the IT resource for the target system has a different name. This point has also been mentioned under Bug 7212391 in the "Known Issues" chapter.
Use SSL
Enter
yesto specify that you will configure SSL between Oracle Identity Manager and the target system. Otherwise, enterno.Default value:
yesNote: It is recommended that you configure SSL to secure communication with the target system. You must configure SSL if you want to set or change user passwords during provisioning operations. Refer to "Configuring SSL for Microsoft Active Directory" for information about enabling SSL.
isADAM
Enter
yesto specify that the target system is Microsoft ADAM.Enter
noto specify that the target system is Microsoft Active Directory.isLookupDN
This parameter has been deprecated. Do not specify a value for this parameter. You will see this parameter only if you upgrade to the current release of the connector.
In Microsoft Active Directory, a user account can have other user accounts defined as its leaf nodes. Use the isUserDeleteLeafNode parameter to configure one of the following events to take place when a Delete User provisioning operation is carried out on a user account that has leaf nodes:
-
Enter
yesas the value of the parameter if you want the user account and its leaf nodes to be deleted on the target system. -
Enter
noas the value of the parameter if you want a message stating that the user account has leaf nodes to be displayed to the user performing the Delete User provisioning operation.
Default value:
noNote: This parameter is not used for Microsoft ADAM. You must not change the default value if the target system is Microsoft ADAM.
Allow Password Provisioning
Enter
yesas the value of this parameter if you want:-
Password changes on Oracle Identity Manager to be propagated to the target system. This applies to both trusted source and target resource modes.
-
Password changes for an OIM User to be propagated to all resources allocated (provisioned) to the OIM User.
Enter
noas the value of this parameter if you do not want password changes on Oracle Identity Manager to be propagated to the target system.AtMap ADGroup
Enter the name of the lookup definition that stores field mappings used for group provisioning:
For Microsoft Active Directory:
AtMap.ADGroupFor Microsoft ADAM:
AtMap.ADAMGroupUPN Domain
Enter the name of the domain in which you want to provision and reconcile users.
Sample value:
example.comOn the Administrative and User Console, the User ID field is prepopulated with the User Login value from the OIM User form. In addition, the User Principal Name field is prepopulated with the concatenated value of the User ID field and UPN Domain parameter value separated by the at sign (@). For example, if you enter
example.comas the value of the UPN Domain parameter and if the user ID isjdoe, then the User Principal Name field is prepopulated withjdoe@example.com.If required, you can change the User ID part of the User Principal Name field value during provisioning operations.
Target Locale: TimeZone
Enter the time zone of the target system. For example, enter
GMT-07:00if the target system is in Arizona in the United States.Backup Server URL
Enter a value for this parameter when both the following conditions are true:
-
You specify
trueas the value of the Connection pooling supported parameter, which is described later in this table. -
You want to configure high availability of the target system.
Enter the complete URL of the secondary target system installations to which Oracle Identity Manager must switch to if the primary target system installation becomes unavailable.
You must specify the complete URL in the following format:
ldap://SERVERADDRESS:PORT/
ldap://SERVERADDRESS1:PORT1/
Default Value:
[NONE]Sample value:
ldap://172.20.55.191:389/ ldap://172.20.55.171:387/Note: Multiple URLs must be separated by space.
LDAP Connection Timeout
Enter the timeout interval (in milliseconds) for which the connector must wait for a response from the target system before switching to one of the backup servers listed in the Backup Server URL parameter.Default Value:
3000Note: This parameter is used only if you specify a value for the Backup Server URL parameter.
Abandoned connection timeout
Enter the time (in seconds) after which a connection must be automatically closed if it is not returned to the pool.
Note: You must set this parameter to a value that is high enough to accommodate processes that take a long time to complete (for example, full reconciliation).
Default value:
600Connection pooling supported
Enter
trueif you want to enable connection pooling for this target system installation. Otherwise, enterfalse.Default value:
falseConnection wait timeout
Enter the maximum time (in seconds) for which the connector must wait for a connection to be available.
Default value:
60Inactive connection timeout
Enter the time (in seconds) of inactivity after which a connection must be dropped and replaced by a new connection in the pool.
Default value:
600Initial pool size
Enter the number of connections that must be established when the connection pool is initialized.
The pool is initialized when it receives the first connection request from a connector.
Default value:
1Sample value:
3Max pool size
Enter the maximum number of connections that must be established in the pool at any point of time
This number includes the connections that have been borrowed from the pool.
Default value:
30Sample value:
10Min pool size
Enter the minimum number of connections that must be in the pool at any point of time.
This number includes the connections that have been borrowed from the pool.
Default value:
2Sample value:
5Native connection pool class definition
This parameter holds the name of the wrapper to the native pool mechanism that implements the GenericPool.
Note: Do not specify a value for this parameter.
Pool excluded fields
This parameter holds a comma-separated list of IT parameters whose change must not trigger a refresh of the connector pool.
Value:
AtMap ADUser, Atmap ADOrg AtMap ADGroupNote:
Do not change the value of this parameter unless you are adding or deleting a parameter from the IT resource. You must ensure that the total length of the list does not exceed 2000 characters. If you are adding a parameter to the IT resource, then that parameter name must be added to the above list with a comma separator. If you are deleting a parameter from the IT resource, then that parameter must be removed from the list if it exists in the list.
You must restart Oracle Identity Manager for changes that you make to this parameter to take effect.
Pool preference
This parameter specifies the preferred connection pooling implementation.
Value:
DefaultNote: Do not change this value of this parameter.
ResourceConnection class definition
This parameter holds the name of the implementation of the ResourceConnection class.
Value:
com.thortech.xl.integration.ActiveDirectory.ADResourceConnectionImplNote: Do not change the value of this parameter.
Target supports only one connection
This parameter indicates whether the target system can support one or more connections at a time.
Value:
falseNote: Do not change the value of this parameter.
Timeout check interval
Enter the time interval (in seconds) at which the other timeouts specified by the other parameters must be checked
Default value:
30Validate connection on borrow
Specify whether or not a connection must be validated before it is lent by the pool.
The value can be
trueorfalse. It is recommended that you set the value totrue.Default value:
false -
2.2.2 Installation on the Target System
This section discusses the following topics:
2.2.2.1 Installing the Remote Manager
The Remote Manager enables you to include the Terminal Services Profile fields of the target system in reconciliation and provisioning operations.
Note:
-
Perform the procedure described in this section only if you want to include Terminal Services Profile fields in reconciliation and provisioning operations.
-
In this guide, the directory in which you install the Remote Manager is referred to as RM_HOME.
To install the Remote Manager:
-
The Remote Manager installation files are shipped along with the Oracle Identity Manager installation files. You can install the Remote Manager on any computer that is a part of the domain.
If you are using Oracle Identity Manager release 11.1.1 or 11.1.2.x, then see the Oracle Fusion Middleware Administrator's Guide for Oracle Identity Manager guide for instructions on installing the Remote Manager.
If you are using Oracle Identity Manager release 9.1.0.x, then depending on the application server that you use, perform the procedure to install the Remote Manager by following the instructions given in one of the following guides:
-
Oracle Identity Manager Installation and Configuration Guide for Oracle WebLogic Server
-
Oracle Identity Manager Installation and Configuration Guide for IBM WebSphere Application Server
-
Oracle Identity Manager Installation and Configuration Guide for JBoss Application Server
-
Oracle Identity Manager Installation and Configuration Guide for Oracle Application Server
-
-
If you are using Oracle Identity Manager release 9.1.0.x, then copy the following JAR files into the RM_HOME\xlremote\JavaTasks directory:
-
OIM_HOME\xellerate\lib\xlVO.jar
-
OIM_HOME\xellerate\lib\xlScheduler.jar
-
OIM_HOME\xellerate\lib\xlAPI.jar
-
OIM_HOME\xellerate\JavaTasks\xliActiveDirectory.jar
-
OIM_HOME\xellerate\ScheduleTask\xliADRecon.jar
-
-
If you are using Oracle Identity Manager release 11.1.1 or 11.1.2.x, then copy the following JAR files into the RM_HOME\xlremote\JavaTasks directory.
-
OIM_HOME\server\lib\xlVO.jar
-
OIM_HOME\server\lib\xlScheduler.jar
-
OIM_HOME\server\lib\xlAPI.jar
-
OIM_HOME\server\lib\xlUtils.jar
-
OIM_HOME\server\lib\xlRemoteManager.jar
-
INSTALL_MEDIA\lib\xliADRecon.jar
Note:
In this guide, the connector installation media is referred to as INSTALL_MEDIA.
-
-
Copy the ReconTerminalServiceAttr.vbs and ProvTerminalServiceAttr.vbs files from the INSTALL_MEDIA/scripts directory to any directory that you create inside the RM_HOME directory.
