1 About the Connector
Oracle Identity Manager automates access rights management, security, and provisioning of IT resources. Oracle Identity Manager connectors are used to integrate Oracle Identity Manager with external, identity-aware applications. This guide discusses the connector that enables you to use Microsoft Active Directory or Microsoft Active Directory Application Mode (ADAM) either as a managed (target) resource or as an authoritative (trusted) source of identity data for Oracle Identity Manager.
Note:
At some places in this guide, Microsoft Active Directory and Microsoft ADAM have been referred to as the target systems.In the account management (target resource) mode of the connector, information about users created or modified directly on the target system can be reconciled into Oracle Identity Manager. In addition, you can use Oracle Identity Manager to perform provisioning operations on the target system.
In the identity reconciliation (trusted source) configuration of the connector, users are created or modified only on the target system and information about these users is reconciled into Oracle Identity Manager.
Note:
It is recommended that you do not configure the target system as both an authoritative (trusted) source and a managed (target) resource.This chapter contains the following sections:
1.1 Certified Components
The target system can be Microsoft Active Directory or Microsoft ADAM. Table 1-1 lists the certified components for both target systems.
Table 1-1 Certified Components
| Item | Requirement for Microsoft Active Directory | Requirement for Microsoft ADAM |
|---|---|---|
|
You can use one of the following releases of Oracle Identity Manager:
|
You can use one of the following releases of Oracle Identity Manager:
|
|
|
The target system can be any one of the following:
|
Microsoft Windows Server 2003 Active Directory Application Mode with SP1 installed on Microsoft Windows Server 2003 with SP1 or later service packs Note: On a Microsoft Windows 2003 server on which SP1 has not been installed, you might come across the "WILL_NOT_PERFORM" error message during the password change operation. You can access information about one of the causes of and a solution for this error on the Microsoft Knowledge Base Web site at |
|
|
JDK |
The JDK version can be one of the following:
|
The JDK version can be one of the following:
|
|
Other software |
Certificate Services |
Certificate Services |
1.2 Usage Recommendation
Depending on the Oracle Identity Manager version that you are using, you must deploy and use one of the following connectors:
-
If you are using an Oracle Identity Manager release that is later than release 9.1.0.1 and earlier than Oracle Identity Manager 11g Release 1 (11.1.1.5.6), then you must use the 9.1.1.x version of this connector.
-
If you are using Oracle Identity Manager 11g Release 1 (11.1.1.5.6) or later, or Oracle Identity Manager 11g Release 2 (11.1.2.0.6) or later, then use the 11.1.1.x version of this connector. However, if you are using Microsoft Exchange 2003, then you must use the 9.1.1.x versions for both Microsoft Active Directory User Management and Microsoft Exchange connectors.
-
If you are using Oracle Identity Manager 11g Release 2 (11.1.2.0.4) or later, then you must perform the steps mentioned in MetaLink note 1535369.1 to ensure the connector works as expected.
-
If you are using the Microsoft Exchange 9.1.x connector, then you must use the Microsoft Active Directory 9.1.x connector, and if you are using the Microsoft Exchange 11.1.1.x connector, then you must use the Microsoft Active Directory 11.1.1.x connector.
1.3 Certified Languages
The connector supports the following languages:
-
Arabic
-
Chinese (Simplified)
-
Chinese (Traditional)
-
Danish
-
English
-
French
-
German
-
Italian
-
Japanese
-
Korean
-
Portuguese (Brazilian)
-
Spanish
See Also:
For information about supported special characters supported by Oracle Identity Manager, see one of the following guides:-
For Oracle Identity Manager release 9.1.0.x:
Oracle Fusion Middleware Developer's Guide for Oracle Identity Manager
-
For Oracle Identity Manager release 11.1.1 or 11.1.2.x:
Oracle Fusion Middleware Developer's Guide for Oracle Identity Manager
1.4 Features of the Connector
This section discusses the following topics:
-
The "Connector Architecture" section describes the architecture of the connector.
-
The following sections describe features of the target resource mode:
-
The "Trusted Source Reconciliation" section describes features of the trusted source mode.
1.4.1 Connector Architecture
This section discusses the following topics:
1.4.1.1 Architecture of the Connector for Microsoft Active Directory
Figure 1-1 shows the architecture of the connector for Microsoft Active Directory.
Figure 1-1 Architecture of the Connector for Microsoft Active Directory
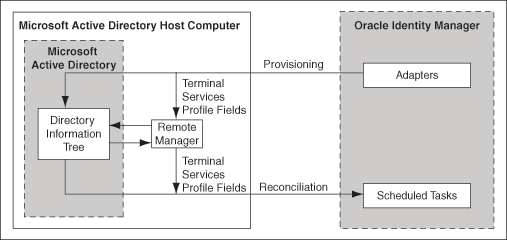
Description of ''Figure 1-1 Architecture of the Connector for Microsoft Active Directory''
The connector can be configured to run in one of the following modes:
Note:
In Oracle Identity Manager releases 11.1.1.x and 11.1.2.x, a scheduled job is an instance of a scheduled task. In this guide, the term scheduled task used in the context of Oracle Identity Manager release 9.1.0.x is the same as the term scheduled job in the context of Oracle Identity Manager releases 11.1.1.x and 11.1.2.x.See Oracle Fusion Middleware Administrator's Guide for Oracle Identity Manager for more information about scheduled tasks and scheduled jobs.
-
Identity reconciliation is also known as authoritative or trusted source reconciliation. In this form of reconciliation, OIM Users are created or updated corresponding to the creation of and updates to users on the target system. The identity reconciliation mode also supports reconciliation of organizations (OUs) created on the target system.
In the identity reconciliation mode, depending on the data that you want to reconcile, you use different scheduled tasks. For example, you use the AD User Trusted Recon scheduled task to reconcile user data from the target system. See Section 3.4.4, "Reconciliation Scheduled Tasks" for more information about scheduled tasks used in this mode.
-
Account management is also known as target resource management. This mode of the connector enables the following operations:
-
Provisioning involves creating or updating users on the target system through Oracle Identity Manager. When you allocate (or provision) a Microsoft Active Directory resource to an OIM User, the operation results in the creation of an account on Microsoft Active Directory for that user. In the Oracle Identity Manager context, the term "provisioning" is also used to mean updates made to the target system account through Oracle Identity Manager.
Users and organizations are organized in hierarchical format on the target system. Before you can provision users to (that is, create users in) the required organizational units (OUs) on the target system, you must fetch into Oracle Identity Manager the list of OUs used on the target system. This is achieved by using a lookup synchronization scheduled task.
The connector enables group assignment provisioning operations in which you set or change the target system group membership profiles of users. The connector also supports provisioning (updating) of the Windows Terminal Services Profile attributes. Accessing these attributes involves the use of components that are native to the Microsoft Windows platform. The connector uses a Remote Manager to update the Terminal Services Profile fields.
