Administration and Deployment Guide
|
|
ALES Architecture
This section describes ALES components and provides information about deploying them on the network.
- ALES Components
- Administration Server
- Service Control Manager (SCM)
- Security Service Module (SSM)
- Security Providers
- Deployment Architecture
- Generalized Architecture
- Location of ALES Components
- WebLogic Clusters
ALES Components
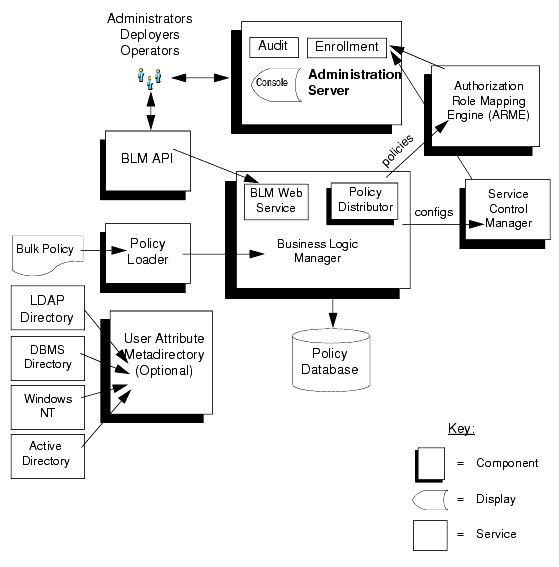
The following diagram gives a high-level view of ALES components.
Figure 1-1 High-Level View of ALES 2.1 Components
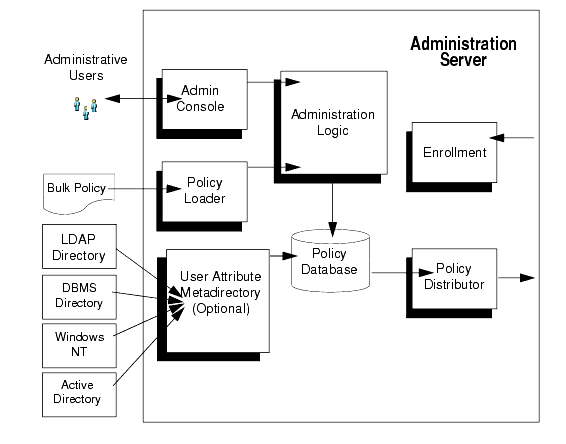
Administration Server
The Administration Server is a servlet-based application and can run in both WebLogic and Tomcat. It consists of the following components:
Business Logic Manager-The BLM is responsible for managing security policies stored in the Policy Database. The BLM includes the policy distributor which pushes policy to the runtime tier of ALES. The BLM features an external API for managing policy and configuration.
Policy Database-Maintains policy data in a relational database. This data is distributed to the Security Service Modules by the Policy Distributor.
Policy Loader-Imports policy data from an external file. The external file can be generated by another system or another Administrative Server, or it can be manually coded. For additional information on how to use the Policy Loader, see the Policy Managers Guide.
Authorization and Role Mapping Engine (ARME)-Enforces security policy for Administration Server and console as it does for any other runtime application.
Administrative Console-Supports administrative policy security and administration delegation through a web browser-based user interface. Security configuration, policy configuration, user attributes (if required), resources, and rules are all managed through the console.
Metadirectory-Stores user attributes from a variety of sources for use in making policy decisions. The metadirectory assembles attributes for each user and caches them for use by Security Service Modules.
Figure 1-2 Administration Server Architecture
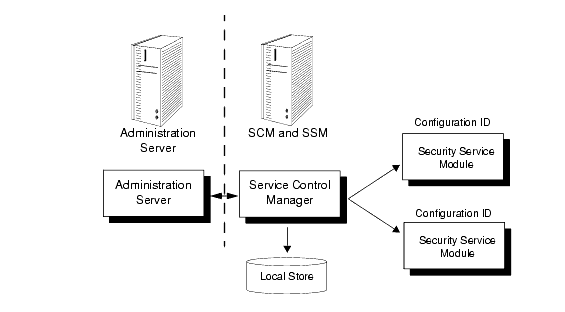
Service Control Manager (SCM)
The Service Control Module (SCM) is an essential component ALES's remote administration mechanism. Each Service Control Module stores SSM configuration data and provides each SSM on its machine the appropriate data.