Note:
-
Ensure that the directory into which you copy the scripts has the required read and write permissions for the target system user account used by Oracle Identity Manager. This user account is described in "Creating a Target System User Account for Connector Operations".
-
Ensure that the RM_HOME directory is secured using Microsoft Windows best practices. Only the target system user account for Oracle Identity Manager must have permissions to access the RM_HOME directory.
-
-
Use the following script to start the Remote Manager:
For Oracle Identity Manager release 9.1.0.x:
RM_HOME\xlremote\remotemanager.batFor Oracle Identity Manager release 11.1.1 or 11.1.2.x:
RM_HOME\remote_manager\remotemanager.bat -
Note the Remote Manager service name and URL. These values are displayed in the Remote Manager command window. You will need these values while creating the IT resource for the Remote Manager.
If you are using Oracle Identity Manager release 9.1.0.x, then the default values for Remote Manager service name and URL are
RManagerandrmi://HOST_NAME:12346.If you are using Oracle Identity Manager release 11.1.1 or 11.1.2.x, then the default values for Remote Manager service name and URL are
RManagerandrmi://HOST_NAME:12345.For example, if you are using Oracle Identity Manager release 9.1.0.x, then for a Remote Manager running on ten.mydomain.com, the default values will be
RManagerandrmi://ten.mydomain.com:12346.
2.2.2.2 Enabling Logging in the Remote Manager
To enable logging in the Remote Manager:
-
Add the
log4j.logger.OIMCP.ADCS=LOG_LEVELline in one of the following files:-
For Oracle Identity Manager release 9.1.0.x:
RM_HOME\xlremote\config\log.properties
-
For Oracle Identity Manager release 11.1.1 or 11.1.2.x:
OIM_HOME\remote_manager\config\log.properties
-
-
In these lines, replace LOG_LEVEL with the log level that you want to set.
For example:
log4j.logger.OIMCP.ADCS=INFO
-
In the log.properties file, use the following parameter to specify the name and location of the file in which you want log information to be recorded:
log4j.appender.logfile.File
2.2.2.3 Enabling Client-Side Authentication for the Remote Manager
To enable client-side authentication for the Remote Manager:
-
Open one of the following files in a text editor:
-
For Oracle Identity Manager release 9.1.0.x:
RM_HOME/xlremote/config/xlconfig.xml
-
For Oracle Identity Manager release 11.1.1 or 11.1.2.x:
RM_HOME/remote_manager/config/xlconfig.xml
-
-
Set the ClientAuth property to
trueas follows:<ClientAuth>true</ClientAuth> -
If you are using Oracle Identity Manager release 9.1.0.x, then ensure that the RMIOverSSL property is set to
trueas follows:<RMIOverSSL>true</RMIOverSSL> -
Save and close the file.
-
If you are using Oracle Identity Manager release 9.1.0.x, then perform Steps 2 through 4 in the OIM_HOME/config/xlconfig.xml file.
2.3 Postinstallation
Postinstallation steps are divided across the following sections:
2.3.1 Postinstallation on Oracle Identity Manager
Configuring Oracle Identity Manager involves performing the following procedures:
Note:
In an Oracle Identity Manager cluster, you must perform these procedures on each node of the cluster.-
Clearing Content Related to Connector Resource Bundles from the Server Cache
-
Configuring Oracle Identity Manager for Request-Based Provisioning
2.3.1.1 Clearing Content Related to Connector Resource Bundles from the Server Cache
Note:
In an Oracle Identity Manager cluster, you must perform this step on each node of the cluster. Then, restart each node.When you deploy the connector, the resource bundles are copied from the resources directory on the installation media into the OIM_HOME/xellerate/connectorResources directory for Oracle Identity Manager release 9.1.0.x and Oracle Identity Manager database for Oracle Identity Manager releases 11.1.1 and 11.1.2.x. Whenever you add a new resource bundle to the connectorResources directory or make a change in an existing resource bundle, you must clear content related to connector resource bundles from the server cache.
To clear content related to connector resource bundles from the server cache:
-
In a command window, perform one of the following steps:
-
If you are using Oracle Identity Manager release 9.1.0.x, then switch to the OIM_HOME/xellerate/bin directory.
-
If you are using Oracle Identity Manager release 11.1.1 or 11.1.2.x, then switch to the OIM_HOME/server/bin directory.
Note:
You must perform Step 1 before you perform Step 2. An exception is thrown if you run the command described in Step 2 as follows:For Oracle Identity Manager release 9.1.0.x:
OIM_HOME/xellerate/bin/SCRIPT_FILE_NAME
For Oracle Identity Manager release 11.1.1 or 11.1.2.x:
OIM_HOME/server/bin/SCRIPT_FILE_NAME
-
-
Enter one of the following commands:
Note:
You can use the PurgeCache utility to purge the cache for any content category. RunPurgeCache.batCATEGORY_NAMEon Microsoft Windows orPurgeCache.shCATEGORY_NAMEon UNIX. TheCATEGORY_NAMEargument represents the name of the content category that must be purged.For example, the following commands purge Metadata entries from the server cache:
PurgeCache.bat MetaDataPurgeCache.sh MetaData-
For Oracle Identity Manager release 9.1.0.x:
On Microsoft Windows:
PurgeCache.bat ConnectorResourceBundleOn UNIX:
PurgeCache.sh ConnectorResourceBundleNote:
You can ignore the exception that is thrown when you perform Step 2. This exception is different from the one mentioned in Step 1.In this command,
ConnectorResourceBundleis one of the content categories that you can delete from the server cache. See the following file for information about the other content categories:OIM_HOME/xellerate/config/xlconfig.xml
-
For Oracle Identity Manager release 11.1.1 or 11.1.2.x:
On Microsoft Windows:
PurgeCache.bat AllOn UNIX:
PurgeCache.sh AllWhen prompted, enter the user name and password of an account belonging to the SYSTEM ADMINISTRATORS group. In addition, you are prompted to enter the service URL in the following format:
t3://OIM_HOST_NAME:OIM_PORT_NUMBER
In this format:
-
Replace
OIM_HOST_NAMEwith the host name or IP address of the Oracle Identity Manager host computer. -
Replace
OIM_PORT_NUMBERwith the port on which Oracle Identity Manager is listening.
-
See Oracle Fusion Middleware Administrator's Guide for Oracle Identity Manager for more information about the PurgeCache utility.
-
2.3.1.2 Enabling Logging
Depending on the Oracle Identity Manager release you are using, perform instructions in one of the following sections:
2.3.1.2.1 Enabling Logging in Oracle Identity Manager Release 9.1.0.x
Note:
In an Oracle Identity Manager cluster, perform this procedure on each node of the cluster. Then, restart each node.When you enable logging, Oracle Identity Manager automatically stores in a log file information about events that occur during the course of provisioning and reconciliation operations. To specify the type of event for which you want logging to take place, you can set the log level to one of the following:
-
ALLThis level enables logging for all events.
-
DEBUGThis level enables logging of information about fine-grained events that are useful for debugging.
-
INFOThis level enables logging of messages that highlight the progress of the application at a coarse-grained level.
-
WARNThis level enables logging of information about potentially harmful situations.
-
ERRORThis level enables logging of information about error events that might allow the application to continue running.
-
FATALThis level enables logging of information about very severe error events that could cause the application to stop functioning.
-
OFFThis level disables logging for all events.
The file in which you set the log level and the log file path depend on the application server that you use:
-
IBM WebSphere Application Server
To enable logging:
-
Add the following line in the OIM_HOME/xellerate/config/log.properties file:
log4j.logger.OIMCP.ADCS=LOG_LEVEL -
In these line, replace LOG_LEVEL with the log level that you want to set.
For example:
log4j.logger.OIMCP.ADCS=INFO
After you enable logging, log information is written to the following file:
WEBSPHERE_HOME/AppServer/logs/SERVER_NAME/SystemOut.log
-
-
JBoss Application Server
To enable logging:
-
In the JBOSS_HOME/server/default/conf/log4j.xml file, locate or add the following lines:
<category name="OIMCP.ADCS"> <priority value="LOG_LEVEL"/> </category> -
In the second XML code line of each set, replace LOG_LEVEL with the log level that you want to set. For example:
<category name="OIMCP.ADCS"> <priority value="INFO"/> </category>
After you enable logging, log information is written to the following file:
JBOSS_HOME/server/default/log/server.log
-
-
Oracle Application Server
To enable logging:
-
Add the following line in the OIM_HOME/xellerate/config/log.properties file:
log4j.logger.OIMCP.ADCS=LOG_LEVEL -
In this line, replace LOG_LEVEL with the log level that you want to set.