-
Target resource reconciliation
To perform target resource reconciliation, the AD User Target Recon scheduled task is used. The connector applies filters to locate users to be reconciled from the target system and then fetches the attribute values of these users. The Remote Manager used to enable propagation of Terminal Services Profile field values during provisioning is also used to enable the connector to fetch values from these fields during reconciliation.
Depending on the data that you want to reconcile, you use different scheduled tasks. For example, you use the AD User Target Recon scheduled task to reconcile user data in the target resource mode. See Section 3.4.4, "Reconciliation Scheduled Tasks" for more information about scheduled tasks used in this mode
-
This connector cannot propagate password changes from Microsoft Active Directory to Oracle Identity Manager. To implement this feature, you must install the Microsoft Active Directory password synchronization connector. See Oracle Identity Manager Connector Guide for Microsoft Active Directory Password Synchronization for more information. That guide describes scenarios in which both the password synchronization connector and this connector are deployed.
Other Major Features of the Connector
The following are other major features of the connector:
-
The connector supports reconciliation and provisioning operations across domains. This means that, for example, you can assign a user in one domain to a group in another domain. You can also reconcile a user record even if the user and the user's manager belong to different domains. See "Enabling Reconciliation and Provisioning Operations Across Multiple Domains" for more information.
-
The connector is compatible with high-availability target system environments. You can store information about backup target system hosts in an Oracle Identity Manager lookup definition. If the connector is unable to connect to the primary host, then it tries to connect to one of the hosts listed in the lookup definition.
-
The connector can be configured to reconcile from and provision to user-defined object classes and their attributes. By default, the target system uses the user object class. The connector can be configured to accommodate additional object classes that you define on the target system.
1.4.1.2 Connector for Microsoft ADAM
Figure 1-2 shows the architecture of the connector for Microsoft ADAM.
Figure 1-2 Architecture of the Connector for Microsoft ADAM
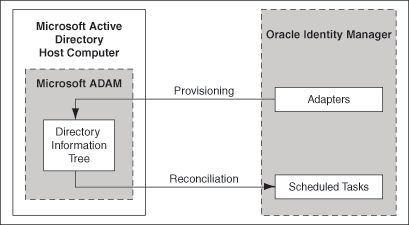
Description of ''Figure 1-2 Architecture of the Connector for Microsoft ADAM''
There are minor attribute-level and operational differences in the support provided by the connector for Microsoft ADAM and Microsoft Active Directory. The field mappings defined between Oracle Identity Manager and the target system are different. The connector can be configured to integrate Microsoft ADAM for either trusted source reconciliation or account management. For Microsoft ADAM, the connector employs a set of attribute mapping rules for provisioning and reconciliation that is different from the attribute mapping rules employed for Microsoft Active Directory.
Where required, this guide provides information and instructions that are specific to Microsoft ADAM.
1.4.2 Lookup Fields Used During Connector Operations
During a provisioning operation, you use a lookup field on the process form to specify a single value from a set of values. For example, you use the Country lookup field to select a country from the list of countries in the lookup field. When you deploy the connector, lookup definitions corresponding to the lookup fields on the target system are created in Oracle Identity Manager. Lookup field synchronization involves copying additions or changes made to the target system lookup fields into the lookup definitions in Oracle Identity Manager.
The following is the format in which data is stored after lookup definition synchronization:
Code Key: <IT_RESOURCE_KEY>~<VALUE_FROM_TARGET_SYSTEM>
Decode: <IT_RESOURCE_NAME>~< VALUE_FROM_TARGET_SYSTEM>
For example, in the Lookup.ADReconciliation.GroupLookup lookup definition, values will be stored in the following format:
Code Key: <IT_RESOURCE_KEY>~<DISTINGUISHED_NAME>
Decode: <IT_RESOURCE_NAME>~<DISTINGUISHED_NAME>
During a provisioning operation, lookup fields are populated with values corresponding to the target system that you select for the operation.
The "Lookup Definition" column of Table 1-2 lists the Oracle Identity Manager lookup definitions that correspond to target system lookup fields listed in the "Target System Field" column of the table.
Table 1-2 Lookup Definitions Synchronized with the Target System
| Lookup Definition | Target System Field | Scheduled Task for Synchronization |
|---|---|---|
|
The distinguishedName field of groups |
You use the AD Group Lookup Recon scheduled task to synchronize this lookup definition. This scheduled task is discussed in "Scheduled Tasks for Lookup Field Synchronization". |
|
|
The distinguishedName field of organizations |
You use the AD Organization Lookup Recon scheduled task to synchronize this lookup definition. This scheduled task is discussed in "Scheduled Tasks for Lookup Field Synchronization". |
Table 1-3 describes the other lookup definitions that are created in Oracle Identity Manager when you deploy the connector. These lookup definitions are either prepopulated with values or values must be entered in them after the connector is deployed.