The Service Control Manager receives and stores both full and incremental configuration updates. When a configuration change relevant to a SSM is made, it is provisioned to the Service Control Manager through the Policy Distributor. The provisioning mechanism ensures that only the configuration data absolutely required by a Service Control Manager is provisioned to that module. Likewise, the Service Control Manager ensures that only the configuration data absolutely required by an SSM is made available to that module.
Figure 1-3 Service Control Manager
Security Service Module (SSM)
SSMs are a platform specific security plug-ins that are embedded in applications, application servers, and web servers to be secured by ALES. The SSM ties the application server (or applications, web servers) into ALES so that all security administration for the application is performed through ALES.
Configuration data for each module is specified centrally and then distributed to and locally cached on the appropriate machine. A benefit of this architecture is that there is no impact on the application if the Administration Server is stopped.
Table 1-1 below describes the SSM modules provided with ALES.
Security Providers
Security providers are used to provide authentication, authorization, auditing, role mapping, and credential mapping, and other services. Each SSM can be configured with a set of security providers as described in Table 1-2.
Deployment Architecture
An ALES environment can consist of a single or multiple instances of the Administration Server, one or more Service Control Managers (hosted on individual machines), and any number of Security Service Modules, each associated with an SCM. Each Security Service Module may share or use different configuration or policy data, based on the business needs of an organization.The Administration Server serves as a central point of contact for instances and system administration tools.
Generalized Architecture
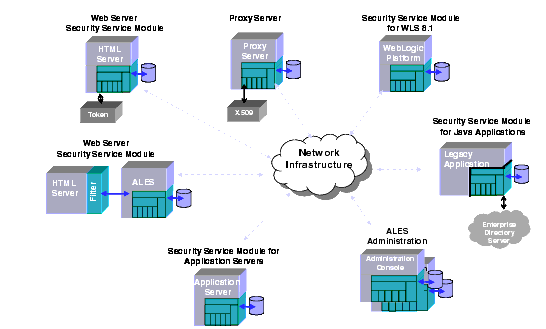
Installation of ALES depends on the application environment being secured. The basic requirement is that the Administration Server must be accessible to all Security Service Modules that are "plugged" into the applications being secured in that domain. A Service Control Manager must be installed on any machine running one or more SSMs.
Figure 1-4 below shows SSMs deployed on varying application environments and connecting to the Administration Server on a separate machine.
Figure 1-4 Distributed Computing Security Infrastructure
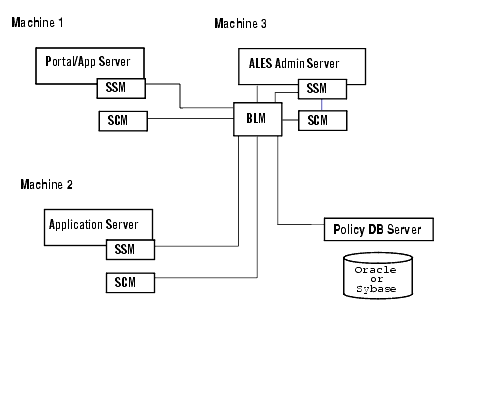
Location of ALES Components
Figure 1-5 below provides some insight into the interconnections of the ALES components.
Figure 1-5 Location of ALES Components
WebLogic Clusters
You can configure multiple servers to be part of a WebLogic cluster to support failover. A cluster is a group of server instances that work together to provide scalability and high-availability for applications. For instructions, see the Installing the Administration Server.