For example:
log4j.logger.OIMCP.ADCS=INFO
After you enable logging, log information is written to the following file:
ORACLE_HOME/opmn/logs/default_group~home~default_group~1.log
-
-
Oracle WebLogic Server
To enable logging in Oracle Identity Manager release 9.1.0.x:
-
Add the following line in the OIM_HOME/xellerate/config/log.properties file:
log4j.logger.OIMCP.ADCS=LOG_LEVEL -
In this line, replace LOG_LEVEL with the log level that you want to set.
For example:
log4j.logger.OIMCP.ADCS=INFO
After you enable logging, the log information is displayed on the server console.
-
2.3.1.2.2 Enabling Logging on Oracle Identity Manager Release 11.1.1 or 11.1.2.x
Oracle Identity Manager release 11.1.1 uses Oracle Java Diagnostic Logging (OJDL) for logging. OJDL is based on java.util.logger. To specify the type of event for which you want logging to take place, you can set the log level to one of the following:
-
SEVERE.intValue()+100
This level enables logging of information about fatal errors.
-
SEVERE
This level enables logging of information about errors that might allow Oracle Identity Manager to continue running.
-
WARNING
This level enables logging of information about potentially harmful situations.
-
INFO
This level enables logging of messages that highlight the progress of the application.
-
CONFIG
This level enables logging of information about fine-grained events that are useful for debugging.
-
FINE, FINER, FINEST
These levels enable logging of information about fine-grained events, where FINEST logs information about all events.
These log levels are mapped to ODL message type and level combinations as shown in Table 2-3.
Table 2-3 Log Levels and ODL Message Type:Level Combinations
| Log Level | ODL Message Type:Level |
|---|---|
|
SEVERE.intValue()+100 |
INCIDENT_ERROR:1 |
|
SEVERE |
ERROR:1 |
|
WARNING |
WARNING:1 |
|
INFO |
NOTIFICATION:1 |
|
CONFIG |
NOTIFICATION:16 |
|
FINE |
TRACE:1 |
|
FINER |
TRACE:16 |
|
FINEST |
TRACE:32 |
The configuration file for OJDL is logging.xml, which is located at the following path:
DOMAIN_HOME/config/fmwconfig/servers/OIM_SERVER/logging.xml
Here, DOMAIN_HOME and OIM_SERVER are the domain name and server name specified during the installation of Oracle Identity Manager.
To enable logging in Oracle WebLogic Server:
-
Edit the logging.xml file as follows:
-
Add the following blocks in the file:
<log_handler name='adcs-handler' level='[LOG_LEVEL]' class='oracle.core.ojdl.logging.ODLHandlerFactory'> <property name='logreader:' value='off'/> <property name='path' value='[FILE_NAME]'/> <property name='format' value='ODL-Text'/> <property name='useThreadName' value='true'/> <property name='locale' value='en'/> <property name='maxFileSize' value='5242880'/> <property name='maxLogSize' value='52428800'/> <property name='encoding' value='UTF-8'/> </log_handler>
<logger name="OIMCP.ADCS" level="[LOG_LEVEL]" useParentHandlers="false"> <handler name="adcs-handler"/> <handler name="console-handler"/> </logger> -
Replace both occurrences of
[LOG_LEVEL]with the ODL message type and level combination that you require. Table 2-3 lists the supported message type and level combinations.Similarly, replace
[FILE_NAME]with the full path and name of the log file in which you want log messages to be recorded.The following blocks show sample values for
[LOG_LEVEL]and[FILE_NAME]:<log_handler name='adcs-handler' level='NOTIFICATION:1' class='oracle.core.ojdl.logging.ODLHandlerFactory'> <property name='logreader:' value='off'/> <property name='path' value='F:\MyMachine\middleware\user_projects\domains\base_domain1\servers\oim_server1\logs\oim_server1-diagnostic-1.log'/> <property name='format' value='ODL-Text'/> <property name='useThreadName' value='true'/> <property name='locale' value='en'/> <property name='maxFileSize' value='5242880'/> <property name='maxLogSize' value='52428800'/> <property name='encoding' value='UTF-8'/> </log_handler> <logger name="OIMCP.ADCS" level="NOTIFICATION:1" useParentHandlers="false"> <handler name="adcs-handler"/> <handler name="console-handler"/> </logger>
With these sample values, when you use Oracle Identity Manager, all messages generated for this connector that are of a log level equal to or higher than the
NOTIFICATION:1level are recorded in the specified file. -
-
Save and close the file.
-
Set the following environment variable to redirect the server logs to a file:
For Microsoft Windows:
set WLS_REDIRECT_LOG=FILENAMEFor UNIX:
export WLS_REDIRECT_LOG=FILENAMEReplace FILENAME with the location and name of the file to which you want to redirect the output.
-
Restart the application server.
2.3.1.3 Configuring High Availability of the Target System
Suppose you have set up multiple, replicated installations of the target system for high availability. To ensure that if the primary target system installation becomes unavailable, then Oracle Identity Manager switches to one of the secondary target system installations, choose one of the following options:
Note:
You can confirm whether connection pooling is enabled by verifying the value of the Connection pooling supported parameter of the IT resource. See Table 2-2, "Parameters of the IT Resource for the Target System" for more information about the Connection pooling supported parameter.-
If connection pooling is enabled, then:
You must use the Backup Server URL parameter of the IT resource. See Section 2.2.1.3, "Configuring the IT Resource for the Target System" for more information about the Backup Server URL parameter.
-
If connection pooling is not enabled, then:
You must use the BackupServerURL parameter of the Lookup.AD.Configuration lookup definition. See Section 3.2.1, "Configuring the Lookup.AD.Configuration Lookup Definition" for information about configuring the Lookup.AD.Configuration lookup definition.
To configure backup servers, you must specify the complete URL in the following format:
Note:
Multiple URLs are separated by space.ldap://SERVERADDRESS:PORT/ ldap://SERVERADDRESS1:PORT1/
For example:
ldap://172.20.55.191:389/ ldap://172.20.55.171:387/
Note:
The preceding URLs must point to backup servers corresponding to the specified IT resource. If the primary IT resource is changed, then the value defined in theBackupServerURL parameter of the Lookup.AD.Configuration lookup definition or Backup Server URL IT resource parameter must be changed. The backup server functionality is not supported for cross-domain operations.2.3.1.4 Configuring Oracle Identity Manager for Request-Based Provisioning
Note:
Perform the procedure described in this section only if you are using Oracle Identity Manager release 9.1.0.x or 11.1.1.In request-based provisioning, an end user creates a request for a resource by using the Administrative and User Console. Administrators or other users can also create requests for a particular user. Requests for a particular resource on the resource can be viewed and approved by approvers designated in Oracle Identity Manager.
The following are features of request-based provisioning:
-
A user can be provisioned only one resource (account) on the target system.
Note:
Direct provisioning allows the provisioning of multiple Microsoft Active Directory accounts on the target system. -
Direct provisioning cannot be used if you enable request-based provisioning.
To configure request-based provisioning, perform the following procedures:
2.3.1.4.1 Copying Predefined Request Datasets
A request dataset is an XML file that specifies the information to be submitted by the requester during a provisioning operation. Predefined request datasets are shipped with this connector. These request datasets specify information about the default set of attributes for which the requester must submit information during a request-based provisioning operation. The following is the list of predefined request datasets available in the DataSets directory on the installation media:
-
ProvisionResourceAD User.xml
-
ModifyResourceAD User.xml
Copy these files from the installation media to any directory on the Oracle Identity Manager host computer. It is recommended that you create a directory structure as follows:
/custom/connector/RESOURCE_NAME
For example:
E:\MyDatasets\custom\connector\AD
Note:
Until you complete the procedure to configure request-based provisioning, ensure that there are no other files or directories inside the parent directory in which you create the directory structure. In the preceding example, ensure that there are no other files or directories inside the E:\MyDatasets directory.The directory structure to which you copy the dataset files is the MDS location into which these files are imported after you run the Oracle Identity Manager MDS Import utility. The procedure to import dataset files is described in the next section.
Depending on your requirement, you can modify the file names of the request datasets. In addition, you can modify the information in the request datasets. See Oracle Fusion Middleware Developer's Guide for Oracle Identity Manager for information on modifying request datasets.
2.3.1.4.2 Importing Request Datasets into MDS
All request datasets must be imported into the metadata store (MDS), which can be done by using the Oracle Identity Manager MDS Import utility.
To import a request dataset definition into MDS:
-
Ensure that you have set the environment for running the MDS Import utility. See Oracle Fusion Middleware Developer's Guide for Oracle Identity Manager for detailed information about setting up the environment for MDS utilities.
Note:
While setting up the properties in the weblogic.properties file, ensure that the value of the metadata_from_loc property is the parent directory of the /custom/connector/RESOURCE_NAME directory. For example, while performing the procedure in Section 2.3.1.4.1, "Copying Predefined Request Datasets," if you copy the files to the E:\MyDatasets\custom\connector\AD directory, then set the value of the metada_from_loc property toE:\MyDatasets. -
In a command window, change to the OIM_HOME\server\bin directory.