Table 1-3 Other Lookup Definitions
| Lookup Definition | Description of Values | Method to Specify Values for the Lookup Definition |
|---|---|---|
|
Values of parameters used during reconciliation and provisioning |
You use this lookup definition to specify parameters that are used during both reconciliation and provisioning. This lookup definition is discussed in "Configuring the Lookup.AD.Configuration Lookup Definition". |
|
|
Country codes and names |
You manually add or update entries in this lookup definition based on the values in the Country lookup field on the target system. This lookup definition is discussed in "Configuring the Lookup.AD.Country Lookup Definition". |
|
|
Names of Terminal Services Profile fields of Microsoft Active Directory Note: This lookup definition is not used for Microsoft ADAM. |
This lookup definition is prepopulated with values. The name of this lookup definition is the default value of the Remote Manager Prov Lookup parameter of the ADITResource IT resource, which is discussed in "Configuring the IT Resource for the Target System". |
|
|
User field mappings between Microsoft Active Directory and Oracle Identity Manager |
This lookup definition is prepopulated with values, and it is used during user provisioning operations. You can add values in this lookup definition by performing the procedure described in "Adding New Fields for Provisioning". |
|
|
User field mappings between Microsoft ADAM and Oracle Identity Manager |
This lookup definition is prepopulated with values, and it is used during user provisioning operations. You can add values in this lookup definition by performing the procedure described in "Adding New Fields for Provisioning". |
|
|
User field mappings between Microsoft Active Directory and Oracle Identity Manager |
This lookup definition is prepopulated with values, and it is used during user reconciliation operations. You can add values in this lookup definition by performing the procedure described in "Adding New Fields for Target Resource Reconciliation" and "Adding New Fields for Trusted Source Reconciliation". |
|
|
User field mappings between Microsoft ADAM and Oracle Identity Manager |
This lookup definition is prepopulated with values, and it is used during user reconciliation operations. You can add values in this lookup definition by performing the procedure described in "Adding New Fields for Target Resource Reconciliation" and "Adding New Fields for Trusted Source Reconciliation". |
|
|
Group field mappings between Microsoft Active Directory and Oracle Identity Manager |
This lookup definition is prepopulated with values, and it is used during group provisioning operations. You can add values in this lookup definition by performing the procedure described in "Adding New Fields for Provisioning". |
|
|
Group field mappings between Microsoft ADAM and Oracle Identity Manager |
This lookup definition is prepopulated with values, and it is used during group provisioning operations. You can add values in this lookup definition by performing the procedure described in "Adding New Fields for Provisioning". |
|
|
Names of constants and variables defined in the Java classes that constitute the connector |
You must not change the predefined values in this lookup definition. |
|
|
Group field mappings between Microsoft Active Directory and Oracle Identity Manager |
This lookup definition is prepopulated with values, and it is used during group reconciliation operations. You can add values in this lookup definition by performing the procedure described in "Adding New Fields for Target Resource Reconciliation". |
|
|
Group field mappings between Microsoft ADAM and Oracle Identity Manager |
This lookup definition is prepopulated with values, and it is used during group reconciliation operations. You can add values in this lookup definition by performing the procedure described in "Adding New Fields for Target Resource Reconciliation". |
|
|
Names of constants that are used to represent Terminal Services Profile fields of Microsoft Active Directory Note: This lookup definition is not used for Microsoft ADAM. |
This lookup definition is used to hold names of constants that are used to represent Terminal Services Profile fields of Microsoft Active Directory. You must not change the predefined values in this lookup definition. |
1.4.3 Target Resource Reconciliation
Target resource reconciliation involves fetching data about newly created or modified accounts on the target system and using this data to add or modify resources assigned to OIM Users.
The AD User Target Recon scheduled task is used to initiate a target resource reconciliation run. This scheduled task is discussed in "Scheduled Tasks for Target Resource Reconciliation".
See Also:
The "Reconciliation" section in Oracle Identity Manager Connector Concepts for conceptual information about target resource reconciliationThis section discusses the following topics:
1.4.3.1 User Fields for Target Resource Reconciliation
Table 1-4 lists the user identity fields whose values are fetched during a target resource reconciliation run. The Remote Manager is used to implement the reconciliation of Terminal Services Profile fields.
Table 1-4 User Fields for Target Resource Reconciliation
| Process Form Field | Target System Field | Description |
|---|---|---|
|
User must change password at next logon This is a check box. |
|
Flag that indicates whether or not the user must change the password at next logon. If the value is |
|
Password never expires This is a check box. |
|
Flag that controls the Password Never Expires property |
|
Account Expiration Date This is a date field. |
accountExpires On Microsoft ADAM 2003, the value is stored in time-stamp format. For example: On Microsoft ADAM 2008, the value is stored in date format. For example: This is a mandatory field. On Microsoft ADAM 2003, you can enter 0 while creating an account. |
Date when the account expires |
|
First Name |
givenName This is a mandatory field. |
First name |
|
Last Name This is a mandatory field. |
sn This is a mandatory field. |
Last name |
|
Middle Name |
initials |
Initials for the user's middle name |
|
Full Name This is a mandatory field. |
displayName This is a mandatory field. |
Full name |
|
Telephone Number |
telephoneNumber |
Telephone number |
|
E Mail |
|
E-mail address |
|
Post Office Box |
postOfficeBox |
Post-office box |
|
State |
st |
State |
|
Zip |
postalCode |
ZIP code |
|
Home Phone |
homePhone |
Home phone number |
|
Pager |
pager |
Pager number |
|
Mobile |
mobile |
Mobile number |
|
Fax |
facsimileTelephoneNumber |
Fax number |
|
IP Phone |
ipPhone |
IP phone number |
|
Department |
department |
Department |
|
Title |
title |
Title |
|
Company |
company |
Company |
|
Country This is a lookup field. |
c |
Country |
|
Street |
StreetAddress |
Street address |
|
Manager Name |
manager |
Manager name |
|
Office |
physicalDeliveryOfficeName |
Office location |
|
City |
l |
City |
|
User ID This is a mandatory field. |
sAMAccountName This is a mandatory field in Microsoft Active Directory. This field does not exist in Microsoft ADAM. |
User's logon name |
|
Terminal Home Directory This is a string data type field. |
Part of the data stored in the userParameters field Note: This field does not exist in Microsoft ADAM. |
Full path of the home directory for the Terminal Server user Note: Reconciliation of values in this field is enabled by the Remote Manager. |
|
Terminal Profile Path This is a string data type field. |
Part of the data stored in the userParameters field Note: This field does not exist in Microsoft ADAM. |
Profile that is used when the user logs on to a Terminal Server The profile can be roaming or mandatory. A roaming profile remains the same, regardless of the computer from which the user logs in. The user can make changes to a roaming profile, but not to a mandatory profile. Any changes a user makes while logged in with a mandatory profile are retained only for that Terminal Services session. Changes are lost when the user starts another Terminal Services session. Note: Reconciliation of values in this field is enabled by the Remote Manager. |
|
Terminal Services Allow Login This is a check box. |
Part of the data stored in the userParameters field Note: This field does not exist in Microsoft ADAM. |
Specifies whether or not the user is permitted to log on to the Terminal Server Note: Reconciliation of values in this field is enabled by the Remote Manager. If the target system is Microsoft Windows 2003, then the "Allow logon to terminal server" check box is used. During a reconciliation run, if the target system check box is selected, then the corresponding process form check box is selected. If the target system is Microsoft Windows 2003 with SP2, then the "Deny this user permissions to log on to any Terminal Server" check box is used. During a reconciliation run, if the target system check box is selected, then the corresponding process form check box is deselected. |
|
Account is Locked Out This is a check box. |
lockoutTime |
Specifies whether the user account must be locked or unlocked |
|
Group Name This multivalued field is a lookup field on the process form. |
memberOf |
Distinguished names of the groups to which a user belongs |
|
User Principal Name This is a mandatory field. |
userPrincipalName This is a mandatory field on the target system. |
The user principal name is the domain-specific name of the user. The format is as follows:
|
|
Common Name This is a mandatory field. |
cn This is a mandatory field. |
Common name on the target system You can change the value of this field. |
|
Organization Name |
The organization name is extracted from the distinguishedName value. |
Organization name on the target system |
1.4.3.2 Group Fields for Reconciliation
Note:
If you are using Oracle Identity Manager release 11.1.1 or 11.1.2.x, then you cannot reconcile data from group fields of the target system. This is also mentioned in the "Known Issues" chapter.Table 1-8 lists the group fields of the target system from which values are fetched during reconciliation. The AD Group Recon scheduled task is used to reconcile group data.
Note:
While creating a group on Microsoft ADAM, you must provide values for the cn and displayName fields. These are mandatory fields on Microsoft ADAM.Table 1-5 Group Fields for Reconciliation
| Group Field on Oracle Identity Manager | Microsoft Active Directory Field | Microsoft ADAM Field | Description |
|---|---|---|---|
|
Organization Name |
ou extracted from the distinguishedName of the group |
ou extracted from the distinguishedName of the group |
Organization name |
|
Group objectGUID |
objectGUID |
objectGUID |
Group objectGUID |
|
Group type |
groupType |
groupType |
Group type |
|
Group name This is a mandatory field. |
sAMAccountName This is a mandatory field. |
displayName This is a mandatory field. |
Group name |
|
Group Display Name |
cn |
cn |
Common name of the group |
These field mappings are stored in the following lookup definitions:
-
For Microsoft Active Directory: Lookup.ADGroupReconciliation.FieldMap
-
For Microsoft ADAM: Lookup.ADAMGroupReconciliation.FieldMap
1.4.3.3 Reconciliation Rules for Target Resource Reconciliation
See Also:
One of the following guides for generic information about reconciliation matching and action rules:-
For Oracle Identity Manager release 9.1.0.x: Oracle Identity Manager Connector Concepts
-
For Oracle Identity Manager release 11.1.1 or 11.1.2.x: Oracle Fusion Middleware User's Guide for Oracle Identity Manager
The following is the process matching rule:
Rule name: Target Resource Recon Rule
Rule element: (ObjectGUID Equals objectGUID) OR (User Login Equals User ID)
In the first rule component:
-
ObjectGUID to the left of "Equals" is the objectGUID of the resource assigned to the OIM User.
-
objectGUID to the right of "Equals" is the objectGUID of the resource on the target system.
In the second rule component:
-
User Login is the User ID field on the OIM User form.
-
User ID is the sAMAccountName field of Microsoft Active Directory or the userPrincipalName field of Microsoft ADAM.
This rule supports the following scenarios:
-
You can provision multiple Microsoft Active Directory resources to the same OIM User, either on Oracle Identity Manager or directly on the target system.
-
You can change the user ID of a user on the target system.
This is illustrated by the following use cases:
-
Use case 1: You provision an AD account for an OIM User, and you also create an account for the user directly on the target system.
When the first rule condition is applied, no match is found. Then, the second rule condition is applied and it is determined that a second account has been given to the user on the target system. Details of this second account are associated with the OIM User by the reconciliation engine.
-
Use case 2: An OIM User has an AD account. You then change the user ID of the user on the target system.
During the next reconciliation run, application of the first rule condition helps match the resource with the record.
After you deploy the connector, you can view the reconciliation rule for target resource reconciliation by performing the following steps:
Note:
Perform the following procedure only after the connector is deployed.-
Log in to the Oracle Identity Manager Design Console.
-
Expand Development Tools.
-
Double-click Reconciliation Rules.
-
Search for Target Resource Recon Rule. Figure 1-3 shows the reconciliation rule for target resource reconciliation.
Figure 1-3 Reconciliation Rule for Target Resource Reconciliation
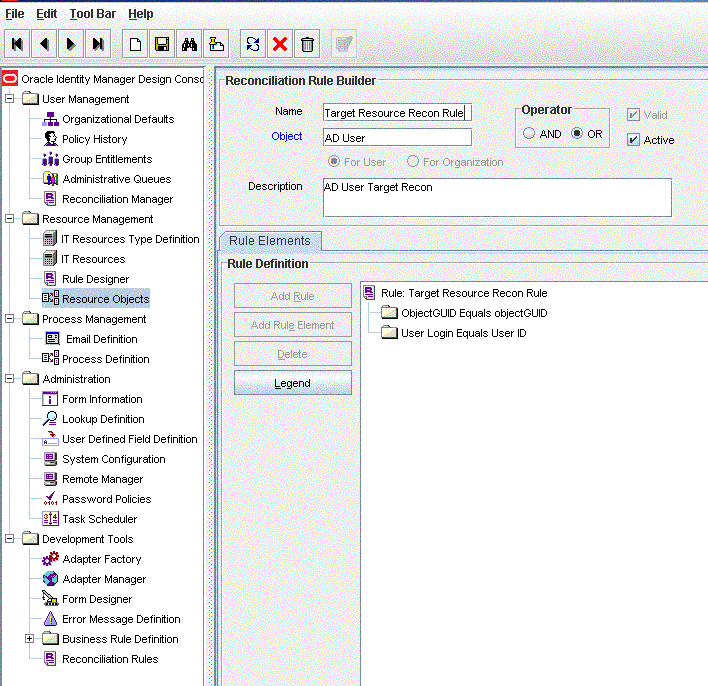
Description of ''Figure 1-3 Reconciliation Rule for Target Resource Reconciliation''
1.4.3.4 Reconciliation Action Rules for Target Resource Reconciliation
Table 1-6 lists the action rules for target resource reconciliation.
Table 1-6 Action Rules for Target Resource Reconciliation
| Rule Condition | Action |
|---|---|
|
No Matches Found |
Assign to Administrator With Least Load |
|
One Entity Match Found |
Establish Link |
|
One Process Match Found |
Establish Link |
Note:
No action is performed for rule conditions that are not predefined for this connector. You can define your own action rule for such rule conditions. For information about modifying or creating reconciliation action rules, see one of the following guides:-
For Oracle Identity Manager release 9.1.0.x: Oracle Fusion Middleware User's Guide for Oracle Identity Manager
-
For Oracle Identity Manager release 11.1.1 or 11.1.2.x: Oracle Fusion Middleware Developer's Guide for Oracle Identity Manager
After you deploy the connector, you can view the reconciliation action rules for target resource reconciliation by performing the following steps:
-
Log in to the Oracle Identity Manager Design Console.
-
Expand Resource Management.
-
Double-click Resource Objects.
-
Search for and open the AD User resource object.
-
Click the Object Reconciliation tab, and then click the Reconciliation Action Rules tab. The Reconciliation Action Rules tab displays the action rules defined for this connector. Figure 1-4 shows the reconciliation action rule for target resource reconciliation.