-
Run one of the following commands:
-
On Microsoft Windows
weblogicImportMetadata.bat
-
On UNIX
weblogicImportMetadata.sh
-
-
When prompted, enter the following values:
-
Please enter your username [weblogic]Enter the username used to log in to WebLogic server
Sample value:
WL_User -
Please enter your password [weblogic]Enter the password used to log in to WebLogic server
-
Please enter your server URL [t3://localhost:7001]Enter the URL of the application server in the following format:
t3://HOST_NAME_IP_ADDRESS:PORTIn this format, replace:
-
HOST_NAME_IP_ADDRESS with the host name or IP address of the computer on which Oracle Identity Manager is installed.
-
PORT with the port on which Oracle Identity Manager is listening.
-
The request dataset is imported into MDS at the following location:
/custom/connector/RESOURCE_NAME
-
2.3.1.4.3 Enabling the Auto Save Form Feature
To enable the Auto Save Form feature:
-
Log in to the Design Console.
-
Expand Process Management, and then double-click Process Definition.
-
Search for and open the AD User process definition.
-
Select the Auto Save Form check box.
-
Click the Save icon.
2.3.1.4.4 Running the PurgeCache Utility
Run the PurgeCache utility to clear content belonging to the Metadata category from the server cache. See Section 2.3.1.1, "Clearing Content Related to Connector Resource Bundles from the Server Cache" for instructions.
The procedure to configure request-based provisioning ends with this step.
2.3.1.5 Configuring Oracle Identity Manager 11.1.2 or Later
If you are using Oracle Identity Manager release 11.1.2 or later, you must create additional metadata such as UI form and an application instance. In addition, you must tag certain form fields, and run entitlement and catalog synchronization jobs. These procedures are described in the following sections:
2.3.1.5.1 Tagging Form Fields
To tag form fields:
-
Log in to the Design Console.
-
Expand Development Tools, and double-click Form Designer.
-
Search for and open the UD_ADUSRC process form.
-
Click Create New Version.
-
In the Label field, enter the version name. For example,
version#1. -
Click the Save icon.
-
Select the current version created in Step 4 from the Current Version list.
-
On the Properties tab, search for the Group Name field, and then add the Entitlement property and set its value to
true. -
Click the Save icon.
-
Click Make Version Active.
-
Repeat Steps 2 through 10 with the following differences:
-
While performing Step 2 of this procedure, search for and open the UD_ADUSER form.
-
While perform Step 8 of this procedure, add properties for the following fields:
-
Search for the AD Server field, and add the "ITResource = true" property.
-
Search for the User ID field, and add the "AccountName = true" property.
-
Search for the Object GUID field, and add the "AccountId = true" property.
-
-
2.3.1.5.2 Creating and Activating a Sandbox
Create and activate a sandbox as follows. For detailed instructions, see the "Managing Sandboxes" section in the Oracle Fusion Middleware Administrator's Guide for Oracle Identity Manager.
-
Log in to Oracle Identity System Administration.
-
In the upper right corner of the page, click the Sandboxes link.
The Manage Sandboxes page is displayed.
-
On the toolbar, click Create Sandbox.
-
In the Create Sandbox dialog box, enter values for the following fields:
-
Sandbox Name: Enter a name for the sandbox.
-
Sandbox Description: Enter a description of the sandbox.
-
-
Click Save and Close.
-
Click OK on the confirmation message that is displayed.
The sandbox is created and displayed in the Available Sandboxes section of the Manage Sandboxes page.
-
From the table showing the available sandboxes in the Manage Sandboxes page, select the newly created sandbox that you want to activate.
-
On the toolbar, click Activate Sandbox.
The sandbox is activated.
2.3.1.5.3 Creating a New UI Form
Create a new UI form as follows. For detailed instructions, see the "Managing Forms" chapter in the Oracle Fusion Middleware Administrator's Guide for Oracle Identity Manager.
-
In the left pane, under Configuration, click Form Designer. The Form Designer page is displayed.
-
From the Actions menu, select Create. Alternatively, click Create on the toolbar. The Create Form page is displayed.
-
On the Create Form page, enter values for the following UI fields:
-
Resource Type: Select the resource object that you want to associate the form with. For example, AD User.
-
Form Name: Enter a name for the form.
-
-
Click Create.
A message is displayed stating that the form is created.
2.3.1.5.4 Creating an Application Instance
Create an application instance as follows. For detailed instructions, see the "Managing Application Instances" chapter in the Oracle Fusion Middleware Administrator's Guide for Oracle Identity Manager.
-
In the left pane of the System Administration console, under Configuration, click Application Instances. The Application Instances page is displayed.
-
From the Actions menu, select Create. Alternatively, click Create on the toolbar. The Create Application Instance page is displayed.
-
Specify values for the following fields:
-
Name: The name of the application instance.
-
Display Name: The display name of the application instance.
-
Description: A description of the application instance.
-
Resource Object: The resource object name. Click the search icon next to this field to search for and select AD User.
-
IT Resource Instance: The IT resource instance name. Click the search icon next to this field to search for and select Active Directory.
-
Form: Select the form name (created in Section 2.3.1.5.3, "Creating a New UI Form").
-
-
Click Save. The application instance is created.
-
Publish the application instance to an organization to make the application instance available for requesting and subsequent provisioning to users. See the "Managing Organizations Associated With Application Instances" section in Oracle Fusion Middleware Administrator's Guide for Oracle Identity Manager for detailed instructions.
2.3.1.5.5 Publishing a Sandbox
To publish the sandbox that you created in Section 2.3.1.5.2, "Creating and Activating a Sandbox":
-
Close all the open tabs and pages.
-
In the upper right corner of the page, click the Sandboxes link.
The Manage Sandboxes page is displayed.
-
From the table showing the available sandboxes in the Manage Sandboxes page, select the sandbox that you created in Section 2.3.1.5.2, "Creating and Activating a Sandbox."
-
On the toolbar, click Publish Sandbox. A message is displayed asking for confirmation.
-
Click Yes to confirm. The sandbox is published and the customizations it contained are merged with the main line.
2.3.1.5.6 Harvesting Entitlements and Sync Catalog
To harvest entitlements and sync catalog:
-
Run the scheduled jobs for lookup field synchronization listed in Section 3.3, "Scheduled Tasks for Lookup Field Synchronization."
-
Run the Entitlement List scheduled job to populate Entitlement Assignment schema from child process form table. See the "Predefined Scheduled Tasks" section in the Oracle Fusion Middleware Administrator's Guide for Oracle Identity Manager for more information about this scheduled job.
-
Run the Catalog Synchronization Job scheduled job. See the "Predefined Scheduled Tasks" section in the Oracle Fusion Middleware Administrator's Guide for Oracle Identity Manager for more information about this scheduled job.
2.3.1.6 Localizing Field Labels in UI Forms
Note:
Perform the procedure described in this section only if you are using Oracle Identity Manager release 11.1.2.x and you want to localize UI form field labels.To localize field label that is added to the UI forms:
-
Log in to Oracle Enterprise Manager.
-
In the left pane, expand Application Deployments and then select oracle.iam.console.identity.sysadmin.ear.
-
In the right pane, from the Application Deployment list, select MDS Configuration.
-
On the MDS Configuration page, click Export and save the archive to the local computer.
-
Extract the contents of the archive, and open the following file in a text editor:
-
For Oracle Identity Manager 11g Release 2 PS2 (11.1.2.2.0):
SAVED_LOCATION\xliffBundles\oracle\iam\ui\runtime\BizEditorBundle_en.xlf
-
For releases prior to Oracle Identity Manager 11g Release 2 PS2 (11.1.2.2.0):
SAVED_LOCATION\xliffBundles\oracle\iam\ui\runtime\BizEditorBundle.xlf
-
-
Edit the BizEditorBundle.xlf file in the following manner:
-
Search for the following text:
<file source-language="en" original="/xliffBundles/oracle/iam/ui/runtime/BizEditorBundle.xlf" datatype="x-oracle-adf">
-
Replace with the following text:
<file source-language="en" target-language="LANG_CODE" original="/xliffBundles/oracle/iam/ui/runtime/BizEditorBundle.xlf" datatype="x-oracle-adf">In this text, replace LANG_CODE with the code of the language that you want to localize the form field labels. The following is a sample value for localizing the form field labels in Japanese:
<file source-language="en" target-language="ja" original="/xliffBundles/oracle/iam/ui/runtime/BizEditorBundle.xlf" datatype="x-oracle-adf">
-
Search for the application instance code. This procedure shows a sample edit for Active Directory application instance. The original code is:
<trans-unit id="${adfBundle['oracle.adf.businesseditor.model.util.BaseRuntimeResourceBundle']['persdef.sessiondef.oracle.iam.ui.runtime.form.model.user.entity.userEO.UD_ADUSER_FNAME__c_description']}"> <source>First Name</source> <target/> </trans-unit> <trans-unit id="sessiondef.oracle.iam.ui.runtime.form.model.ADForm.entity.ADFormEO.UD_ADUSER_FNAME__c_LABEL"> <source>First Name</source> <target/> </trans-unit> -
Open the resource file from the connector package, for example ActiveDirectory_ja.properties, and get the value of the attribute from the file, for example, global.udf.UD_ADUSER_FNAME=\u540D.