Figure 1-4 Reconciliation Action Rules for Target Resource Reconciliation
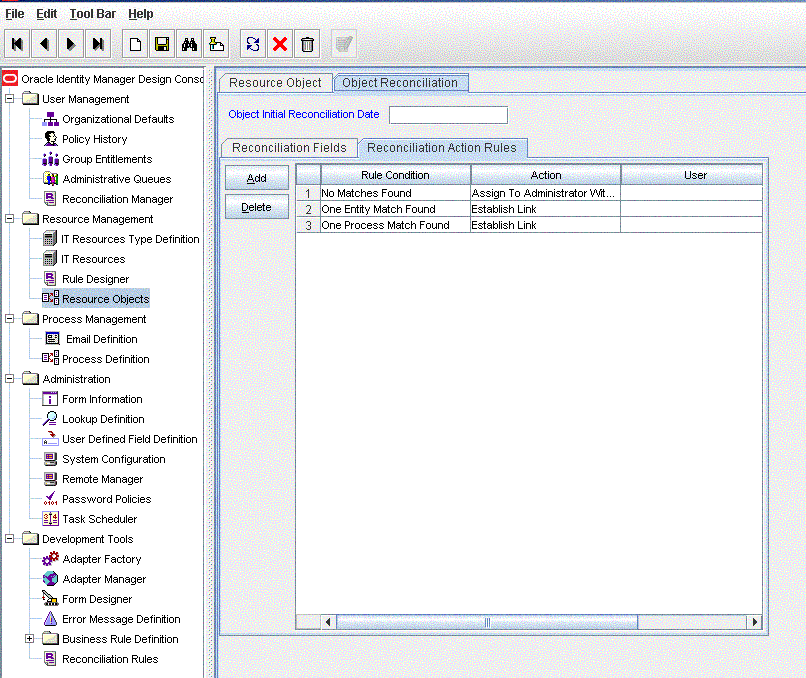
Description of ''Figure 1-4 Reconciliation Action Rules for Target Resource Reconciliation''
1.4.4 Provisioning
Provisioning involves creating or modifying user data on the target system through Oracle Identity Manager.
See Also:
One of the following guides for conceptual information about provisioning:-
For Oracle Identity Manager release 9.1.0.x: Oracle Identity Manager Connector Concepts
-
For Oracle Identity Manager release 11.1.1 or 11.1.2.x: Oracle Fusion Middleware User's Guide for Oracle Identity Manager
This section discusses the following topics:
1.4.4.1 User Provisioning Functions Supported by the Connector
Table 1-7 lists the supported user provisioning functions and the adapters that perform these functions. The functions listed in the table correspond to either a single or multiple process tasks.
See Also:
Oracle Fusion Middleware User's Guide for Oracle Identity Manager for generic information about process tasks and adaptersTable 1-7 User Provisioning Functions Supported by the Connector
| Function | Adapter |
|---|---|
|
Create a user account |
ADCS Create User If the user is successfully created, then the following adapters are triggered:
Note: If you do not want the ADCS Execute Remote Script adapter to run during the Create User provisioning operation, then see "Removing the ExecuteRemoteScripts Process Task". The ADCS Execute Remote Script adapter is not used in Microsoft ADAM. |
|
Move a user account from one organization to another in the same domain |
ADCS Move User |
|
Delete a user account |
ADCS Delete User |
|
Enable a disabled user account |
ADCS Enable User |
|
Disable a user account |
ADCS Disable User |
|
Lock a user account |
ADCS Lock_Unlock User |
|
Unlock a user account |
ADCS Lock_Unlock User |
|
Update the "User Must Change Password at Next Logon" flag |
ADCS Must Change PWD |
|
Update the account expiration date |
ADCS Set Account Exp Date |
|
Update the "Password Never Expires" flag |
ADCS Pwd Never Expires |
|
Update the user ID |
ADCS Change Attribute |
|
Update the first name |
ADCS Change Attribute |
|
Update the last name |
ADCS Change Attribute |
|
Update common name |
ADCS Rename User Account |
|
Update the password Note: The password can be changed only if SSL communication is configured between Oracle Identity Manager and the target system. The procedure to configure SSL is described later in the guide. |
ADCS Set User Password |
|
Add a user account to a group |
ADCS ADD User To Group |
|
Remove a user account from a group |
ADCS Remove User From Group |
|
Update the redirection e-mail address |
ADCS Update Redirect Mail ID |
|
Update middle name |
ADCS Change Attribute |
|
Update city |
ADCS Change Attribute |
|
Update company |
ADCS Change Attribute |
|
Update country |
ADCS Change Attribute |
|
Update department |
ADCS Change Attribute |
|
Update e-mail address |
ADCS Change Attribute |
|
Update fax number |
ADCS Change Attribute |
|
Update IP phone number |
ADCS Change Attribute |
|
Update manager name |
ADCS Change Attribute |
|
Update mobile number |
ADCS Change Attribute |
|
Update office phone number |
ADCS Change Attribute |
|
Create OU |
ADCS Create OU |
|
Rename OU |
ADCS Change Org Name |
|
Move OU |
ADCS Move OU |
|
Delete OU |
ADCS Delete OU |
1.4.4.2 User Fields for Provisioning
Table 1-8 lists the user identity fields of the target system for which you can specify or modify values during provisioning operations. The Remote Manager is used to implement the provisioning of Terminal Services Profile fields.
Note:
The adapters listed in the Adapter column of the table are used during Update User provisioning operations. During a Create User provisioning operation, the ADCS Create User adapter is used to populate values in all the target system user fields.Table 1-8 User Fields for Provisioning
| Process Form Field | Target System Field | Description | Adapter |
|---|---|---|---|
|
Password This field is on both the process form and the OIM User form. It is a mandatory field on the OIM User form. During a provisioning operation, the Password field on the process form is prepopulated with the value entered in the Password field on the OIM User form. If SSL is configured between Oracle Identity Manager and the target system, then the Password field on the process form is a mandatory field. |
unicodePwd |
User's password in UTF-8 format |
ADCS Set User Password |
|
User must change password at next logon This is a check box. |
|
Flag that indicates whether or not the user must change the password at next logon. If the value is |
ADCS Must Change PWD |
|
Password never expires This is a check box. |
|
Flag that controls the Password Never Expires property |
ADCS Pwd Never Expire |
|
Account Expiration Date This is a date field. |
accountExpires When you create a user on Microsoft ADAM:
|
Date when the account expires |
ADCS Set Account Exp Date |
|
Object GUID This is a hidden field on both the process form and the OIM User form. |
objectGUID |
Object GUID of the user |
ADCS Get ObjectGUID |
|
Organization Name This is a Lookup field. It is a mandatory field on the OIM User form. |
Distinguished name of the organization |
Name of the organization |
ADCS Move User |
|
First Name This field is on both the process form and the OIM User form. It is a mandatory field on the OIM User form. During a provisioning operation, the First Name field on the process form is prepopulated with the value entered in the First Name field on the OIM User form. |
givenName |
First name |
ADCS Change Attribute |
|
Last Name This field is on both the process form and the OIM User form. It is a mandatory field on the OIM User form. During a provisioning operation, the Last Name field on the process form is prepopulated with the value entered in the Last Name field on the OIM User form. |
sn |
Last name |
ADCS Change Attribute |
|
Middle Name This field is on both the process form and the OIM User form. During a provisioning operation, the Middle Name field on the process form is prepopulated with the value entered in the Middle Name field on the OIM User form. |
initials |
Initials for the user's middle name |
ADCS Change Attribute |
|
Full Name This is a mandatory field on the process form. |
cn, displayName |
Display name for a user During a Create User provisioning operation, the cn and displayName fields are populated with a combination of the user's first name, middle initial, and last name entered on the OIM User form. The full name is displayed in the following format on the process form: FIRSTNAME MIDDLE_INITIAL. LASTNAME For example: If the middle initial is not entered, then the name is displayed as, for example, During an Update provisioning operation, only the value in the displayName field is updated. |
ADCS Change Attribute |
|
Telephone Number |
telephoneNumber |
Telephone number |
ADCS Change Attribute |
|
E Mail This field is on both the process form and the OIM User form. |
|
E-mail address |
ADCS Change Attribute |
|
Post Office Box |
postOfficeBox |
Post-office box |
ADCS Change Attribute |
|
State |
st |
State |
ADCS Change Attribute |
|
Zip |
postalCode |
ZIP code |
ADCS Change Attribute |
|
Home Phone |
homePhone |
Home phone number |
ADCS Change Attribute |
|
Pager |
pager |
Pager number |
ADCS Change Attribute |
|
Mobile |
mobile |
Mobile number |
ADCS Change Attribute |
|
Fax |
facsimileTelephoneNumber |
Fax number |
ADCS Change Attribute |
|
IP Phone |
ipPhone |
IP phone number |
ADCS Change Attribute |
|
Department |
department |
Department |
ADCS Change Attribute |
|
Title |
title |
Title |
ADCS Change Attribute |
|
Company |
company |
Company |
ADCS Change Attribute |
|
Country This is a lookup field. |
c |
Country |
ADCS Change Attribute |
|
Street |
StreetAddress |
Street address |
ADCS Change Attribute |
|
Manager Name |
manager |
Manager name You must enter the manager name in the DN format. For example:
|
ADCS Change Attribute |
|
Office |
physicalDeliveryOfficeName |
Office Location |
ADCS Change Attribute |
|
City |
l |
City |
ADCS Change Attribute |
|
Redirection Mail ID |
ProxyAddresses |
E-mail address to which e-mail sent to the user must be redirected This e-mail address overrides the one set in the E Mail field. |
ADCS Update Redirect Mail ID |
|
Account is Locked out This is a check box. |
lockoutTime |
Specifies whether the user account must be locked or unlocked |
ADCS Lock_Unlock User |
|
User ID This field is on both the process form and the OIM User form. It is a mandatory field. During a provisioning operation, the User ID field on the process form is prepopulated with the value entered in the User ID field on the OIM User form. |
sAMAccountName This is a mandatory field in Microsoft Active Directory. This field does not exist in Microsoft ADAM. |
User's logon name |
ADCS Change Attribute |
|
Group Name This multivalued field is a lookup field on the process form. |
memberOf |
Distinguished name of the groups to which a user belongs |
The following adapters are for provisioning operations that involve changes to the memberOf field: ADCS ADD User To Group ADCS remove User From Group |
|
Common Name |
cn |
Common name of the user |
ADCS Rename User Account |
|
Part of the data stored in the userParameters field Note: This field does not exist in Microsoft ADAM. A value that you enter in this field would be ignored during provisioning operations in Microsoft ADAM. |
Full path of the home directory for the Terminal Server user Sample value: During a provisioning operation, you must enter the full, absolute path of the home directory, as shown in the sample value. Note: The Remote Manager enables provisioning operations on this field. |
ADCS ExecuteRemote Script |
|
|
Part of the data stored in the userParameters field Note: This field does not exist in Microsoft ADAM. A value that you enter in this field would be ignored during provisioning operations in Microsoft ADAM. |
Profile that is used when the user logs on to a Terminal Server The profile can be roaming or mandatory. A roaming profile remains the same, regardless of the computer from which the user logs in. The user can make changes to a roaming profile, but not to a mandatory profile. Any changes a user makes while logged in with a mandatory profile are retained only for that Terminal Services session. The changes are lost when the user starts another Terminal Services session. Note: The Remote Manager enables provisioning operations on this field. |
ADCS ExecuteRemote Script |
|
|
This is a check box. |
Part of the data stored in the userParameters field Note: This field does not exist in Microsoft ADAM. A value that you enter in this field would be ignored during provisioning operations in Microsoft ADAM. |
Specifies whether or not the user is permitted to log on to the Terminal Server Note: The Remote Manager enables provisioning operations on this field. If the target system is Microsoft Windows 2003, then the "Allow logon to terminal server" check box is used. During a provisioning operation, if the process form check box is selected, then the target system check box is selected. If the target system is Microsoft Windows 2003 with SP2, then the "Deny this user permissions to log on to any Terminal Server" check box is used. During a provisioning operation, if the process form check box is selected, then the target system check box is deselected. |
ADCS ExecuteRemote Script |
|
User Principal Name This is a mandatory field. |
userPrincipalName This is a mandatory field. Note: The value for UserPrincipalName must be entered in the format shown in the following example: If the root context is |
The user principal name is the domain-specific name of the user. This field is pre-populated on the Administrative and User Console. The format is as follows: USER_ID_VALUE@UPN_DOMAIN_VALUE Note: When you update this field, you can change the User ID part but you must not change the domain name. If you change the domain name, then the user will not be matched on the target system. |
ADCS Change Attribute |
Table 1-9 lists special characters that are supported in process form fields.
Note:
The following special characters are not supported in process form fields:-
Single quotation mark (')
-
Double quotation mark (")
Table 1-9 Special Characters Supported in Process Form Fields
| Name of the Character | Character |
|---|---|
|
ampersand |
& |
|
asterisk |
* |
|
at sign |
@ |
|
caret |
^ |
|
comma |
, |
|
dollar sign |
$ |
|
equal sign |
= |
|
exclamation point |
! |
|
hyphen |
- |
|
left brace |
{ |
|
left bracket |
[ |
|
left parenthesis |
( |
|
number sign |
# |
|
percent sign |
% |
|
period |
. |
|
plus sign |
+ |
|
question mark |
? |
|
right brace |
} |
|
right bracket |
] |
|
right parenthesis |
) |
|
slash |
/ |
|
underscore |
_ |
|
vertical bar Note: This special character is supported only in the Password field |
| |
1.4.4.3 Group Fields for Provisioning
Table 1-8 lists the group fields of the target system for which you can specify or modify values during provisioning operations.