-
Replace the original code shown in Step 6.c with the following:
<trans-unit id="${adfBundle['oracle.adf.businesseditor.model.util.BaseRuntimeResourceBundle']['persdef.sessiondef.oracle.iam.ui.runtime.form.model.user.entity.userEO.UD_ADUSER_FNAME__c_description']}"> <source>First Name</source> <target>\u540D</target> </trans-unit> <trans-unit id="sessiondef.oracle.iam.ui.runtime.form.model.ADForm.entity.ADFormEO.UD_ADUSER_FNAME__c_LABEL"> <source>First Name</source> <target>\u540D</target> </trans-unit> -
Repeat Steps 6.a through 6.d for all attributes of the process form.
-
Save the file as BizEditorBundle_LANG_CODE.xlf. In this file name, replace LANG_CODE with the code of the language to which you are localizing.
Sample file name: BizEditorBundle_ja.xlf.
-
-
Repackage the ZIP file and import it into MDS.
See Also:
The "Deploying and Undeploying Customizations" chapter in the Oracle Fusion Middleware Developer's Guide for Oracle Identity Manager, for more information about exporting and importing metadata files -
Log out of and log in to Oracle Identity Manager.
2.3.2 Postinstallation on the Target System
Postinstallation on the target system consists of the following procedure.
2.3.2.1 Enabling or Disabling Password Policies in Microsoft Active Directory
In Microsoft Active Directory, the "Passwords must meet complexity requirements" policy setting is used to enable or disable password policies.
The procedure that you must perform depends on whether or not you want to achieve either or both of the following objectives:
-
Enable password policies
-
Configure SSL between Oracle Identity Manager and the target system
Note:
The procedure to configure SSL is discussed later in this guide.
Suppose there is a password policy on the target system for enforcing that the password field of user accounts is never left empty. At the same time, suppose you do not configure SSL. Under these conditions, the target system would reject provisioning operations that leave the password field empty. Therefore, you would not be able to perform such provisioning operations from Oracle Identity Manager. To enable provisioning operations under these conditions, you must disable password policies on the target system.
If you configure SSL and you want to enable both the default Microsoft Windows password policy and a custom password policy, then you must enable the "Passwords must meet complexity requirements" policy setting.
To enable or disable the "Passwords must meet complexity requirements" policy setting:
Note:
If you install Microsoft ADAM in a domain controller then it acquires all the policies of Microsoft Active Directory installed in the same domain controller. If you install Microsoft ADAM in a workgroup, then the local system policies are applied.-
On the Microsoft Windows computer hosting the target system, click the Start menu, Programs, Administrative Tools, and Domain Security Policy.
-
Select Security Settings, expand Account Policies, and then click Password Policy.
-
Double-click Passwords must meet complexity requirements.
-
In the Password Must Meet Complexity Requirements Properties dialog box, select Define this policy setting and then select:
-
Enabled, if you want to enable password policies
-
Disable, if you do not want to enable password policies
-
-
Click OK.
-
Restart the target system.
2.3.3 Configuring the Remote Manager
This section discusses the following topics:
-
Configuring Oracle Identity Manager Release 9.1.0.x to Trust the Remote Manager
-
Configuring Oracle Identity Manager Release 11.1.1 and 11.1.2.x to Trust the Remote Manager
2.3.3.1 Creating the IT Resource for the Remote Manager
Note:
-
The information in this section does not apply to Microsoft ADAM.
-
If the target system is Microsoft Active Directory, then perform this procedure only if you want to use the Terminal Services Profile fields of the target system during reconciliation and provisioning operations.
To create the IT resource for the Remote Manager:
-
Depending on the Oracle Identity Manager release you are using, perform one of the following steps:
-
For Oracle Identity Manager release 9.1.0.x:
-
Log in to the Administrative and User Console.
-
Expand Resource Management, and then click Create IT Resource.
-
-
For Oracle Identity Manager release 11.1.1:
-
Log in to the Administrative and User Console.
-
On the Welcome to Oracle Identity Manager Self Service page, click Advanced in the upper-right corner of the page.
-
On the Welcome to Oracle Identity Manager Advanced Administration page, in the Configuration region, click Create IT Resource.
-
-
For Oracle Identity Manager release 11.1.2.x:
-
Log in to Oracle Identity System Administration.
-
In the left pane, under Configuration, click IT Resource.
-
In the Manage IT Resource page, click Create IT Resource.
-
-
-
On the Step 1: Provide IT Resource Information page, perform the following steps:
-
IT Resource Name: Enter a name for the IT resource.
-
IT Resource Type: Select Remote Manager from the IT Resource Type list.
-
Remote Manager: Do not enter a value in this field.
-
-
Click Continue. Figure 2-3 shows the IT resource values added on the Create IT Resource page.
Figure 2-3 Step 1: Provide IT Resource Information
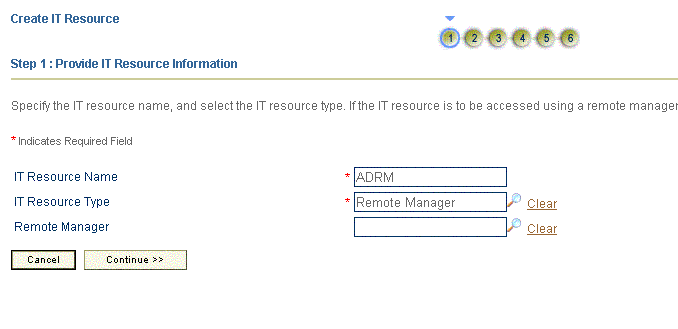
Description of ''Figure 2-3 Step 1: Provide IT Resource Information''
-
On the Step 2: Specify IT Resource Parameter Values page, specify values for the parameters of the IT resource and then click Continue. Figure 2-4 shows the Step 2: Specify IT Resource Parameter Values page.
Figure 2-4 Step 2: Specify IT Resource Parameter Values
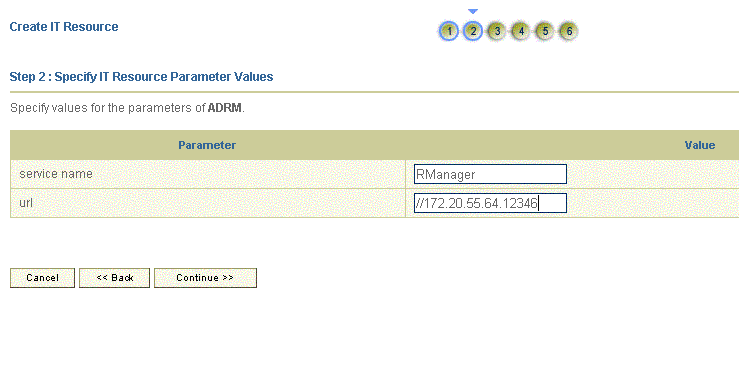
Description of ''Figure 2-4 Step 2: Specify IT Resource Parameter Values''
Table 2-4 provides information about the parameters of the IT resource.
Table 2-4 Parameters of the IT Resource for the Remote Manager
Parameter Description service name
Enter a name for the Remote Manager.
Sample value:
RManagerurl
Enter the IP address of the target system host computer and the port number at which the Remote Manager is listening.
Sample value:
rmi://10.0.0.1:12346 -
On the Step 3: Set Access Permission to IT Resource page, the
SYSTEM ADMINISTRATORSgroup is displayed by default in the list of groups that have Read, Write, and Delete permissions on the IT resource that you are creating.Note:
This step is optional.If you want to assign groups to the IT resource and set access permissions for the groups, then:
-
Click Assign Group.
-
For the groups that you want to assign to the IT resource, select Assign and the access permissions that you want to set. For example, if you want to assign the
ALL USERSgroup and set the Read and Write permissions to this group, then you must select the respective check boxes in the row, as well as the Assign check box, for this group. -
Click Assign.
-
-
On the Step 3: Set Access Permission to IT Resource page, if you want to modify the access permissions of groups assigned to the IT resource, then:
Note:
-
This step is optional.
-
You cannot modify the access permissions of the
SYSTEM ADMINISTRATORSgroup. You can modify the access permissions of only other groups that you assign to the IT resource.
-
Click Update Permissions.
-
Depending on whether you want to set or remove specific access permissions for groups displayed on this page, select or deselect the corresponding check boxes.
-
Click Update.