Note:
The adapters listed in the Adapter column of the table are used during Update Group provisioning operations. During a Create User provisioning operation, the ADCS Create Group adapter is used to populate values in all the target system user fields.Table 1-10 Group Fields for Provisioning
| Group Field on Oracle Identity Manager | Target System Field | Description | Adapter |
|---|---|---|---|
|
Organization Name |
ou |
Organization name |
ADCS Move Group |
|
Group Name |
For Microsoft Active Directory: sAMAccountName For Microsoft ADAM: displayName |
Group name |
ADCS Change Group Attribute |
|
Group objectGUID |
objectGUID |
Group objectGUID |
ADCS Get Group ObjectGUID Created |
|
Group Display Name |
cn |
Group display name |
ADCS Rename Group |
|
Group type |
groupType |
Group type |
Not applicable for an existing user |
These field mappings are stored in the following lookup definitions:
-
For Microsoft Active Directory: AtMap.ADGroup
-
For Microsoft ADAM: AtMap.ADAMGroup
1.4.5 Trusted Source Reconciliation
Trusted source reconciliation involves fetching data about newly created or modified accounts on the target system and using that data to create or update OIM Users.
The AD User Trusted Recon scheduled task is used to initiate a trusted source reconciliation run. This scheduled task is discussed in "Scheduled Tasks for Trusted Source Reconciliation".
This section discusses the following topics:
1.4.5.1 User Fields for Trusted Source Reconciliation
Table 1-11 lists the user identity fields whose values are fetched from the target system during a trusted source reconciliation run.
Note:
While creating a user on Microsoft ADAM, you must provide values for the userPrincipalName, sn, givenName, displayName, cn, and accountExpires fields. These are mandatory fields on Microsoft ADAM.On Microsoft ADAM 2003, enter 0 as the default value of the accountExpires field.
Table 1-11 User Fields for Trusted Source User Reconciliation
| OIM User Form Field | Target System Field | Description |
|---|---|---|
|
User ID This is a mandatory field. |
|
User's logon name |
|
First Name This is a mandatory field. |
givenName This is a mandatory field. |
First name |
|
Last Name This is a mandatory field. |
sn This is a mandatory field. |
Last name For a record fetched during trusted source reconciliation, if there is no value in this attribute, then the value from the Common Name attribute is populated in the Last Name field on the process form. |
|
Middle Name |
initials |
Middle name |
|
Organization This is a mandatory field. |
The name of the organization is extracted from the distinguished name of the organization. |
This is the name of the organization to which users belong if you set the value of the Maintain Hierarchy attribute to If Maintain Hierarchy is set to |
|
E Mail |
|
E-mail address |
|
Status |
|
This field stores the status of the user account. See "Guidelines on Configuring Reconciliation" for information about a guideline related to this field on Microsoft ADAM. |
1.4.5.2 Reconciliation Rule for Trusted Source Reconciliation
See Also:
Oracle Fusion Middleware User's Guide for Oracle Identity Manager for generic information about reconciliation matching and action rulesThe following is the entity matching rule:
Rule name: Trusted Source Recon Rule
Rule: User Login Equals User ID
In this rule:
-
User Login is the User ID field on the OIM User form.
-
User ID is the sAMAccountName field of Microsoft Active Directory or the userPrincipalName field of Microsoft ADAM.
After you deploy the connector, you can view the reconciliation rule for trusted source reconciliation by performing the following steps:
-
Log in to the Oracle Identity Manager Design Console.
-
Expand Development Tools.
-
Double-click Reconciliation Rules.
-
Search for Trusted Source Recon Rule. Figure 1-5 shows the reconciliation rule for trusted source reconciliation.
Figure 1-5 Reconciliation Rule for Trusted Source Reconciliation
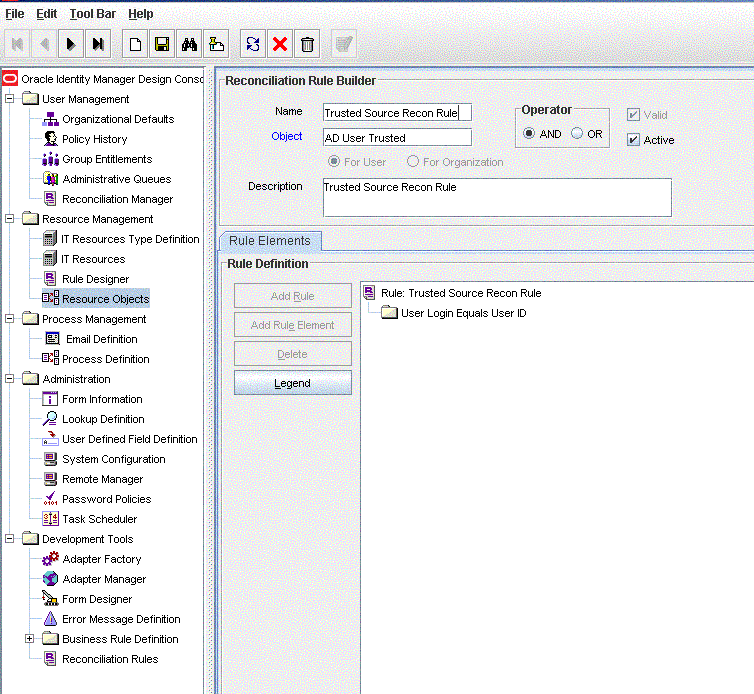
Description of ''Figure 1-5 Reconciliation Rule for Trusted Source Reconciliation''
Note:
In Microsoft Active Directory,sAMAccountName attribute is a mandatory and unique field.1.4.5.3 Reconciliation Action Rules for Trusted Source Reconciliation
Table 1-12 lists the action rules for trusted source reconciliation.
Table 1-12 Action Rules for Trusted Source Reconciliation
| Rule Condition | Action |
|---|---|
|
No Matches Found |
Create User |
|
One Entity Match Found |
Establish Link |
|
One Process Match Found |
Establish Link |
Note:
No action is performed for rule conditions that are not predefined for this connector. You can define your own action rule for such rule conditions. For information about modifying or creating reconciliation action rules, see one of the following guides:-
For Oracle Identity Manager release 9.1.0.x:Oracle Fusion Middleware User's Guide for Oracle Identity Manager
-
For Oracle Identity Manager release 11.1.1 or 11.1.2.x: Oracle Fusion Middleware Developer's Guide for Oracle Identity Manager
After you deploy the connector, you can view the reconciliation action rules for target resource reconciliation by performing the following steps:
-
Log in to the Oracle Identity Manager Design Console.
-
Expand Resource Management.
-
Double-click Resource Objects.
-
Locate the AD User resource object.
-
Click the Object Reconciliation tab, and then the Reconciliation Action Rules tab. The Reconciliation Action Rules tab displays the action rules defined for this connector. Figure 1-6 shows the reconciliation action rule for trusted source reconciliation.