-
-
On the Step 3: Set Access Permission to IT Resource page, if you want to unassign a group from the IT resource, then:
Note:
-
This step is optional.
-
You cannot unassign the
SYSTEM ADMINISTRATORSgroup. You can unassign only other groups that you assign to the IT resource.
-
Select the Unassign check box for the group that you want to unassign.
-
Click Unassign.
-
-
Click Continue. Figure 2-5 shows the Step 3: Set Access Permission to IT Resource page.
Figure 2-5 Step 3: Set Access Permission to IT Resource
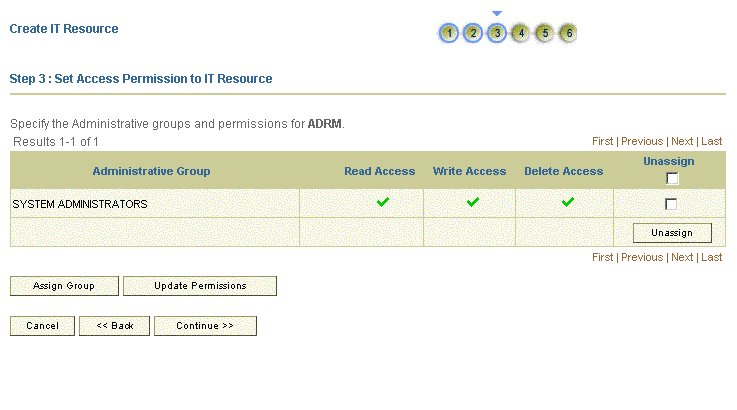
Description of ''Figure 2-5 Step 3: Set Access Permission to IT Resource''
-
On the Step 4: Verify IT Resource Details page, review the information that you provided on the first, second, and third pages. If you want to make changes in the data entered on any page, click Back to revisit the page and then make the required changes.
-
To proceed with the creation of the IT resource, click Continue. Figure 2-6 shows Step 4: Verify IT Resource Details page.
Figure 2-6 Step 4: Verify IT Resource Details
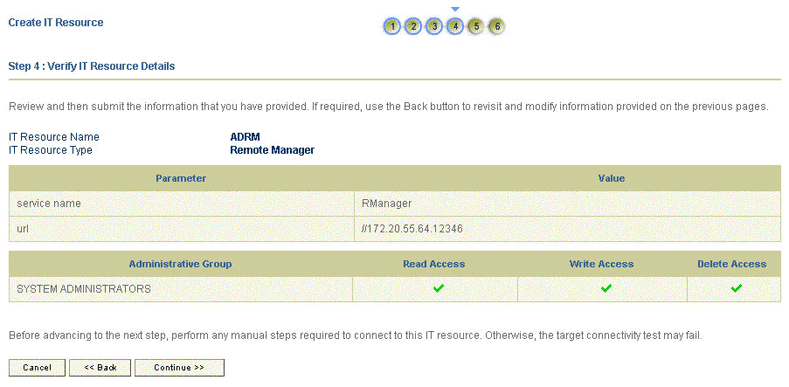
Description of ''Figure 2-6 Step 4: Verify IT Resource Details ''
-
The Step 5: IT Resource Connection Result page displays the results of a connectivity test that is run using the IT resource information. If the test is successful, then click Create. If the test fails, then you can perform one of the following steps:
-
Click Back to revisit the previous pages and then make corrections in the IT resource creation information.
-
Click Cancel to stop the procedure, and then begin from the first step onward.
-
Proceed with the creation process by clicking Create. You can fix the problem later, and then rerun the connectivity test by using the Diagnostic Dashboard.
Note:
If no errors are encountered, then the label of the button is Create, not Continue.Figure 2-7 shows the Step 5: Resource Connection Result page.
Figure 2-7 Step 5: IT Resource Connection Result
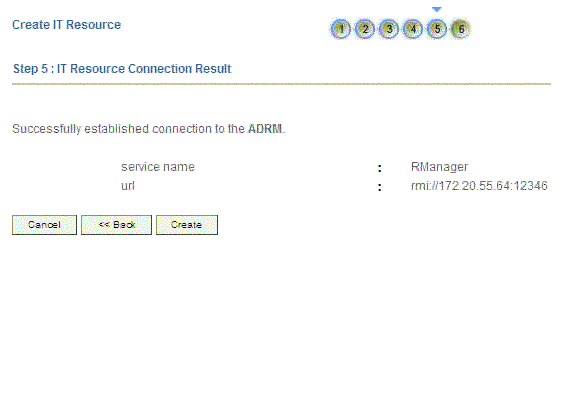
Description of ''Figure 2-7 Step 5: IT Resource Connection Result ''
-
-
Click Finish. Figure 2-8 shows the IT Resource Created Page
2.3.3.2 Configuring Oracle Identity Manager Release 9.1.0.x to Trust the Remote Manager
To configure Oracle Identity Manager to trust the Remote Manager:
-
From the computer hosting the Remote Manager, copy the RM_HOME/xlremote/config/xlserver.cert file to a temporary directory on the Oracle Identity Manager host computer.
Note:
The server certificate in the OIM_HOME directory is also named xlserver.cert. Ensure that you do not overwrite that certificate. -
To import the certificate by using the keytool utility, run the following command:
JAVA_HOME/jre/bin/keytool -import -alias ALIAS -file RM_CERT_LOCATION/xlserver.cert -keystore OIM_HOME/xellerate/config/.xlkeystore -storepass PASSWORD
In the preceding command, replace:
-
JAVA_HOMEwith the location of the Java directory for your application server. -
ALIASwith an alias for the certificate in the store. -
RM_CERT_LOCATIONwith the full path of the temporary directory where you copied the certificate. -
PASSWORDwith the password of the keystore.
-
-
Copy the OIM_HOME/xellerate/config/xlserver.cert file to a temporary directory on the Remote Manager host computer.
-
To import the certificate by using the keytool utility on the Remote Manager host computer, run the following command:
JAVA_HOME/jre/bin/keytool -import -alias ALIAS -file OIM_CERT_LOCATION/xlserver.cert -keystore RM_HOME/xlremote/config/.xlkeystore -storepass PASSWORD
In the preceding command, replace:
-
JAVA_HOMEwith the location of the Java directory for your application server. -
ALIASwith an alias for the certificate in the store. -
OIM_CERT_LOCATIONwith the full path of the temporary directory where you copied the certificate. -
PASSWORDwith the password of the keystore.Note:
It is recommended that you follow security best practices and change the default passwords used for the Remote Manager keystore. To change the Remote Manager keystore password, follow the instructions given in Oracle Identity Manager Installation and Configuration Guide for your application server.
-
2.3.3.3 Configuring Oracle Identity Manager Release 11.1.1 and 11.1.2.x to Trust the Remote Manager
To configure Oracle Identity Manager to trust the Remote Manager:
-
On the computer hosting Oracle Identity Manager, export the certificate by running the following command:
keytool -export -keystore KEYSTORE_FILE -storepass KEYSTORE_PASSWORD -alias ALIAS -file CERT_FILE_NAME
In this command:
-
KEYSTORE_FILE is the complete path and name of the keystore.
-
KEYSTORE_PASSWORD is the password of the keystore.
-
ALIAS is the alias of the certificate to be exported.
-
CERT_FILE_NAME is the file name containing the exported certificate
The following is a sample command:
keytool -export -keystore D:\March11g\Middleware\user_projects\domains\MARCHWIN\config\fmwconfig\default-keystore.jks -storepass MyPa55word -alias xell -file oim.cer
-
-
Copy the exported certificate to any directory on the target system.
-
To import the certificate, run the following command:
keytool -import -keystore KEYSTORE_FILE -storepass KEYSTORE_PASSWORD -alias ALIAS -file CERT_FILE_NAME
In this command:
-
KEYSTORE_FILE is the complete path and name of the keystore.
-
KEYSTORE_PASSWORD is the password of the keystore.
-
ALIAS is the alias of the certificate to be imported.
-
CERT_FILE_NAME is the file name containing the imported certificate
The following is a sample command:
keytool -import -keystore C:\Oracle\Middleware1\Oracle_IDM1\remote_manager\config\default-keystore.jks -storepass MyPa55word -alias oimserver -file C:\Oracle\Middleware1\OIMCert\oim.cer
-
-
Copy the OIM_HOME\server\config\xlserver.cert file from the Remote Manager host computer to a temporary directory on the Oracle Identity Manager host computer.
-
To import the certificate, run the following command:
keytool -import -keystore KEYSTORE_FILE -storepass KEYSTORE_PASSWORD -alias ALIAS -file CERT_FILE_NAME
In this command:
-
KEYSTORE_FILE is the complete path and name of the keystore.
-
KEYSTORE_PASSWORD is the password of the keystore.
-
ALIAS is the alias of the certificate to be imported.
-
CERT_FILE_NAME is the file name containing the imported certificate
The following is a sample command
keytool -import -keystore D:\March11g\Middleware\user_projects\domains\MARCHWIN\config\fmwconfig\default_keystore.jks -storepass Welcome1 -alias rmcert -file D:\March11g\Middleware\RMCert146\xlserver.cert
-
2.3.3.4 Verifying That the Remote Manager Is Running
To verify that the Remote Manager is running:
-
Use the following script to start the Remote Manager:
For Oracle Identity Manager release 9.1.0.x:
RM_HOME\xlremote\remotemanager.bat
For Oracle Identity Manager release 11.1.1 and 11.1.2.x:
OIM_HOME\remote_manager\remotemanager.bat
-
Log in to the Design Console.
-
Expand Administration, and double-click Remote Manager.
-
Search for and open the Remote Manager that you have created.
-
Click the Refresh icon. The screen displays details of the Remote Manager that you have configured. The "running" check box should be selected for the Remote Manager. This implies that the status of the Remote Manager is active.
2.3.4 Configuring SSL for Microsoft Active Directory
To configure SSL communication between Oracle Identity Manager and Microsoft Active Directory, you must perform the following tasks:
2.3.4.1 Installing Certificate Services
To install Certificate Services on the target system host computer:
Note:
Before you begin installing Certificate Services, you must ensure that Internet Information Services (IIS) is installed on the target system host computer.-
Insert the operating system installation media into the CD-ROM or DVD drive.
-
Click Start, Settings, and Control Panel.
-
Double-click Add/Remove Programs.
-
Click Add/Remove Windows Components.
-
Select Certificate Services.
-
In the Windows Components Wizard, follow the instructions to start Certificate Services.
Note:
While providing input to the wizard, select Enterprise root CA as the CA type. This is required for adding a policy with the Domain Controller template, which is a step that you perform in the next procedure.
2.3.4.2 Enabling LDAPS
The target system host computer must have LDAP over SSL (LDAPS) enabled. To enable LDAPS:
-
On the Active Directory Users and Computers console, right-click the domain node, and select Properties.
-
Click the Group Policy tab.
-
Select Default Domain Policy.
-
Click Edit.
-
Click Computer Configuration, Windows Settings, Security Settings, and Public Key Policies.
-
Right-click Automatic Certificate Request Settings, and then select New and Automatic Certificate Request. A wizard is started.
-
Use the wizard to add a policy with the Domain Controller template.
At the end of this procedure, the certificate is created and LDAPS is enabled on port 636. You can use an LDAP browser utility to verify that LDAPS is working.
Note:
While performing the procedure described in "Configuring the IT Resource for the Target System", you specify the port number as the value of the Port Number parameter.2.3.4.3 Setting Up the Target System Certificate As a Trusted Certificate
If the Microsoft Active Directory certificate is not issued or certified by a CA, then set it up as a trusted certificate. To do this, you first export the certificate and then import it into the keystore of the Oracle Identity Manager host computer as a trusted CA certificate.
To export the Microsoft Active Directory certificate:
-
Click Start, Programs, Administrative Tools, and Certification Authority.
-
Right-click the Certification Authority that you create, and then select Properties.
-
On the General tab, click View Certificate.
-
On the Details tab, click Copy To File.
-
Use the wizard to create a certificate (
.cer) file using base-64 encoding.
To import the target system certificate into the certificate store of the Oracle Identity Manager release 9.1.0.x host computer:
Note:
All application server releases supported by Oracle Identity Manager release 9.1.0.x are supported.In an Oracle Identity Manager cluster, you must perform this procedure on each node of the cluster.
-
Copy the target system certificate to the Oracle Identity Manager host computer.
-
Change to the directory where you copy the certificate file, and then enter a command similar to the following:
keytool -import -alias ALIAS -file CER_FILE -keystore MY_CACERTS -storepass PASSWORD
For example:
keytool -import -alias WS9102 -file D:\WebSphOIM\Server\Remote_cert\cert\919cert1.cer -keystore D:\Program Files\IBM\WebSphere\AppServer\java\jre\lib\security\cacerts -storepass xellerate
In this command:
-
ALIASis the alias for the certificate (for example, the server name). -
CER_FILEis the full path and name of the certificate (.cer) file.Table 2-5 shows the location of the certificate store for each of the supported application servers.
Table 2-5 Certificate Store Locations
Application Server Certificate Store Location Oracle WebLogic Server
-
If you are using Oracle jrockit_R27.3.1-jdk, then copy the certificate into the following directory:
JROCKIT_HOME/jre/lib/security/cacerts
-
If you are using the default Oracle WebLogic Server JDK, then copy the certificate into the following directory:
$JAVA_HOME/jre/lib/security/cacerts
IBM WebSphere Application Server
-
For a nonclustered configuration of any supported IBM WebSphere Application Server release, import the certificate into the following certificate store:
WEBSPHERE_HOME/java/jre/lib/security/cacerts
-
For IBM WebSphere Application Server 6.1.x, in addition to the
cacertscertificate store, you must import the certificate into the following certificate store:WEBSPHERE_HOME/AppServer/profiles/SERVER_NAME/config/cells/CELL_NAME/nodes/NODE_NAME/trust.p12
For example:
C:\Program Files\IBM\WebSphere\AppServer\profiles\AppSrv02\config\cells\wkslaurel3224Node02Cell\nodes\wkslaurel3224Node02\trust.p12
-
For IBM WebSphere Application Server 5.1.x, in addition to the
cacertscertificate store, you must import the certificate into the following certificate store:WEBSPHERE_HOME/etc/DummyServerTrustFile.jks
JBoss Application Server
JAVA_HOME/jre/lib/security/cacerts
Oracle Application Server
ORACLE_HOME/jdk/jre/lib/security/cacerts
-
-
-
To confirm whether or not the certificate has been imported successfully, enter a command similar to the following:
keytool -list -alias ALIAS -keystore MY_CACERTS -storepass PASSWORD
For example:
keytool -list -alias MyAlias -keystore C:\mydir\java\jre\lib\security\cacerts -storepass changeit
-
For a nonclustered configuration of IBM WebSphere Application Server, download the jsse.jar file from the Sun Web site and copy this file into the WEBSPHERE_HOME/java/jre/lib/ext directory.
-
For a clustered configuration of IBM WebSphere Application Server, download the jnet.jar, jsse.jar, and jcert.jar files from the Sun Web site and copy these files into the WEBSPHERE_HOME/java/jre/lib/ext directory.
To import the target system certificate into the certificate store of the Oracle Identity Manager release 11.1.1 host computer:
-
Copy the target system certificate to the Oracle Identity Manager host computer.
-
Import the target system certificate into the JDK used by Oracle Identity Manager by running the following command:
keytool -import -keystore MY_CACERTS -file CERT_FILE_NAME -storepass PASSWORD
In this command:
-
MY_CACERTS is the full path and name of the certificate store (the default is cacerts).
-
CERT_FILE_NAME is the full path and name of the certificate file.
-
PASSWORD is the password of the keystore.
The following is a sample command:
keytool -import -keystore /home/testoc4j/OIM/jrockit_160_14_R27.6.5-32/jre/lib/security/cacerts -file /home/testoc4j/OIM/globalv.crt -storepass changeit
-
-
Import the target system certificate into WebLogic keystore by running the following command:
keytool -import -keystore WEBLOGIC_HOME/server/lib/DemoTrust.jks -file CERT_FILE_NAME -storepass PASSWORD
In this command:
-
CERT_FILE_NAME is the full path and name of the certificate file.
-
PASSWORD is the password of the keystore.
The following is a sample command:
keytool -import -keystore WEBLOGIC_HOME/server/lib/DemoTrust.jks -file /home/testoc4j/OIM/globalv.crt -storepass DemoTrustKeyStorePassPhrase -
2.3.5 Configuring SSL for Microsoft ADAM
To configure SSL communication between Oracle Identity Manager and Microsoft ADAM, you must perform the following tasks:
2.3.5.1 Generating the Certificate in Microsoft ADAM
Note:
Before you begin generating the certificate, you must ensure that Internet Information Services (IIS) is installed on the target system host computer.To generate the certificate in Microsoft ADAM, perform the following procedures:
2.3.5.1.1 Submitting a Request for the Certificate
To submit a request for the certificate:
-
On the target system host computer, open Internet Information Services (IIS) Manager.
You can use one of the following methods to open Internet Information Services (IIS) Manager:
-
Use the following URL:
http://localhost/certsrv -
Open Control Panel, double-click Administrative Tools, and then double-click IIS Service.
-
-
Expand Web Sites, and then expand Default Web Site.
-
Right-click CertSrv, and then select Browse.
-
Click Request a certificate.
-
Click Advanced certificate request.
-
Click Create and submit a request to this CA.