Figure 1-6 Reconciliation Action Rules for Trusted Source Reconciliation
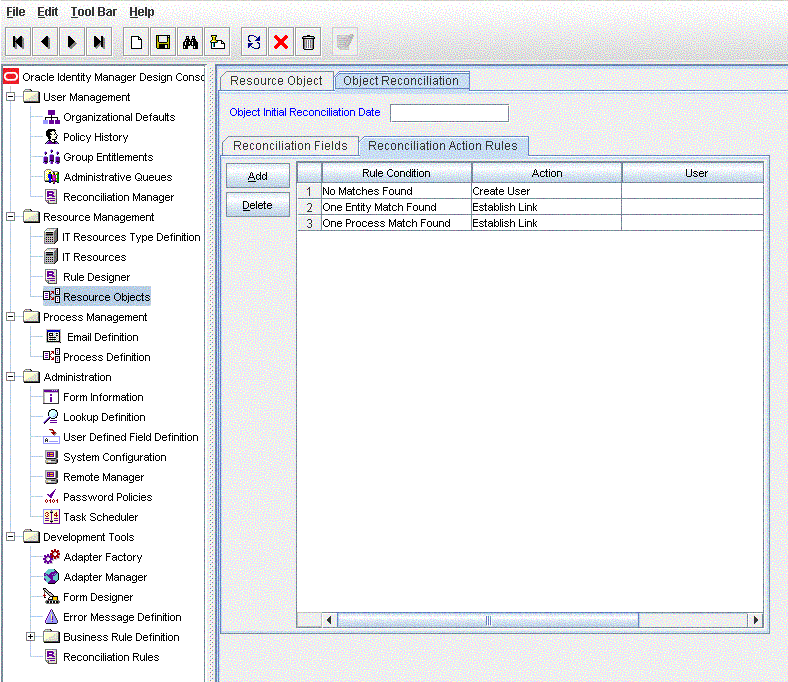
Description of ''Figure 1-6 Reconciliation Action Rules for Trusted Source Reconciliation''
1.4.5.4 Organization Reconciliation
As mentioned earlier, trusted source reconciliation fetches data about target system users into Oracle Identity Manager. This data is used to create or update records of OIM Users. You can configure trusted source reconciliation so that newly created OIM Users are placed in OIM Organizations that correspond to users' organizations on the target system. To enable this feature, you set the value of the MaintainHierarchy attribute of the trusted source reconciliation scheduled task (AD User Trusted Recon) to yes.
Note:
The scheduled tasks mentioned in this section are discussed in detail in "Scheduled Tasks for Trusted Source Reconciliation".To ensure that OIM Organizations corresponding to the target system organizations are created and ready for user data fetched during a trusted source reconciliation run, the organization reconciliation scheduled task (AD Organization Recon) must be run before the scheduled task for trusted source reconciliation. When the AD Organization Recon scheduled task is run, data about target system organizations is fetched and used to create OIM Organizations.
Note:
-
It is recommended that you set the MaintainHierarchy attribute to
yesonly if this option is acceptable in your operating environment. Otherwise, the default option of the MaintainHierarchy attribute set tonomust be used while running the trusted source reconciliation scheduled task. -
The AD Organization Recon scheduled task is independent of the organization lookup synchronization scheduled task (AD Organization Lookup Recon), which is used only in the account management mode.
OIM Organizations cannot completely model the organizational structure that is found on the target system because:
-
Although parent-child hierarchical relationships between organizations are supported in Oracle Identity Manager, the OIM Organizations namespace is a flat namespace. Therefore, two target system OUs that have the same name cannot be re-created in Oracle Identity Manager, even if their parent OUs are different.
-
In Oracle Identity Manager, organization names cannot contain special characters such as the equal sign (=) and the comma (,). This does not permit the reconciliation of fully qualified distinguished names (FQDNs) of target system OUs into Oracle Identity Manager.
-
Organization reconciliation does not cover reconciliation of updates to existing organizations on the target system. If you modify the name of an organization on the target system, then it is reconciled as a new organization in Oracle Identity Manager.
See Also:
"Guidelines on Configuring Reconciliation" for detailed information about guidelines on configuring organization reconciliation. Some of the points mentioned earlier are repeated in that section.Table 1-13 lists the organization fields whose values are fetched from the target system during organization reconciliation.
Table 1-13 Organization Fields for Trusted Source Organization Reconciliation
| Xellerate Organization Form Field | Target System Field | Description |
|---|---|---|
|
Organization Name |
Organization |
Distinguished name of the organization |
|
Organization Parent Name |
Distinguished name of the parent organization |
Name of the parent of the organization |
|
Organization Type |
- |
This field is not actually reconciled, because there is no corresponding Microsoft Active Directory field. During organization reconciliation, the value of this field is set to |
The following is the reconciliation rule for organization reconciliation:
Rule name: Organization Recon
Rule: Organization Name Equals Organizations.Organization Name
In this rule:
-
Organization Name is the Organization Name field on the Xellerate Organization form.
-
Organizations.Organization Name is the Organization Name field of Microsoft Active Directory or Microsoft ADAM.
Table 1-12 lists the action rules for organization reconciliation.
1.5 Roadmap for Deploying and Using the Connector
The following is the organization of information in the rest of this guide:
-
Chapter 2, "Deploying the Connector" describes procedures that you must perform on Oracle Identity Manager and the target system during each stage of connector deployment.
-
Chapter 4, "Extending the Functionality of the Connector" describes procedures that you can perform if you want to extend the functionality of the connector.
-
Chapter 3, "Using the Connector" describes guidelines on using the connector and the procedure to configure reconciliation runs and perform provisioning operations.
-
Chapter 5, "Testing the Connector" describes the procedure to use the connector testing utility and the Diagnostic Dashboard for testing the connector.
-
Chapter 6, "Known Issues" lists known issues associated with this release of the connector.
-
Appendix A, "Character Lengths of Target System Fields and Process Form Fields" provides information about the differences in lengths of target system fields and process form fields. This appendix also describes the procedure to change the lengths of process form fields.
-
Appendix B, "Special Characters Supported for Passwords" lists special characters that you can use in the Password field on the target system and Oracle Identity Manager.
-
Appendix C, "Terminal Services Profile Field Names for Reconciliation and Provisioning" lists the names of special Microsoft Active Directory fields. You use these names if you want to add one of these fields for reconciliation or provisioning.
-
Appendix D, "Sample Transformation Class" provides the code for a sample Java class. You can use this sample class to create a class for transforming reconciled data according to your requirements.
-
Appendix E, "Sample Validation Class" provides the code for a sample Java class. You can use this sample class to create a class for transforming reconciled data according to your requirements.