-
On the Advanced Certificate Request page, perform the following actions:
Note:
There are instructions for only some of the fields on this page. For the remaining fields, you can enter values according to your requirements.-
In the Name field, enter the fully qualified domain name (FQDN) of the target system host computer. For example, enter
hk128.corp.example.com.Note:
On your target system installation, if a value is already selected in this field, then you need not change it.You need not enter values in the remaining fields of the Identifying Information region.
-
Select Store certificate in local computer certificate store.
-
Select PCKS10 as the format.
-
In the Friendly name field, enter the FQDN of the target system host computer. For example, enter
hk128.corp.example.com.
-
-
Click Submit.
-
When a message asking you to confirm that you want to request a certificate is displayed, click Yes.
2.3.5.1.2 Issuing the Certificate
To issue the certificate:
-
On the target system host computer, open Control Panel.
-
Double-click Administrative Tools, and then double-click Certification Authority.
-
In the Certification Authority window, expand Administrator and then open Pending Requests.
The request that you created earlier is displayed on the right pane.
-
Right-click the request, select All Tasks, and then select Issue.
-
Open the Issued Certificates folder.
The certificate is displayed on the right pane.
-
Open Internet Information Services (IIS) Manager.
-
Expand Web Sites, and then expand Default Web Site.
-
Right-click CertSrv, and then select Browse.
-
Click View the status of pending certificate request.
-
Click the link for the certificate request.
-
Click Install this certificate.
-
When a message asking you to confirm that you want to add the certificate is displayed, click Yes.
A message saying that the certificate has been successfully installed is displayed.
2.3.5.1.3 Adding the Certificate to the Personal Store of the Microsoft ADAM Service
To add the certificate to the personal store of the Microsoft ADAM service:
-
On the target system host computer, use the Run dialog box to run the command for opening the Microsoft Management Console:
mmc -
On the Microsoft Management Console, click File and then select Add/Remove Snap-in.
-
On the Standalone tab of the Add/Remove Snap-in dialog box, click Add.
-
From the list of snap-ins, select Certificates and then click Add.
-
In the Certificates snap-in dialog box, select Service account.
-
In the Select Computer dialog box, select Local computer and then click Next.
-
From the Service account list in the Certificates snap-in dialog box, select the Microsoft ADAM service instance and then click Finish.
-
In the Certificates snap-in dialog box, select My user account and then click Finish.
-
In the Certificates snap-in dialog box, select Computer account and then click Next.
-
In the Select Computer dialog box, select Local computer and then click Finish.
-
Click Close, and then click OK.
-
In the Microsoft Management Console window, expand Certificates - Local Computer, expand Personal, and then open Certificates.
-
Right-click the certificate that you have added and copy it.
The name of this certificate is the FQDN of the host computer.
-
Paste the certificate into the following folders:
-
Personal folder under the Certificates - Service (ADAM_INSTANCE_NAME) on Local Computer folder
-
Personal folder under the Certificates - Current User folder
-
-
To save the changes that you have made to the Microsoft Management Console, click File and then select Save.
2.3.5.1.4 Assigning Permissions to the Certificate Key
To assign the required permissions to the folder containing the certificate key:
-
In Microsoft Windows Explorer, navigate to the MachineKeys folder. The path to this folder is similar to the following:
C:\Documents and Settings\All Users\Application Data\Microsoft\Crypto\RSA\MachineKeys
-
Right-click the MachineKeys folder, and then select Properties.
-
Use the Add button to add the following groups and users:
-
Administrators
-
Everyone
-
NETWORK SERVICE
-
The user name of the account used to install Microsoft ADAM
-
SYSTEM
-
-
From the Permissions list, select Full Control.
-
Click Apply, and then click OK.
-
In Microsoft Windows Explorer, expand the MachineKeys folder and select the certificate key. The time stamp for this certificate key is the date and time at which you created the certificate.
Note:
Refresh the folder if the certificate key that you created is not displayed. -
Right-click the key, and select Properties.
-
Use the Add button to add the following groups and users:
-
Administrators
-
Everyone
-
NETWORK SERVICE
-
The user name of the account used to install Microsoft ADAM
-
SYSTEM
-
-
From the Permissions list, select Full Control.
-
Click Apply, and then click OK.
2.3.5.1.5 Restarting the Microsoft ADAM Instance
To restart the Microsoft ADAM instance:
-
Open Control Panel.
-
Double-click Administrative Tools, and then select Services.
-
In the Services window, right-click the Microsoft ADAM instance and then select Restart.
2.3.5.1.6 Testing the Certificate
To test the certificate:
-
To open the ADAM Tools Command Prompt window on the target system host computer, click Start, Programs, ADAM, and ADAM Tools Command Prompt.
-
In the ADAM Tools Command Prompt window, enter
ldpand then press Enter. -
From the Connection menu of the LDAPS dialog box, select Connect.
-
In the Connect dialog box:
-
In the Server field, enter the FQDN of the target system host computer.
-
In the Port field, enter the SSL port number.
-
Select SSL.
-
-
Click OK.
-
If SSL has been successfully configured, then status messages about the connection are displayed on the right pane of the LDAPS window.
2.3.5.2 Setting Up the Target System Certificate As a Trusted Certificate
If the Microsoft ADAM certificate is not issued or certified by a CA, then set it up as a trusted certificate. To do this, you first export the certificate and then import it into the keystore of the Oracle Identity Manager host computer as a trusted CA certificate.
To export the Microsoft ADAM certificate:
-
Open the Microsoft Management Console.
-
In the Microsoft Management Console window, expand Certificates - Local Computer, expand Personal, and then open Certificates.
-
Right-click the certificate, select All Tasks, and then select Export.
-
Use the wizard to create a certificate (.cer) file using base-64 encoding.
To import the target system certificate into the certificate store of the Oracle Identity Manager release 9.1.0.x host computer:
Note:
All application server releases supported by Oracle Identity Manager release 9.1.0.x are supported.In an Oracle Identity Manager cluster, you must perform this procedure on each node of the cluster.
-
Copy the target system certificate to the Oracle Identity Manager host computer.
-
Change to the directory where you copy the certificate file, and then enter a command similar to the following:
keytool -import -alias ALIAS -file CER_FILE -keystore MY_CACERTS -storepass PASSWORD
In this command:
-
ALIASis the alias for the certificate (for example, the server name). -
CER_FILEis the full path and name of the certificate (.cer) file.Table 2-6 shows the location of the certificate store for each of the supported application servers.
Table 2-6 Certificate Store Locations
Application Server Certificate Store Location Oracle WebLogic Server
-
If you are using Oracle jrockit_R27.3.1-jdk, then copy the certificate into the following directory:
JROCKIT_HOME/jre/lib/security
-
If you are using the default Oracle WebLogic Server JDK, then copy the certificate into the following directory:
WEBLOGIC_HOME/java/jre/lib/security/cacerts
IBM WebSphere Application Server
-
For a nonclustered configuration of any supported IBM WebSphere Application Server release, import the certificate into the following certificate store:
WEBSPHERE_HOME/java/jre/lib/security/cacerts
-
For IBM WebSphere Application Server 6.1.x, in addition to the
cacertscertificate store, you must import the certificate into the following certificate store:WEBSPHERE_HOME/AppServer/profiles/SERVER_NAME/config/cells/CELL_NAME/nodes/NODE_NAME/trust.p12
For example:
C:\Program Files\IBM\WebSphere\AppServer\profiles\AppSrv02\config\cells\wkslaurel3224Node02Cell\nodes\wkslaurel3224Node02\trust.p12
-
For IBM WebSphere Application Server 5.1.x, in addition to the
cacertscertificate store, you must import the certificate into the following certificate store:WEBSPHERE_HOME/etc/DummyServerTrustFile.jks
JBoss Application Server
JAVA_HOME/jre/lib/security/cacerts
Oracle Application Server
ORACLE_HOME/jdk/jre/lib/security/cacerts
-
-
-
To confirm whether the certificate has been imported successfully, enter a command similar to the following:
keytool -list -alias ALIAS -keystore MY_CACERTS -storepass PASSWORD
For example:
keytool -list -alias MyAlias -keystore C:\mydir\java\jre\lib\security\cacerts -storepass changeit
-
For a nonclustered configuration of IBM WebSphere Application Server, download the jsse.jar file from the Sun Web site and copy this file into the WEBSPHERE_HOME/java/jre/lib/ext directory.
-
For a clustered configuration of IBM WebSphere Application Server, download the jnet.jar, jsse.jar, and jcert.jar files from the Sun Web site and copy these files into the WEBSPHERE_HOME/java/jre/lib/ext directory.
To import the target system certificate into the certificate store of the Oracle Identity Manager release 11.1.1 and 11.1.2.x host computer:
See the "To import the target system certificate into the certificate store of the Oracle Identity Manager release 11.1.1 host computer:" section for the procedure.